Four Strategies for Enhanced GRC Capabilities
From accounts receivable to payroll to line of business applications, companies rely on SAP applications in the cloud. Whether you use a few or a full suite of these critical apps, you also have to manage and monitor who has access to them—and how that access is being used. If not, your sensitive customer information, company financial records, and employee data could easily get into the wrong hands.
SAP offers its own Governance Risk and Compliance (GRC) tool that can give you visibility into Separation of Duty (SoD) violations in your SAP apps. What SAP GRC can’t give you is visibility into these same risks across your Oracle, Oracle Financials, Salesforce, or any of your other non-SAP applications. If SoD violations are slipping through cracks there, you’re also inviting in breaches, business disruptions, and significant compliance penalties.
You need a user-friendly way to control and manage identity and access controls across the entire enterprise — not just within your SAP footprint. You need an easier way to complete access reviews and stay compliant. But you don’t want to rip out your SAP GRC solution and reinvent the wheel.
Unfortunately, there hasn’t been a good option on the market. Until Saviynt.

Even if your organization has already invested a lot of time, skills, and money into implementing your rulesets and mitigating controls into SAP GRC, Saviynt offers four configurations that allow you to enhance and extend your GRC capabilities beyond SAP—while preserving the core benefits of your original investment.
Let’s look at how Identity Governance and Administration (IGA) and Application Access Governance (AAG) can enhance SAP GRC, and improve your cross-application governance—all while avoiding the hassle of stitching together multiple solutions.
4 Ways to Connect SAP GRC With Saviynt
Saviynt offers a range of options for SAP customers who want to retain some or all of their SAP GRC-based management. Each of these approaches delivers better compliance, better user experience, and better return on investment—all with a lower total cost of ownership.
Option 1: Enterprise Approach to Risk Management
In this setup, Saviynt IGA imports the rules and controls that you’ve already set up in SAP GRC, and fully manages ruleset governance, mitigating controls, and any of the detective reports from risk simulations. This delivers an enterprise-wide view of all SOD and access control risks and violations across SAP and Non-SAP Applications.
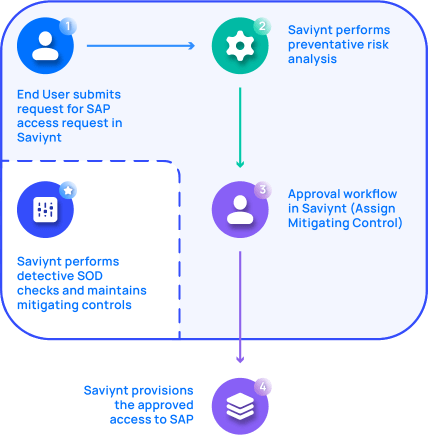 Saviynt can run preventative SOD analysis for SAP and Non-SAP systems.
Saviynt can run preventative SOD analysis for SAP and Non-SAP systems.
Option 2: Saviynt Enterprise SOD Engine for Preventative Risk Analysis
While both options 1 and 2 allow you to maintain your current SAP risk management process, option 2 keeps your rulesets and mitigating controls in SAP GRC. Saviynt sets up a synch pattern where AAG runs the preventative SOD analysis for SAP and Non-SAP systems and, similar to option 1, delivers risk analysis capabiities in IGA such as access requests, detective reports, and risk simulations.
Option 3: Leverage SAP GRC
In this configuration, SAP GRC houses the rules and mitigating controls, and Saviynt initiates the access request and passes it to SAP GRC. SAP GRC runs the risk analysis, simulations and detective reports and provisions to SAP. The results are returned to Saviynt IGA for last-mile provisioning.
Option 4: Integrated Solution
Finally, in this instance, SAP GRC houses rules and mitigating controls, and access requests are kicked off in Saviynt IGA before getting passed to SAP GRC. The key difference here is SAP GRC completes the last mile provisioning and sends a notification to IGA when the process is complete. Risk simulations and detective reports are also executed within SAP GRC.
Choosing The Right Access Control For Your Organization
The benefits of options 1 and 2 are clear: gain the full user lifecycle management features of Saviynt IGA alongside complete SAP license management functionality. If you have SAP licenses provisioned that you don’t really need, this gives you the flexibility to remove redundancies: simply turn them off and save money.

Rather than the complexity of multiple solutions with multiple dashboards, you also get a single HR source of truth that can drive technical rules like birthright and peer-group analysis. Saviynt’s full Control Center capabilities (with over 1200 different reports for compliance and operational controls) delivers audit trails for your joiners, movers, and leavers, as well as SOD and sensitive access reporting in a single pane of glass—all through your AAG license.
If your team includes dyed-in-the wool SAP GRC users, options 3 and 4 allow you to maintain your current SAP GRC risk management process and work the way you always have. While this may require more configuration, these last two options deliver a standardized access provisioning approach to all applications—SAP and non-SAP. You also get an enterprise-wide audit trail through a single pane of glass through your Saviynt IGA license.
How Application Access Governance Enhances and Extends Your SAP GRC Capabilities
Saviynt’s vision for identity centers on clearing away the multi-tool clutter and converging all capabilities in one unified platform. Adding AAG to your SAP GRC infrastructure can help you achieve a level of access control and performance that would normally require a far bigger investment:
User Experience. One unified interface means your teams only have to learn one technology—no toggling between different systems. All administration processes can happen in a centralized management console that gets you up and running quickly.
- Compliance. Got applications with complex security architecture? No problem. Saviynt’s Control Exchange provides out-of-the-box SoD rulesets for all of the major applications, including SAP, Epic, Oracle EBS, Oracle Cloud, Workday, Microsoft Dynamics, PeopleSoft, and Infor, to name a few. You can customize these, import any existing SoD rulesets that you have, or create new ones from scratch.
- Visibility. While Other GRC solutions can address a single application (or provide coarse-grained visibility across a few applications) AAG provides fine-grained visibility that can identify SoD violations across multiple technologies, regardless of whether the user is privileged or a third party.
- Automation. If you’re not clear on how a user’s role and access will impact your SoD risks, Saviynt replaces manual guesswork with real-time monitoring, access request and approval workflows, and role-based access controls. Automate access certification and remediation, policy enforcement, and risk assessments so you can stay on top of your GRC responsibilities, reduce the risk of data breaches, and avoid costly non-compliance fines.
10 Questions To Better Application Security
How well are your current application safeguards performing? Our 10-minute 10-question Assessment Tool can give your environment a quick check-up and show you exactly which features you need, which ones you don’t, and where you need to improve.
Or, take a deeper dive into standardizing GRC access control requirements across your enterprise. Watch our webinar to learn more about getting the most out of your SAP GRC solution.






 Saviynt can run preventative SOD analysis for SAP and Non-SAP systems.
Saviynt can run preventative SOD analysis for SAP and Non-SAP systems.



