Identity Governance & Administration (IGA)
Control identity risk without compromising productivity.
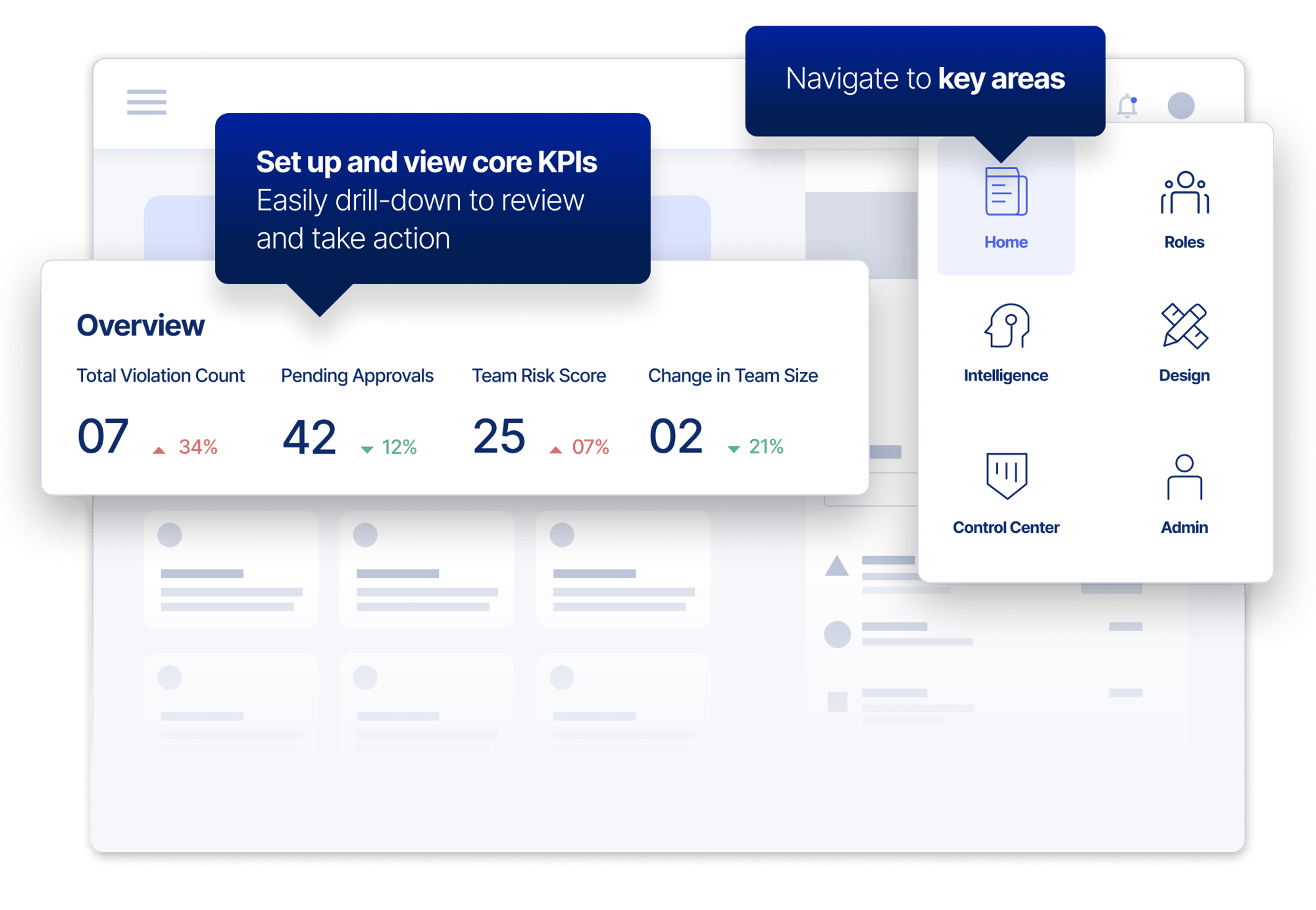
Simple To Use, Fast To Deploy
Give users seamless access to the applications and data they need, wherever and whenever they work
- Protect your business from attack.
