Embrace a modern identity threat detection and remediation program using real-time threat intelligence from CrowdStrike Falcon to streamline investigations and enable rapid containment of identity-based risks.
Map compromised endpoints to identity access for a complete view of enterprise risk
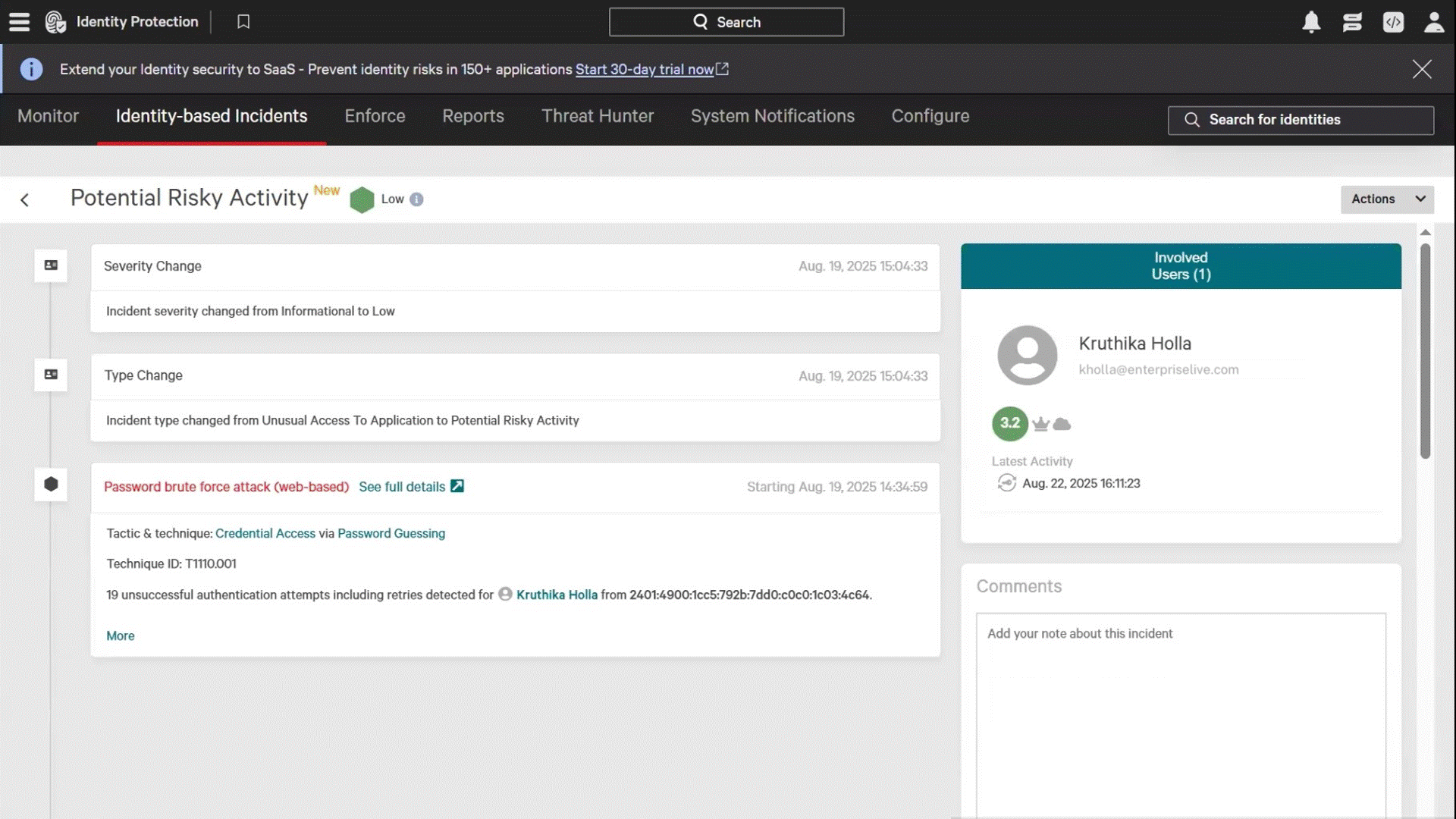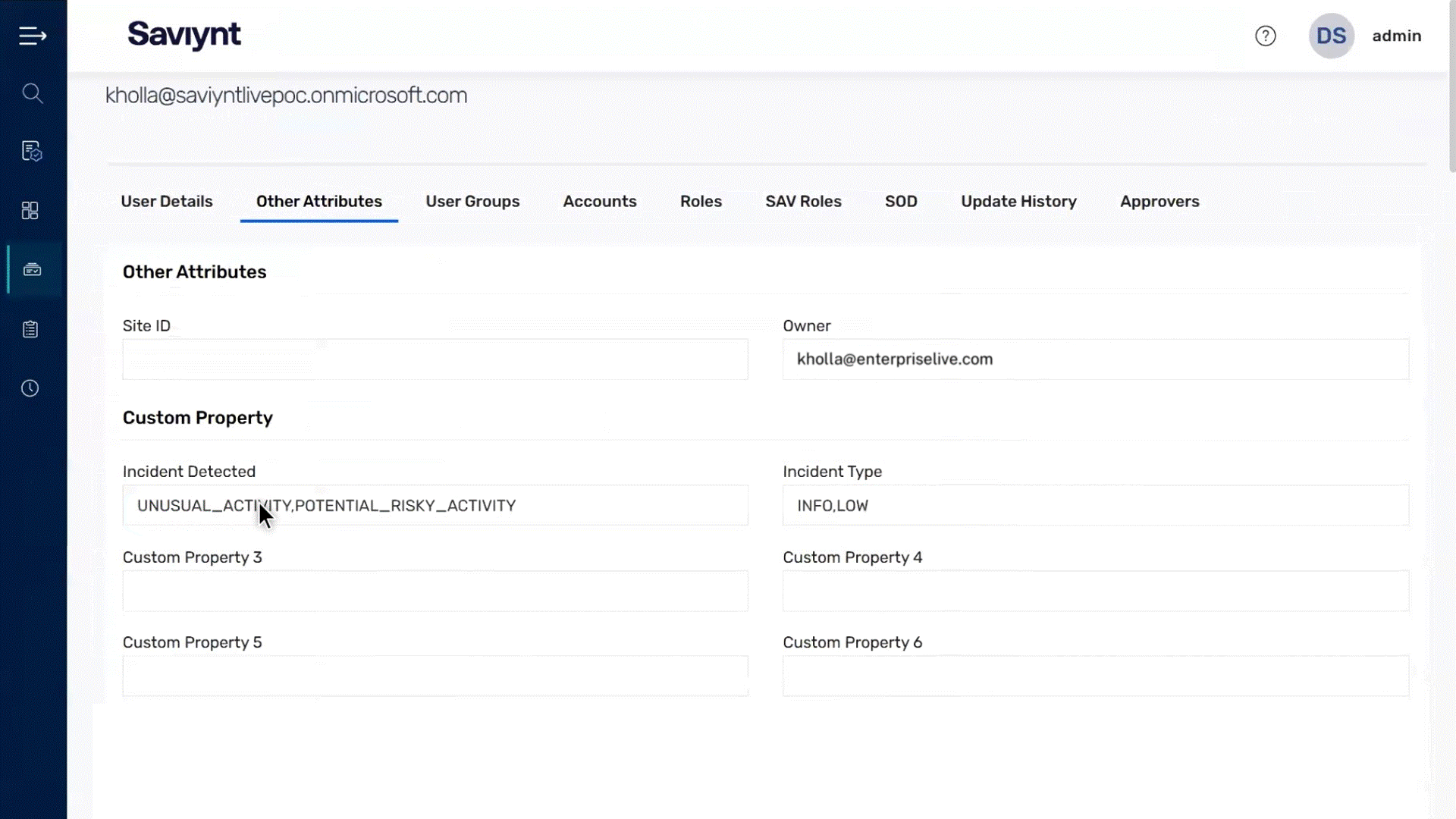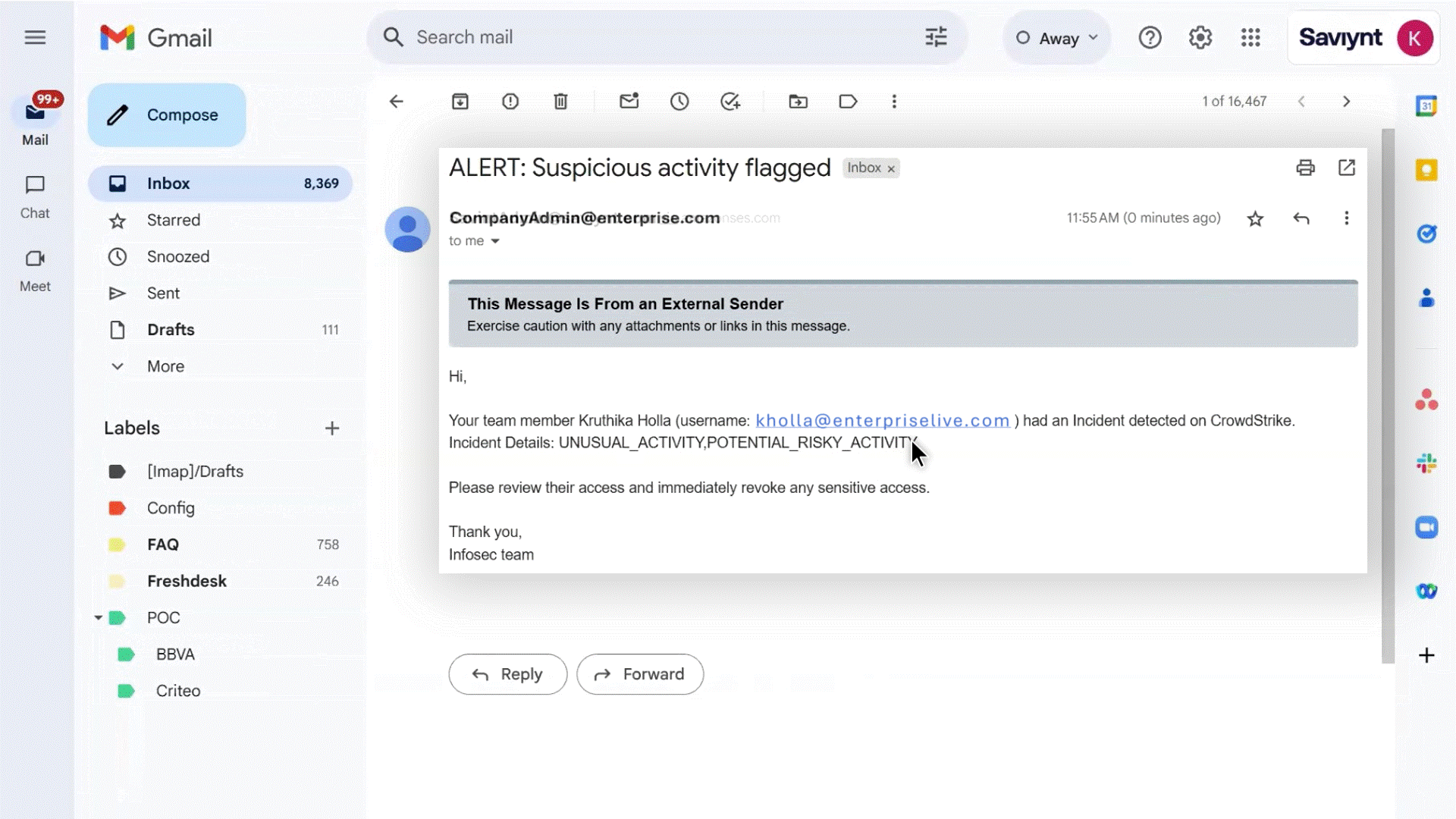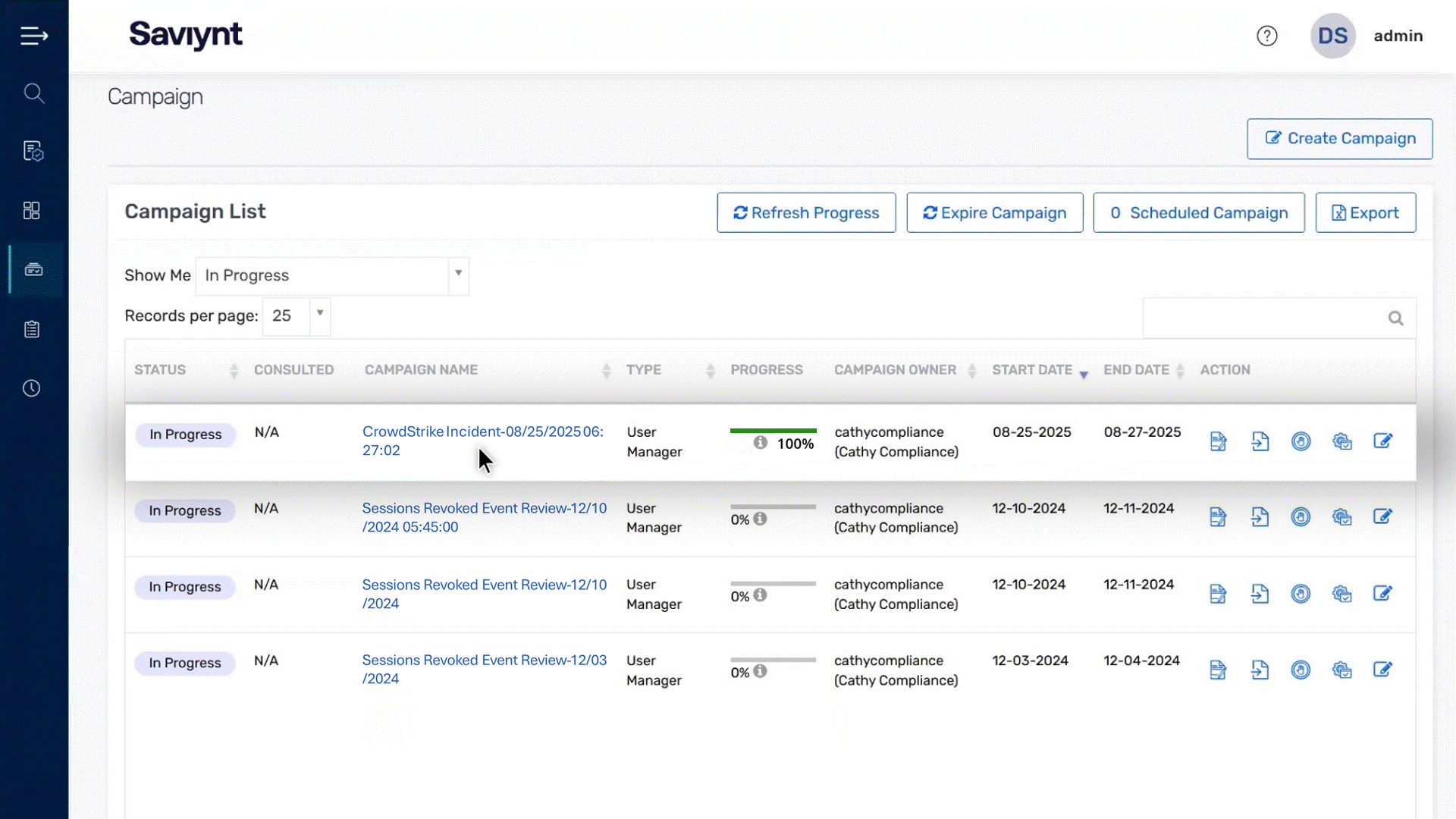
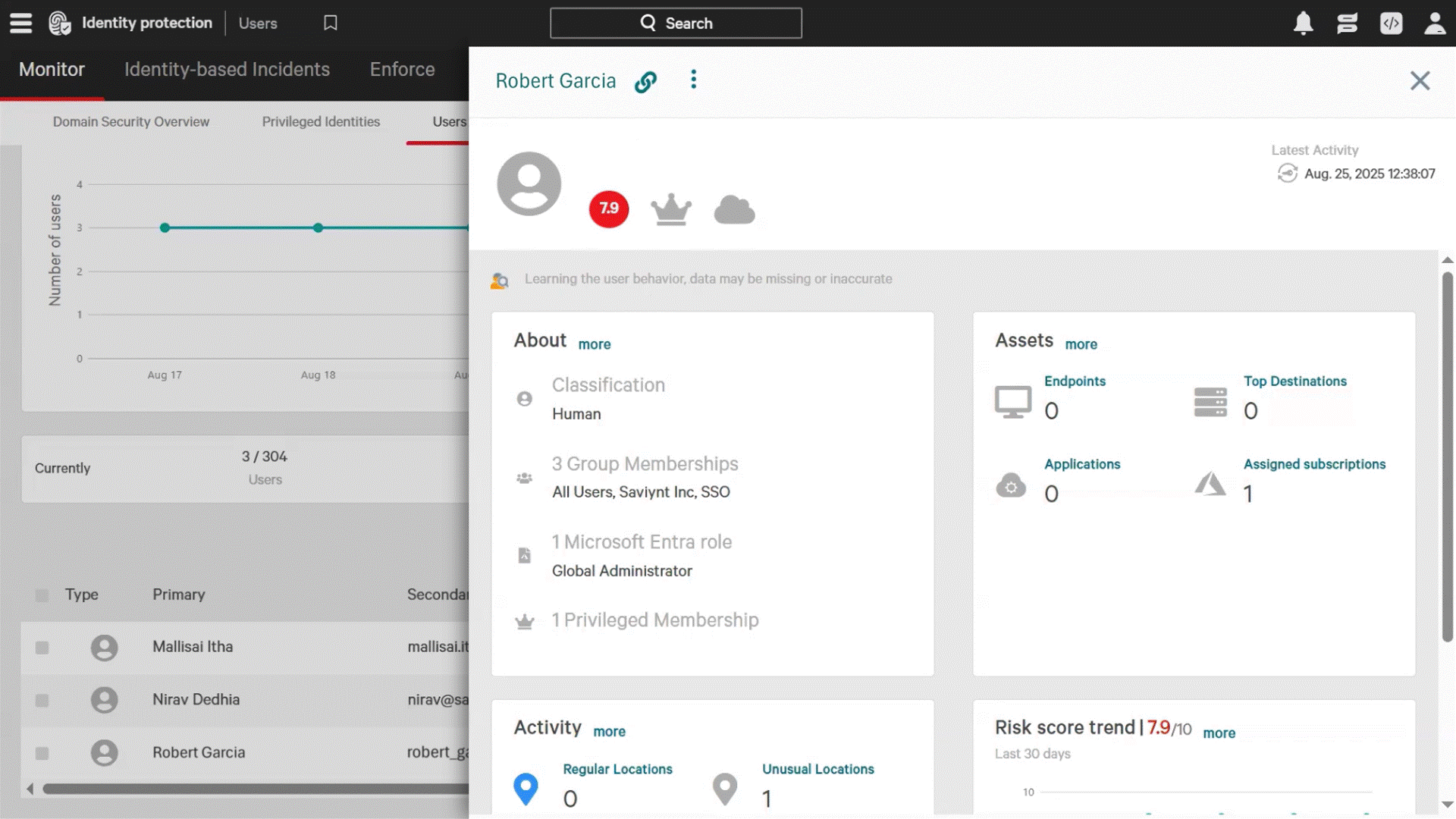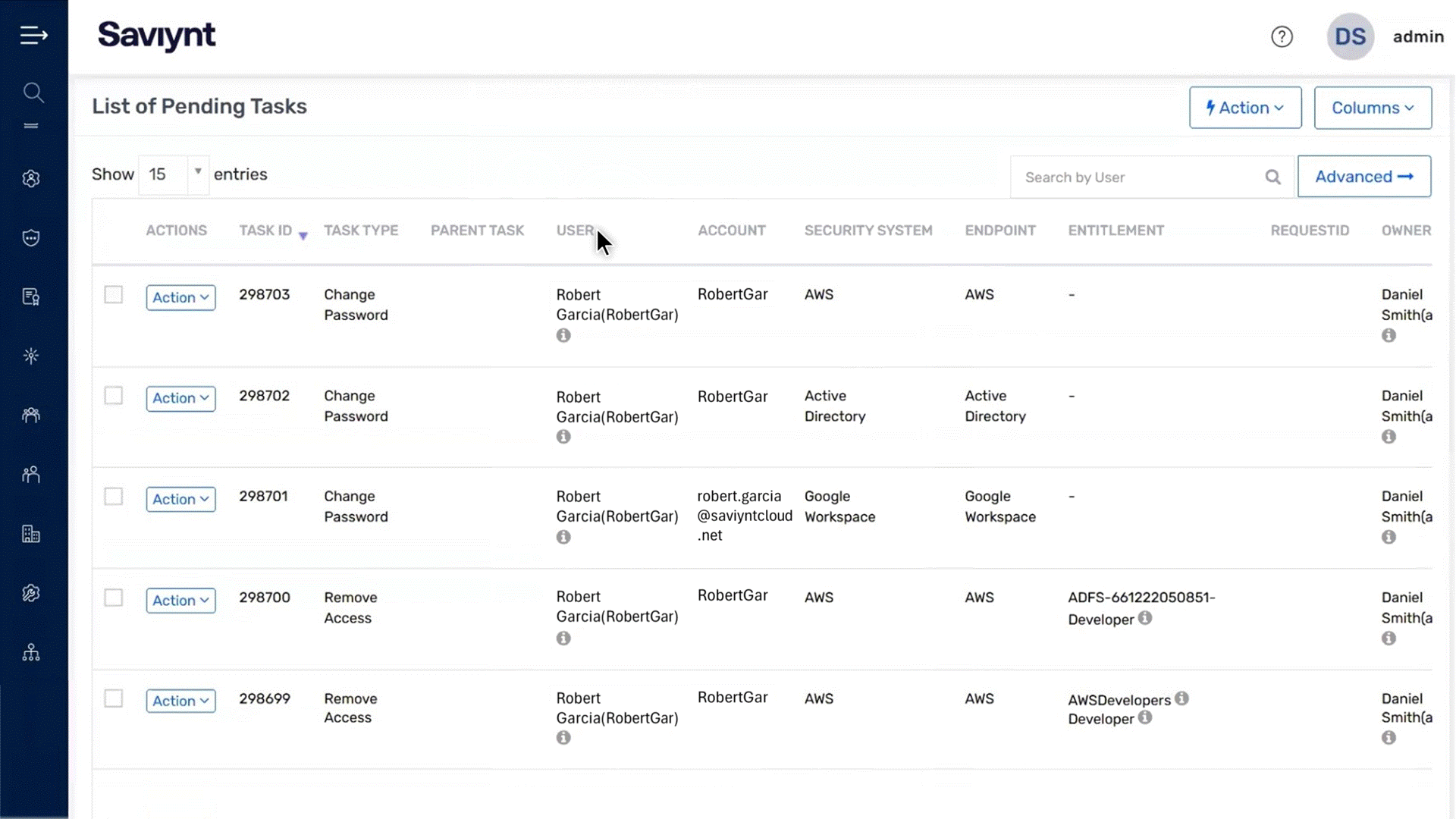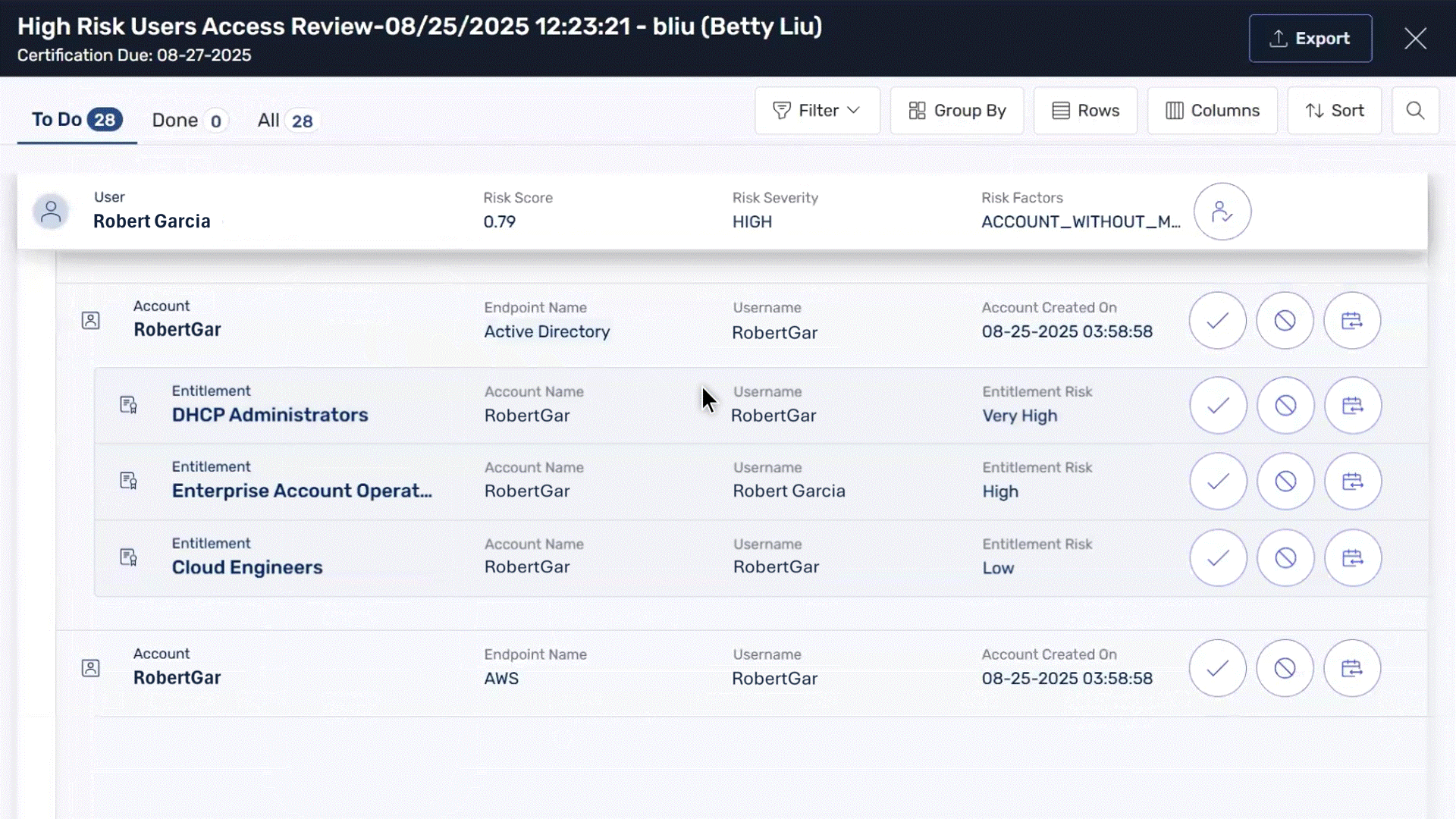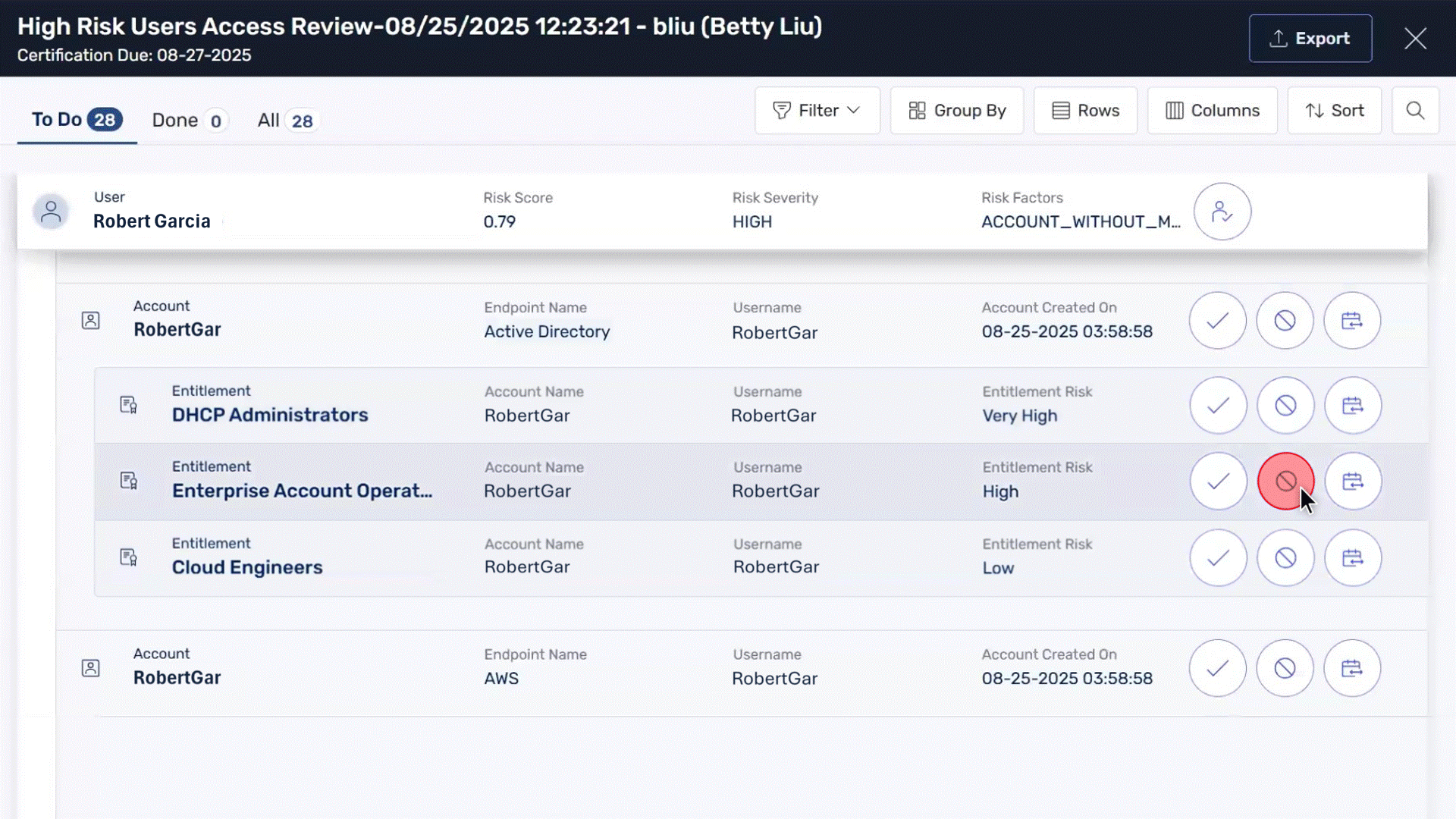
