Automate up to 75% of access review decisions and focus approvers’ attention on the most critical areas to reduce review fatigue and rubberstamping.
Eliminate the guesswork and reduce decision times for access requests and reviews by up to 70% with AI-powered recommendations and guidance.
Bring together your identity data, security controls, and compliance processes into a single platform for more comprehensive policy enforcement and easier audit reporting.
Eliminate the redundancies and management overhead of disparate security products, while gaining unified visibility and consistent control across your entire environment.
Accelerate deployment with a cloud-native platform and a catalog of pre-built integrations, enabling consistent identity security and governance at any scale.
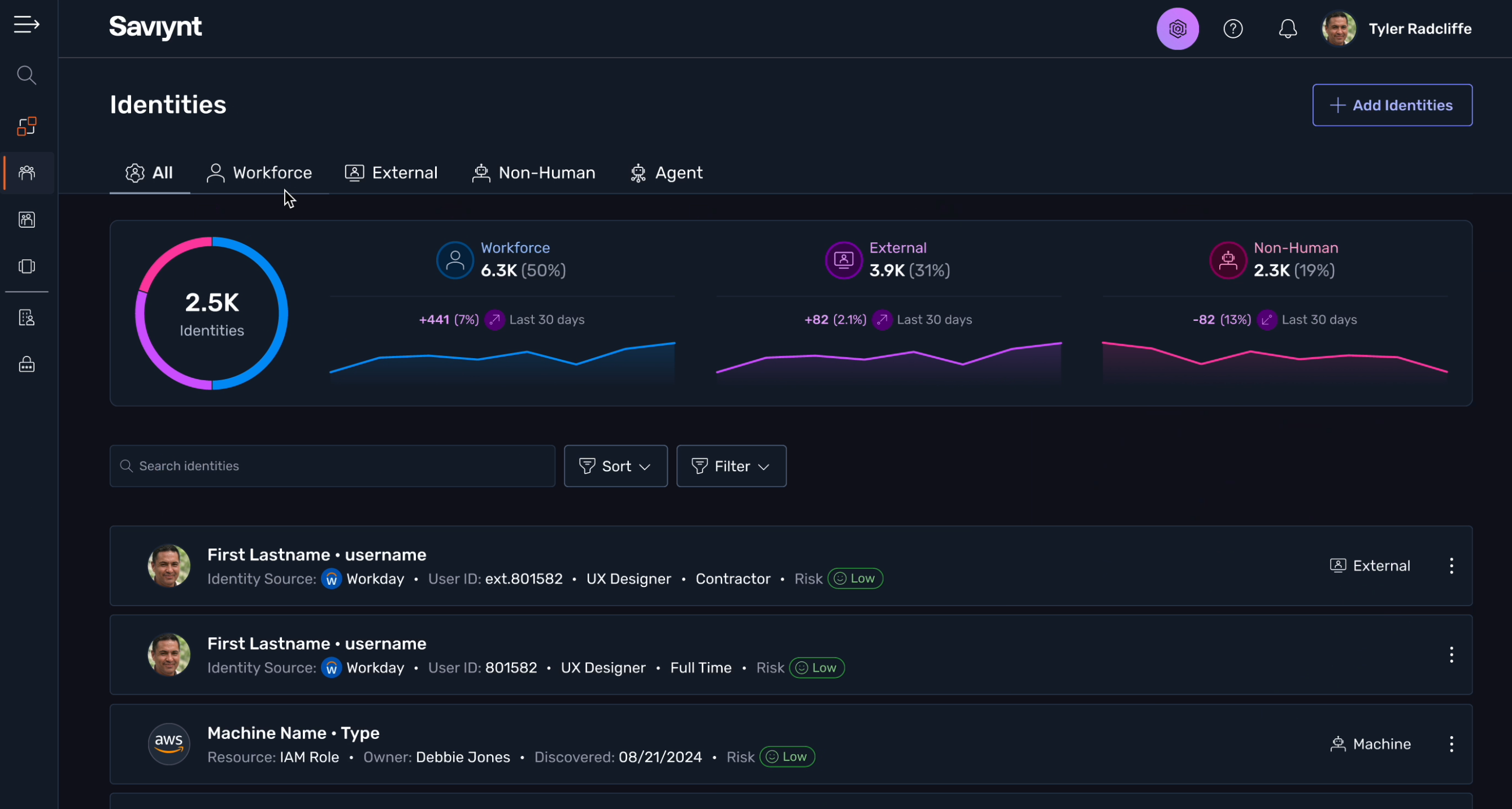
Achieve an enterprise-wide view of access risks, across all apps, all entitlements, for all identities.
All identity types
Support traditional internal workforce users, plus external users, non-human identities and AI agents.
All apps and resources
Integrate with and manage all types of apps, platforms and ecosystems, such as SaaS, hybrid, on-prem, IaaS, ERP/EMR, CRM, and HR.
