No Matter How Complex Your Application Environment, AAG Controls Help You Catch More SoD Violations
On average, companies use 34 SaaS apps in their enterprise. Each app correlates to hundreds of functions, potentially to thousands of people. But it only takes one wrong role with the wrong type of access to create a toxic combination.
Access sprawl is real — 80% of data breaches result from excessive application access and access to sensitive data. Without automated controls, your security team is mired in a time-consuming process with poor visibility, leaving the door open to breaches, business disruption, and significant fines.
Regulations like Sarbanes Oxley (SOX) or the Graham-Leach-Bilely Act (GLBA) don’t just place stiff Separation-of-Duties (SoD) penalties on companies — they can also lead to whistleblower lawsuits if employees see lax controls with no action taken. To stay compliant — and out of court — internal auditors and Boards of Directors must ensure your SoD controls are operating effectively.
When your sales orders are performed in Salesforce, and Accounts Receivable is maintained in Oracle EBS — how do you maintain a healthy SoD between the two apps?
Let’s look under the hood to see how out-of-the-box rulesets, prevent-and-detect analysis, and fine-grained controls operate in your day-to-day workflow. And once a risk is detected, we’ll see how Saviynt ensures quick remediation.
Out-of-the-Box Rulesets Simplify Prevention and Detection
Every enterprise has a long list of business functions that includes “rulesets” or entitlements that allow users to access applications. As we discussed in the first blog in this series, basic SoD controls detect conflicts within these functions. They prevent users who hire vendors, for example, from being able to pay those vendors, or ensure that employees who fill out timesheets aren’t also able to approve them.
But each ERP application speaks a different security “language.” SAP’s security model is speaking one language, and Oracle another. Understandably, when you’re provisioning many different functions across different apps with different rulesets, detecting SoD violations gets tricky.
