Content Hub
Industry
Solutions






07 / 09 / 2024
Ask the Experts: Solving Top Multi-Cloud Identity Management & Governance Challenges
READ BLOG
07 / 09 / 2024
Identity and Access Intelligence: Infusing Analytics & Intelligence to Improve Identity Governance
READ BLOG










07 / 09 / 2024
Gain Peace of Mind with Emergency Access Management & Out-of-the-Box Compliance Reporting
READ BLOG
























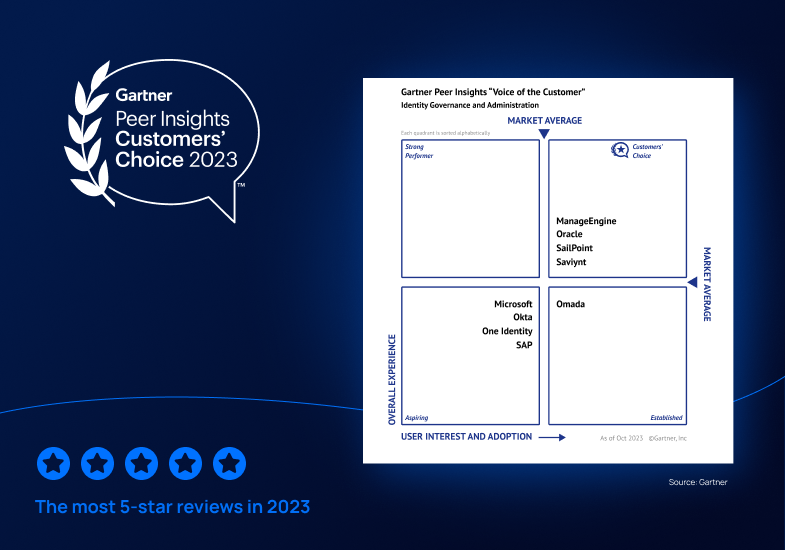
07 / 09 / 2024
Saviynt a Gartner® Peer Insights™ Customers' Choice in Identity Governance and Administration—Three Years in a Row
READ BLOG




07 / 09 / 2024
Saviynt EIC Scores 95/100 for Core Criteria in the 2022 Gartner® Solution Comparison for Identity Governance and Administration¹
READ BLOG
