Related Resources:
Solution Guide: Replacing SAP GRC
Analysis Tool: Identity Security Impact Analysis
Webinar: Transforming Access Management: Strategies for the New Digital Landscape
SAP has announced several changes to their identity security lineup that has organizations around the world re-evaluating their identity security programs. In addition to the upcoming end of maintenance for SAP IDM, SAP has announced the end of maintenance for SAP GRC, including Access Control, while also moving their core platform from ECC to S/4HANA Cloud.
The days of organizations using a single GRC vendor for their critical applications have long passed. In the past, most had been able to standardize on one ERP system. The changing nature of how businesses interact with one another, combined with the rise of best-of-breed, cloud-based applications has compelled companies to adopt solutions from multiple vendors.
As this evolution has taken place, application security teams have encountered new challenges. Among them, siloed solutions, lack of risk visibility, and managing an increasing number of internal, external, and non-human identities.
With all of these changes, now is a good time to assess your access control and governance needs. Organizations may decide to keep SAP GRC, hang onto Access Control as long as possible, or find a more complete solution for an SAP GRC replacement.
Why Modernize Your Application Access Program
While powerful, SAP GRC provides a limited view of application and enterprise risk. Often, SAP security teams lack visibility into other connected applications and the identities that have access to them. The lack of integrated identity governance and fine-grained integration creates additional blind spots. Deficiencies occur around separation of duty (SoD) support, and limited role engineering and management, access certification capabilities, continuous controls monitoring, emergency access management and more. As a whole, they add up to significant gaps needed for strong application access governance in today’s business and regulatory climate.
SAP GRC actually reinforces silos due to the lack of cross-application support. Siloed solutions need increased customization to support cross-application security needs, leading to more complexity and increased costs.
Filling in SAP’s Access Security Gaps
Saviynt Application Access Governance (AAG) is recognized by the analyst community as an industry leader in access governance, not only for SAP environments but for supporting non-SAP applications such as Oracle, Salesforce, Workday, etc. The Identity Cloud from Saviynt can actually support any application with fine-grained integrations that allow you to consolidate your view of enterprise risk.
Saviynt unifies enterprise resource planning (ERP) and Line of Business (LoB) application security models under a single umbrella to standardize controls across your environment. This allows you to align security policies across applications, devices, and operating platforms for simplified management that identifies and remediates risks and anomalous activities more effectively.
Saviynt’s deep integrations with ERP, enterprise health records (EHR), and other critical applications provide increased levels of risk detection. With The Identity Cloud, you can proactively assess access requests and prevent cross-application risks before they occur. You can also quickly identify and understand potential and actual risks across all applications with out-of-the-box rulesets and controls that promptly see and alert on toxic conflicts.
Continuously Monitor Access and Activity
The number of regulations organizations need to adhere to, especially in highly regulated industries such as financial services and healthcare, makes it difficult to maintain ongoing compliance. Simply knowing who and what has access to applications and critical information and controlling that access, as SAP GRC does, doesn’t help identify how those identities are using that access.
Saviynt not only monitors who has access but quickly alerts administrators to access and activity irregularities. Saviynt logs all changes to create an end-to-end audit trail with report creation that allows administrators to slash data analysis times while also mitigating risks and building trust with internal/external auditors.
Enable Emergency Access Management, Eliminate Standing Privileges with Just-in-Time Access
Grant users elevated privileges for a limited time and leverage automated session monitoring to provision, record, and de-provision privileged sessions. Session reporting lets you continuously monitor access and supports documentation and audit preparation. And having start and end times and dates for access helps eliminate the potential for orphaned accounts once the need for the access expires.
Save Big by Eliminating Unnecessary Licensing Costs
Paying too much for unused and overprovisioned access is an ongoing issue that can be hard to fix. Saviynt provides a clear picture of what existing access is being used and who has access that shouldn’t. Saviynt’s Intelligent Recommendations capabilities also provides highly accurate recommendations so that unnecessary access isn’t given in the first place, significantly reducing the amount of money spent on unneeded license costs by eliminating excessive and unused access.
Benefits of Using The Identity Cloud for AAG
- Cross Application Risk Visibility and Segregation of Duties Management
- Role and Attribute-based Access Control
- Continuous Controls Monitoring
- Reduced License Costs
- Automated Role Engineering
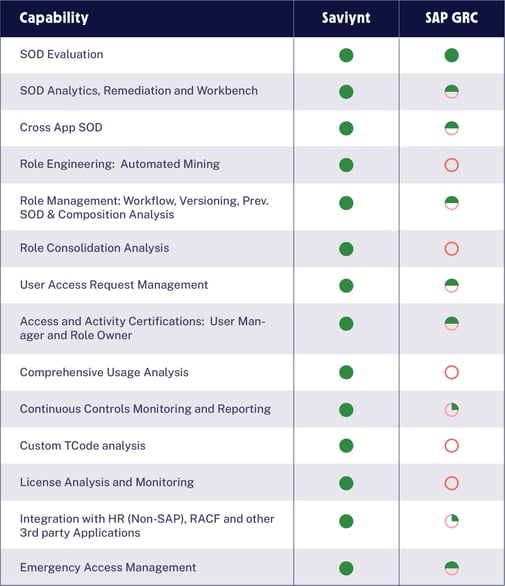
The comparison chart below provides a high-level look at where Saviynt’s AAG capabilities can enhance SAP GRC and Access Governance. Additionally, Saviynt can be used as an SAP GRC replacement to provide a complete and holistic solution.
Saviynt vs. SAP GRC
Learn More
If you have any questions about your existing SAP GRC implementation or want to learn more about how Saviynt can support modernizing your application access program, please reach out to us. You can also take our Application Security Assessment to gauge how well your existing program is going.








