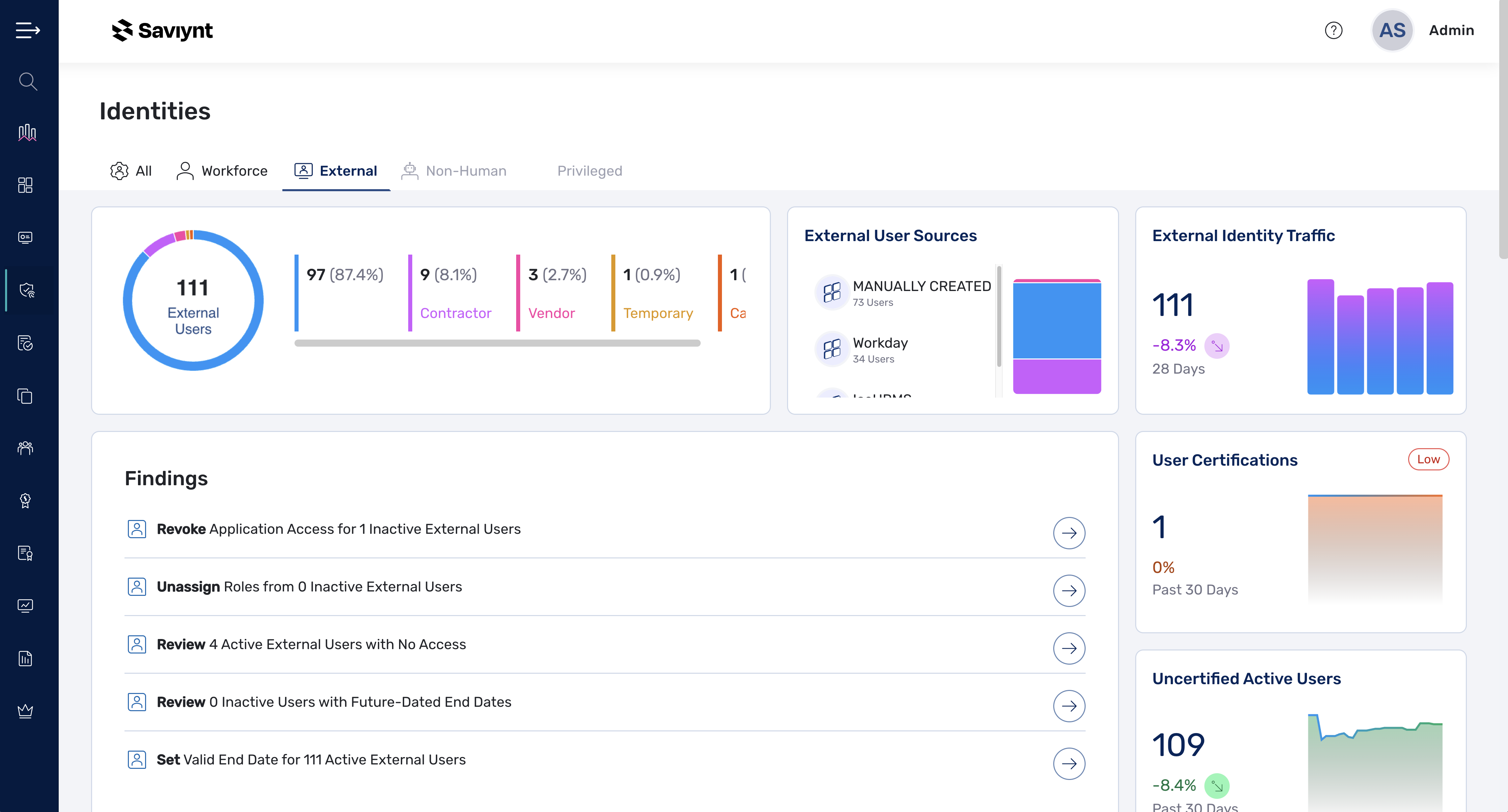
Ensure external users have only the access they need to do their job, for the right amount of time, right when they need it.

Identify the external users already present in your organization and bring them under management to ensure visibility and security.
Listing of external users
Easily identify external users anywhere in your system with their current status and entitlements.
Classification rules
Organize existing external users to ensure they are included in roles, rules and analytics that apply.
.png?noresize&width=327&height=177&name=Inventory%20External%20Users%20(1).png)
How many vendors have the keys to your kingdom? Use this guide to inventory, onboard, and provision with confidence.

Enforce holistic identity security policies for internal and external users, across cloud, on-prem, and hybrid environments without straining your admins or users.
.png?noresize&width=327&height=177&name=IGA%20dashboard%20(4).png)
.jpg?noresize&width=2119&height=1415&name=iStock-1299972215%20copy%20(1).jpg)
.webp?noresize&width=1702&height=1174&name=uwa-bg%20(1).webp)