Privileged Access Management Reimagined
An Integrated Cloud PAM Solution Offers Easy Integrations & Solves Multi-Cloud Challenges
Any publicity is good publicity, or so the saying goes. And security breaches are big news. Yet, security breaches lead to data exposure, and that’s not the kind of publicity any company wants. Sure, the economic impact can be tough to stomach, but more importantly, it causes irreparable damage to your brand and customers’ trust. That doesn’t even account for the expense of eDiscovery, legal fees, and the notification costs.
The ephemeral nature of the cloud and the broad range of deployments — including hybrid, multi-cloud IT, and “shadow IT” setups — make securing enterprise resources challenging. Limited visibility of privileged access across infrastructure and applications only amplifies things. This lack of visibility coupled with the complex relationships between entitlements allows excessive privileges to go unnoticed. With each addition of a new resource or service, there is a chance that over-permissioning will occur.
According to an IDC survey of CISOs in the US, 80% of respondents can’t identify excessive access to sensitive data in cloud production environments. Two of the top three threats identified were lack of adequate visibility and permission errors. It’s virtually impossible to fix the unknown. Unless organizations can detect these misconfigurations and related vulnerability gaps, it’s hard to remediate them, let alone apply automated, policy-based preventative controls.
An integrated approach to privileged access management should weave together visibility, governance, and security into a single platform. An integrated Cloud PAM solution allows organizations to achieve frictionless identity and resource onboarding, as well as automated detection and remediation of misconfigured digital assets. Zero-Trust principles, applied to privileged access through an integrated, identity-led approach, provide organizations with a robust framework to improve their overall security posture.

Visibility drives access governance to improve overall security posture
Legacy PAM Falls Short
We’ve heard from our customers that the traditional vendor approach to Privileged Access Management (PAM) doesn’t scale with the current needs of a growing enterprise. Existing solutions lack holistic oversight and require expensive deployment and operational costs. And combined with ever-expanding DevOps pipelines and SaaS adoption, legacy solutions quickly start to lose their overall value. Organizations need a solution that allows them to keep pace with business agility, and simultaneously balance the security needs of an ever-changing business environment.
Silos Emerge and Visibility Suffers
Inherently, PAM tools are limited to traditional privileged user access capabilities; they lack a depth of visibility into privileges and access governance across managed resources. Organizations often choose disparate platforms for cloud security services, access management, privileged user access, and comprehensive governance capabilities. This leads to disjointed access management processes and inconsistent implementation of infosec policies. The inherent complexity and inconsistency that comes with this approach weaken an organization’s overall security posture.
Complicated Deployments Increase TCO
Legacy PAM isn’t able to keep up with cloud deployment architectures that are based on high availability, scalability, security, and business requirements. They are suited towards more static environments and do not have the flexibility to automatically identify changes in assets and resources as they get created or destroyed. Manually replicating this effort can waste significant staff hours, translating to additional costs and an overall higher total cost of ownership.
Read 5 Reasons Lifting-and-Shifting Legacy PAM to the Cloud Doesn’t Work to learn more about the insufficiency of legacy PAM tools for securing cloud resources.
Unmanaged Access Introduces Unnecessary Risk
Privileged access sprawl is on the rise. This stems from increased IaaS and SaaS adoption by IT and other departments running shadow IT. Business units are continuously expanding their SaaS application use to meet customer demands. Often, these apps bypass IT processes and InfoSec governance controls. Infrastructure is dynamic, with workloads spun-up and terminated on an ad-hoc basis.
The rapid transformation in organizations’ operating models increases the challenges that today’s security and compliance teams face. Traditional PAM tools can’t provide the visibility and governance at the scale needed to prevent privilege creep and reduce organizations’ overall risk.
