Content Hub
Research, advice, guides, and best practices from identity experts
Content Type
Content Type
- All Content Type
- eBook
- Analyst Report
- Whitepaper
- Data Sheet
- Case Study
- Solution Guide
- On-Demand Webinars
- Video
- Article
- get solution
- Blog
- Report
Industry
All Industry
- All Industry
- Energy
- Federal Government
- Financial Services
- Healthcare
- Higher Education
- Manufacturing
- State & Local Government
- Retail
Solutions
All Solutions
- All Solutions
- Application Access Governance
- The Saviynt Identity Platform
- Identity Governance & Administration
- Privileged Access Management
- External Identities & Risk Management
- non-human_identity

On-Demand Webinars
When AI Becomes an Identity: Rethinking Governance in the Age of AI Agents

On-Demand Webinars
Securing the Fastest-Growing Identity Surface: The Rise of NHIs and AI Agents
.png)






Analyst Report
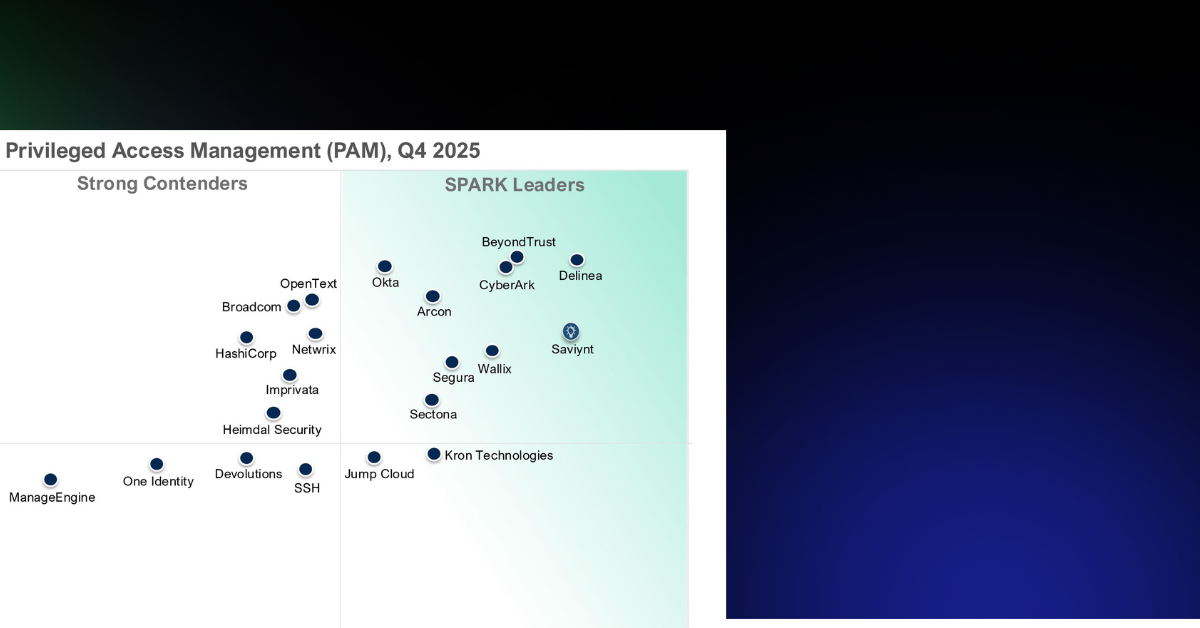
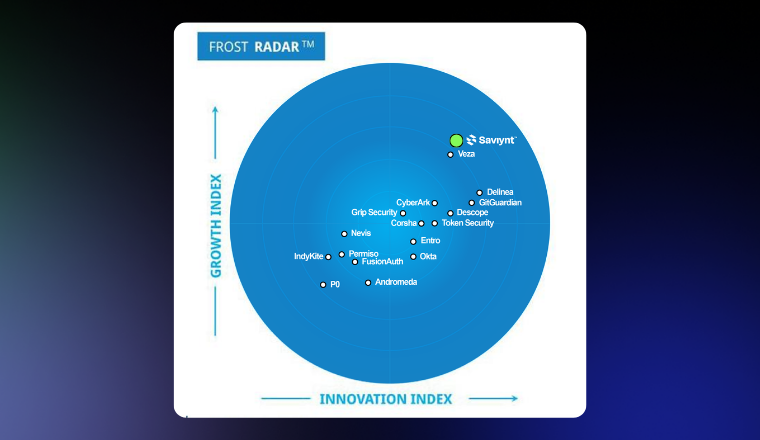
Saviynt Named a Challenger in the 2025 Gartner® Magic Quadrant™ for Privileged Access Management






On-Demand Webinars
Controlling the Unseen: Managing the Risk of Non-Human Identities in a Hyperconnected World


On-Demand Webinars
From Fragmented to Frictionless: AI-Driven Identity Security for AWS at Scale

On-Demand Webinars
Identity-Centric Security: Leveraging AI for Scalable, Future-Ready Programs

On-Demand Webinars
Identity-Centric Security: Leveraging AI for Scalable, Future-Ready Programs




Press Release
AWS Signs Strategic Collaboration Agreement With Saviynt to Advance AI-Driven Identity Security

