Saviynt Blog
Stay up to date on the latest identity security news, research and more.
Content Type
Industry
Solutions


12 / 19 / 2025
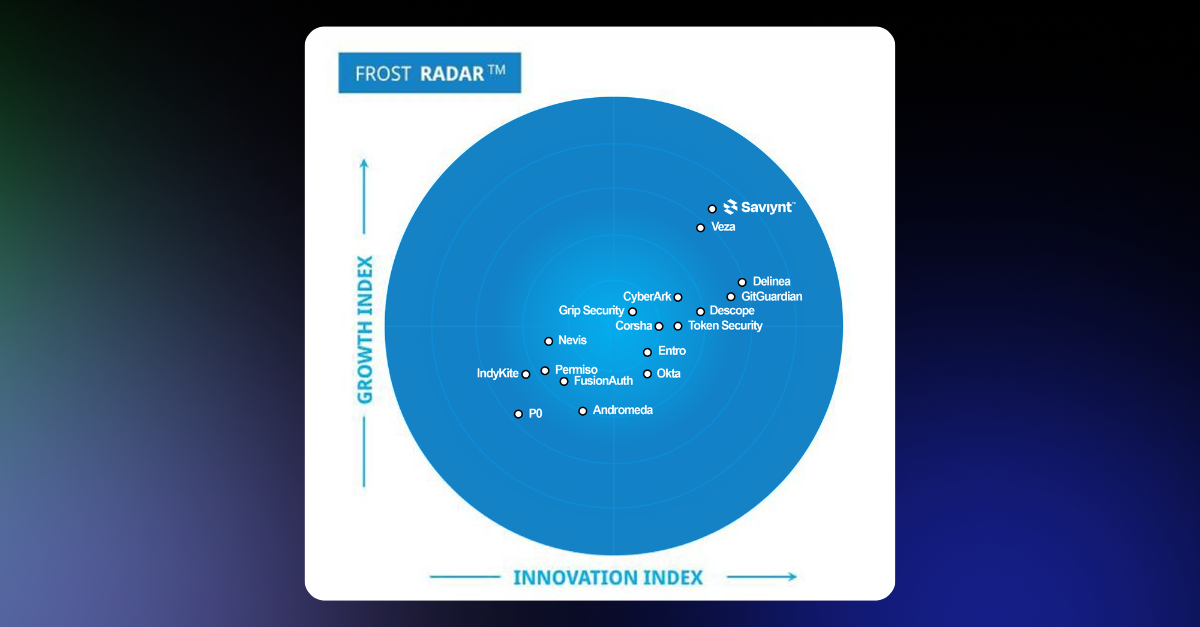
Saviynt Recognized as a Leader in Frost Radar™: Non-Human Identity Solutions, 2025
READ BLOG


11 / 11 / 2025
Savitalk Episode 5: Identity Security at a Crossroads with Jim McDonald and Jeff Steadman
READ BLOG
10 / 29 / 2025
Non-Human Identities Are the New Attack Surface: How Saviynt Brings Visibility and Governance for NHIs
READ BLOG
10 / 27 / 2025
Infrastructure as Code Meets Identity Governance: The Saviynt Terraform Advantage
READ BLOG


10 / 16 / 2025
Saviynt Named a Challenger in the 2025 Gartner® Magic Quadrant™ for Privileged Access Management
READ BLOG




09 / 22 / 2025
Governing Mission-Critical Access: Saviynt is Writing a New Chapter in Airline Identity Security
READ BLOG
09 / 17 / 2025
Eliminating Blind Spots: How Integrated Endpoint Protection and Identity Security Stop Modern Threats
READ BLOG
09 / 08 / 2025
SaviTalk Ep. 4: When AI Speaks Human: The Future of Identity Security with IBM’s Mike Amadei
READ BLOG


08 / 14 / 2025
Saviynt’s Commitment to Customers Shines Through in Latest Platform Updates
READ BLOG
08 / 08 / 2025
SaviTalk Ep. 3: Visionary Product Leadership, The Story Behind Saviynt ISPM With Vibhuti Sinha
READ BLOG

07 / 16 / 2025
Saviynt joins AWS AI Agent Marketplace as Launch Partner with New MCP Server Available Today
READ BLOG


07 / 04 / 2025
SaviTalk Ep. 2: Rewriting the Rules of Identity Security with Ian Glazer and Richard Bird
READ BLOG

06 / 18 / 2025
Saviynt Brings Innovation and Expertise to Identiverse 2025: Leading Identity
READ BLOG
06 / 13 / 2025
SaviTalk Ep. 1: Turning Obsession Into Innovation – Saviynt CEO Sachin Nayyar’s Identity Security Story
READ BLOG
06 / 11 / 2025
Saviynt ChangeMakers: How the University of Ottawa Integrated Digital and Physical Access Control Systems—A First in Higher Ed
READ BLOG
06 / 04 / 2025
Meet Saviynt at AWS re:Inforce 2025: Your Identity Security Partner for AWS and Beyond
READ BLOG


05 / 28 / 2025
5 Ways to Solve Compliance Challenges with Saviynt’s Identity Security Platform
READ BLOG


%20Certification_1242x828.jpg)
05 / 01 / 2025
From Talent Shortage to Talent Surge: Introducing Identity Security for the AI Age (ISAA) Certification
READ BLOG


04 / 17 / 2025
A Movement for Identity Security Transformation: Introducing Saviynt ChangeMakers
READ BLOG

