A couple of weeks ago, we were delighted to have Visions Federal Credit Union from Endicott, NY, invite us to co-present with them on a virtual roundtable for the CUNA Technology Council. Visions was founded in 1966 by eight IBM employees with five dollars each. It was impressive to see that those 40 bucks have grown to over $5B in assets and 56 branches in three states serving 240,000 members.
The members who participated in our discussion are experiencing the daily challenges of transitioning to digital banking and member services. While every credit union is at a different stage in its cybersecurity maturity journey, they share similar concerns: how to manage the account provisioning process, protect every identity, increase efficiency, and fast-track access decisions. The FFIEC’s Automated Cybersecurity Examination Tool (ACET) is a great way to begin assessing your inherent risk profile, prioritizing next steps, and ensuring you get the most from an Identity Governance and Administration (IGA) program.
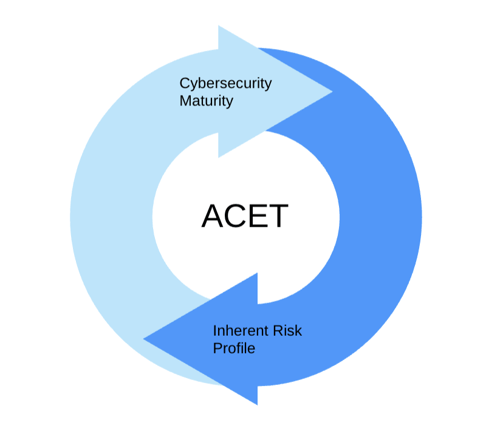 The Automated Cybersecurity Examination Tool (ACET) has two assessment modules to help identify where you are in your cybersecurity preparedness.
The Automated Cybersecurity Examination Tool (ACET) has two assessment modules to help identify where you are in your cybersecurity preparedness.
What is IGA?
At its core, IGA is a way to ensure that users have seamless application and infrastructure access to do their jobs without compromising compliance by over-provisioning access — or allowing access to remain in place once it’s no longer needed.
IGA can be viewed through the lens of the lifecycle of an identity. That identity begins with birthright provisioning, which is the least-privileged access required by a new joiner to the organization. Your IGA solution should be able to let users request access and have that access request be risk-evaluated so a manager granting the request doesn’t miss any unforeseen risk. This automation helps reduce management loads and reduce costs while improving security.
Why — and When — Should Credit Unions Start a Program?
As an identity’s lifecycle matures, the user may move between functions within the credit union, and it’s important to terminate any access that’s no longer needed. Likewise, when an employee leaves a credit union, access needs to be turned off since orphaned accounts are a prime target for cybercriminals. Setting up a user once — and forgetting about them — opens the door for audit findings, and that’s why an IGA system needs to be a true governance and management tool. Regular access reviews and certifications by management will prove the credit union is paying attention to identity access security. Predictive and detective controls that catch Separation of Duties (SoD) violations will dramatically reduce the overhead required to ensure compliance and make a credit union more risk-aware and proactive.
If your credit union is finding gaps in your ability to onboard users in a timely manner with least-privilege access — and you don’t have a clear line of sight to the management of identities over time — you’ll benefit from the provisioning and management capabilities of an IGA solution. If you struggle to identify and remediate potential or real SoD violations, it’s probably time to start implementing an IGA program. If you have third-party vendors and users who need access to sensitive systems and data, it’s definitely time.

Artificial intelligence in IGA solutions can continuously learn about your environment, provide access and provisioning recommendations, enable automation, reduce rubberstamping of certifications, and decrease decision times by 70%.
Achieving Cybersecurity Maturity Step by Step
At Saviynt, our approach to identity lifecycles is to Get Clean, Stay Clean, and Optimize.
The first step is to ensure that all user requests go into the IGA system with clean, consistent, risk-aware user data. You can establish risk rulesets to meet your specific needs, do SoD risk assessments, document any mitigating controls you have in place, and address any SoD risks in a prioritized manner.
Next, access review workflows make sure that over time, users have just the access that they need without any that they don’t. You can enable temporary emergency access when needed that automatically times out and removes access to eliminate orphaned accounts. These steps help to ensure that your credit union stays clean.
Finally, a sound IGA system will allow you to optimize your environment by utilizing advanced intelligence and analytics as you move through your cybersecurity maturity journey.
You don’t have to be a huge credit union to benefit from an Identity Governance and Administration program. As with ACET, you can start out with the basics and improve your cybersecurity maturity step-by-step while reducing your inherent risk profile. Ultimately, your members win by having a secure and efficient credit union.
Thank you to Visions Federal Credit Union for their partnership. We look forward to many more years of joint collaboration.






 The Automated Cybersecurity Examination Tool (ACET) has two assessment modules to help identify where you are in your cybersecurity preparedness.
The Automated Cybersecurity Examination Tool (ACET) has two assessment modules to help identify where you are in your cybersecurity preparedness.



