Reduce Third-Party Security Risks by Creating a Single System of Record
As we discussed in the first part of this series, the majority of companies don’t know how many third-party relationships they have, let alone which users have been granted access to corporate applications and sensitive data. That’s a problem.
It also shouldn’t come as a surprise that shadow IT has grown significantly as line-of-business leaders deploy SaaS software solutions to solve departmental use cases. These applications require access to, or integration with, core ERP solutions and data warehouses so that third parties can do their jobs.
If companies admit they don’t track third-party relationships, it is a fair assumption that they have little to no visibility into the third-party user access or the risks those users may pose. To make matters even worse, most third parties also have their own business-to-business relationships. These relationships, called “nth party” relationships, introduce another layer of complexity – and risk.
Let’s examine a real-world scenario where these types of risks were exploited. In the now-infamous Target attack, bad actors gained access to Target’s data by exploiting an nth party relationship with a legitimate third-party service provider. The data breach, which happened in 2013 and exposed the credit and debit card data of some 110 million customers, still reverberates with security professionals today.
The good news? There is an ongoing effort between companies and their third-party counterparts to improve security posture and provide better access control. If your organization is on the journey, we have outlined five key steps you can take to consolidate third-party relationships and close vulnerable security gaps.
1. Create a System of Record
Establishing an identity lifecycle management program for third parties begins with consolidating these relationships into a system of record to capture the pertinent information about the organization before granting access.
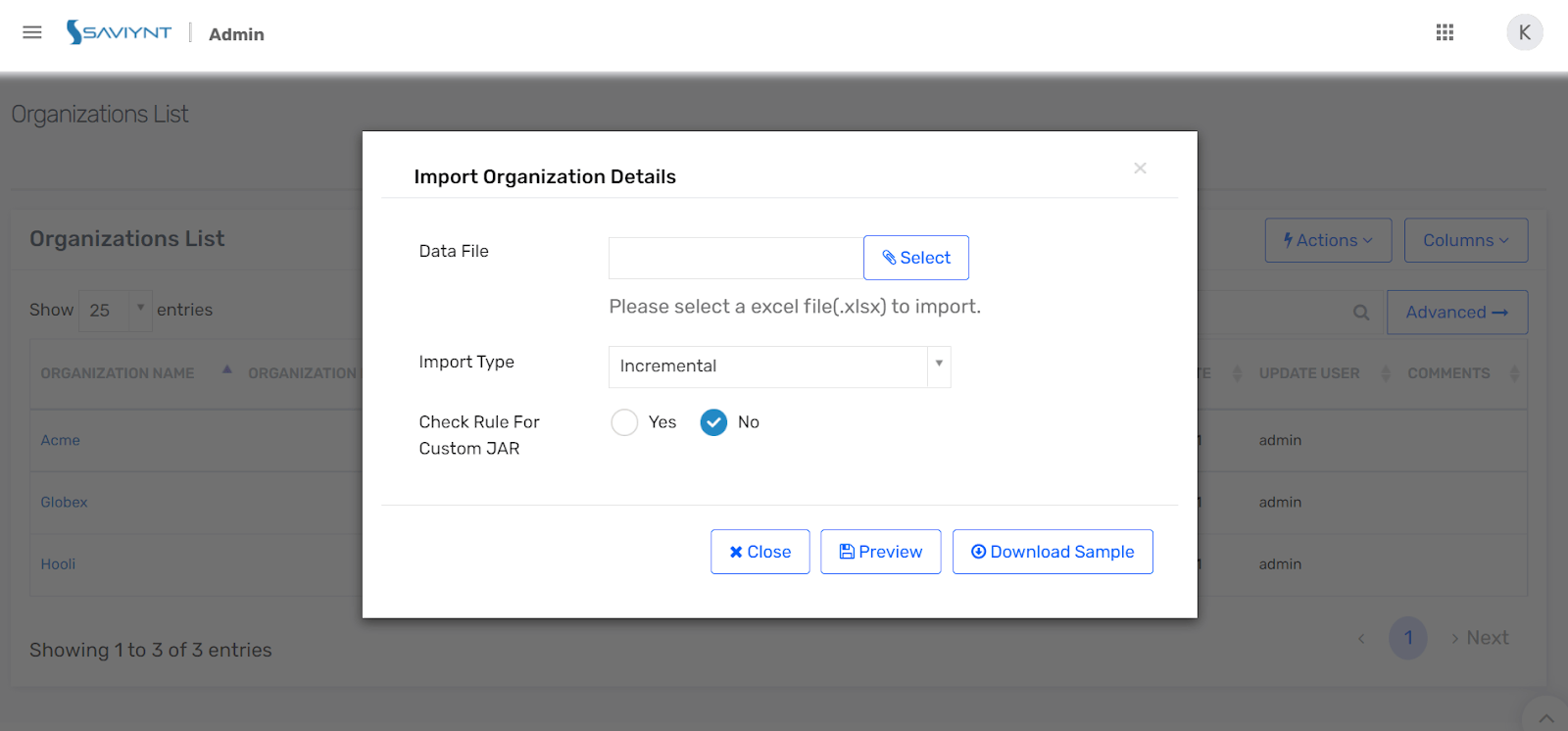
Saviynt provides multiple ways to populate your third-party system of record.
