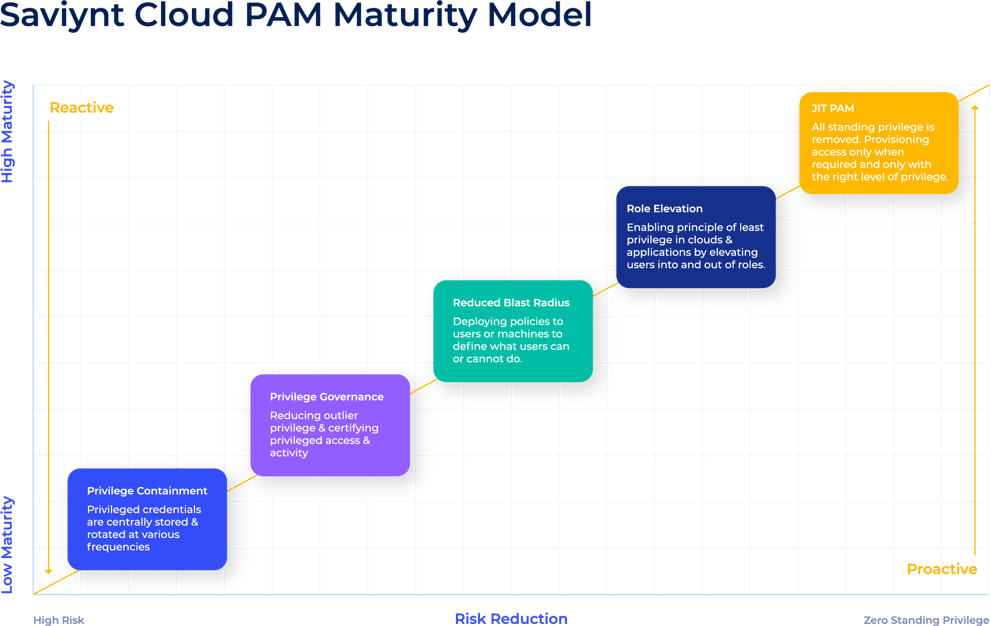
Advancing to Proactive Controls
Reducing The Impact of a Security Breach: Levels 3 and 4
Organizations can reduce the blast radius of a breach by removing standing administrative privileges and defining what permissions are needed for what systems — and the duration of those permissions. From there, they should extend least privilege access for human and machine identities to applications and cloud services by provisioning users in and out of elevated roles as needed.
In a traditional PAM world, getting to this stage is ultimately about deploying agents and capturing events that happen over time on desktops, servers, and other systems. Role elevation rules will need to be created, tested, and managed by staff resources. At the end of the day, however, agents aren’t really designed for cloud or ephemeral workloads, and many organizations only roll it out to a few critical apps.
With Saviynt’s identity-based, agentless Cloud PAM solution, our customers can avoid lengthy rule-creation cycles and advance to role elevation more easily. Using our identity connectors, we actually delete roles from a user’s account and remove excessive, “always-on” access in real time.
Role management originally comes from the IGA world. This is why many traditional PAM vendors are now trying to move into identity management. As a leading IGA vendor, Saviynt has more than a decade of experience developing the industry’s only Identity Warehouse, which houses every identity — human or machine and provides granular insights on all identities from a single repository.