- Stay ahead of compliance.
- Enable zero trust.
Identity Governance. Simplified.
Protect Every Identity
Manage all human & machine identities through a single control plane.
Increase Efficiency
Unify identity workflows with a multi-channel and frictionless user experience.
Fast Track Access Decisions
Reduce decision times by 70% & automatically approve low-risk access or flag reviews.
Accelerate Zero Trust Adoption
Grant just-in-time access for all access— not just privileged users — and achieve zero standing privilege.
Gain the Cloud Advantage
Increase agility and accelerate business transformation with a cloud-native IGA solution.
Deploy Quickly & See ROI in Weeks
Implement Saviynt in 6-8 weeks & see a 240% return on initial investment over three years.

Within each quadrant, vendors are listed only in the alphabetical order and no other particular order.

Saviynt Named a Customers’ Choice in the Gartner® Peer Insights™ Voice of the Customer report for IGA
Voice of the Customer for Identity Governance and Administration (IGA) Report for 4th Consecutive Year!
The Most Comprehensive
IGA Solution
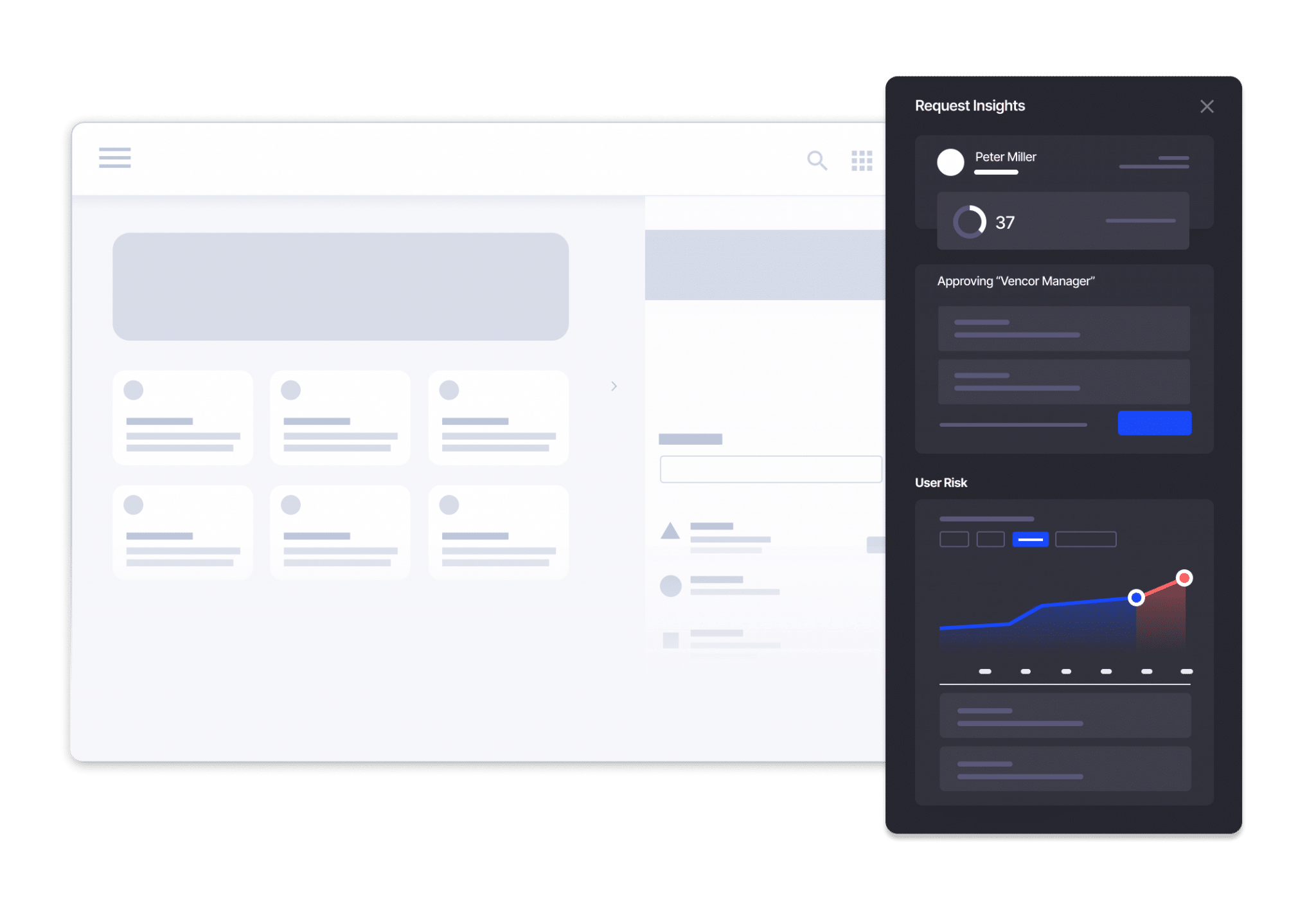
Intelligent at Its Core
Reduce risk with advanced identity governance and intelligence through the most versatile cloud identity warehouse
- Get 360-degree visibility across identities and access
- The most accurate recommendations and approvals through Saviynt Intelligence advanced AI/ML capabilities
- Automate the entire identity lifecycle
- Ingest any identity and analyze complex access & usage data
A Smooth Experience at Every Touchpoint
Make identity governance and administration seamless across all user touchpoints
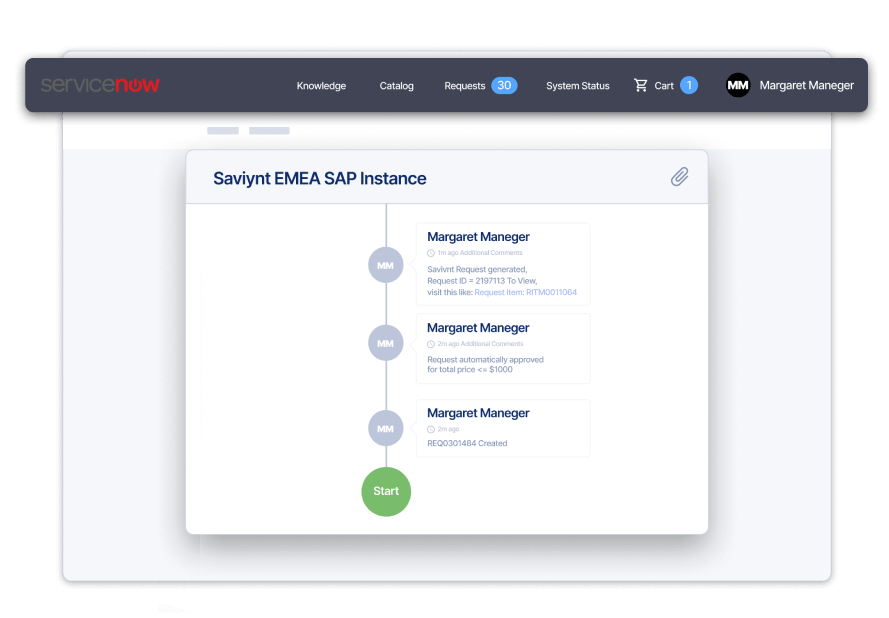
- Extend governance and access management with our native ServiceNow app
- Streamline access requests through Saviynt’s browser plugin, Slack and Microsoft Teams integration
- Unify administration across environments
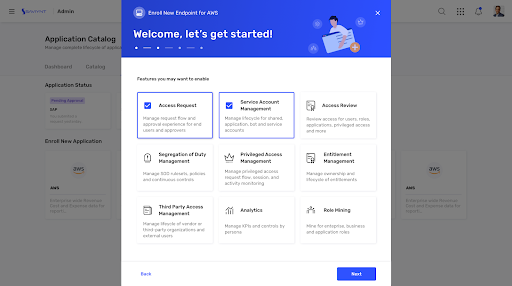
Secure Without Slowing Business Down
Configure, use, and scale IGA with a modern UX/UI and elastic cloud-based infrastructure
- Reduce application onboarding time by 70% or more