Most organizations rely on point solutions or time-intensive, burdensome spreadsheets for in-scope apps. And too often, new users are put on hold while admins follow outdated or manual procedures to hunt down access approvals from other team members.
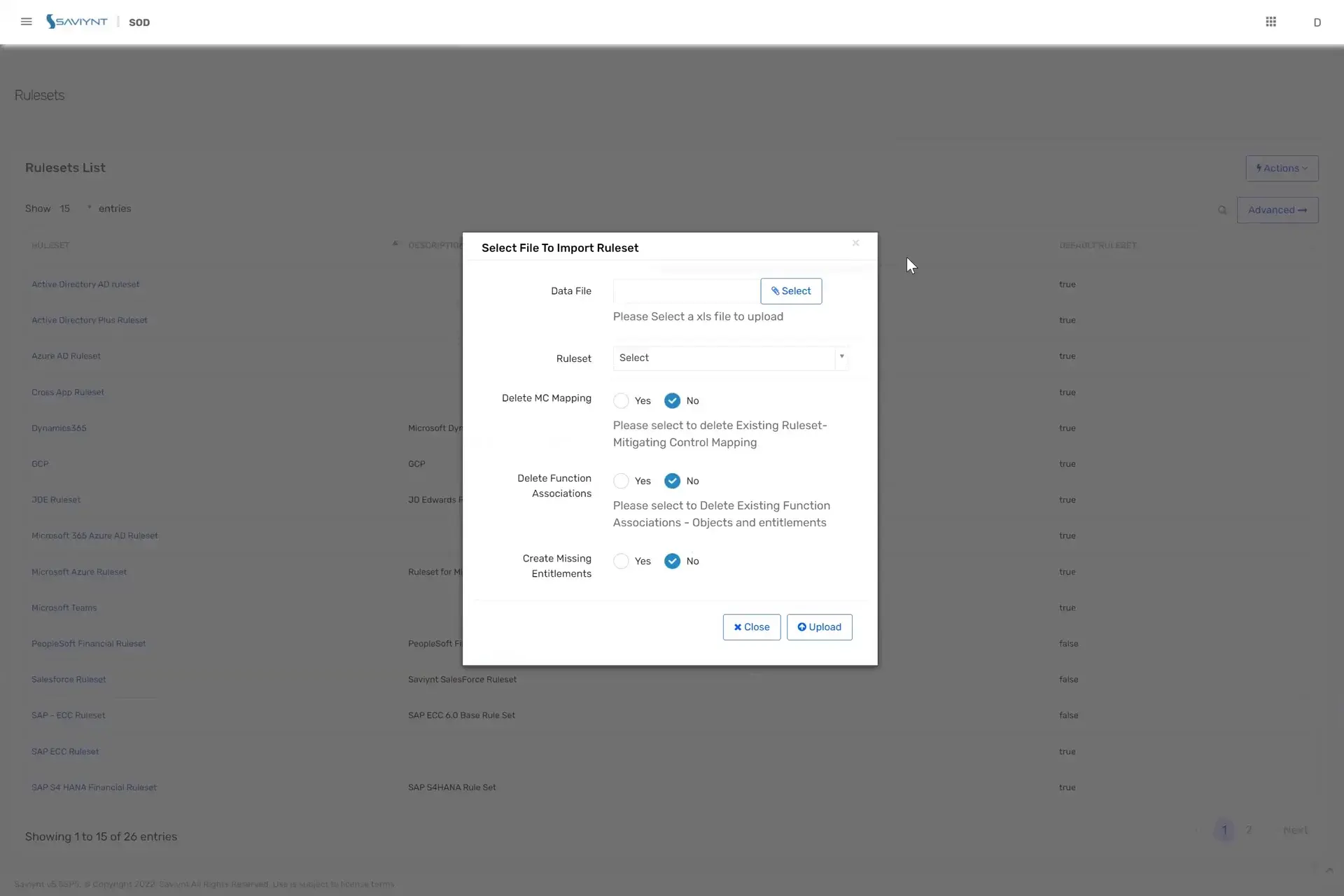
Demo 1: Out-of-the-box SoD analysis allows simplified identity management.
Saviynt’s intuitive workbench comes preloaded with built-in rulesets for a long list of ERP applications. These out-of-the-box SoD management controls allow for deep integration with all of your SaaS or on-prem applications.
In the SoD module, you can upload and view rulesets for different applications and easily view a description of what the risk entails. You can also bundle hundreds of functions together to define risk. Or, create your own ruleset per your organizational needs, job titles, or other factors, removing risks and entitlements that are not in scope.
Plus, SoD assessments can be run in real time. You can easily detect all the violations in the system — including users added before SoD solutions were even in place — along with priority, description, and the user associated with it, right down to the most fine-grained fields possible.
When and if a user makes a problematic access request, preventative SoD analysis detects anomalies and can stop the problem before it starts. Risks can then be auto-rejected, flagged, or escalated for further levels of approval.

Fine-Grained Controls Go Deeper to Score SoD Risks
Some solution providers can get you partly compliant by assessing SoD at the role level, but if your organization is adding custom roles or functionalities, this level of risk analysis won’t be enough for auditors.
Effective SoD controls must be “fine-grained” — equipped to identify risks where transactions for critical tasks occur: deep in your applications at the page, function, TCode, Auth Object, or privilege level. Coarse-grained Governance Risk and Compliance (GRC) solutions simply can’t detect violations at this level.
