PAM tools originated back in the days when human administrators were working primarily in on-premises infrastructure. Since then, cloud infrastructures, remote work, and an avalanche of machine identities have outstripped the capabilities of traditional tools. Adopting best practices has become infinitely more challenging.
So where does that leave organizations and their PAM deployments? How should leaders move beyond the basics (think: vaulting) and reduce their privileged attack surface?
Look no further than Saviynt. With our pioneering approach to identity-driven PAM delivered on our converged Enterprise Identity Cloud (EIC), we have created a number of educational resources to help customers modernize their approach to PAM and improve security. No matter where you are on your PAM journey—assessing your current state, acquiring new solution capabilities, or activating modern capabilities, like just-in-time privileged access—we have a resource for you.
Phase 1: Assessing Cloud PAM Maturity
Identify strengths and gaps in your cloud PAM program with a modern maturity model designed to help you assess your current PAM program capabilities and future needs. It’s estimated that 80% of data breaches involve privilege misuse or compromise. Traditional, siloed identity tools were not built to deliver the scale and flexibility needed to match the pace and dynamic nature of cloud workloads.
To keep pace, organizations need to take their defensive strategies to where the battle is—in the cloud. It’s time to redefine what success looks like with a new PAM maturity model.
Our white paper, “Privileged Access Management Maturity in the Cloud – A Framework for PAM Success,” will help you better align your PAM programs to security goals and identify gaps in their identity tool suite. Saviynt’s cloud PAM maturity model can serve as your roadmap to achieving just-in-time enabled zero standing privilege (ZSP) across your entire ecosystem, including multi-cloud, SaaS, and IaaS.
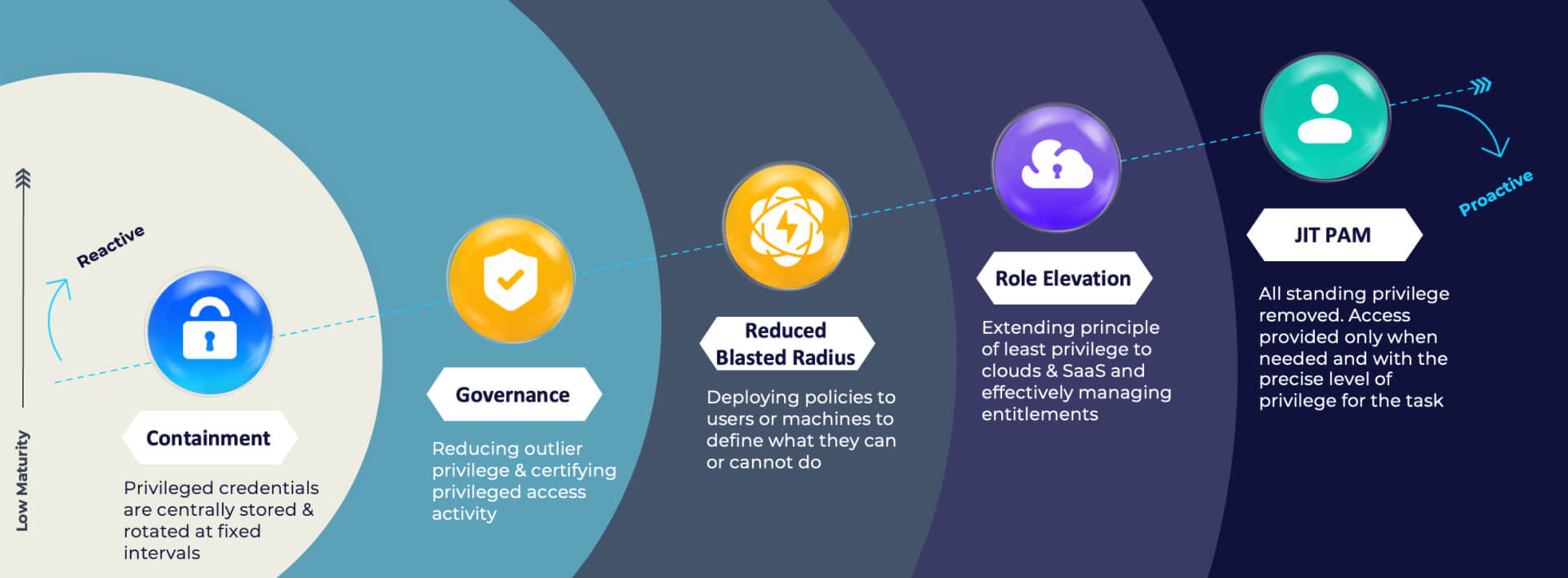
Find out the maturity level of your identity security
Take this one-minute assessment and get some insights on strengths and potential gaps in your cloud PAM program.
Phase 2: Acquiring a Modern PAM Solution: Requirements That Matter
Once you know where you are on the cloud PAM journey and where you need to be, you need to find the best vehicle to get you there. To that end, Saviynt created the “Cloud PAM Buyer’s Guide: A No-Fuss, Non-Salesy Tour of What Matters Most.”
The PAM market is mature and crowded with legacy providers as well as new entrants. You can find solutions with all the bells and whistles you may ever want. There are also point products which can provide some functionality but may not deliver real risk reduction. Saviynt’s Cloud PAM Buyer’s Guide will help you zero in on the most important success factors to help you get the most value out of your investment.

Tip: start with minimally disruptive solutions that will help you reduce complexity and unify siloed IAM tools. In the planning stages, interview a wide variety of PAM stakeholders to understand their relationships with risk. After all, a modern PAM program needs to move past operations and governance to deliver real risk reduction benefits.
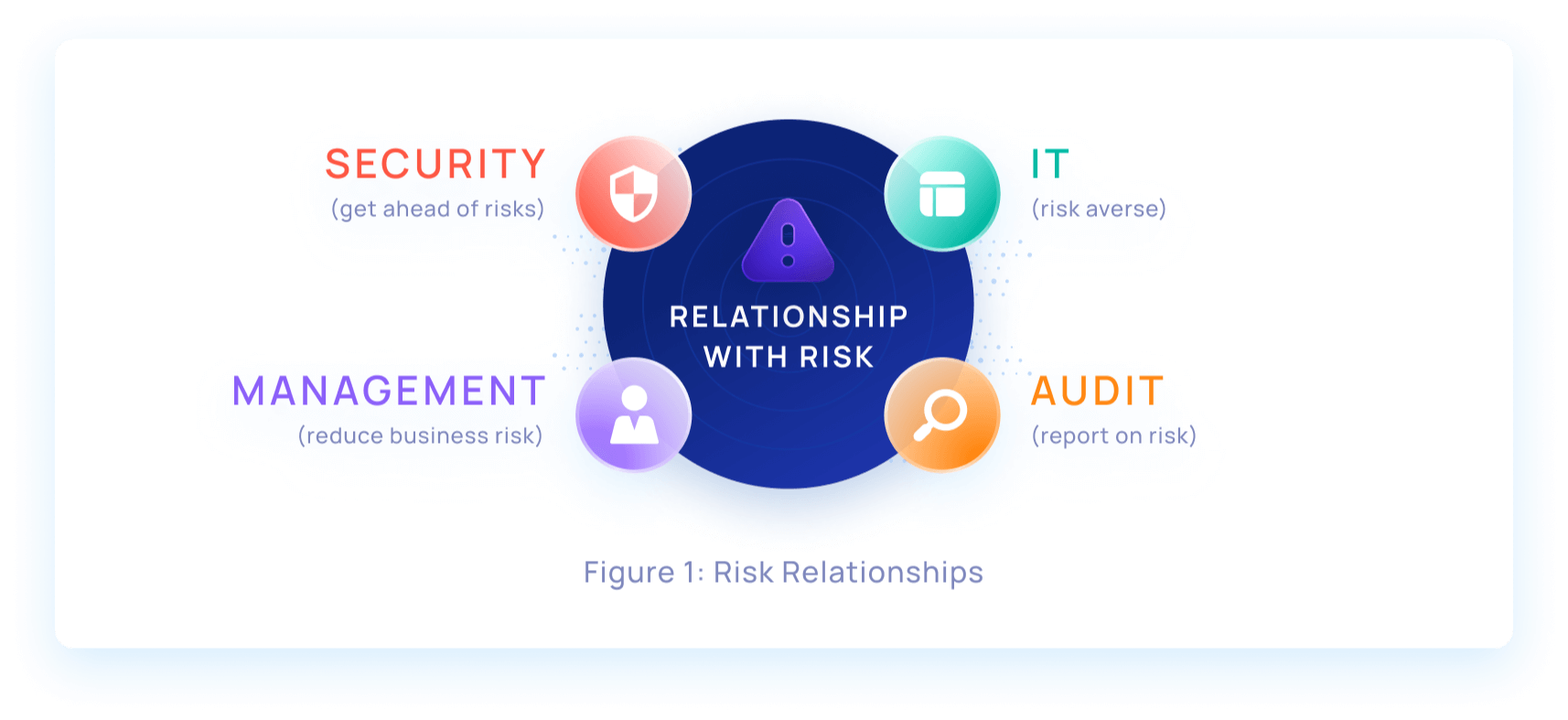
Saviynt’s Buyer’s Guide breaks down the key characteristics of a modern PAM solution, including:
- Built on cloud-native architecture (“Cloud-born”)
- Delivers awareness around cloud risks
- Robust governance and policy engine
- Enables zero trust/zero standing privilege
Phase 3: Activating Modern Just-in-Time (JIT) Capabilities
Privilege abuse or misuse is a factor in nearly every cyber breach. Cyber attackers have been able to bypass the traditional security perimeter with ease. Once inside a network, hackers can lurk undetected, looking for elevated privileges to open up more attack vectors.
This is why the old model of privileged credential vaulting and session recording falls short. As long as standing accounts still exist, retain a high level of privilege, and stay centrally stored in a vault, your organization can remain unnecessarily exposed.

As part of a Zero Trust strategy, most industry analysts recommend moving to a zero standing privilege (ZSP) model, whereby all privileged accounts, except those needed for break-glass purposes, are removed. ZSP is enabled by a just-in-time approach to privilege elevation.