This consolidation requires a cohesive effort between department heads and the identity access management team or IT security team. It’s helpful to have executive sponsorship from the CISO or your internal audit leader to raise awareness and ensure that departments give the project the attention and resources it deserves.
Begin by gathering a list of all current third-party relationships. If you’re unsure where to start, reach out to your procurement or accounts payable team — since many of the third parties have contractual relationships or monthly invoices being paid out.
2. Establish a Sponsor for Each Relationship
Next, you’ll need to select a sponsor inside the company to manage communications with each vendor, contractor, or service provider. Remember, depending on your industry or use case, not all third parties will have a contractual relationship. Consider volunteers, student interns, IoT devices, and even bots. Every identity needs to be captured in the system of record and assigned to an administrator for future access reviews and certifications. This initial step is certainly the most time-consuming and challenging— but remains absolutely necessary as you build your program’s successful foundation.
3. Add Contractual Requirements for Security and Disclosure
We recommend reviewing your contracts to ensure they address any third parties’ shared security responsibilities, such as promptly administering identity access for their joiners, movers, and leavers. You should also ensure they are required to disclose breaches quickly, so your organization can take quick action to reduce the potential fallout.
4. Check for Orphaned Accounts
Once your company has consolidated its third-party relationships, the next step is to verify that there are no orphaned identities with access that should have been revoked. Orphaned accounts are prime targets for hackers since they are rarely monitored or reviewed for accuracy.
5. Segment Users By Role and Access Needs
Working with your designated third-party administrators, the identity and access management team can segment the users based on their roles and access needs — starting with the concept of least privilege. Once you’ve organized the users, you can onboard them into the system of record using manual entry, data uploading via spreadsheet, or a federated system.
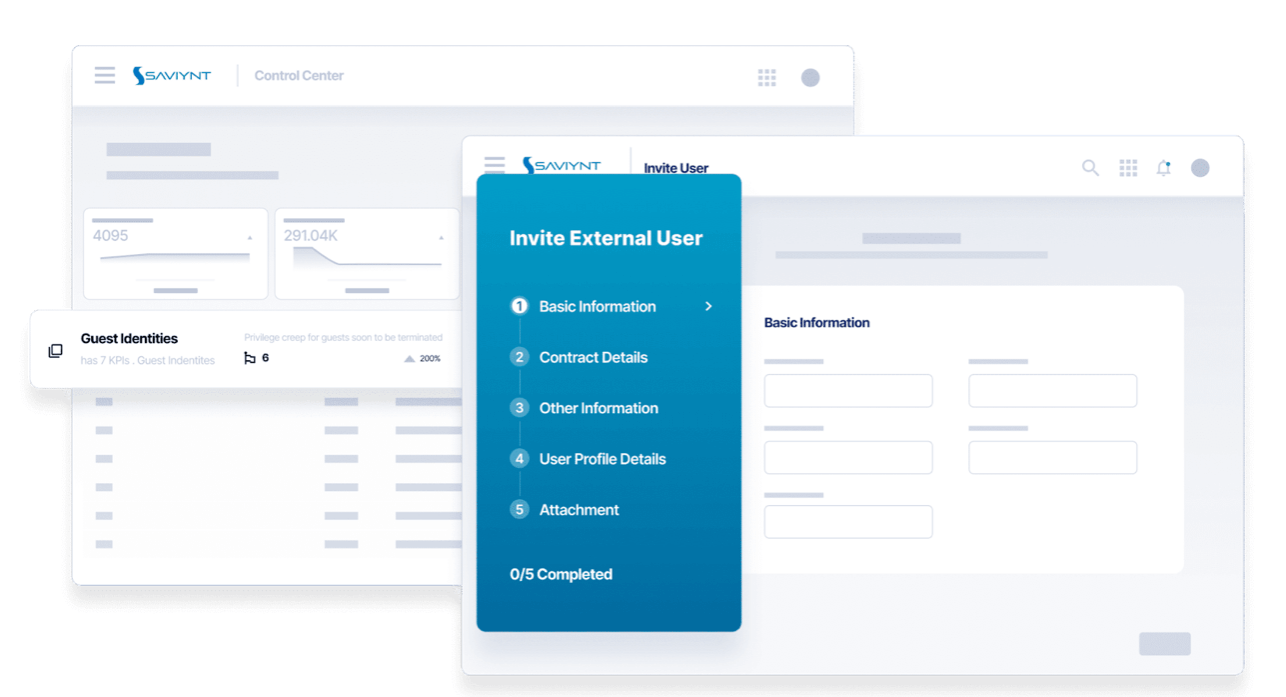
Saviynt’s automation capabilities help organizations quickly onboard third-party users securely.
Enable Zero Trust and Least Privilege Across Your
Entire Workforce
We believe the ultimate goal of any third-party access governance is to enable Zero Trust and least privilege across your extended workforce. Consolidating your third-party workforce and systems is a critical first step to program success.
In future blog posts in this series, we’ll cover why delegating admins for your third-party relationships is so critical to your overall security posture, and how automation can improve the efficiency of third-party provisioning.











