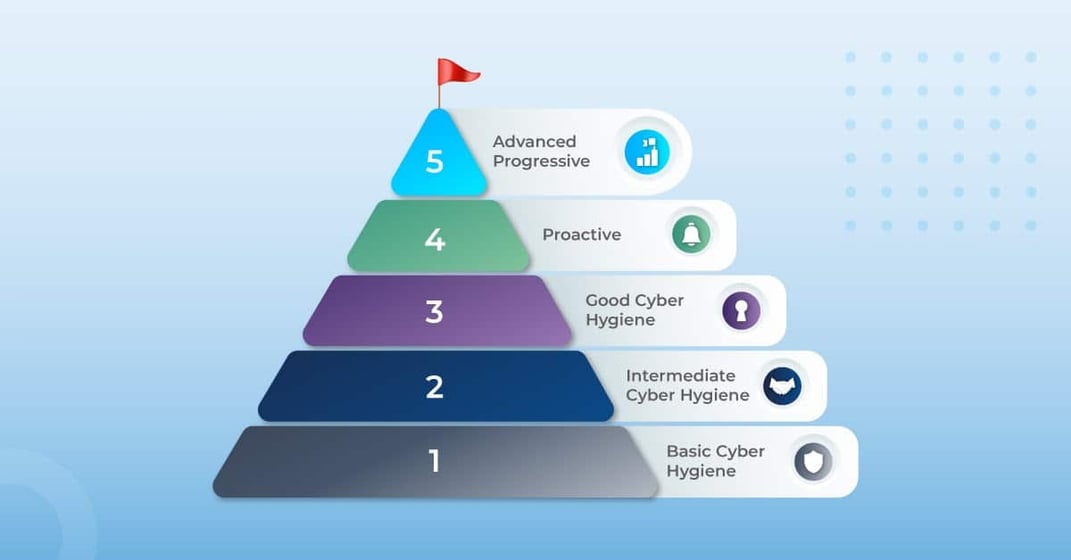
What CMMC Level Do Contractors Need?
In general, Level 3 clearance serves as a baseline for security, and it will often be enough to secure contracts. To meet Level 3, a company must have a management plan designed to conduct operations with cyber hygiene best practices in mind, including NIST 171 standards. The NIST 171 standards are security requirements aimed at protecting controlled unclassified information (CUI). CUI is typically defined as “any information that law, regulation, or government-wide policy requires to have safeguarding or disseminating controls.”
Demonstrating full NIST 171 compliance can be challenging to maintain, especially when assets reside on-premises and in the cloud. However, automation and risk-based assessment of access requests can streamline the access management process in the face of dissolved network boundaries. It accomplishes this by extending governance uniformly throughout the IT ecosystem, making it easy to meet compliance requirements consistently. Likewise, implementing risk-based data governance helps provide consistent controls no matter where the data resides.
Costs and Labor
Extra security also means extra costs, so you’ll need to keep that in mind. The external assessment comes in the form of third-party auditors, or C3PAOs, required under the CMMC framework. Hiring the auditors and going through the audit process will add additional expenses and time investments to your operations. Some estimates show that the typical assessment audit program will cost between $20,000 and $40,000. However, continuous monitoring and tracking of controls provide the evidence auditors will require, minimizing employee time invested.
Of course, it isn’t easy to manage subcontractor access and guarantee that they are appropriately scoped and accessed. It can also be a challenge to ensure their access is removed when they leave. Because all DoD contractors and subcontractors will need to be CMMC compliant by October 1, 2025, it’s recommended that prime contractors begin working with their subcontractors to develop the relevant compliance programs. That doesn’t have to be a challenge, however. Vendor access management solutions can oversee contractor access to sensitive materials and manage their access throughout the vendor-subcontractor lifecycle.
Finally, meeting the evidentiary burden of the CMMC requirements can be difficult. You’ll need to prove that you’re constantly and consistently meeting the requirements. That process can be labor-intensive if the proper evidence isn’t readily available or adequately tracked. That’s why it’s in your best interest to automate your evidence collection. Continuous monitoring and tracking of controls provide the evidence auditors will require, minimizing employee time invested.