Does your identity program work in the AI era?
New research from Cybersecurity Insiders and Saviynt reveals the real state of AI identity risk inside large enterprises, including unsanctioned AI tools, uncontrolled agent privileges, and the fastest-growing governance blind spot CISOs now face.

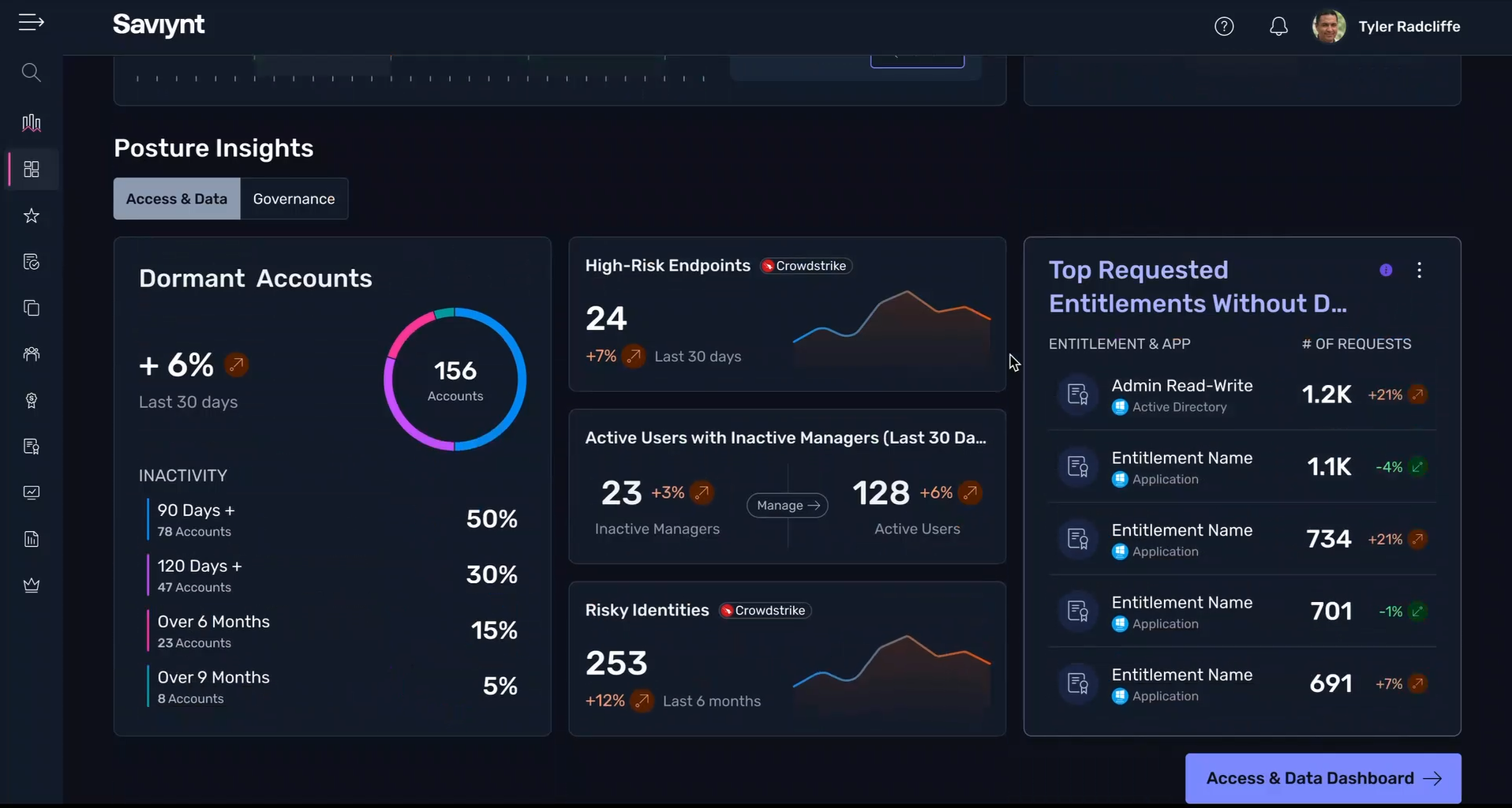
Identify everything within your organization — including all the identities (human and non-human), apps, secrets and systems you didn’t know about — now and as they’re added, no matter the makeup of your enterprise environment.