Related Post

Report
2024 Identity and Security Trends

Report
Saviynt a Gartner Peer® Insights Customers Choice for IGA

Solution Guide
IGA Buyer's Guide
-1.png)
Solution Guide
PAM Buyers Guide

Whitepaper
Use our partner finder to discover your perfect business match.
Tune in for expert-led live demos on how Saviynt’s identity security solutions transform your digital security with actionable insights and best practices.

The world of third party access governance is – and isn’t – like identity governance and administration (IGA). The motivations may be the same but the risks are very different.
Recently, Anirudh Sen (AS), Saviynt VP of Products, and Nitish Deshpande (ND), Research Analyst with KuppingerCole, sat down to discuss third-party lifecycle management, process challenges, and the ways organizations are taking steps to solve this problem.
Here’s a snapshot of their conversation.
ND: These are two related concepts but with a different focus and scope. Obviously third-party access governance deals with the relationships with external employees, while IGA is about internal employees. But there are similar requirements with lifecycle management and enabling self-service.
AS: I think you make a great point. At the end of the day we are managing identities. But there is a large difference in terms of the risk involved with managing third parties. And if you look at some of the recent breaches that have occurred, a lot of them have to do with suppliers and their access being compromised, which in turn affects your organization. One reason for this is with third parties, management is not centralized. Usually what we see is that each line of business manages their own relationships, which means the risk is highly distributed. Contrast this to IGA, where internal workers tend to be centralized through the human resources department.
Another reason is the rise in remote working. Third party workers may not be coming into an office, so it’s easy to lose sight of what work they’re doing and if their access is appropriate, and this has a lot of enterprises very worried. There are some proposed SEC changes that will require companies to report on their third party relationships and how they are managing them. This is bringing third party management into sharp focus for many publicly traded companies.

ND: I completely agree. Take a look at supply chains. With each new vendor you bring in, the risk just gets greater. This is why we are seeing organizations – especially those that operate in multiple geographies – work to increase their supply chain resilience. And as you have pointed out with SEC rules, compliance is a big driver for public companies.
Regulatory requirements are also evolving in other sectors such as healthcare, finance, and technology. It’s important to make sure that your third party relationships can meet compliance needs. Organizations will need to do better risk assessments and more due diligence of their external relationships.
AS: The motivations for every customer are different, but they all need to arrive at a solution that provides a few important functions. First is a single source of truth for all third party relationships. Many companies cannot give an accurate accounting of their external B2B users. Their solution needs to make it easy to collaborate with third parties. There’s a reason companies are outsourcing work. Management complexity is a non-starter.
And finally, any solution needs to enable the line of business owners to own their relationships and associated risks.
ND: As they strengthen their access controls, customers are also putting better encryption protocols in place to prevent breaches and data leaks. The goal is to avoid unauthorized access by vendors who don’t need a high level of permission and only need access for a limited period of time. The larger the organization, the more complex their vendor ecosystem tends to be.
One area companies should focus on is the termination process. It’s important to have sound lifecycle management in place so that access is removed, in real-time if possible, to protect sensitive data.
Another change that is evolving quickly is the integration of AI and automation and machine learning, and it’s becoming a challenge now to secure this autonomous world. More and more companies are moving towards digital transformation or AI and machine learning and these new trends. But that means we will have a bigger attack surface. How will identity governance solutions address these challenges—which currently lack the contextual understanding that humans have.
AS: That’s a great point about AI. Everyone’s jumping on it but nobody’s thinking about what risks it introduces. Anything that’s on the bleeding edge of technology is going to move us forward but we need to make sure we’re not introducing any unforeseen risks.
At Saviynt, we are taking a hard look at what’s happening in the market, the industry, and any regulatory changes surrounding third party ecosystems.
What’s gaining traction are many different use cases including:
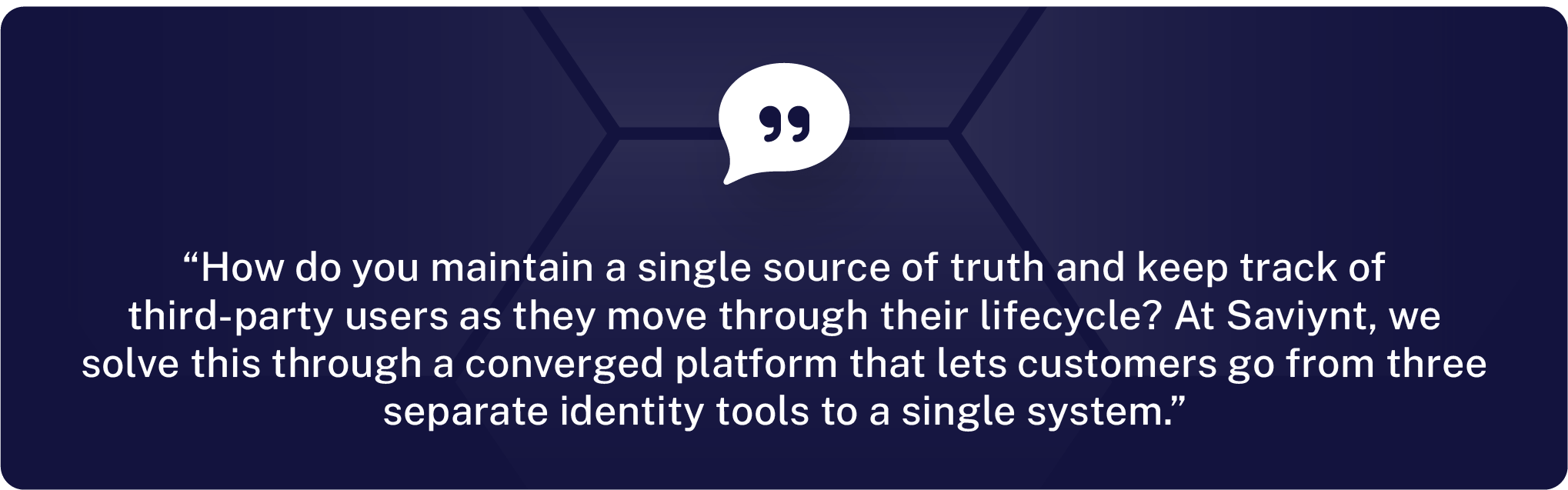
The common challenges seem to center around bringing them onboard quickly and securely collaborating with them. How do you maintain a single source of truth and keep track of third party users as they move through their lifecycle? For example, you may need to grant privileged access to certain systems. The last thing you want to do is give them yet another access tool for this environment. And if you want to convert a contractor to an employee, you’re now talking about transferring them to the IGA system.
At Saviynt, we solve this through a converged platform that lets customers go from three separate identity tools to a single system.
ND: That’s a very nice example about onboarding an external employee; it shows the convergence between third party and IGA solutions. What would be your advice to organizations when they want to implement third party governance?
AS: If I put my practitioner hat on, the main thing I would advise is that external access governance is not the same as IGA. A lot of customers will ask why they can’t just use their HR tool to manage contractors. The problem with that approach is that HR doesn’t own the risk of managing third parties. There are different contracting mechanisms that need to be managed outside of HR. By using the right tools for the job, companies can get better visibility into who has access to what and who has provided this access to address issues and reduce risk.
Saviynt Third-Party Access Governance provides complete third-party identity management. Start the relationship off securely with seamless onboarding, then simplify lifecycle management with automation and AI-driven identity intelligence. Manage third-party identities in the same system as your badged employees and make continuous compliance a reality in your organization.


Report

Report

Solution Guide
-1.png)
Solution Guide

Whitepaper