Saviynt Blog
Stay up to date on the latest identity security news, research and more.
Content Type
Industry
Solutions


10 / 29 / 2025
Non-Human Identities Are the New Attack Surface: How Saviynt Brings Visibility and Governance for NHIs
READ BLOG
10 / 27 / 2025
Infrastructure as Code Meets Identity Governance: The Saviynt Terraform Advantage
READ BLOG


09 / 22 / 2025
Governing Mission-Critical Access: Saviynt is Writing a New Chapter in Airline Identity Security
READ BLOG
08 / 08 / 2025
SaviTalk Ep. 3: Visionary Product Leadership, The Story Behind Saviynt ISPM With Vibhuti Sinha
READ BLOG
06 / 18 / 2025
Saviynt Brings Innovation and Expertise to Identiverse 2025: Leading Identity
READ BLOG

05 / 28 / 2025
5 Ways to Solve Compliance Challenges with Saviynt’s Identity Security Platform
READ BLOG

12 / 02 / 2024
Saviynt named a leader in KuppingerCole’s Identity and Access Governance Leadership Compass
READ BLOG


12 / 20 / 2023
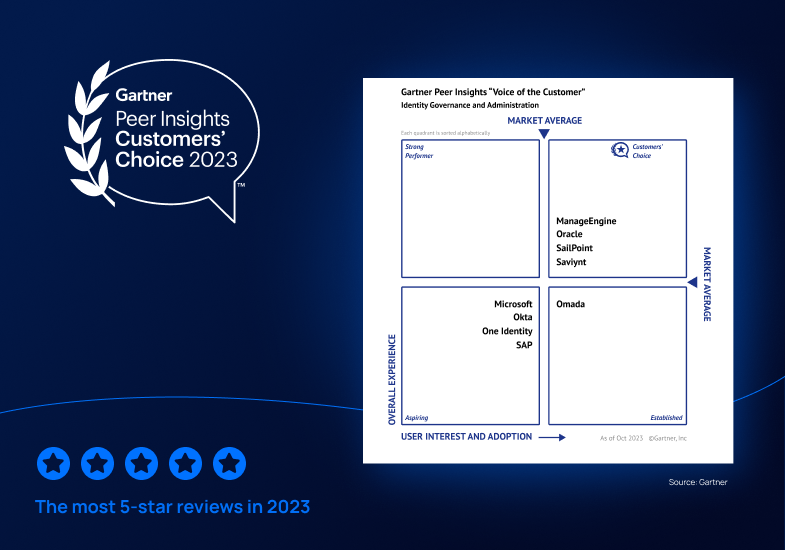
Saviynt a Gartner® Peer Insights™ Customers' Choice in Identity Governance and Administration—Three Years in a Row
READ BLOG




















12 / 13 / 2022
Saviynt EIC Scores 95/100 for Core Criteria in the 2022 Gartner® Solution Comparison for Identity Governance and Administration¹
READ BLOG




08 / 17 / 2022
3 Key IGA Modernization Must-Haves: All the Features, None of the Compromise
READ BLOG








06 / 09 / 2022
Gain Peace of Mind with Emergency Access Management & Out-of-the-Box Compliance Reporting
READ BLOG





03 / 22 / 2022
Ask the Experts: Solving Top Multi-Cloud Identity Management & Governance Challenges
READ BLOG









09 / 19 / 2017