Identity security is no longer a back-office concern; it is a boardroom priority. Governments and industries across the globe are tightening compliance requirements around digital identities, privacy, and cybersecurity. Organizations that fail to keep pace face escalating risks end up with regulatory penalties and data breaches that erode customer trust.
Saviynt President Paul Zolfaghari underscores this urgency in his recent Forbes article, "Beyond Compliance: Mastering The Challenges of Identity Security Today", where he explores how modern enterprises can move from reactive compliance to proactive identity governance at scale.
It’s clear that to navigate today’s regulatory maze, enterprises must go beyond traditional IAM tools and embrace identity as a strategic enabler of compliance. Leading CISOs and risk leaders are shifting their approach from reactive controls to proactive, actionable continuous assurance frameworks that don’t just manage access but actively enforce policy, monitor risk, and generate real-time compliance insights across the entire identity lifecycle.
Saviynt’s Identity Cloud offers a compliance-driven, AI-powered identity security platform designed to meet modern regulatory mandates head-on. By unifying identity governance, access control, and privileged risk management, Saviynt empowers organizations to secure every identity while staying audit-ready and future-proof for both modern and hybrid enterprises.
- Addressing the Expanded Identity Regulations Needs with a Converged Compliance Framework
Challenge: Managing compliance across regulations like SOX, HIPAA, PCI DSS, and GDPR is complex due to scattered controls, changing requirements, and inconsistent enforcement across cloud and on-prem environments. Security and compliance teams are stuck in reactive mode, manually chasing audit trails across fragmented systems, leading to burnout, missed violations, and rising regulatory risk. Without unified enforcement, organizations face blind spots, insider threats, and compliance costs that drain strategic focus and erode trust.
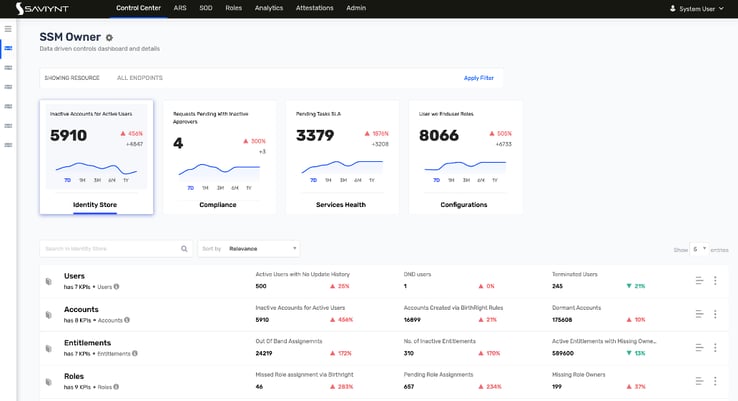
Solution: Saviynt delivers a Unified Compliance Framework with pre-built, customizable control templates, enabling business teams to manage compliance without coding. Pre-mapped to regulations like SOX, PCI DSS, GDPR, FedRAMP, and others for instant use.
Key Technical Capabilities:
- Dynamic control libraries pre-mapped to industry standards such as SOX, PCI DSS, GDPR, FedRAMP, and others
- Centralized audit dashboards streamline evidence collection for compliance reporting
- Cross-environment and cross application policy enforcement across cloud and on-prem
- Automated audit trails with visual compliance
- Managing the Identity Explosion (Humans & NHIs)
Challenge: Proliferation of both human and non-human identities (NHIs) like bots, APIs, and service accounts, create a sprawling attack surface. This increases the risk of credential theft, privilege escalation, and breaches, leading to costly incident response and regulatory fallout.
Solution: Saviynt solves the identity explosion challenge by providing a unified, cloud-native platform that governs both human and non-human identities across hybrid and multi-cloud environments. It centralizes access control, automates identity lifecycle management, and enforces continuous compliance through intelligent policy, risk-based analytics, and just-in-time provisioning. This enables organizations to secure every identity, minimize risk, and meet evolving regulatory demands with agility and scale.
