Embracing Innovation Without Sacrificing HIPAA Compliance
“Staying on the cutting edge of technology means running the risk of bleeding.” I’ve heard this saying a hundred times. For a long time, the healthcare industry appeared to live by a similar tenet. Risks of adopting new technology kept the healthcare industry dragging its collective feet for many years.
According to a 2014 study by Harvard Business Review Analytic Services, only 27% of healthcare organizations proactively sought to be early adopters of new technology. Much of this resistance hinged on the difficulty of meeting complex regulatory requirements, such as the Health Insurance Portability and Accountability Act (HIPAA), California Consumer Privacy Act (CCPA), HIPAA, Payment Card Industry Data Security Standard (PCI/DSS), and numerous others. Then came the pandemic.
In spite of the risks, the healthcare industry adapted rapidly to serve patients in the midst of a global health crisis. Healthcare technology moved at a breakneck pace, accelerating technology trend adoption in many areas, including:
- Telehealth and Virtual Visits
- Remote Monitoring and Management
- Clinical Decision Support
- Cloud Electronic Health Records (Cloud EHRs)
- Patient Engagement
- Consumer Access to Clinical Data,
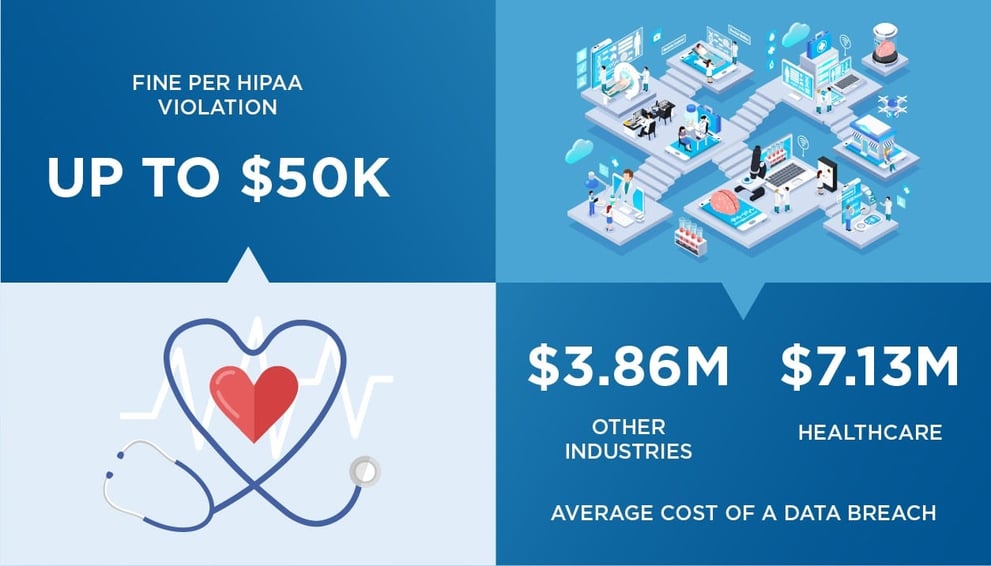
Cloud EHRs continued expanding to account for a majority of the market share. Innovations such as these allow providers to serve patients better and improve efficiency. Yet maintaining compliance with regulations like HIPAA and CCPA is exceptionally challenging. Missteps lead to large fines and costly remediation plans.
This guide reviews ways that healthcare providers and associated vendors can embrace innovative technology by adopting smarter identity and access management practices — all without sacrificing healthcare security or patient privacy.
EHR Compliance
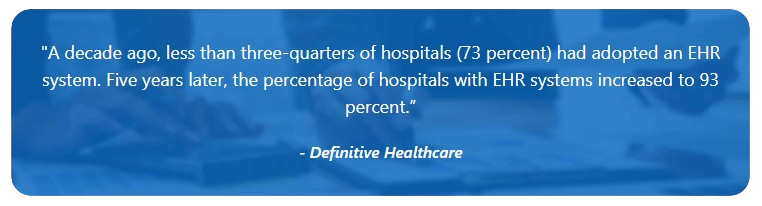
In 2010, the Patient Protection and Affordable Care Act (PPACA) mandated EHR solutions for providers to receive Medicare and Medicaid money. Since then, the adoption of EHR solutions has proliferated, recently expanding to include Cloud EHRs. EHR Intelligence points out that by 2018, the percentage of hospitals with an EHR system implemented or planned rose to 98 percent.
Compliance regulations require organizations to demonstrate they actively work to protect against fraud. At a minimum, this means gathering sufficient evidence to present at an audit. Regulations such as HIPAA and CCPA require more than merely gathering evidence of proactive data security. They require that organizations uphold least privilege, address Segregation of Duties (SoD), and eliminate the inappropriate access of patient records.
Protecting patient data includes addressing both internal and external threats. The multiple modules within an EHR solution cover every aspect of the patient experience, from treatment to billing. This creates large quantities of valuable healthcare data — putting a target on providers’ backs and tempting cybercriminals.
Patient Privacy in Telehealth
Telehealth is another swiftly growing healthcare sector that encompasses mobile services, patient portals, remote monitoring, and provider collaboration. The increased usage of telehealth creates challenging questions for providers to answer, including:
- How is information secured?
- What specific data is collected?
- Is the collection’s scope restricted to only what is necessary for providing care?
Remote care’s popularity is partially due to the COVID-19 pandemic, but adoption was increasing even before the pandemic. According to the American Medical Association (AMA), telehealth doubled from 14 to 28 percent between 2016 and 2019. A 2020 Accenture survey reported a 900 percent increase in the use of telehealth services, and usage isn’t expected to decrease even after the pandemic is over.
Challenges in Healthcare Security
The nature of modern healthcare makes compliance incredibly complex, and role-based access controls (RBAC) alone no longer address modern healthcare technology needs. Let’s look at three significant challenges that healthcare must address.
Identity Sprawl
One of the most significant challenges in establishing security in healthcare, especially in a large organization, is identity sprawl. This term describes a situation where an identity is managed by multiple siloed sources that are not synchronized with each other. This results in multiple identities for each user. To be secure, companies need to match these duplicates and merge them into a single identity to understand who has access to what data.
Compliance regulations mandate that users only have the level of access needed to perform their jobs and only for the necessary length of time. Tying all access to a single identity for each user is essential for ensuring least privilege and reducing SoD violations. It provides a holistic view of what access ties back to an individual.
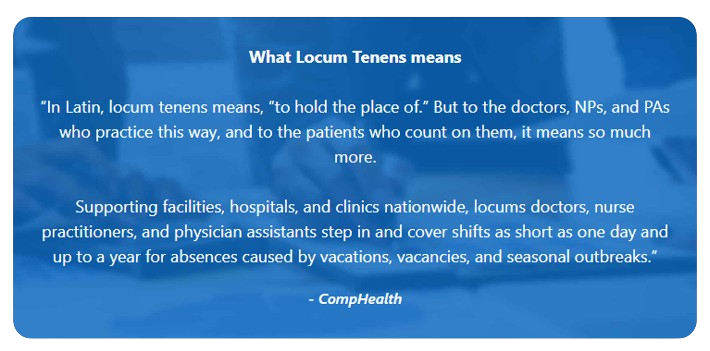
Healthcare’s Rotating Workforce
