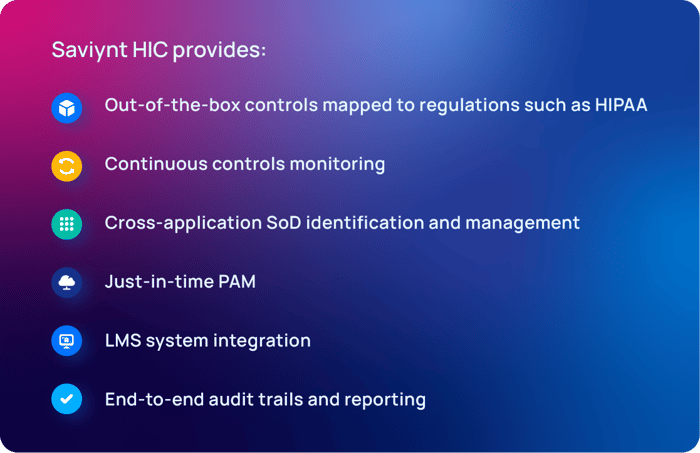
CIPs Deliver Controls Mapped to Regulations
CIPs deliver out-of-the box controls within a unified controls framework cross-mapped to essential regulations (HIPAA, PCI DSS, etc.), standards, and control types (CIS, NIST CSF, etc.) to provide additional safeguards to restrict access to PHI and other sensitive information. Regular and elevated access can be monitored for usage and control violations, even if gained through a backdoor. Custom access controls can also be analyzed based on user type. For third-party identities, access is able to be deprovisioned automatically when contracts or employment status ends.
Centralizing identities and identity governance on a converged platform helps take better advantage of the controls needed to comply with a wide variety of regulations. By mapping controls to various regulations, you can align processes and program management to ensure processes are followed and monitored, and that anomalous activities can be identified for quick and accurate remediation.
Ensuring staff members have taken and passed their HIPAA training, annually and during onboarding, is a necessity. CIPs that integrate your learning management system (LMS) with your identity security program ensure employees gain access to the critical systems they need. Integration allows automatic access to resources only upon completion of required training to maintain HIPAA compliance.








.jpg)