How Saviynt and CrowdStrike create an AI-powered, unified security fabric
The cybersecurity landscape has reached a critical inflection point as the number and types of endpoints and identities organizations need to protect continues to rise. While 81% of businesses experienced at least one malware attack in recent years, the statistics paint an even starker picture when examining the financial impact: the average data breach costs $4.88 million globally, with endpoint security breaches specifically costing organizations an average of $8.94 million.
On the identity governance front, independent research from the nonprofit Identity Defined Security Alliance (IDSA) reveals equally concerning trends. Their 2024 study of over 520 identity and security professionals found that 90% of organizations experienced at least one identity-related incident in the past year, with 84% of those incidents causing direct business impact—a significant increase from 68% in 2023.
This escalating threat landscape demands a fundamental shift in security strategy. When endpoint protection operates independently from identity governance, dangerous blind spots can emerge that sophisticated attackers exploit with devastating effectiveness.
Why Unify CrowdStrike Endpoint Protection and Saviynt Identity Security
In today's cyber threat landscape, siloed security tools create the very vulnerabilities that cybercriminals target most aggressively. The integration of CrowdStrike's industry-leading endpoint and response capabilities with Saviynt's AI-powered comprehensive Identity Cloud platform represents a paradigm shift—eliminating dangerous gaps by creating a unified identity security program that intelligently adapts to emerging risk and threats.
Saviynt Identity Cloud's deep integration with CrowdStrike delivers dramatically improved threat detection, automated risk response, and intelligent access controls that adapt in real-time to emerging risks. This unified approach doesn't just detect risks and threats—it understands the identity context behind every endpoint interaction, enabling security teams to respond with unprecedented precision and speed.
Mapping the Complete Attack Surface
When CrowdStrike detects compromised devices, traditional security approaches often struggle to understand the broader implications. Saviynt's Identity Security Posture Management (ISPM) immediately maps which users and entitlements are connected to those compromised devices, revealing exactly which users can be affected and what level of access they possess.
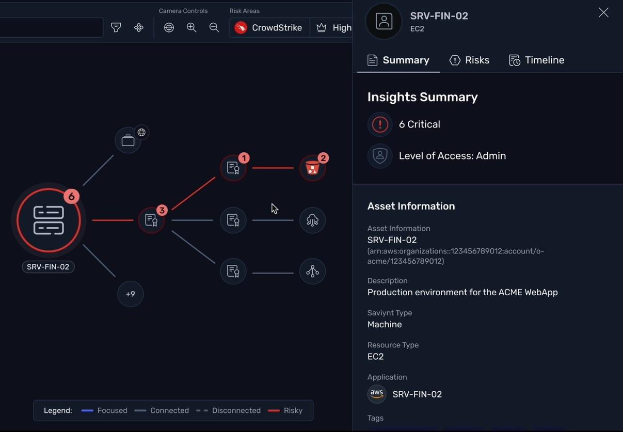
Saviynt leverages CrowdStrike endpoint data to quickly identify identity-related threats and the users affected by those threats.
This unified visibility extends beyond individual endpoints. By leveraging CrowdStrike's Cloud Security Posture Management (CSPM) registration for APIs across AWS, Azure, GCP, and other cloud platforms, Saviynt ISPM ingests misconfiguration data to provide unified visibility across cloud identities and resources. This enables security teams to identify toxic combinations—such as privileged users operating on compromised endpoints—and prioritize remediation efforts through a single, identity-focused dashboard.
The result is a complete picture of enterprise risk that transforms how organizations understand and respond to security threats. Rather than managing disparate alerts from multiple tools, security teams gain contextualized intelligence that reveals the true business impact of each security event through a single system.
Risk-Responsive Cyber Security That Adapts in Real-Time
The integration also enables intelligent, risk-responsive access controls that automatically adapt to real-time security conditions. When CrowdStrike detects high endpoint risk or identifies unusual behavioral patterns, Saviynt dynamically adjusts user privileges without requiring manual intervention.