04 / 07 / 2025
Introducing Enhanced Governance for Entra ID Service Principals: Now Generally Available!
READ BLOG
03 / 24 / 2025
Identity Security in the Age of AI: Why Modernizing IAM Is a Business Imperative
READ BLOG
03 / 19 / 2025
ICAM as an Essential Mission Enabler: Securing Federal Operations While Optimizing Budgets
READ BLOG
03 / 18 / 2025
Behind the Scenes of an Identity Security Transformation: Our Journey with LIXIL
READ BLOG
03 / 12 / 2025
Navigating Existential Identity: Join Saviynt at Identity Management Day 2025
READ BLOG
03 / 06 / 2025
External Identity Management: New Capabilities to Improve Visibility and Control
READ BLOG






02 / 06 / 2025
Saviynt Celebrates 2024 Global Partner Award Winners for Transforming Identity Security and Driving Customer Success
READ BLOG
02 / 03 / 2025
A New Era for ICAM – Addressing Federal Challenges with Accenture Federal Services and Saviynt
READ BLOG



01 / 08 / 2025
Saviynt Recognized as Gartner® Peer Insights™ Customers' Choice in Identity Governance and Administration—Four Years in a Row
READ BLOG
12 / 17 / 2024
Innovate, Build, Share: Discover the Saviynt Exchange Open Developer Ecosystem
READ BLOG
12 / 02 / 2024
Saviynt named a leader in KuppingerCole’s Identity and Access Governance Leadership Compass
READ BLOG
11 / 20 / 2024
Separation of Duties: What it means for your business and how Saviynt can help
READ BLOG
11 / 13 / 2024
Breaking Free from SAP GRC: Modern Solutions for Application Access Challenges
READ BLOG

10 / 30 / 2024
Don’t Neglect Your Applications: The Increasing Importance of Application Access Governance
READ BLOG




09 / 26 / 2024
Building Saviynt Intelligence: the World’s Best Access Recommendation Engine
READ BLOG


_1242x828.jpg)





06 / 11 / 2024
Manage Complete Identity Lifecycle and Eliminate Unused Access throughout AWS Environments
READ BLOG


05 / 28 / 2024
Leaving Legacy Challenges Behind – The Triumph of Converged Identity Platforms
READ BLOG

05 / 15 / 2024
Why Henrique Teixeira Joined Saviynt | The IGA Problem, The Technology, The People
READ BLOG






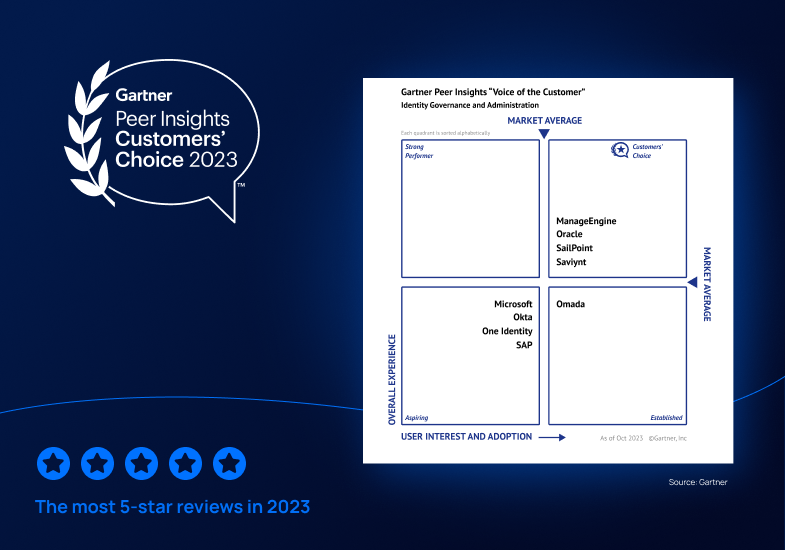
12 / 20 / 2023
Saviynt a Gartner® Peer Insights™ Customers' Choice in Identity Governance and Administration—Three Years in a Row
READ BLOG




























04 / 17 / 2023
Choosing a Cloud Privileged Access Management (PAM) Solution?: Three Must-Ask Questions
READ BLOG













01 / 05 / 2023
Saviynt Recognized as a 2022 Gartner® Peer Insights™ Customers’ Choice in Identity Governance and Administration
READ BLOG



12 / 13 / 2022
Saviynt EIC Scores 95/100 for Core Criteria in the 2022 Gartner® Solution Comparison for Identity Governance and Administration¹
READ BLOG





10 / 13 / 2022
New EIC v2022 Enhancements Boost Speed & Efficiency in Application Onboarding
READ BLOG










08 / 17 / 2022
3 Key IGA Modernization Must-Haves: All the Features, None of the Compromise
READ BLOG







07 / 06 / 2022
Top Challenges to Achieving Enterprise-Wide Visibility of Privileged Access
READ BLOG





06 / 09 / 2022
Gain Peace of Mind with Emergency Access Management & Out-of-the-Box Compliance Reporting
READ BLOG
06 / 02 / 2022
Solve Compliance Headaches with Cross-App Reporting and Automated Certification
READ BLOG

05 / 26 / 2022
Stop Remediation Burnout With Fine-Grained Controls and Out-of-the-Box Rulesets
READ BLOG










03 / 22 / 2022
Ask the Experts: Solving Top Multi-Cloud Identity Management & Governance Challenges
READ BLOG




11 / 19 / 2021
Getting GRC Right: Three Steps to Achieving Application Access Governance Maturity
READ BLOG
11 / 15 / 2021
Enterprise Identity Cloud: Accelerate Your Zero-Trust Journey with New Microsoft Integrations
READ BLOG












































03 / 29 / 2019
NIST 800-53 Identity and Access Management (IAM) Compliance via Saviynt’s FedRAMP ATO
READ BLOG

09 / 19 / 2017
Identity and Access Intelligence: Infusing Analytics & Intelligence to Improve Identity Governance
READ BLOG