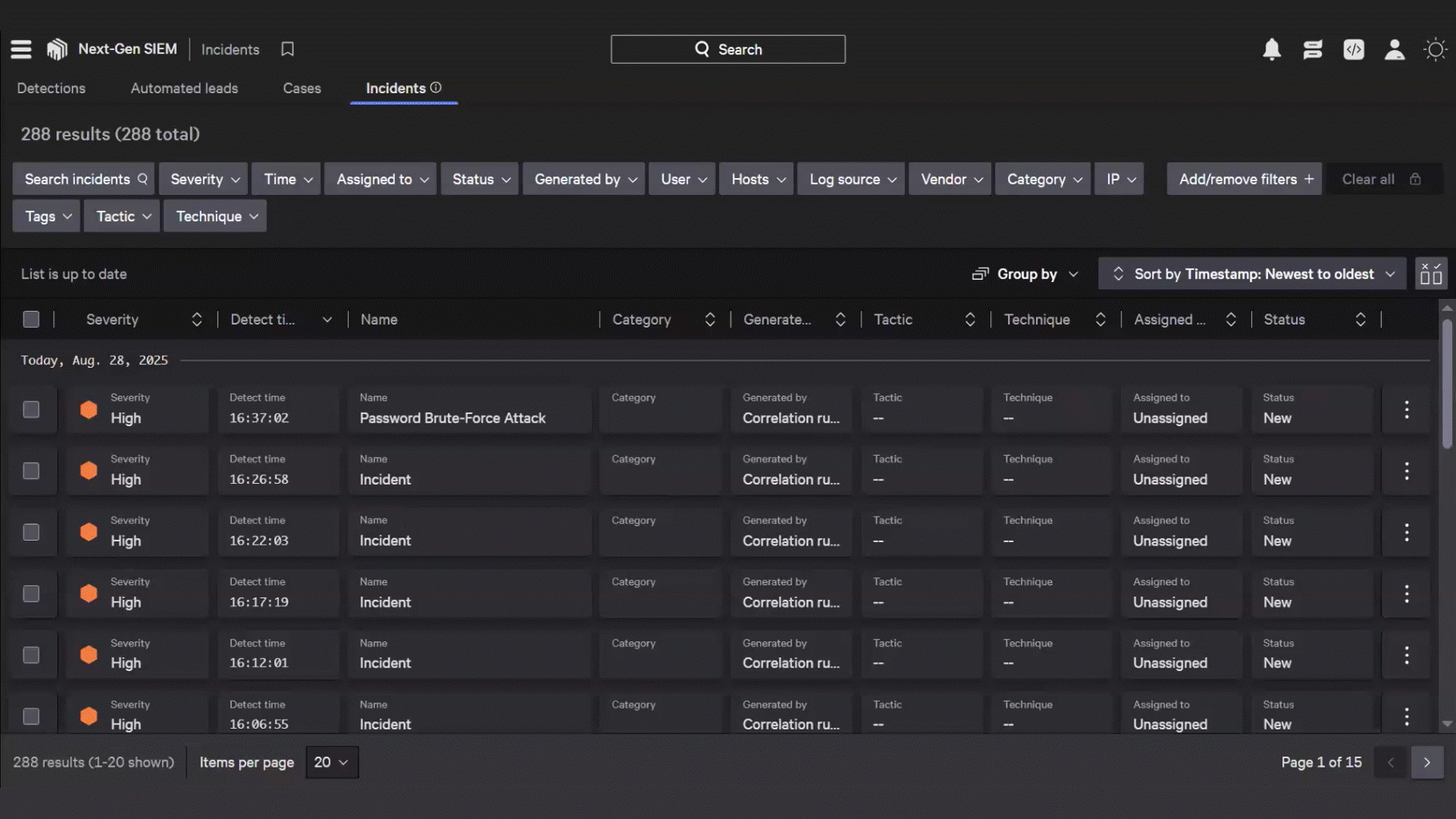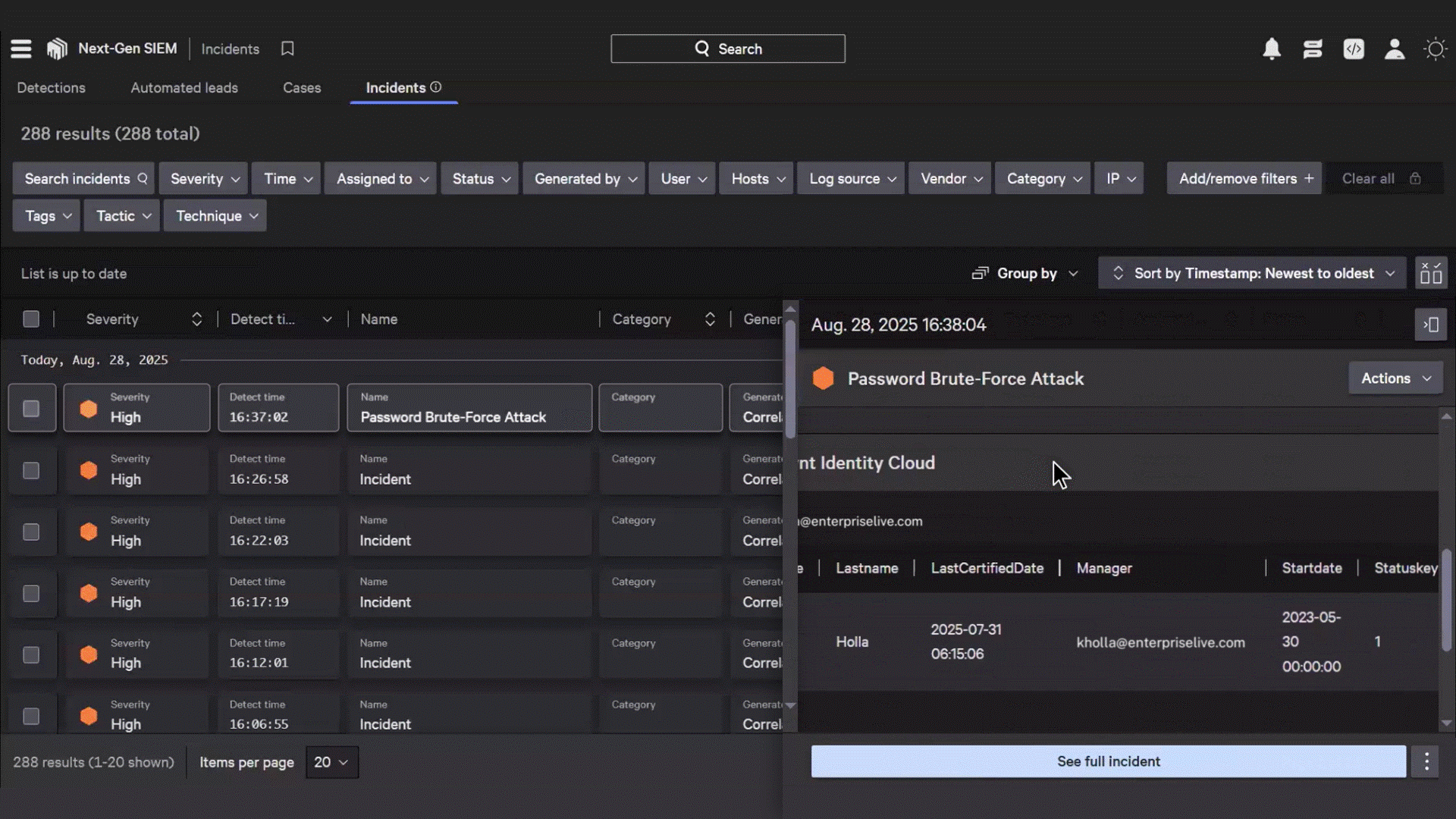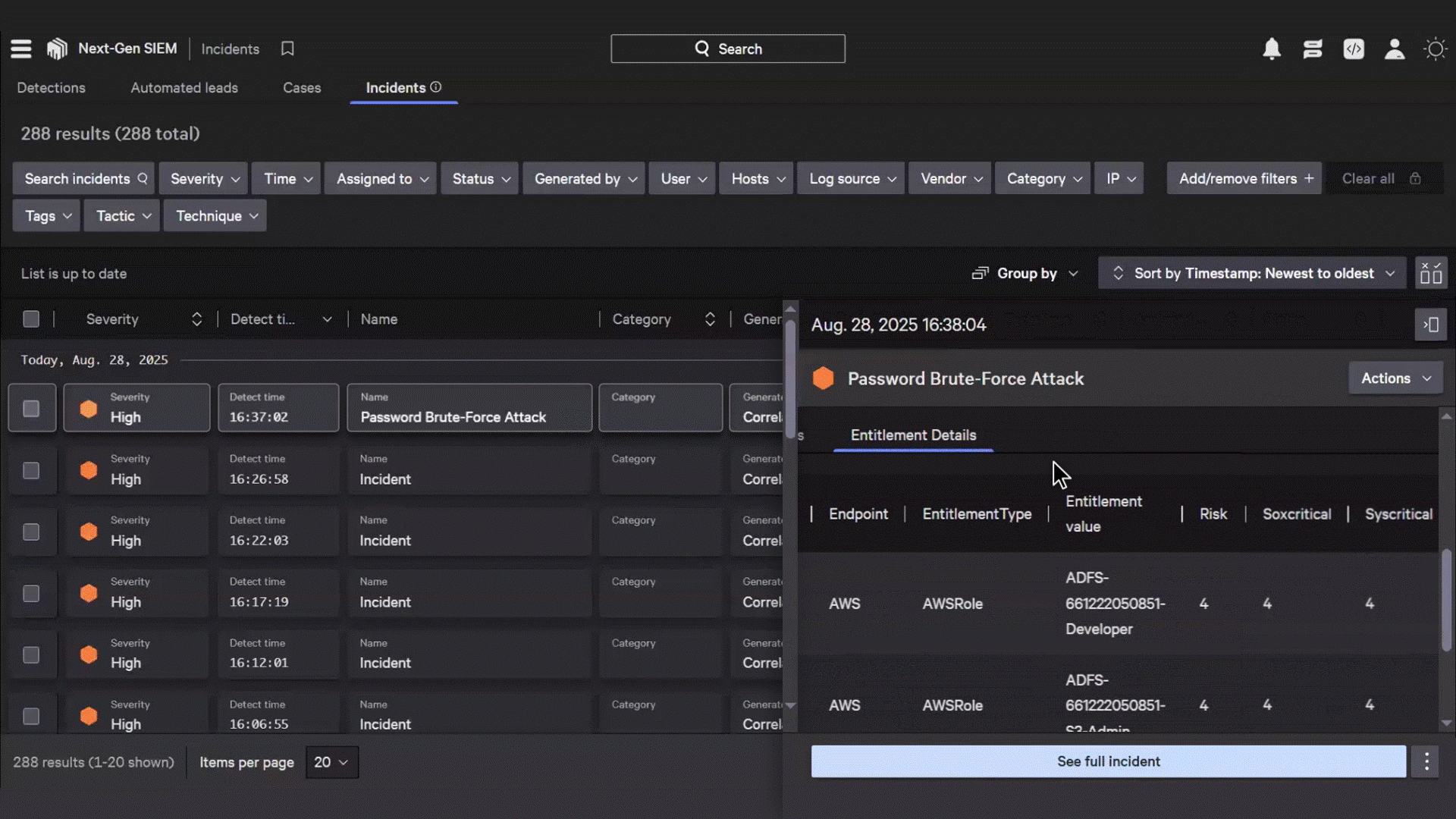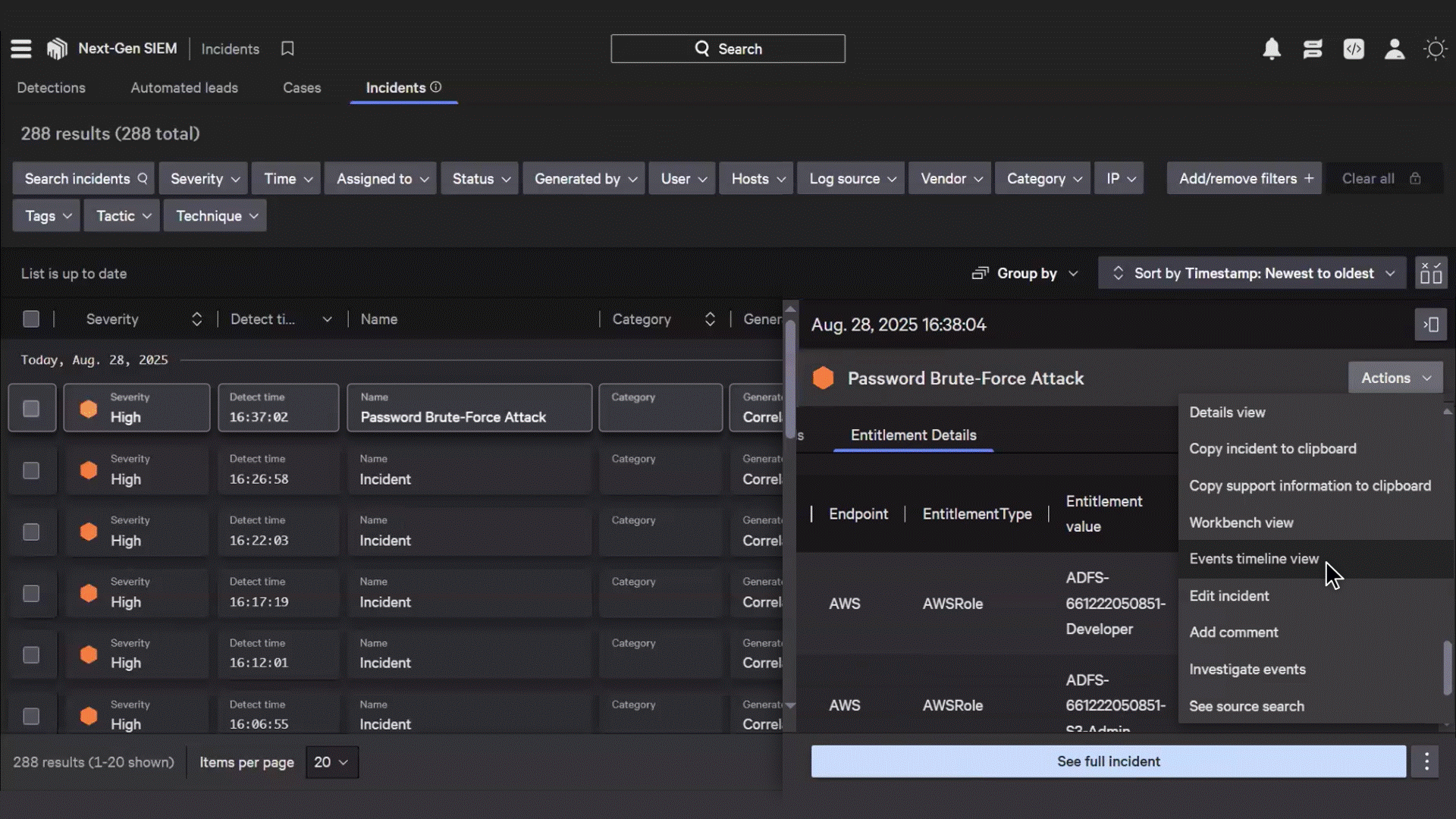
Understand incident blast radiuses by visualizing which human, non-human, and AI identities have access to compromised resources with real-time risk and threat mapping