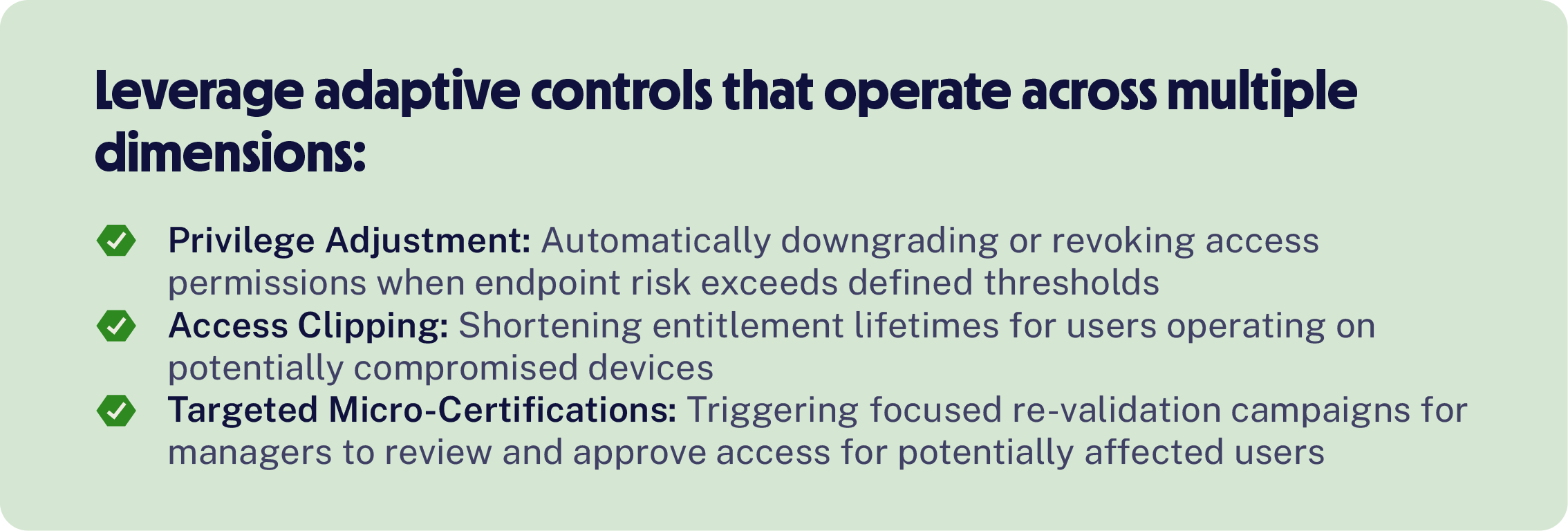
This automated approach ensures that access privileges continuously align with your current security posture, preventing compromised devices from maintaining elevated permissions while minimizing disruption to legitimate business operations. The system learns from each interaction, becoming more precise in its risk assessments and response strategies over time.
From Threat Detection to Resolution in Minutes, Not Hours
When CrowdStrike identifies high endpoint and device risk, Saviynt automatically triggers appropriate remediation actions based on predefined security policies and real-time risk assessment, including account suspension, high-risk entitlement revocation, and approval escalation.

The system enriches access reviews by flagging users with patterns of device compromise, enabling auditors and security teams to make informed decisions about risky access patterns. This intelligence-driven approach ensures rapid response to security incidents while maintaining detailed audit trails for compliance and forensic analysis.