Introducing a New Approach to PAM

Manage privileged access to any kind of identity for any kind of digital asset to improve security using Saviynt Enterprise Identity Cloud
Last year, Saviynt introduced a new kind of PAM solution within our Enterprise Identity Cloud (EIC). It’s cloud-native, secure (FedRAMP certified), and utilizes a converged platform to deliver Identity Governance and Administration (IGA) plus Privileged Access Management services. EIC forms the foundation for organizations implementing Zero-Trust architecture by enabling visibility, management, and privileged access monitoring. Augmenting this with just-in-time (JIT) provisioning of accounts with Zero Standing Privileges that are time-bound — and automatically revoked — reduces organizational risk.
Saviynt Enterprise Identity Cloud consistently applies governance, compliance, and security rules throughout the cloud and on-prem ecosystem. This is important when providing evidence and demonstrating continuous compliance in the audit process.
The intuitive, wizard-based onboarding interface makes application integration easy and efficient. Cloud service integration is accelerated through auto-discovery and rapid enrollment of cloud workloads which helps companies securely ramp up in the cloud.
Oversight of full identity lifecycle with access governance, Segregation of Duties (SoD) risk evaluation, privileged access management, and risk-based access certification is centralized in a single platform. Such centralization creates a consistent user experience for all personas through a single-pane-of-glass interface. This reduces the strain of splitting focus between multiple point solution interfaces, increasing effectiveness and saving time.
CIEM Comes Out of the Box