Many healthcare providers have a large temporary workforce to assist in everything from accounting to providing care. Temporary staff is widespread, with 94% of healthcare facilities utilizing locum physicians in their organization. Organizations must manage these individuals’ identities — while re-tying them back to the original identity — without re-initiating permissions. Administrators must deal with this complexity and assign access based on the person’s needs at the precise moment they require resources. Speed and simplicity are crucial for ensuring access is available when needed and closed up when no longer required while maintaining an in-depth audit trail for compliance.
Flex staff may work at various hospital locations on different days, resulting in frequently changing permission needs. Many organizations use staffing firms and temp firms to fill in workforce needs as required. For example, California has historically not allowed hospitals to employ doctors, meaning a lot of physicians are also contractors. If access remains for these individuals when they are no longer working in that specific capacity, healthcare records are left vulnerable. By using identity and continuous controls, healthcare organizations can create a holistic approach to security.
Insider Threats
Security threats aren’t limited to those outside the organization. Insider threats account for almost one-third of all attacks. Standing privilege, orphaned accounts, and a rotating workforce leave healthcare organizations vulnerable to access abuse.
Even individuals with the best intentions can unwittingly fall prey to bad actors through social engineering or phishing. Any compromised account is a security hole. The modern healthcare environment is under attack as it has never been before. Protecting patient information requires a shift from static access controls to more dynamic identity and access management.
Experian describes the coming year as a ‘cyber-demic,’ calling COVID-19 vaccine rollout information and personal healthcare data “particularly vulnerable.” Last year, 90% of the breaches Experian serviced were healthcare or telehealth related. Meanwhile, new statistics show a 45% increase in cyberattacks against the global healthcare sector since November — over double an increase of 22% against all worldwide industries in the same time period.
One Identity for Life and Zero Standing Privilege
So many healthcare organizations have moved to the cloud to benefit from modern technology’s advantages, that half of all EHR revenue is cloud-based. As a result, security solutions need to be more focused on the cloud to meet modern business needs. Additionally, IoT (Internet of Things) technology connects numerous devices from the local network to the EHR wherever it resides, creating vulnerabilities. With a single identity and continuous controls, organizations can take a holistic, agile approach to security.
Identity Management and Access Management
Security in the cloud requires establishing a full portrait of a user’s risk profile, including:
- Access Analytics
- Usage Analytics
- Individual User Activity
- Inherent User Risk
By aligning data and user access across the systems, healthcare organizations can create detailed user roles and groups to manage contextual identity information. User activity can then be tracked and monitored by multiple factors such as type, role, and functionality performed. Access management performs real-time authentication and the application of policy to deliver appropriate access to each user.
The importance of addressing both identity and access management is evident when you consider the example of a clinical worker who prescribes medication. This person should not also be able to dispense medication. Identity management dictates the identity and rights of this user. It prevents them from having the ability to both prescribe and dispense. Access management applies the access rights when the person logs into the clinical application, ensuring segregation of duties.
Zero Standing Privilege
Zero Standing Privilege is a security model based on the assumption no identity should have standing privileges, even administrators. Implementing Zero Standing Privilege using a combination of identity access management (IAM) and cloud privileged access management (CloudPAM) ensures that the principle of least privilege is applied. Zero Standing Privilege guarantees compliance for healthcare organizations by requiring those with access to hold it only for a limited period.
Take Advantage of Technology While Ensuring Compliance
While healthcare security challenges are significant, it’s possible to meet privacy mandates and achieve regulatory compliance with the right tools. A Zero Standing Privilege model, based on a convergence of identity governance and access management, will enable healthcare organizations and vendors to use modern technology without compromising security.
Learn what the future of healthcare security holds during Saviynt’s CONVERGE 20 session with Michael Allred, Director Identity and Access Management at Intermountain Healthcare.
Related Post


Report
Saviynt Named Gartner Voice of the Customer for IGA

EBook
Welcoming the Age of Intelligent Identity Security

Press Release
AWS Signs Strategic Collaboration Agreement With Saviynt to Advance AI-Driven Identity Security

Solution Guide