On September 10, Saviynt announced Saviynt Intelligence, a new suite of capabilities bringing additional insights and clarity for identity security. Intelligent Recommendations is the first offering introduced under the Saviynt Intelligence umbrella and is not simply an incremental improvement in existing Saviynt Identity Cloud features, but a radical reimagining of how Identity Governance and Administration (IGA) is achieved.
The Vision
Development began almost two years ago when we engaged with industry experts, seasoned identity security practitioners, and a group of engineers, data scientists, and product managers to glean better insights and understanding of complex identity needs to solve a specific pain point afflicting identity security programs – accurate access. The goal was to craft a recommendation engine that would solve these needs using the state of the art advances in AI and machine learning.
The most critical issue was not surprising – the cognitive overload users face, leading to rubber stamping and a weakened threat defense. The question then became, “How do we reduce administrative and end-user burdens while enhancing security?” Identity security programs should predict what entitlements users may want to request, and provide actionable information for those users and those that would need to approve or validate access.
The solution needed to strike the right balance between intelligent automation and human insight. Innovative algorithms needed to crunch massive amounts of access data and combine multiple trust signals to identify high-trust, high-volume access suitable for automation. Low-trust and unique situations would need to be escalated to humans where nuanced decisions could be made based on intelligence provided by Saviynt’s Identity Platform. Customers and their users also needed complete transparency in how recommendations were made.
The Approach
From an architectural perspective, the most secure approach was clearly where each customer has their own Machine Learning (ML) model. Our design approach was to train the model exclusively on the customer’s data and have everything reside solely within their designated Saviynt cloud environment, ensuring its accessibility is restricted to only them. By integrating Intelligent Recommendations directly into the core platform, we are able to uphold all our commitments to data security and privacy.
As alluded to above, the oil that drives the recommendations is a customer’s access data and data sources that reside both inside and outside Saviynt. Addressing this problem requires specialized, scalable machine learning approaches.

The fundamental technical challenge we faced was a bit different from the recommendation engine problems encountered in other business domains such as e-commerce or online video streaming services. In those domains, the goal is to predict the next set of products or videos that the user would be most interested in based on their data and history. However, in the IGA space, the goal is to predict the next entitlements that the user may want to request while being completely transparent from an auditability standpoint as to why a particular recommendation was made. This meant that the traditional approaches such as collaborative filtering or ‘Restricted Boltzmann Machines’ (RBM) used in other domains were not suitable, as we wanted clear transparency as to why a particular recommendation was being made.
In order to address the shortcomings of the approaches from other domains, we have developed a unique, proprietary machine learning algorithm. This algorithmic strategy allows us to identify the precise reason behind a particular recommendation, offering complete transparency from an auditability standpoint and also offers administrators enhanced control should they decide to disable specific recommendations.
Automated, Accurate, and Performant
The above machine learning approach also paired well with the design goals that we were pursuing: automation, accuracy, and scalable performance. We aimed to create a system that requires minimal intervention from administrators, even in the face of organizational changes, mergers, or divestitures.
We made algorithmic improvements that ensured that the right set of attributes (up to 40) will be automatically selected to model each entitlement, leading to improved prediction accuracy. We also incorporated 14+ trust signals as a part of the trust modeling framework to provide recommendations that are based on a holistic view of all the identity access data that is available (SoD analysis, certification history, etc.).
All this was done while continuously stress testing the recommendation engine’s algorithm to ensure proper handling of the huge volumes of identity data of our customers. In the case of one early access program participant in the financial space, we were able to achieve a prediction accuracy of 93% for over 90% of their user access.
Looking Ahead
And we’re not stopping. Future releases will see Saviynt use Generative AI in concert with our machine learning models to provide interactive chat experiences for end users. These experiences will help further simplify identity governance management and provide powerful new tools to help complete tasks. The overall vision for how the Intelligence capabilities will evolve is laid out in Figure 1.
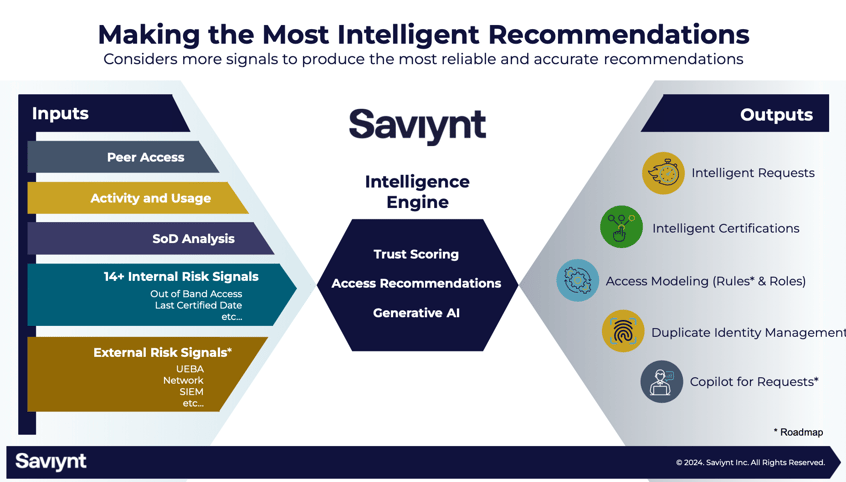
Fig 1. Saviynt leverages data from various sources (left) to deliver intelligent Identity Governance experiences (right) through our intelligence engine.
To learn more about Intelligent Recommendations or see a demo, please reach out to a member of your Saviynt account team or fill out this online form.
The next blog in our Intelligent series will delve into more specifics regarding recommendations for requests.