Enhanced Threat Hunting and Investigation
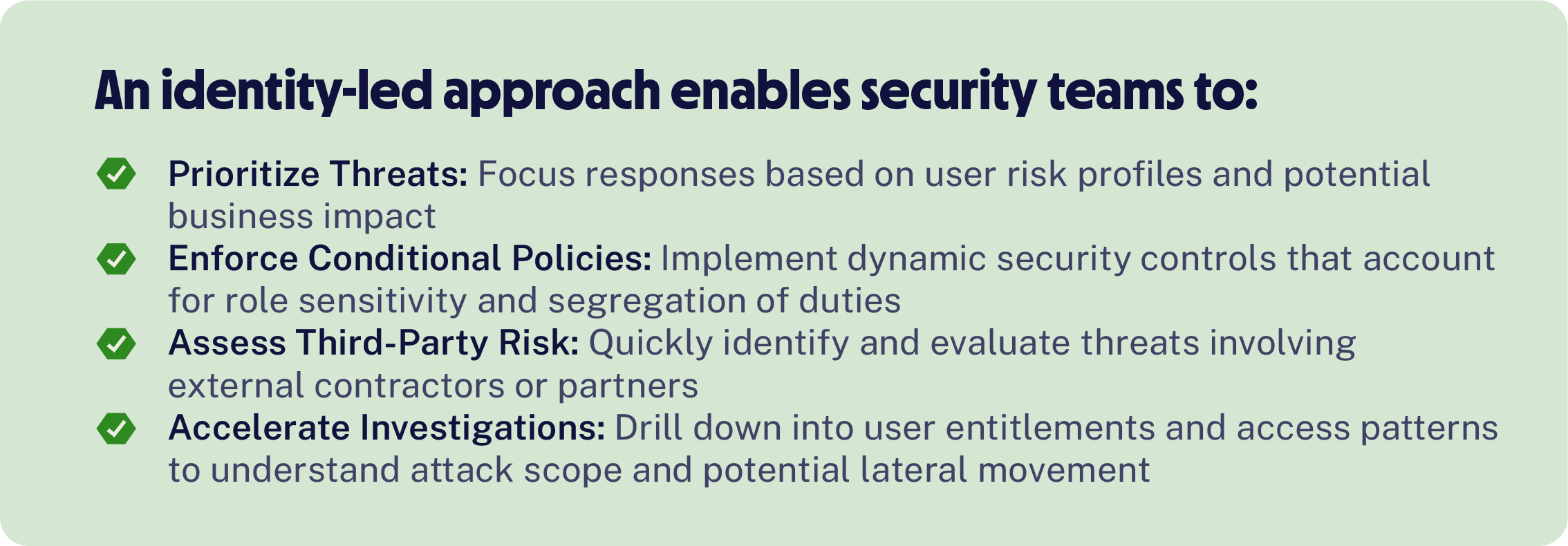
Saviynt also enriches CrowdStrike's threat detection capabilities by providing identity context that fundamentally transforms how security teams understand and respond to incidents. With Saviynt, CrowdStrike analysts gain comprehensive visibility into user roles, entitlements, access history, and behavioral patterns, enabling them to quickly determine whether compromised sessions involve privileged users, contractors, or other sensitive accounts.
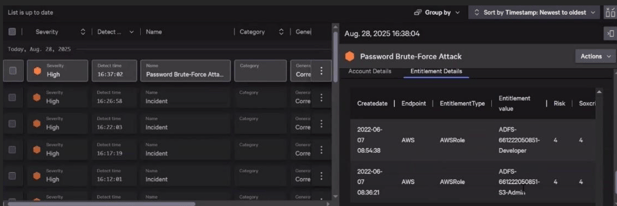
Quickly drill down in CrowdStrike to understand the entitlements of users targeted by attacks.
The result is precision security response that moves beyond generic threat detection to intelligent, context-aware incident management.
The Future of Unified Security
The integration of Saviynt and CrowdStrike represents more than a technical achievement—it's a fundamental reimagining of how enterprise security should operate. By eliminating the artificial boundaries between endpoint protection and identity governance, organizations can finally achieve the unified, intelligent security posture that modern threats demand.
With cyber-attacks happening approximately every three seconds globally, the need for this unified approach has never been more critical. Organizations that embrace AI-powered, integrated security architectures will not only better protect their assets but will also gain operational efficiencies that transform security from a cost center into a business enabler.
The question isn't whether your organization will face ongoing risks or sophisticated threats—it's whether you'll be better prepared with the unified, intelligent defenses necessary to detect, understand, and neutralize them before they can cause damage.
Learn more about unifying endpoint protection and identity security by visiting our Saviynt for CrowdStrike web page.