According to Gartner, Cloud Infrastructure Entitlement Management (CIEM) is a specialized identity-centric SaaS solution focusing on managing cloud access risk using time-limited access controls.
Saviynt’s integrated approach creates a comprehensive solution for cloud security by merging IGA, CPAM, and CIEM. Not only does it provide visibility and privileged access management, but it also includes:
- Automated Entitlement Discovery
- Entitlement Relationship Visibility
- Policy-Driven Management of Privileges
- Just-in-Time Access Provisioning With Automated Revocation
- Monitoring and Reporting of Privileged Access Usage
- Remediation of Excessive Privileges
Instead of relying on point solutions, customers get a single platform to improve their cloud security and compliance posture continuously. Customers like Equifax have reduced their risk footprint by enabling Saviynt CPAM capabilities in as little as three months and quickly benefit from the results.
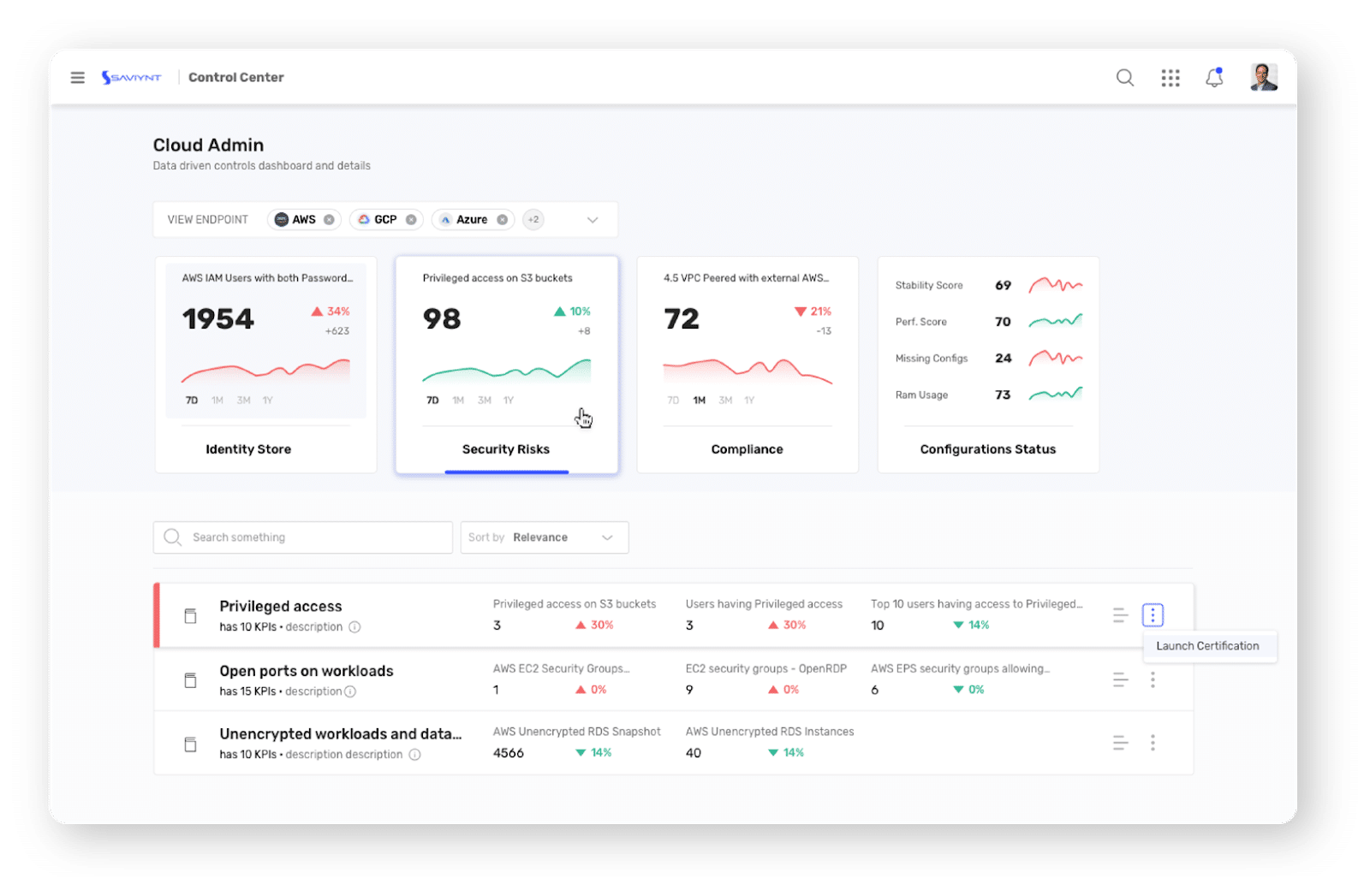
The Cloud Administration Dashboard offers a comprehensive set of KPIs drive platform analytics that are made available in a user-friendly dashboard
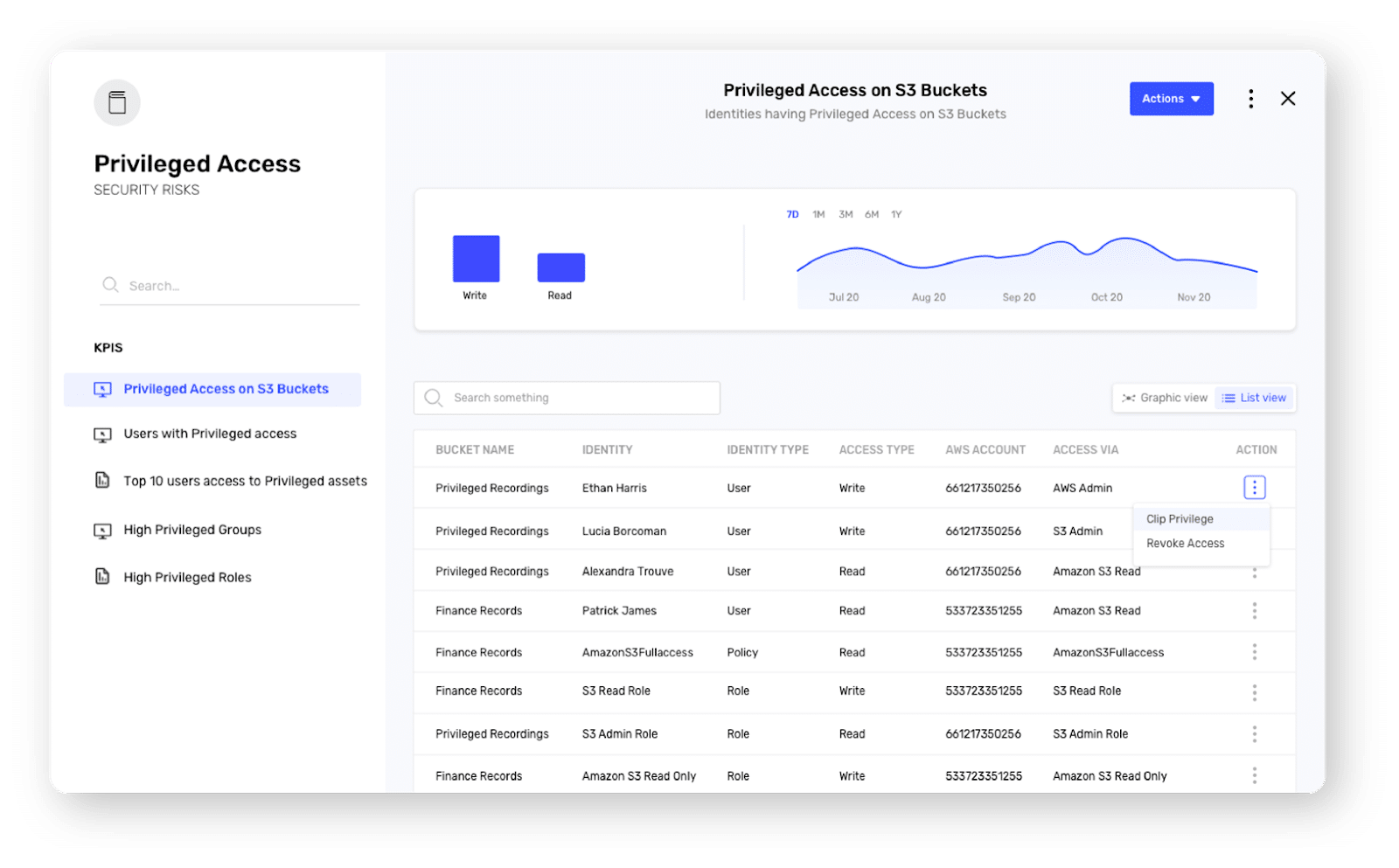
Privileged Access Management
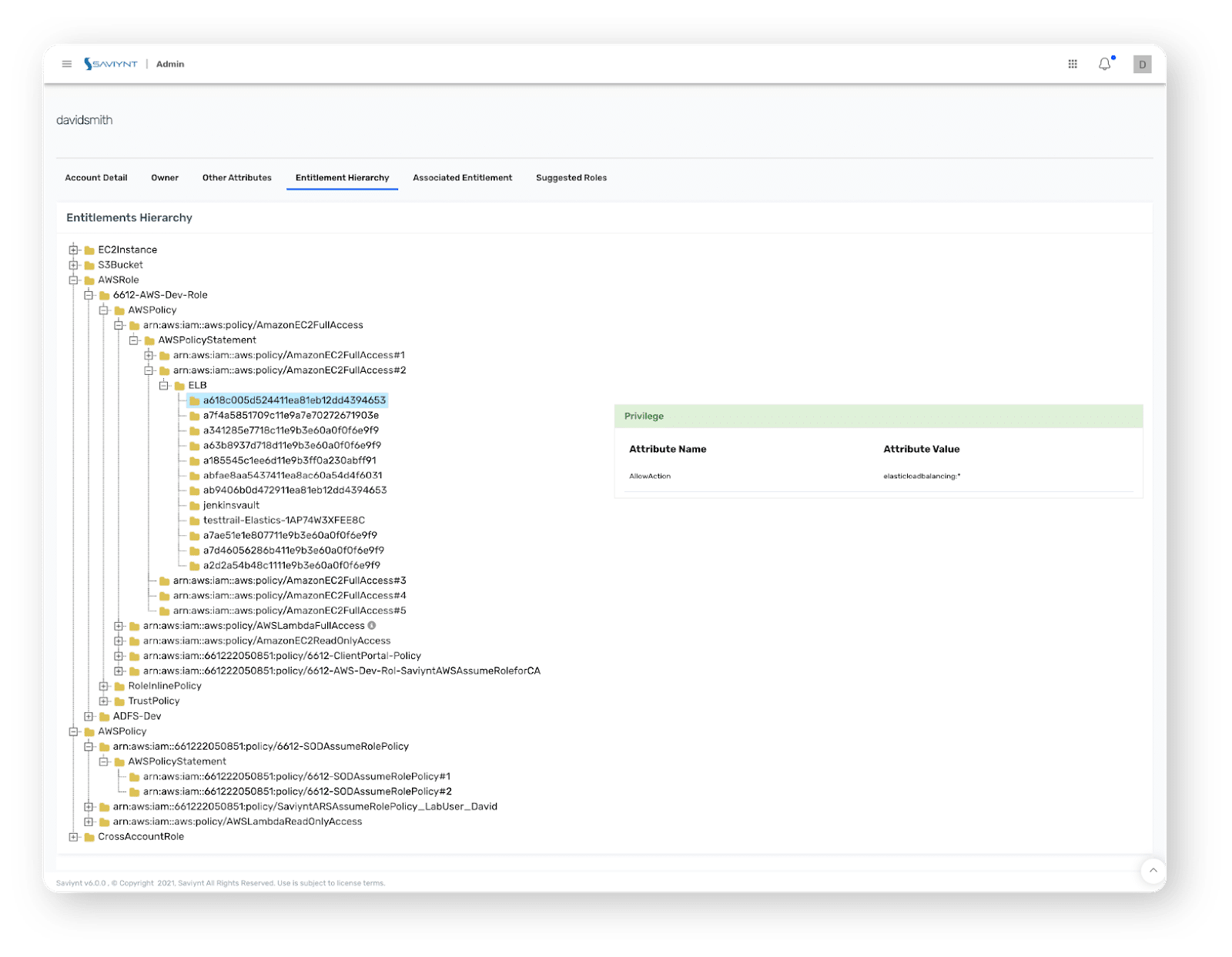
Saviynt provides an easy to view complex permission model of your cloud infrastructure as shown in images 1-3 above.
Zero-Touch Jump Box Solution and Frictionless Experience
Traditional PAM tools rely on jump boxes through which end users access resources. This leads to increased maintenance and operational overhead and creates a disjointed experience without any risk reduction.
Saviynt’s cloud privileged access management solution eliminates the need for any jump boxes. This allows customers to get their PAM implementation up and running faster. There is no need to maintain additional systems for PAM end-users to access the protected resources and applications.