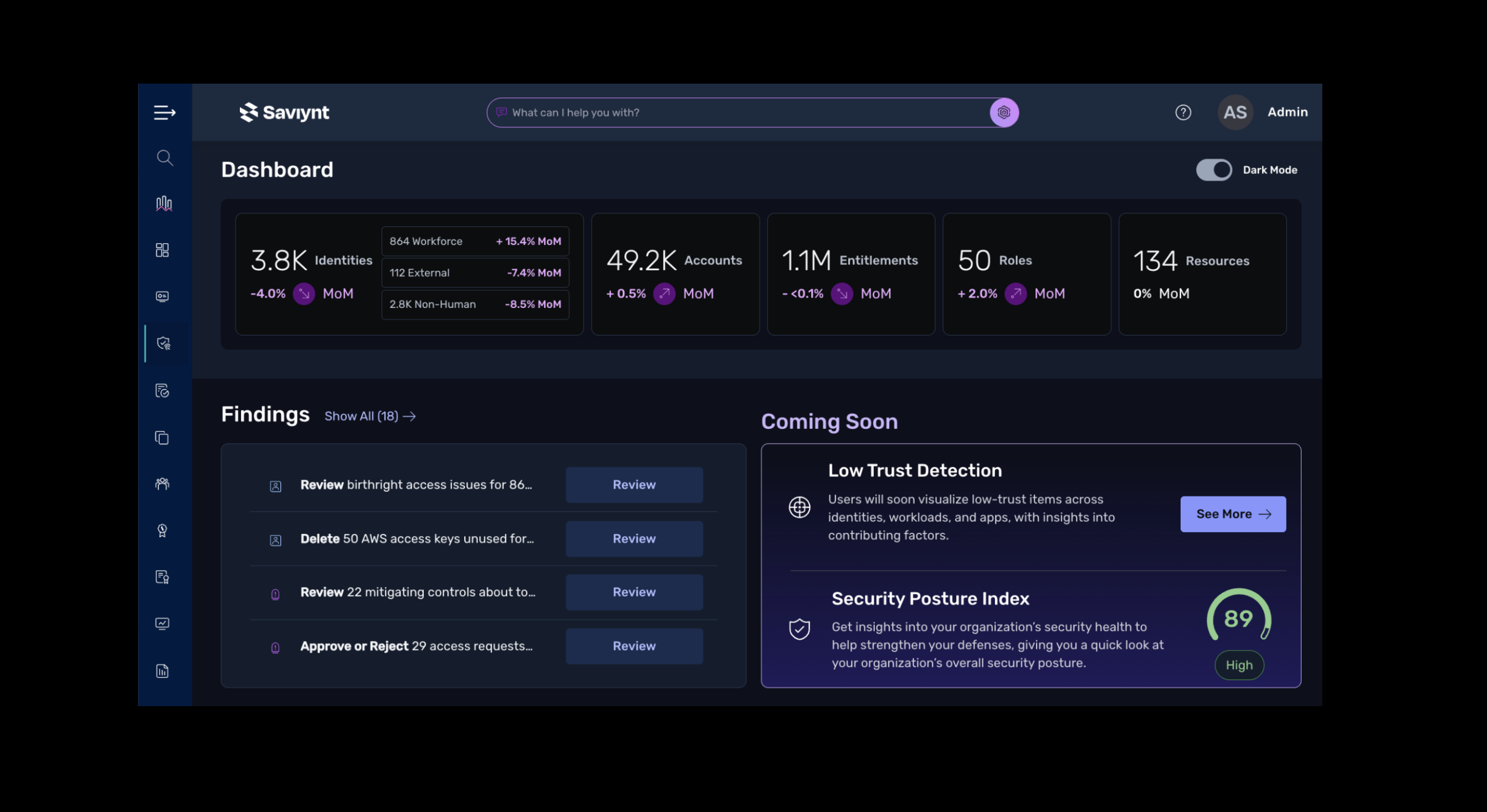
Learn about the foundation of The Saviynt Identity Platform by diving into our identity governance & administration solutions capabilities.

Accelerate your Zero Trust journey and ensure even the highest-risk access for all identities — human, non-human, AI agents, internal, or external — is secure.
.png?noresize&width=327&height=177&name=Dicovery%20and%20control%20(5).png)



.jpg?noresize&width=1359&height=800&name=banner-background-healthcare%20(1).jpg)

Identity Governance and Administration (IGA) is crucial for managing digital identities and access privileges within an organization. Its primary goal is to provide employees with seamless access to necessary data while simultaneously protecting that data from cyber threats and accidental disclosure.
IGA solutions also help companies maintain compliance with regulatory requirements. To achieve these objectives, IGA employs various interconnected tools, policies, and methodologies. These encompass several key areas, including identity management, data governance, and role-based access control policies, all while ensuring that IGA processes do not hinder operational efficiency.