
Related Post

Report
2024 Identity and Security Trends

Report
Saviynt a Gartner Peer® Insights Customers Choice for IGA

Solution Guide
IGA Buyer's Guide
-1.png)
Solution Guide
PAM Buyers Guide

Whitepaper
Use our partner finder to discover your perfect business match.
Tune in for expert-led live demos on how Saviynt’s identity security solutions transform your digital security with actionable insights and best practices.

According to the IBM Cost of Data Breach Report for 2022, healthcare breach costs have risen by almost 42% since 2020, with estimated costs rising from $9.23 million in 2021 to $10.10 million in 2022, an increase of just over 9%. While there are certainly direct financial costs associated with breaches, reputational and trust losses also hurt the affected organizations.
Healthcare providers must not only help patients through stressful times in their lives, but are also charged with protecting sensitive Protected Health Information (PHI) and financial data. With so many regulations to keep track of, maintaining continuous compliance is imperative.

So, what are some of the ways converged identity platforms (CIPs) can help healthcare providers maintain compliance?
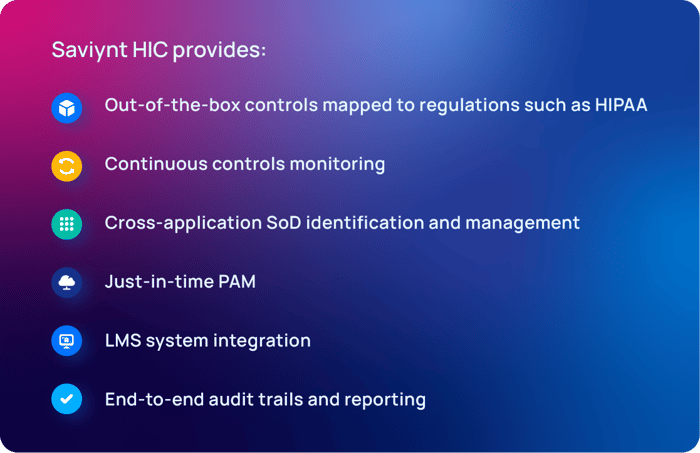
CIPs deliver out-of-the box controls within a unified controls framework cross-mapped to essential regulations (HIPAA, PCI DSS, etc.), standards, and control types (CIS, NIST CSF, etc.) to provide additional safeguards to restrict access to PHI and other sensitive information. Regular and elevated access can be monitored for usage and control violations, even if gained through a backdoor. Custom access controls can also be analyzed based on user type. For third-party identities, access is able to be deprovisioned automatically when contracts or employment status ends.
Centralizing identities and identity governance on a converged platform helps take better advantage of the controls needed to comply with a wide variety of regulations. By mapping controls to various regulations, you can align processes and program management to ensure processes are followed and monitored, and that anomalous activities can be identified for quick and accurate remediation.
Ensuring staff members have taken and passed their HIPAA training, annually and during onboarding, is a necessity. CIPs that integrate your learning management system (LMS) with your identity security program ensure employees gain access to the critical systems they need. Integration allows automatic access to resources only upon completion of required training to maintain HIPAA compliance.
The number of applications providers work with has spiraled over the past several years. Converged platforms provide a consolidated way to quickly identify and manage separation of duty (SoD) violations. Knowing who has access to what applications, and their specific entitlements for those applications, is critical in maintaining compliance, especially in revenue/billing cycles. CIPs not only provide that information but also identify toxic crossover access between applications.
Pre-emptive alerts can be sent to administrators, identity owners, and identity requestors that a bad combination is about to take place. SoD management can be mapped to regulatory controls and isn’t limited to internal staff–it can also include third parties–to help extend protection across the entire threat landscape.
Historically, staff within healthcare have had expanded access to systems. This expansion of access has several causes: mismanagement, technological limitations, and conscious decisions to accept risk. Unfortunately, providers can no longer afford to ignore expanded privileges. CIPs combine privileged access management with identity governance and administration (IGA) to batten down the hatches without impacting patient care.
Time-bound access and clipping recommendations based on roles and attributes allow for better enforcement of privileged access. Better enforcement of policies help further limit the threat landscape while simplifying overall program management.
Audits are necessary to be able to prove compliance, however, they are time-consuming and expensive, taking administrators away from more important tasks. CIPs provide end-to-end audit trails and analytics. Converging capabilities also results in converged reporting and analytics capabilities, allowing administrators to limit the number of data sources they need to comb through to find and collate needed data for auditors.
Healthcare will continue to be a focal point for bad actors to target, however, implementing a strong identity security program can help reduce the chances of either malicious or accidental incidents from occurring.
Converged identity platforms (CIPs), such as Saviynt Healthcare Identity Cloud (HIC), help organizations maintain continuous compliance and shrink the threat landscape all without introducing friction with staff needing access to critical information. Saviynt HIC converges Identity Governance and Administration (IGA), Privileged Access Management (PAM), Application Access Governance (AAG/GRC), and Third-Party Access Governance (TPAG) onto a single platform that centralizes critical identity security program components to help organizations maintain continuous compliance.
For more information on converged identity platforms in healthcare organizations, check out our three previous blogs in the series: Empowering Healthcare Workforces, Improving Operational Efficiency, and Protecting Healthcare Data.


07 / 04 / 2025


Report

Report

Solution Guide
-1.png)
Solution Guide

Whitepaper