.png?noresize&width=148&height=84&name=Untitled%20design%20(83).png)
Protect non-human identities from Day 1 with Saviynt Identity Cloud. Gain full visibility, contextual insights, and risk-based evaluation for non-human identities, just as you do for human identities without any additional integration effort. Secure all identities comprehensively and seamlessly throughout a single, unified identity security platform.
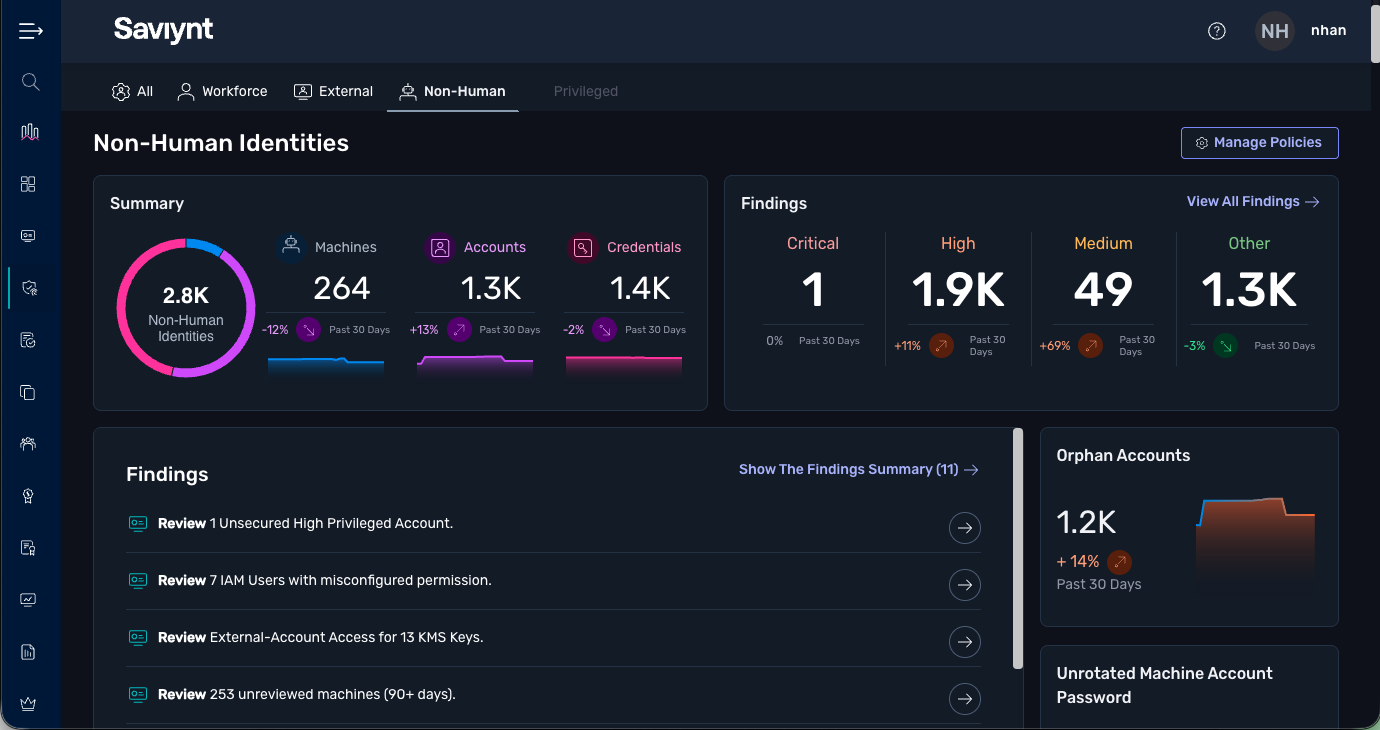
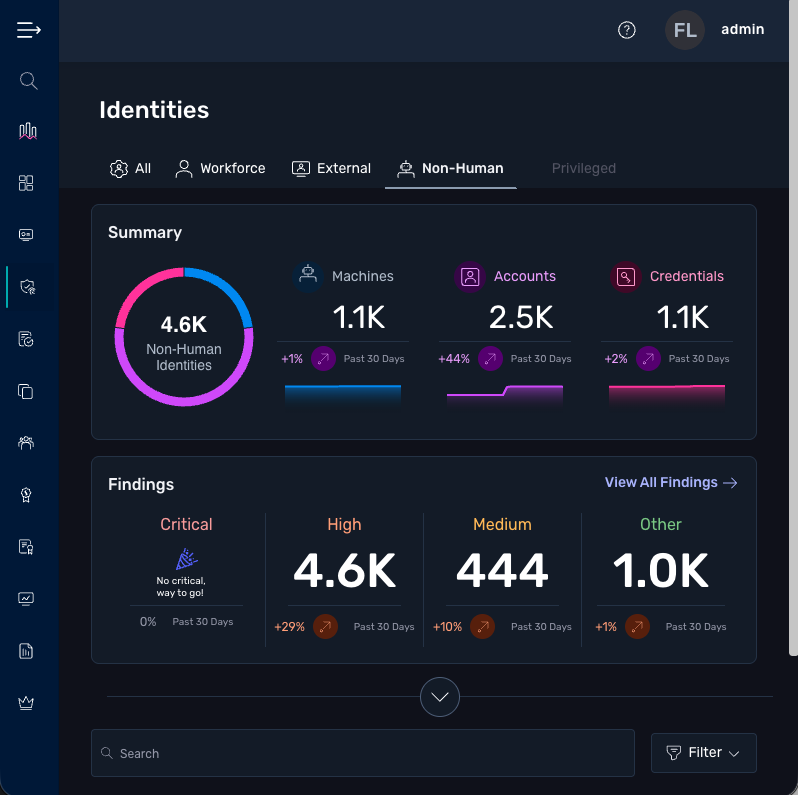
Get a comprehensive, real-time inventory of your non-human identity landscape.
NHI dashboard
Automatically discover all workloads, accounts, and credentials across your environments.
Unified NHI policy view
Gain complete visibility into all NHI policies, including violations, status, and severity, in a unified view.
View personalization
Customize your view with flexible filters, sort by identity type, ownership, risk level, and more.
Learn how AI-powered identity security platforms can become the cornerstone of a scalable, resilient, and future-ready cybersecurity strategy.

Proactively detect access risks and ensure audit-readiness for both human and non-human identities.
.jpg?noresize&width=327&height=177&name=ISPM%20Main%20Dashboard%20Squared%20(2).jpg)
.jpg?noresize&width=2119&height=1415&name=iStock-1299972215%20copy%20(1).jpg)

Non-human identities (NHI) are digital identities used to represent software workloads, robotic process automation (RPA), and other non-human actors within IT environments. They are not limited to machine identities — a common misconception — and include a broader range of identity types that interact with systems, data, and applications.
Key Components of Non-Human Identities: