Content Hub
Industry
Solutions







07 / 09 / 2024
Enterprise Identity Cloud: Accelerate Your Zero-Trust Journey with New Microsoft Integrations
READ BLOG














07 / 09 / 2024
Ask the Experts: Solving Top Multi-Cloud Identity Management & Governance Challenges
READ BLOG


07 / 09 / 2024
Identity and Access Intelligence: Infusing Analytics & Intelligence to Improve Identity Governance
READ BLOG


07 / 09 / 2024
NIST 800-53 Identity and Access Management (IAM) Compliance via Saviynt’s FedRAMP ATO
READ BLOG



























07 / 09 / 2024
Choosing a Cloud Privileged Access Management (PAM) Solution?: Three Must-Ask Questions
READ BLOG

07 / 09 / 2024
Solve Compliance Headaches with Cross-App Reporting and Automated Certification
READ BLOG


07 / 09 / 2024
Gain Peace of Mind with Emergency Access Management & Out-of-the-Box Compliance Reporting
READ BLOG











07 / 09 / 2024
Top Challenges to Achieving Enterprise-Wide Visibility of Privileged Access
READ BLOG
































07 / 09 / 2024
New EIC v2022 Enhancements Boost Speed & Efficiency in Application Onboarding
READ BLOG









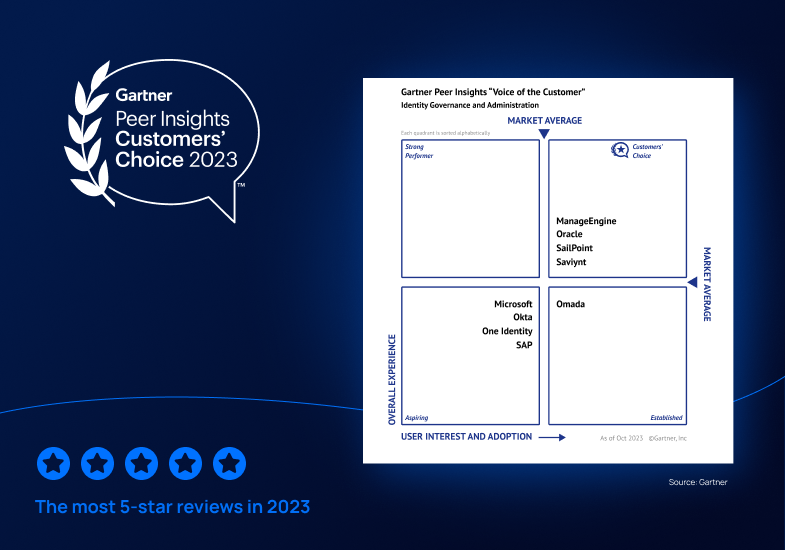
07 / 09 / 2024
Saviynt a Gartner® Peer Insights™ Customers' Choice in Identity Governance and Administration—Three Years in a Row
READ BLOG




.jpg)

07 / 09 / 2024
Why Henrique Teixeira Joined Saviynt | The IGA Problem, The Technology, The People
READ BLOG

07 / 09 / 2024
Manage Complete Identity Lifecycle and Eliminate Unused Access throughout AWS Environments
READ BLOG



07 / 09 / 2024
Saviynt EIC Scores 95/100 for Core Criteria in the 2022 Gartner® Solution Comparison for Identity Governance and Administration¹
READ BLOG

07 / 09 / 2024
Leaving Legacy Challenges Behind – The Triumph of Converged Identity Platforms
READ BLOG


07 / 09 / 2024
Saviynt Recognized as a 2022 Gartner® Peer Insights™ Customers’ Choice in Identity Governance and Administration
READ BLOG