- Onboard once, then enable features on-demand
- Streamline access with roles, rules, and policies
- Simplify service account management
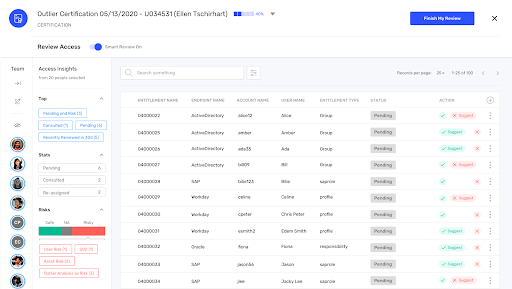
Rapid Identity Governance Meets Rapid ROI
Ensure a highly efficient and interactive identity governance and administration program
- Reduce IT dependence by empowering users and admins with self-service features
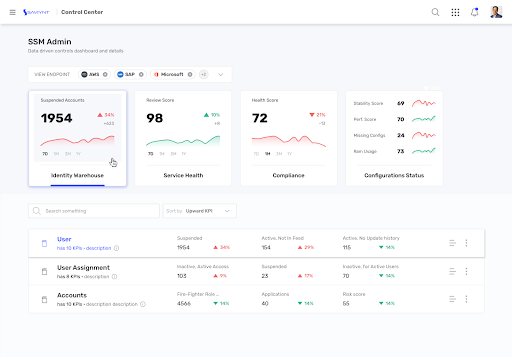
- Ensure visibility, control, and compliance through a centralized Control Center
- Reduce review fatigue with intelligent certification campaigns that surface high-risk access
- Tailor IGA processes with bring-your-own connectors, widgets, and more
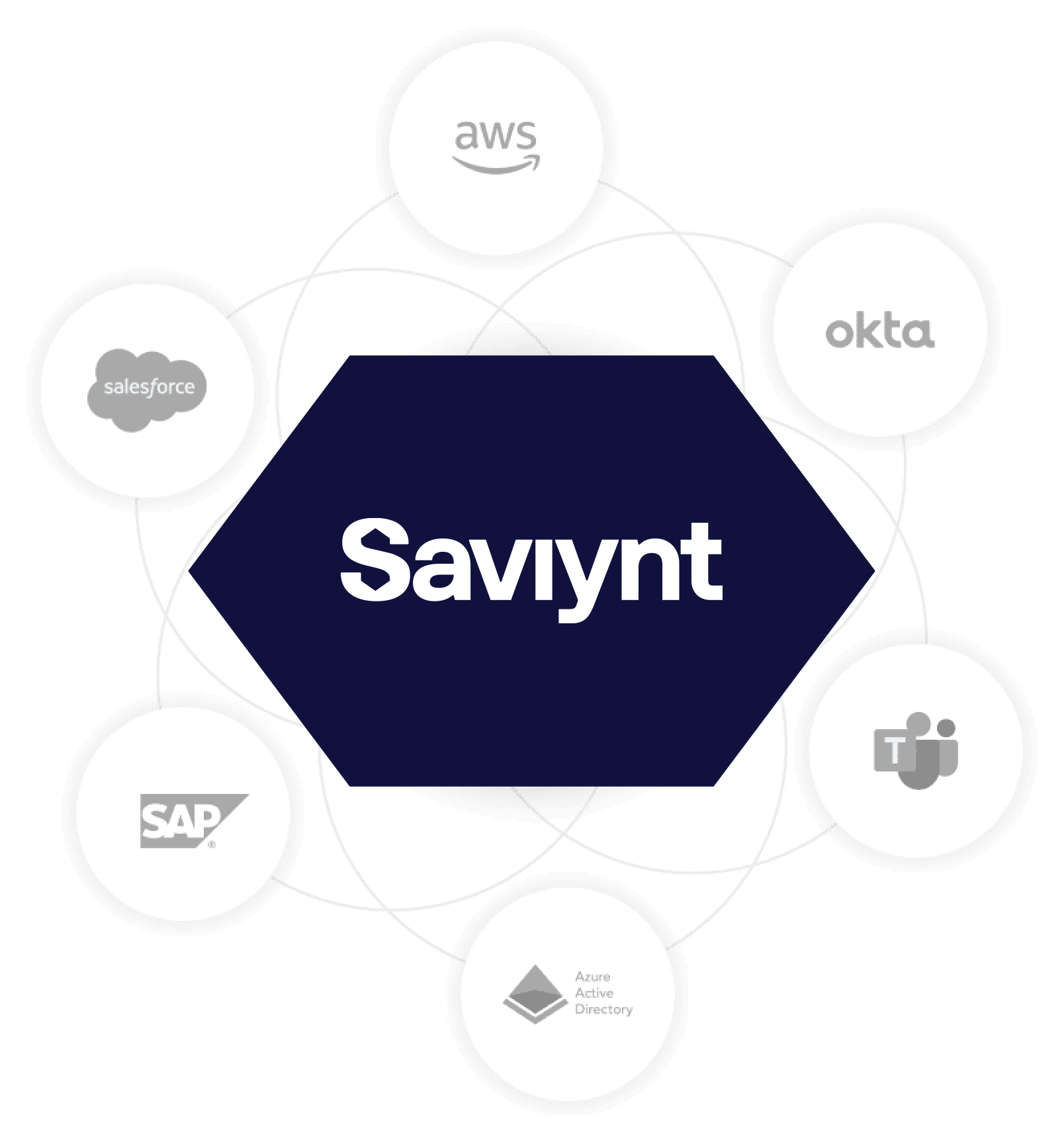
Deeper Integrations for Better Visibility & Control
Enable identity governance and provisioning to all enterprise systems
- Improve visibility with fine-grained integration with ERP/EHR platforms
- Connect everything quickly and securely with certified integrations in Saviynt Exchange
- Automate provisioning tasks with IdentityBot – a built-in RPA engine
- Make identity management event driven by responding to changes in real-time
.webp?width=545&height=435&name=kc_545x435%20(1).webp)
Saviynt Identity Cloud IGA Capabilities Recognized as Industry-Leading by KuppingerCole Analysts AG
KuppingerCole Leadership Compass Report 2024
Customers Share Their Stories
The world’s largest organizations trust Saviynt
Award-Winning Deployment Achieves 83% Faster Onboarding

"Executing a project of this size, across three continents and multiple time zones, during a global pandemic was a major achievement. The spirit of collaboration and sense of teamwork was invaluable in delivering the project in time. Saviynt did a wonderful job.
Daniel Tunes
Director, Head of Identity & Access Management at Danfoss

Journey to the Cloud with Phillips 66 and Saviynt IGA

Saviynt helped Phillips 66 with their IGA modernization initiative
"Our on-prem solution could only manage other things on-prem, and Saviynt has the ability to manage things both on-prem and in the cloud, so that was one of the things that made us realize that this is really a good solution for us in both realms."