Press Release
Saviynt announces availability of Saviynt MCP Server in the new AWS Marketplace AI Agents and Tools category




On-Demand Webinars
Beyond Legacy: Pathways to Complex Migrations & Minimizing Technical Debt


Blog
Saviynt joins AWS AI Agent Marketplace as Launch Partner with New MCP Server Available Today

Solution Guide
Identity Security Posture Management (ISPM) for Non-Human Identity

eBook
Many Identities, Unified Security: Converging Human and Non-Human Identity Management


On-Demand Webinars
From Siloed SAP to Centralized Enterprise Governance: A Practical Playbook





%20page_760x440.jpg)





Analyst Report
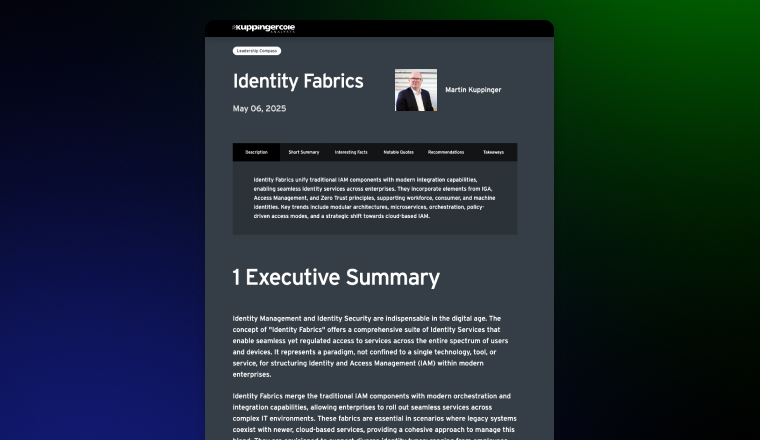
Saviynt named a Leader in KuppingerCole’s 2025 Identity Fabrics Leadership Compass


On-Demand Webinars
GE Healthcare’s Journey to Proactive Identity Security with Identity Security Posture Management (ISPM)











Video
Chalk Talk: The Science Behind Saviynt’s Identity Security Posture Management (ISPM)





Case Study
The University of Western Australia Finds Power and Simplicity in the Cloud

Analyst Report
Saviynt Named a Customers’ Choice in the Gartner® Peer Insights™ Voice of the Customer for IGA Report

On-Demand Webinars
Innovative IAM Strategies: New Tools and Guidance for Modern Identity Security

On-Demand Webinars
From Fragmented to Unified: Transforming IAM in the Age of Digital Complexity

On-Demand Webinars
Powering and Protecting the Extended Workforce with an Identity-Centric Approach



Analyst Report
Saviynt named a Leader in KuppingerCole’s 2024 Identity and Access Governance Compass Report




On-Demand Webinars
Transforming Access Management: Strategies for the New Digital Landscape

On-Demand Webinars
Unlocking the Promise of Productivity in Your Third Party Workforce
%20analyst%20report_760x440.jpg)
Analyst Report
Saviynt PAM is Recognized as a Value Leader by Analyst Enterprise Management Associates (EMA)


On-Demand Webinars
Analyst Webinar | The Need for Identity Intelligence: How Identity Proliferation is Changing Identity Security

%20analyst%20report_760x440.jpg)
Analyst Report
Saviynt included in the 2024 Gartner® Market Guide for Identity Governance and Administration (IGA)







Analyst Report
Saviynt Identity Cloud IGA Capabilities Recognized as Industry-Leading by KuppingerCole Analysts AG

On-Demand Webinars
How Unified IGA and PAM Can Protect Organizations from Ransomware and Other Identity-Based Threats

Video
Joiners, Movers, Leavers, and Failures: Why is Identity Management Still Struggling?








On-Demand Webinars
Navigating Identity Governance in Financial Services: Navy Federal Credit Union's Journey with Saviynt & Accenture



Case Study
Ingredion Replaces Legacy Solution with Flexible, Modern Cloud IGA Platform


























Case Study
Syneos Health Futureproofs Identity Governance for Flexibility and Rapid Growth













Analyst Report
Recognized By KuppingerCole Analysts As Leaders In The Access Control Market For SAP & Multi-Vendor LoB

Analyst Report
Recognized By KuppingerCole Analysts As Leaders In The Access Control Market For SAP

%20analyst%20report_760x440.jpg)
Analyst Report
Saviynt Cloud PAM is Recognized as Best Privileged Access Governance and Strong Value by Analyst Enterprise Management Associates® (EMA)

Analyst Report
Saviynt is named a Customers’ Choice in the 2023 Gartner® Peer Insights™ Voice of the Customer: IGA
%20modernization%20whitepaper_760x440.jpg)





















%20solution%20guide_760x440.jpg)





On-Demand Webinars
Identity, Credentialing, and Access Management (ICAM) and Executive Order 14028





On-Demand Webinars
Use Identity Convergence to Collaborate More Securely with External Partners

On-Demand Webinars
Modern Identity Governance & Administration for Mid-sized Organizations

On-Demand Webinars
Identity Security Converged: Expert Insights from Top International Brands










On-Demand Webinars