Deloitte recognizes the use of behavioral analytics to create baseline markers of normal user behaviors. Additionally, built-in natural language processing (NLP) can help easily monitor for abnormal occurrences – and learn (and infer) from behavior patterns. This supports faster, frictionless identity-related decision making.
During our recent CONVERGE 20 Roadshow, Michael Allred, Director of Identity and Access Management at Intermountain Healthcare shared how his team benefits from analytics (and making smarter, more secure decisions) at scale: “Reviewing user-behavior and auditing access for 50,000 users is simply not sustainable.”
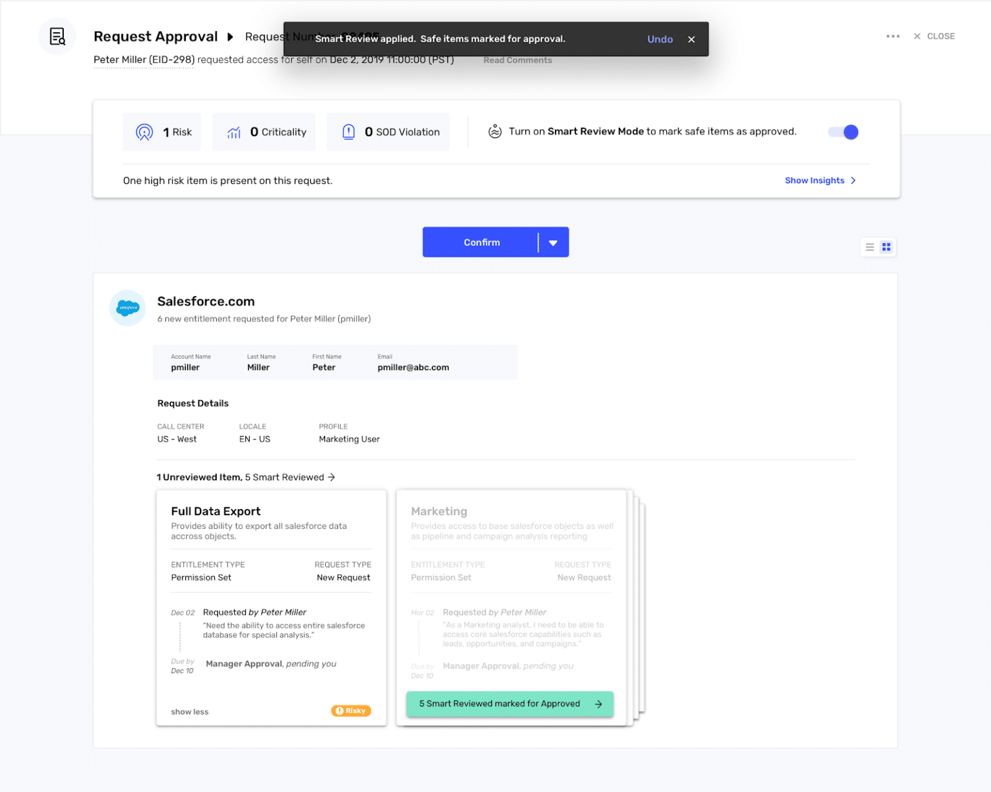
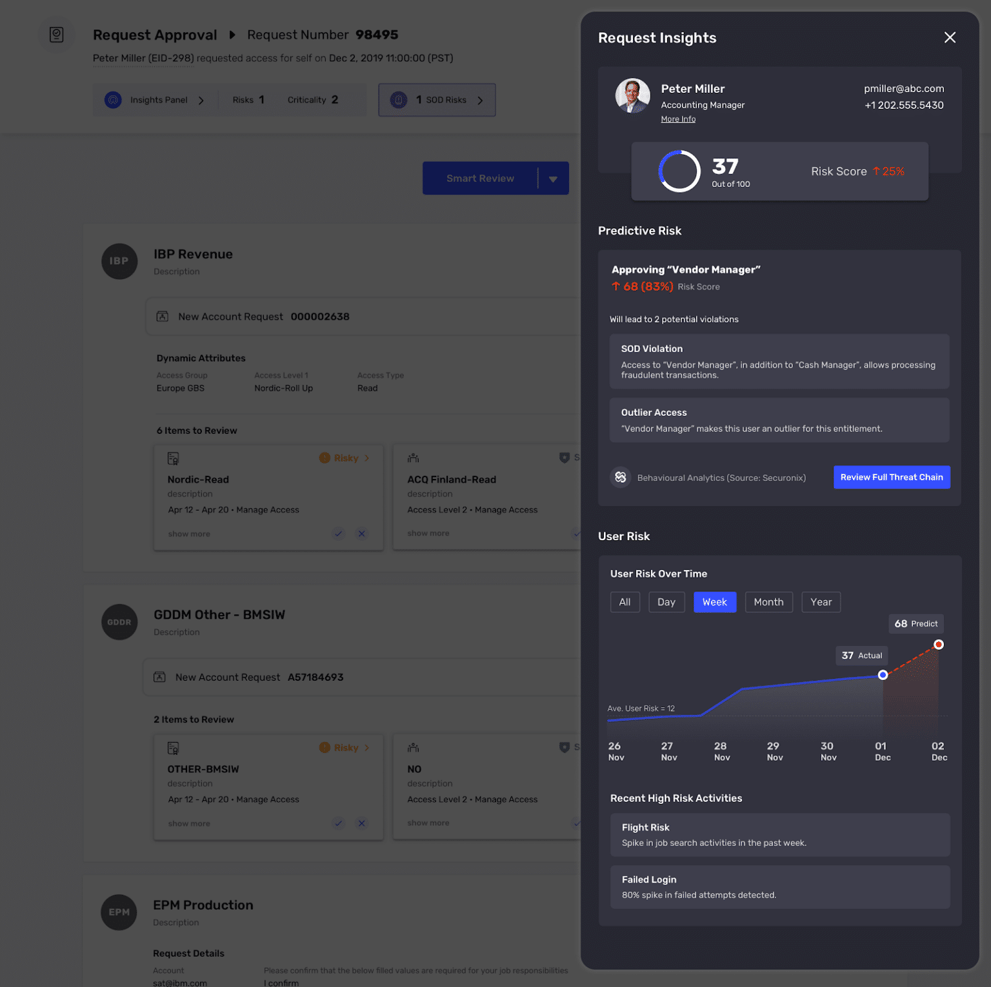
With Saviynt’s actionable analytics, enterprises can visualize data and risks, and promptly respond. These include real-time insights into user risk changes due to excessive access or the presence of activities outside a role/user’s typical behavior. Insights lead to smarter controls, too, including creating and managing access policies & roles.
Intelligence without actionability isn’t useful, which is why Saviynt integrates with (and ingests data from) SIEM and UEBA solutions. Most companies use multiple tools to evaluate their security postures, which requires managing large quantities of logs, alerts, and notifications. Our platform intelligently curates these – adding visibility and risk scoring to support anomalous activity detection and incident responses.
AI & ML
Central to ‘intelligent identity’ is smarter work underpinned by AI & ML. One of the most useful applications of these technologies is risk modeling and decision making.
For example, we recently announced Assisted AI, which bridges human and machine intelligence interactions to create better governance strategies. Identity-centric security starts with knowing who accesses what resources, why they need access, and how they ultimately use that access.