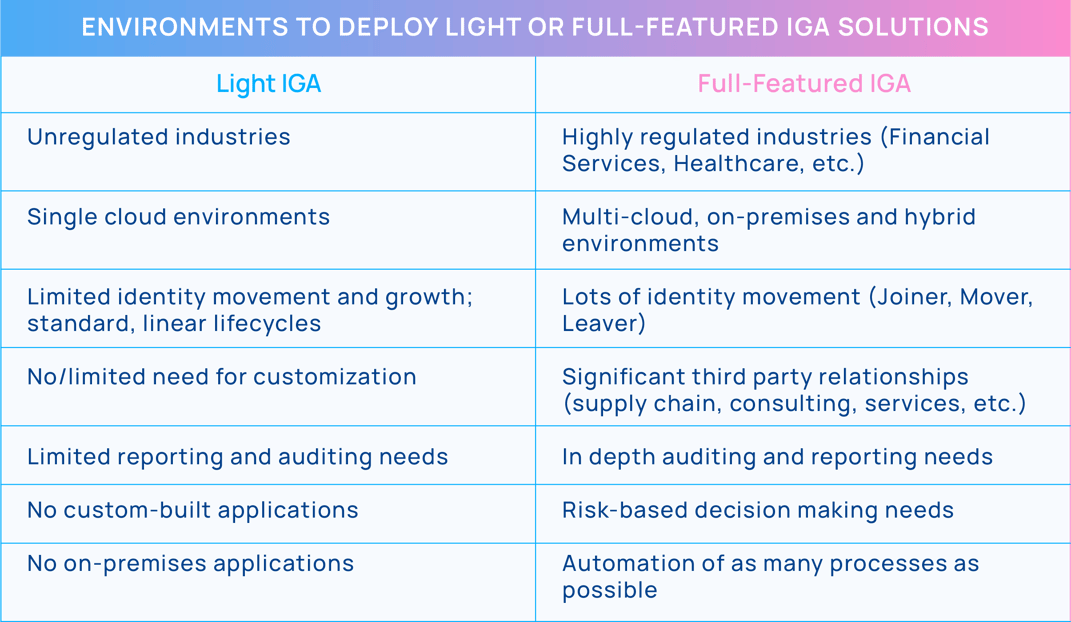
Characteristics of Light IGA Solutions
Light solutions are more likely to be able to only support identities in a single cloud and generally can’t manage on-premises or custom-built applications and the identities associated with them. Additionally, light solutions often lack coverage for applications in multi-cloud and hybrid environments.
While light solutions may have some automation capabilities, they don’t provide full automation, which means administrators and support teams may still have to rely on manual processes for routine tasks, increasing to additional management needs. These tasks could include, but are not limited to, access requests, certification campaigns, provisioning, etc. Like most IGA solutions, there will be reporting and auditing capabilities, but the usability of this information may be limited and not actionable related to validating continuous compliance.
The lack of features and functionality, if not researched properly, could mean the purchase and integration of additional point products to meet outlying needs, contributing to increased management, training, professional services, and more, leaving organizations right where they started: with an IT and security stack built with point solutions that costs more, is difficult to manage, and doesn’t shrink the threat landscape.








.jpg)