Turn to Saviynt’s ebook, “JIT PAM: Time to Turn Off ‘Always On’” for guidance on engaging the right teams, the pros and cons of several different approaches to JIT PAM, how to map your risk landscape, and where to focus for quick wins.
Tip: build momentum by onboarding assets that carry a high level of risk and are minimally disruptive to daily operations.
 These three guides are good primers for those looking to embrace cloud PAM use cases. With our pioneering approach to identity-driven PAM delivered on our converged Enterprise Identity Cloud (EIC), we work with customers everyday to help them advance their PAM programs and improve security.
These three guides are good primers for those looking to embrace cloud PAM use cases. With our pioneering approach to identity-driven PAM delivered on our converged Enterprise Identity Cloud (EIC), we work with customers everyday to help them advance their PAM programs and improve security.
Saviynt Approach
Saviynt Cloud PAM is built on our Enterprise Identity Cloud which converges IGA, granular application access, cloud security, and privileged access into the industry’s only enterprise-grade, SaaS-based identity solution. Our identity-driven PAM approach means that customers can manage all identities and entitlements more efficiently to improve enterprise-wide visibility and leverage identity intelligence to make better access decisions.











 These three guides are good primers for those looking to embrace cloud PAM use cases. With our pioneering approach to identity-driven PAM delivered on our converged Enterprise Identity Cloud (EIC), we work with customers everyday to help them advance their PAM programs and improve security.
These three guides are good primers for those looking to embrace cloud PAM use cases. With our pioneering approach to identity-driven PAM delivered on our converged Enterprise Identity Cloud (EIC), we work with customers everyday to help them advance their PAM programs and improve security.


