With the rapid growth of SaaS adoption, organizations are using more applications than ever—an average of 625 apps per enterprise. From collaboration tools to business-critical platforms, this expanding app landscape is driving productivity. As organizations rely on more apps to get work done, elevated access is no longer confined to IT or IAM administrators. Business users, developers, and even contractors are increasingly requesting privileged access to complete tasks, troubleshoot issues, or meet tight deadlines.
But here’s the problem: most current solutions weren’t built to manage elevated access across all your applications. Critical entitlements and shared credentials often go unmonitored and unmanaged—dramatically expanding the attack surface and putting compliance at risk.
It’s time to ask: are your existing tools truly securing access across your entire application ecosystem? That’s where our latest product release changes the equation.
Saviynt is introducing a powerful new extension for Identity Cloud customers: Just-in-Time (JIT) Access. With JIT Access, we bring the true principles of Zero Standing Privileges (ZSP) to the application layer—ensuring access is dynamically provisioned only when needed and automatically removed when it’s not.
Introducing Saviynt Just-in-Time Access
Saviynt JIT Access flips this model on its head with ease, addressing three key Identity Security challenges:
You can’t protect what you can’t see
Identity security starts with discovering—and truly knowing—where your risks lie. With hundreds or even thousands of applications in play, manually tracking this access is no longer feasible. Organizations need a scalable solution to manage risk effectively and continuously. Saviynt’s Identity Platform with JIT Access empowers organizations to uncover access to high-risk entitlements, detect orphaned accounts, and expose shared credentials—all of which increase the attack surface. Know who has access to what, whether they should have it, and how risky entitlements and credentials are actually being used.
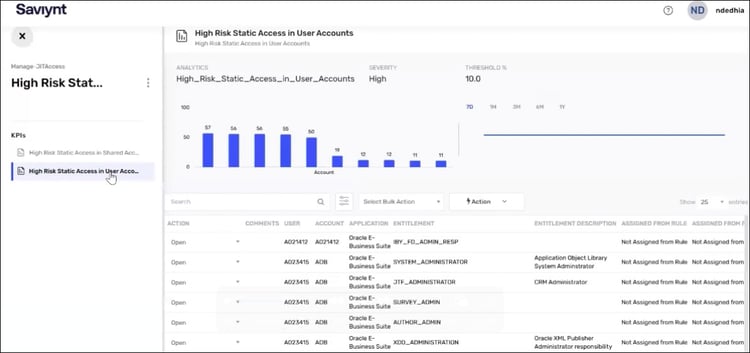
Remediation Shouldn’t Be Complicated
Discovering risky access is only half the battle—acting on it quickly and efficiently is where most organizations struggle. Manual remediation processes are time-consuming, error-prone, and often disconnected from application owners. JIT Access makes risk remediation simple and immediate. You can instantly revoke access to all identified risky entitlements and shared credentials in bulk, without waiting on lengthy review cycles—minimizing your attack surface with just a few clicks.
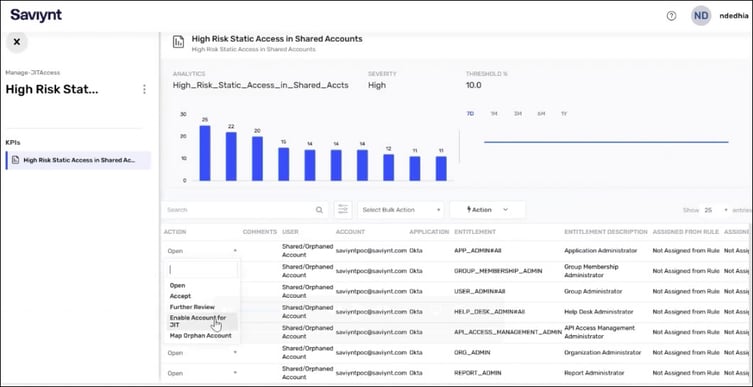
Streamlining JIT Access Is the Key to Secure Productivity
Security should enable, not hinder. With Saviynt JIT Access, organizations can automate access decisions using policy-driven controls, defining who gets access, when, and under what conditions. Built-in workflows support approvals based on business need, and time of access, while MFA and time-limited grants reduce risk from stolen or lingering standing access.
App Owners avoid manual reviews, and Admins gain peace of mind knowing risky access is locked down by smart, scalable policies. Users get timely access to do their jobs without waiting through lengthy approval cycles.
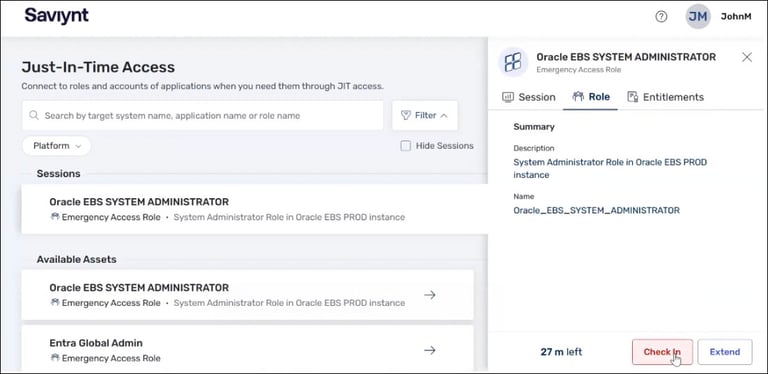
Say Goodbye to Standing Access. Say Hello to Just-in-Time
Industry analysts agree that adopting Just-in-Time (JIT) and Just-Enough-Access (JEA) models is critical to reducing the identity attack surface. While many identity security tools promote Zero Trust principles, few go far enough—often stopping short of enforcing JIT access within applications themselves.
Saviynt takes it further. We’re not just securing infrastructure—we’re eliminating the blind spots where standing access still lingers. Saviynt JIT Access delivers full visibility, rapid remediation, and seamless JIT access with just a few clicks. Access is granted only when needed for any app, keeping your environment secure without disrupting productivity.
It’s time to move beyond persistent, high-risk access. Step into the future of identity-driven application security with Saviynt Just-in-Time Access.
Please join our Just-in-Time Access launch webinar to learn more.