After authorization, end users can quickly and easily access their sessions through a button click in the browser. Every action taken is monitored, recorded, and, when necessary, replayed. The system can proactively flag any anomalous activities and escalate them to the designated administrator.
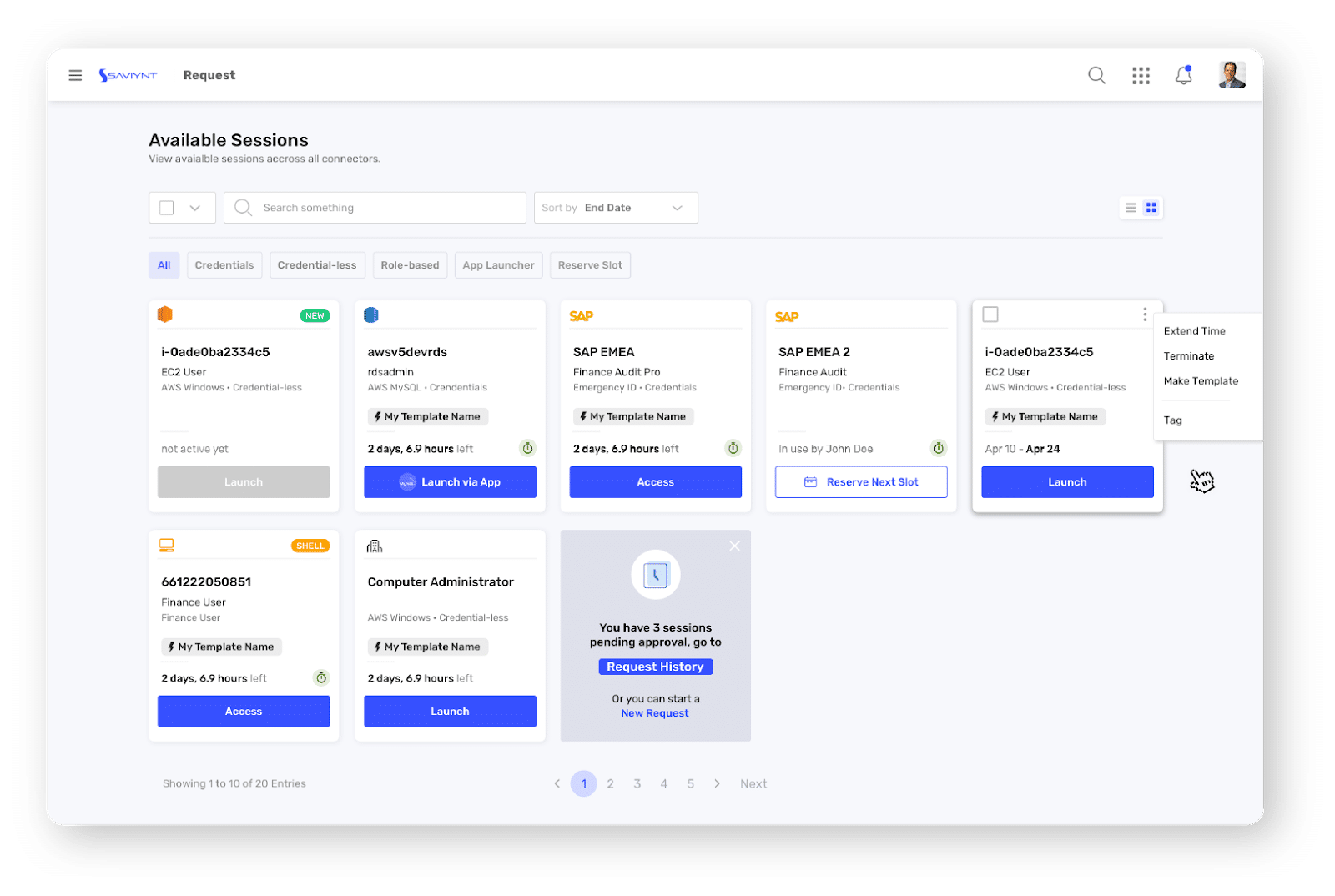
Session Launch by End User
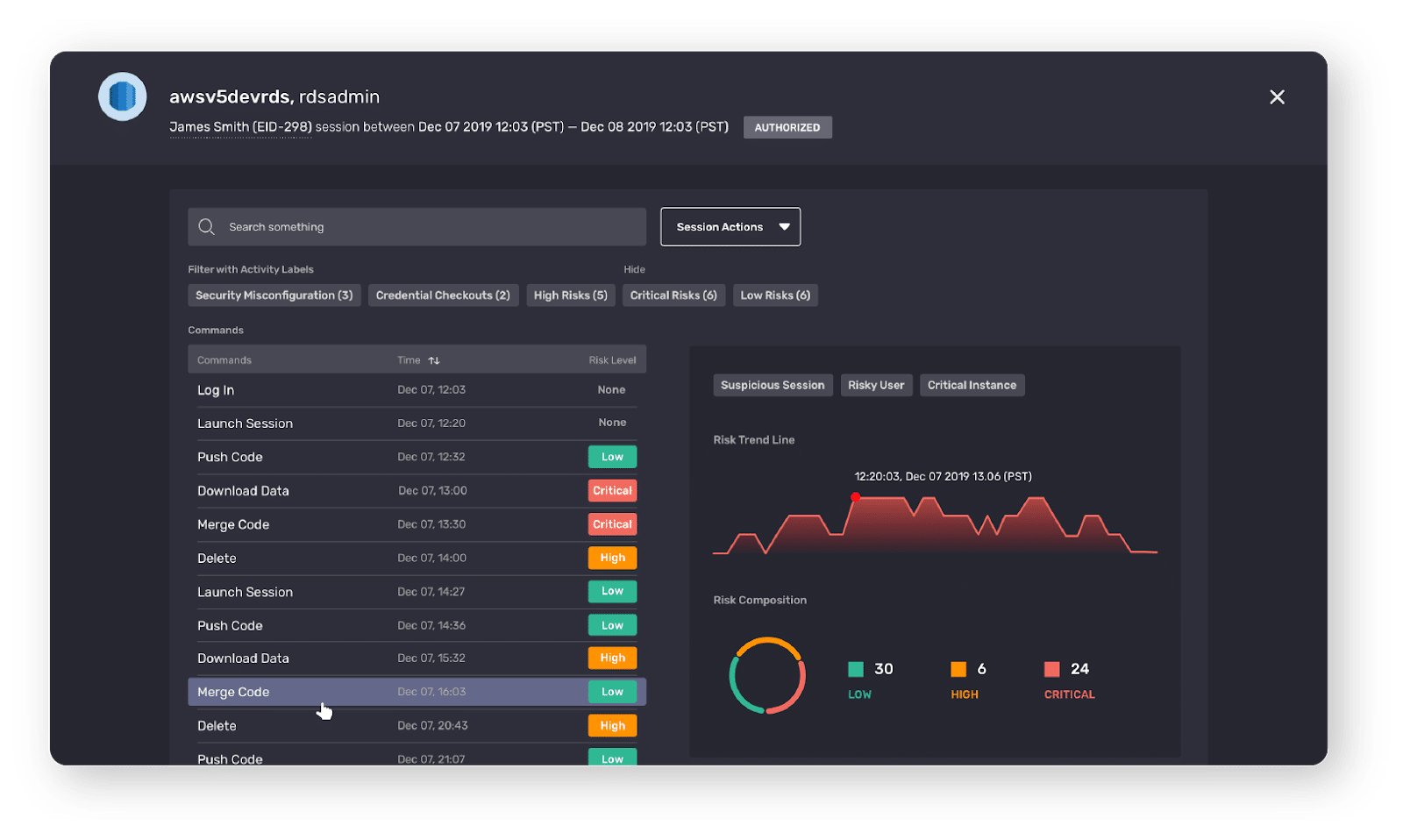
PAM Administrator View
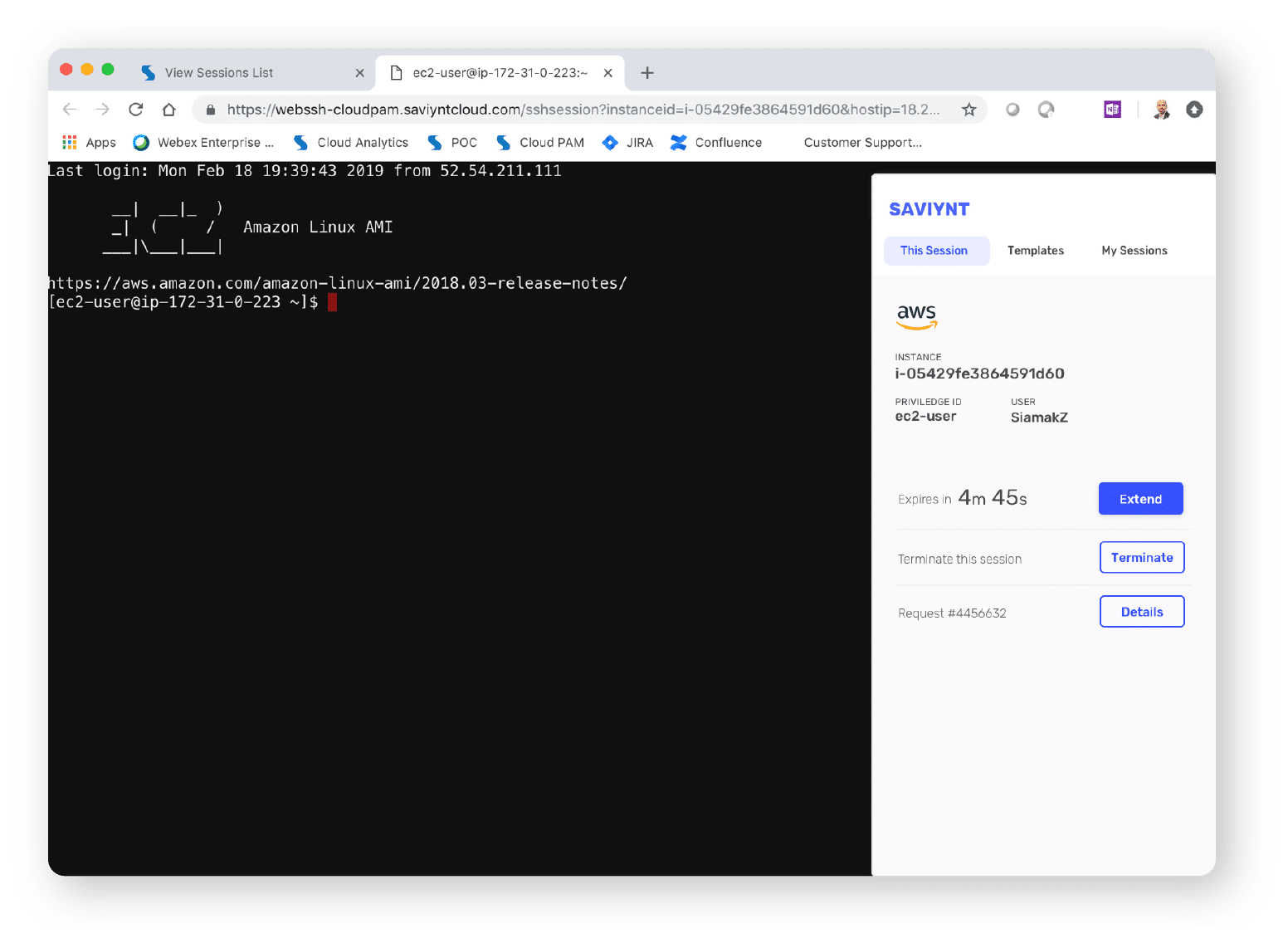
After Launch
Check out our on-demand webinar, Securing Your Remote Workforce, to learn more about how an identity-based perimeter will help you meet today’s security challenges.
Complete Lifecycle of Service and Privileged Accounts