Steve Edford
Analyst, Identity and Privileged Account Management

Resources for your identity journey
Analyst Report
Saviynt included in the 2024 Gartner® Market Guide for Identity Governance and Administration (IGA)

EBook
Making the Move to Modern IGA

Case Study
Ingredion Replaces Legacy Solution with Flexible, Modern Cloud IGA Platform
.jpg)
Analyst Report
Saviynt Identity Cloud IGA Capabilities Recognized as Industry-Leading by KuppingerCole Analysts AG
Solution Guide
Unify IGA and PAM with Saviynt Identity Cloud

Analyst Report
Saviynt is named a Customers’ Choice in the 2023 Gartner® Peer Insights™ Voice of the Customer: IGA

Case Study
Startup Chooses Saviynt IGA For Top Features
.jpg)
Solution Guide
Modernizing SAP Identity Management
Identity Governance and Administration (IGA): FAQs
What is identity governance and administration?
IGA (identity governance and administration) manages user and digital access privileges and digital identities in the organization.
The goal of identity access governance and administration is to provide employees seamless access to relevant data while keeping that same data safe from cybercriminals or accidental disclosure. Identity governance solutions can also help a company comply with regulatory requirements. At the same time, IGA processes shouldn’t get in the way of an efficient operation.
To achieve this objective, identity access governance and administration solutions encompass various tools, policies, and methodologies that work in tandem. It manages multiple areas, including identity management, data governance, role-based access control policies, and more.
What are the primary functions of an identity governance and administration solution?
A good IGA solution should cover the following functions.
First (and arguably the most important) is identity lifecycle management. It’s concerned with onboarding new users, creating accounts, granting access privileges, and (if needed) revoking them. It also involves constant review to ensure users’ privileges are still relevant.
Identity governance and administration also helps with access request management. The goal is to make asking for access privileges seamless and self-service. This helps lessen the burden with the administration team.
IGA solutions should also provide access control policies. Examples include role-based, resource-based, or attribute-based approaches. The aim is to give access based on a person’s role, authority, and security clearance within the organization.
Managing policies is crucial for any IGA platform. It helps the admin team detect high-risk requests, enforce access policies, and prevent unauthorized users from breaching the system. Saviynt Identity Governance and Administration also includes a strong auditing and reporting workflow that helps provide and document continuous compliance so that management can trace the source of a data breach when it happens.
What are the benefits of an IGA platform?
The main benefit you’ll get from an IGA platform is security. An effective identity governance and administration platform can help reduce data breaches and accidental leaks by limiting data access based on job specific activities. Furthermore, even when breaches occur, an IGA platform can minimize the damage by limiting the information an attacker can access.
Another benefit of an IGA platform is compliance with relevant government and industry regulations. For instance, an IGA solution in Europe is vital for complying with the General Data Protection Regulation (GDPR). Not only can this help make your data safe, but it also saves you from paying hefty fines and enduring public scrutiny.
An automated IGA approach also improves your organization’s efficiency. Many manual tasks, like providing access privileges, can be taken off your staff’s plate, giving employees more time to work on more productive tasks.
Modern, cloud-based IGA solutions also provide cost savings through the use of machine learning. In addition to management savings through the use of automation, you don’t need to hire costly professional services to customize or help maintain your program while also reducing the chance of facing heavy fines for non-compliance.
Do all businesses need IGA security?
While beneficial for any organization, IGA security isn’t necessary for all of them. The main limitation is resources.
Implementing a proper IGA solution takes time, money, and effort. This can be more trouble than it’s worth for smaller organizations with only a handful of employees, that operate in a single cloud, and don’t have many external or third-party identities needing management. These companies can often do better with manual identity governance and enforcing simple access policies.
However, an IGA solution is mandatory for a growing enterprise. Aside from the potential threats facing larger operations, management should also be keen on complying with regulations such as GDPR, HIPAA, and PCI DSS.
Can an identity governance and administration solution work with other security solutions?
Yes. In fact, an IGA platform will become much more effective when paired with other security elements.
For example, an IGA solution can be paired with identity access management (IAM) solutions to ensure that the right person is signing into their account. Or, it can interface with Security Information and Event Management (SIEM) software for real-time monitoring.