Identify toxic identity-endpoint combinations to narrow investigation scope and reduce time to containment
Flag users with repeatedly compromised devices during access reviews to identify risky access patterns
Act on real-time conditions to prevent incidents without impacting productivity
Downgrade or revoke user access to prevent compromised devices from maintaining elevated permissions
Ensure access privileges continuously align with current security postures using condition-based controls
Accelerate remediation through automation
Enable instant security responses without manual delays
Automatically suspend user accounts, revoke dangerous entitlements, or escalate approvals by leveraging CrowdStrike’s endpoint risk data
Trigger access certification reviews to prevent ongoing credential abuse or require additional authorization for requests until threats are fully resolved
Transform how security teams recognize and respond to incidents
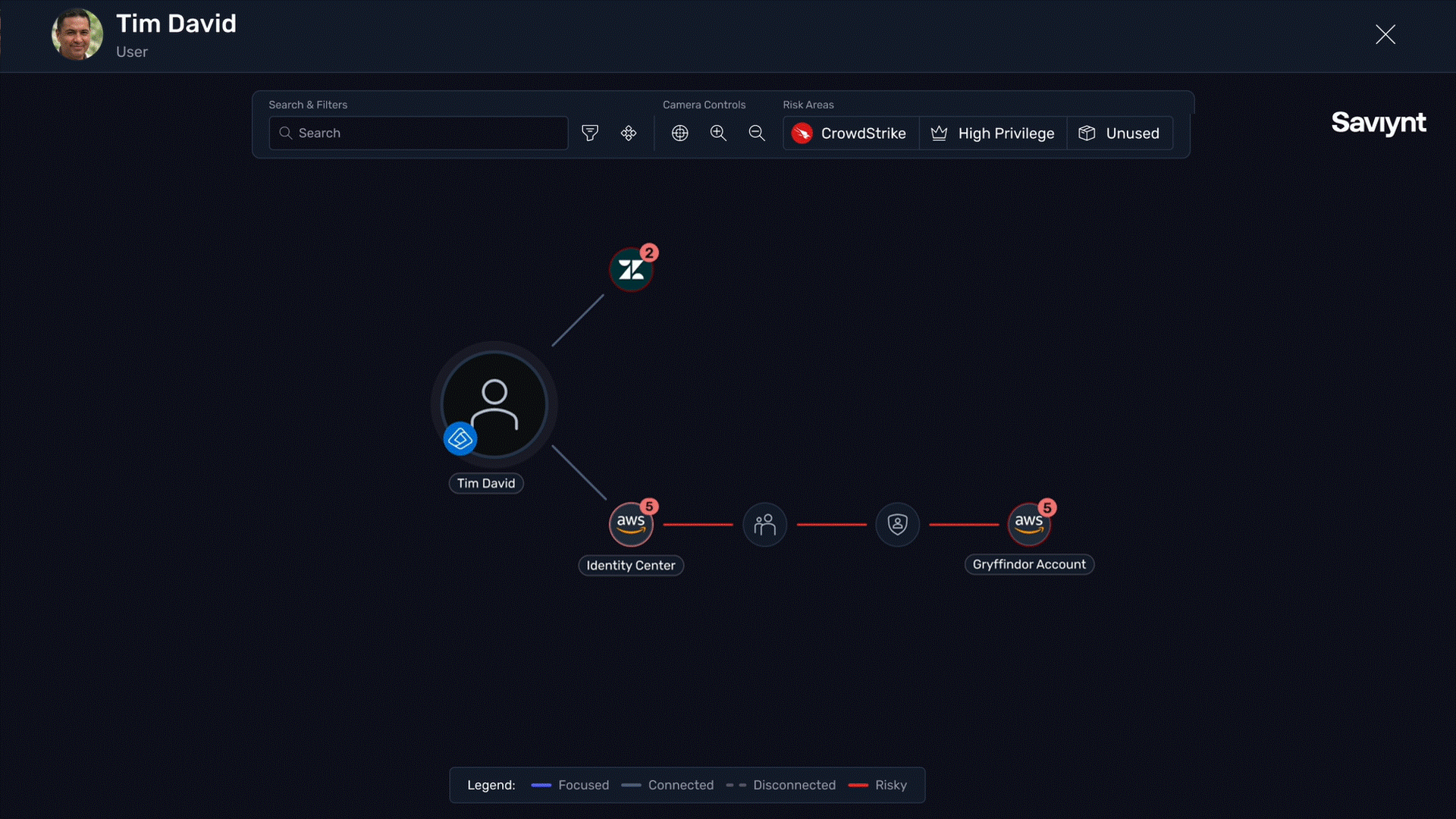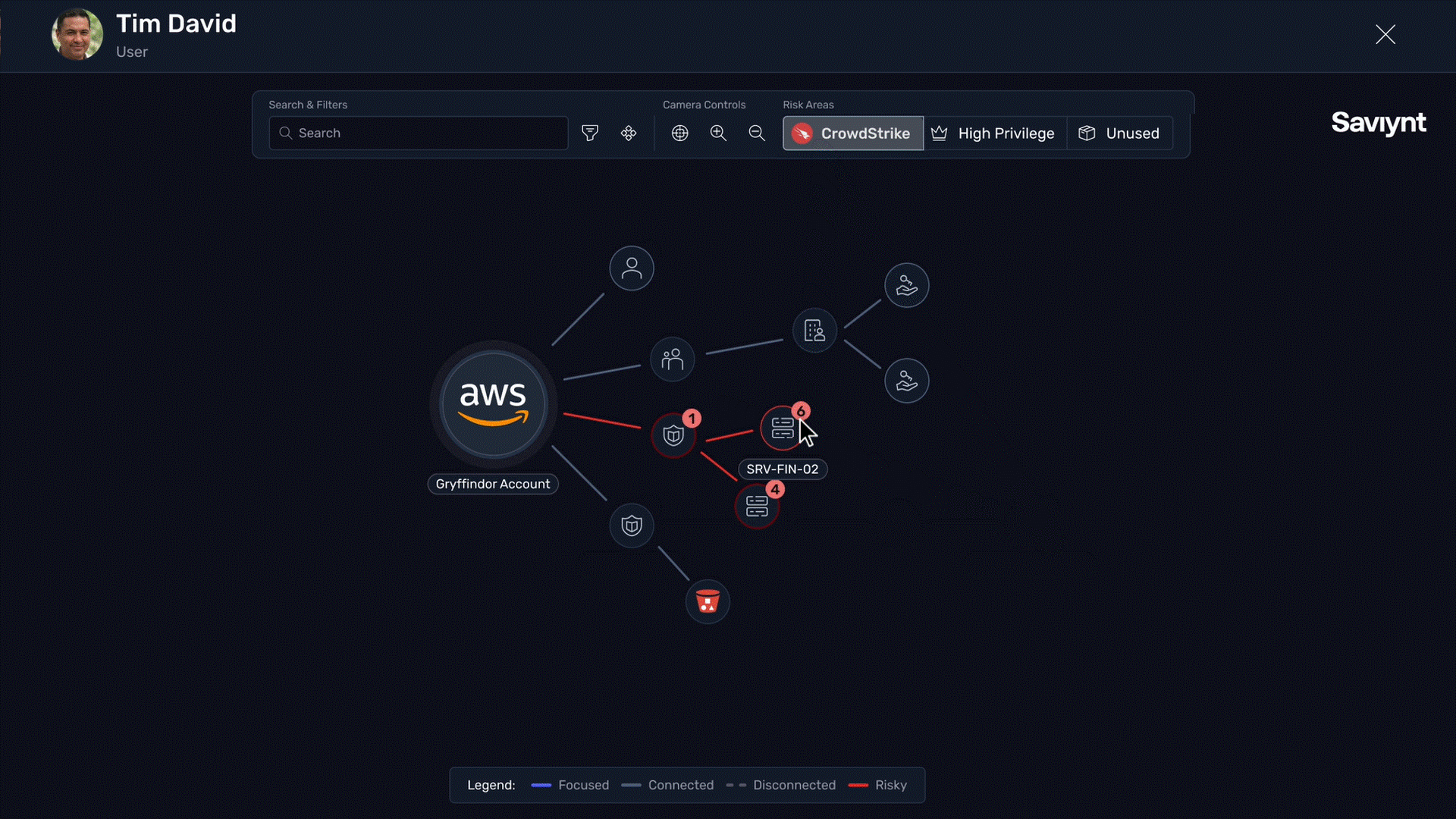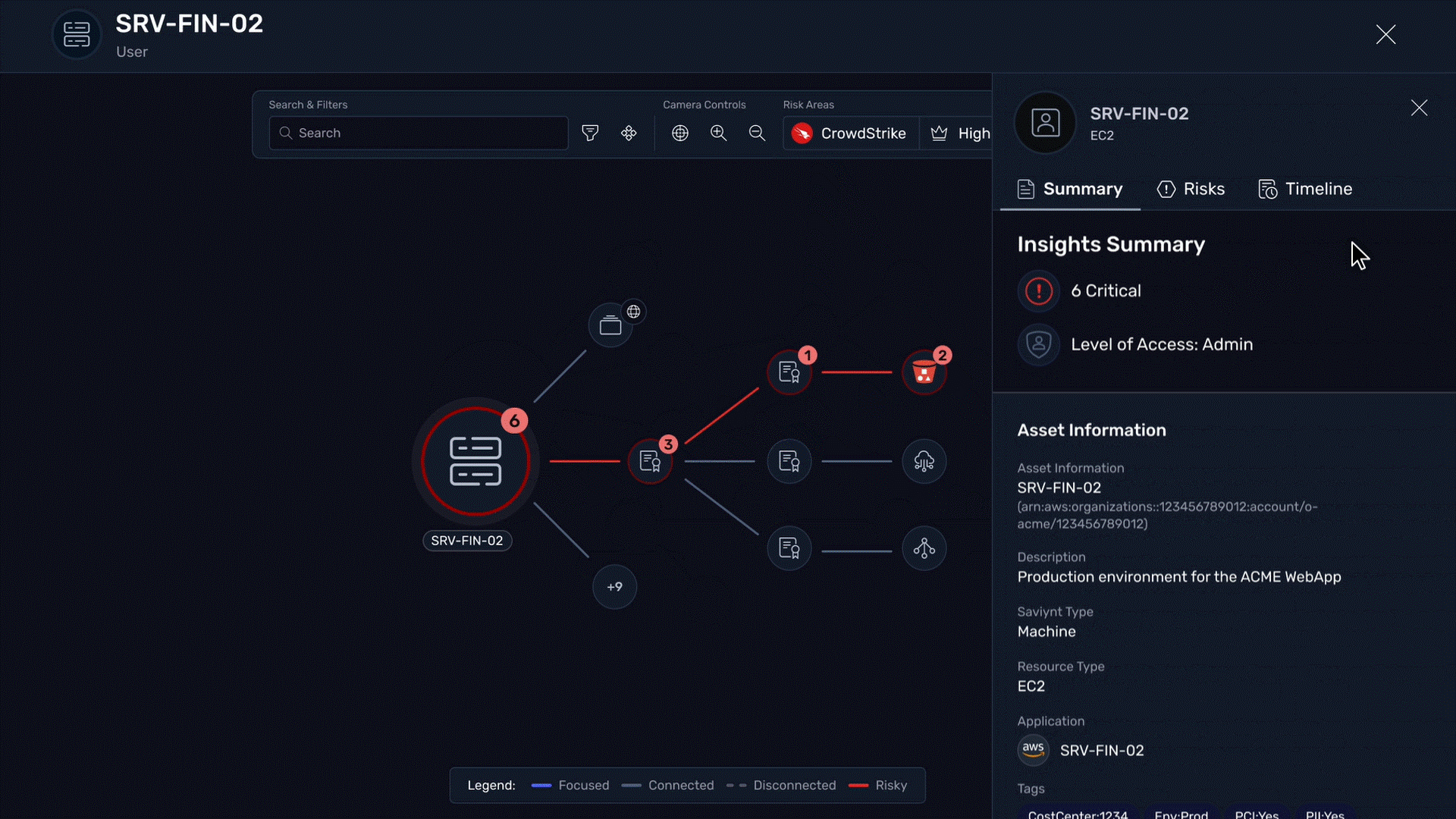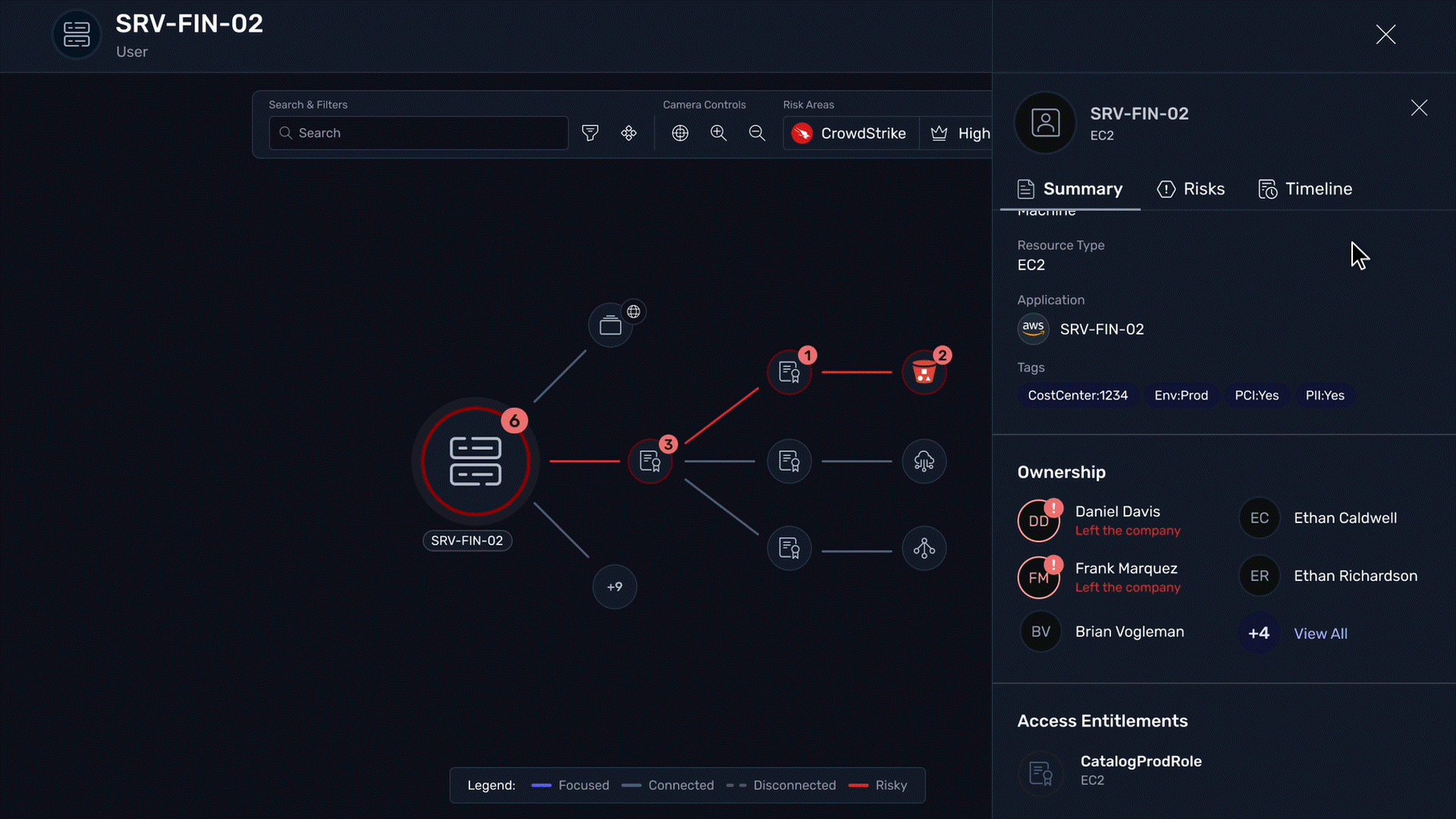
Use identity context from Saviynt to prioritize and respond to risks with precision
Instantly identify if compromised sessions involve privileged users, contractors or sensitive accounts with comprehensive visibility into roles, entitlements, and access history
Improve threat response with visibility into user risk profiles and role sensitivity











"Saviynt provides a single pane of glass to manage identity security across all our applications, data, and business processes."