Most PAM solutions focus on how users and applications check-out the privileged and service accounts’ credentials, ignoring the creation and governance of the service accounts themselves.
Saviynt is the only PAM solution built on top of an integrated IGA product. This means enterprises can ensure the entire lifecycle of service and privileged accounts in a single solution, including:
- Ownership and Workflows for Creation, Updating, and Decommissioning
- Enforce Naming Standards and Controls to Prevent Sprawl of Service Accounts
- Manage Authorizations for Check-Out of Credentials
- Prevent Out of Band Creation of Any Service Accounts
- Succession Management
- Scheduled and Risk-Based Access Reviews
Additionally, you can also manage the credentials and check-out process as part of Saviynt’s overall PAM solution.

Saviynt's comprehensive CPAM and IGA platform provides much more than what traditional PAM tool can deliver
Going to the Next Level
Ensuring security in the cloud relies on the visibility that your security tools can deliver. By bringing together multiple data streams related to access and usage, valuable insights can be derived and leveraged. Implementing comprehensive risk-based strategies using this data ensures that the right people get access to the data they need at the correct times, no matter where the resources reside.
Learn more about how Saviynt’s Cloud Privileged Access Management Solution is addressing the challenges of the modern cloud era.
Related Post

02 / 20 / 2026
Bridging Cloud and Identity Security: Saviynt and Wiz Redefine Cloud Identity Security
READ BLOG
.jpg)

Report
Saviynt Named Gartner Voice of the Customer for IGA

EBook
Welcoming the Age of Intelligent Identity Security

Press Release
AWS Signs Strategic Collaboration Agreement With Saviynt to Advance AI-Driven Identity Security

Solution Guide