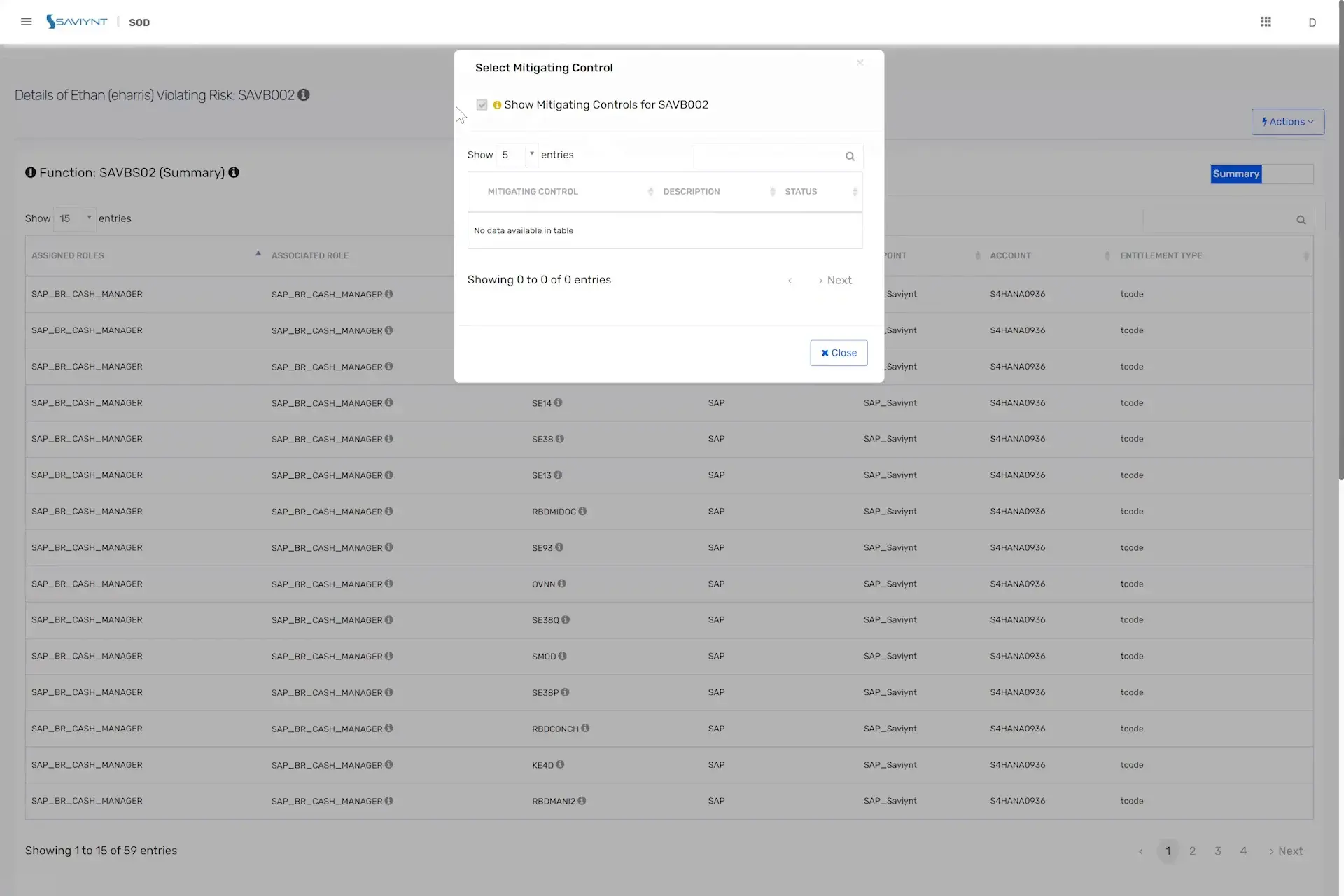
Demo 2: AAG’s easy-to-use interface helps you move from risk identification to risk remediation with just a few clicks.
Once you’ve found these potential violations, security teams and auditors can confront or accept a wide variety of risks using AAG’s extensive library of user-friendly controls. Our risk scoring tools include not only static and inherent risk scores assigned to an account, but also dynamic risk scores derived from usage, behavior analytics, peer group analytics, and data gathered from external systems.
Whether on the ground, in the cloud, or in a hybrid environment, you’ll be equipped to run automatic mitigation to address suspicious activities, prioritize remediation, and prevent breaches — all while preserving the time and productivity of your security teams.
In the next installment, we’ll show you how AAG reduces compliance headaches with automated certifications and cross-application risk reporting.