Technical Capabilities:
- Unified Identity Governance for human and non-human identities (bots, APIs, service accounts)
- Automated Joiner-Mover-Leaver (JML) Processes for lifecycle management
- Just-in-Time (JIT) Access Provisioning with risk-based policies
- Continuous Compliance Enforcement using intelligent policy and analytics
- Role & Policy-Based Access Controls (RBAC & ABAC) for fine-grained governance
By addressing the identity explosion head-on, Saviynt empowers organizations to move beyond fragmented tools and manual processes. Its intelligent, unified approach ensures that every identity whether human or machine is governed with precision, granted only the right access at the right time, and continuously monitored for risk.
- Enforcing Zero Trust with Just-In-Time (JIT) Access
Challenge: Legacy access models are inadequate for hybrid, multi-cloud environments. Organizations rely on always-on privileges that increase the risk of lateral movement, insider threats, and credential misuse. Static entitlements become outdated quickly, leading to excessive access and audit failures and it harder to enforce least privilege, especially in dynamic, multi-cloud environments. The result? Higher breach risk, compliance gaps, and operational inefficiencies
Solution: Saviynt’s Identity Cloud enforces zero trust by delivering just-in-time, time-bound access through integrated IGA, PAM, and AAG. Access is granted only when needed, based on contextual risk signals, and continuously verified to eliminate standing privileges and minimize attack surfaces.
Technical Capabilities:
- Integration with PAM tools and cloud providers
- Dynamic role elevation and automatic revocation
- Zero standing privilege management and response triggers
Saviynt operationalizes zero trust by enforcing least privilege at every access point, reducing risk exposure.
- AI-Driven Identity Governance & ISPM
Challenge: Manual identity processes are error-prone and reactive, often leading challenges include managing excessive or unused access, detecting sensitive access violations, and governing non-human identities and end up delaying responses to emerging threats. They struggle to keep up with the pace of dynamic environments, increasing the risk of unaddressed vulnerabilities and complicating audits due to inconsistent or outdated access records.
Solution: Saviynt’s AI-driven Identity Governance capabilities leverages machine learning for dynamic access recommendations, automated role recommendation, and intelligent certification workflows. Saviynt’s newly released Identity Security Posture Management (ISPM) integrates actionable analytics and real-time risk assessments, continuously identifying identity-related vulnerabilities, policy violations, and compliance gaps. Automated peer access reviews enable actionable insights, mitigating insider threats and reducing attack surfaces.
 Technical Capabilities:
Technical Capabilities:
- Automated Role recommendation and access modeling
- Intelligent Peer Access Reviews
- Risk score driven Access Certification
- Continuous Compliance Reporting & Auditing
With AI, Saviynt automates compliance and elevates security posture management across the identity ecosystem.
- Out-of-the-Box Controls & Actionable Analytics
Challenge: Time-to-value is critical, and many organizations struggle with deploying comprehensive identity controls efficiently. Without relevant, real-time data insights, security teams struggle to prioritize threats and make informed decisions. This results in inconsistent policy enforcement, missed compliance requirements, and undetected security gaps
Solution: Saviynt accelerates time-to-value by providing Actionable Analytics and Control Center, enabling real-time decision-making and rapid deployment of identity controls. Its out-of-the-box compliance rulesets streamline regulatory adherence, while centralized risk dashboards offer real-time visibility into security risks and automated alerts, ensuring proactive management of identity governance.
Technical Capabilities:
- Segregation of Duties simulation and impact analysis
- Drill-down reports and control efficacy views
- Integration with ServiceNow, SAP, Workday, and other ERPs with out-of-the-box rulesets facilitates
Saviynt’s Identity Cloud enables organizations to automate and streamline identity management across hybrid environments, providing seamless integration with on-premises, cloud, and SaaS applications at high velocity. It scales governance to cover all identities and applications, ensuring dynamic, policy-driven compliance enforcement across complex infrastructures. Through continuous innovation and real-time updates, Saviynt empowers organizations to stay ahead of evolving regulatory requirements, rapidly adapting to compliance changes while ensuring robust, auditable security controls at scale.
Learn more by requesting a demo today.






 Technical Capabilities:
Technical Capabilities:

.jpg)