
Related Post

Report
2024 Identity and Security Trends

Report
Saviynt a Gartner Peer® Insights Customers Choice for IGA

Solution Guide
IGA Buyer's Guide
-1.png)
Solution Guide
PAM Buyers Guide

Whitepaper
Use our partner finder to discover your perfect business match.
Tune in for expert-led live demos on how Saviynt’s identity security solutions transform your digital security with actionable insights and best practices.

Despite the widespread use of third-party contractors, vendors, and agencies in many industries, most organizations don’t actually understand the scope of their third-party relationships or the security risks they present. A survey from the Ponemon Institute noted that 66% of companies surveyed had no idea how many third-party relationships they had or how they were managed, even though 61% of the surveyed companies reported having a breach attributable to a third party.
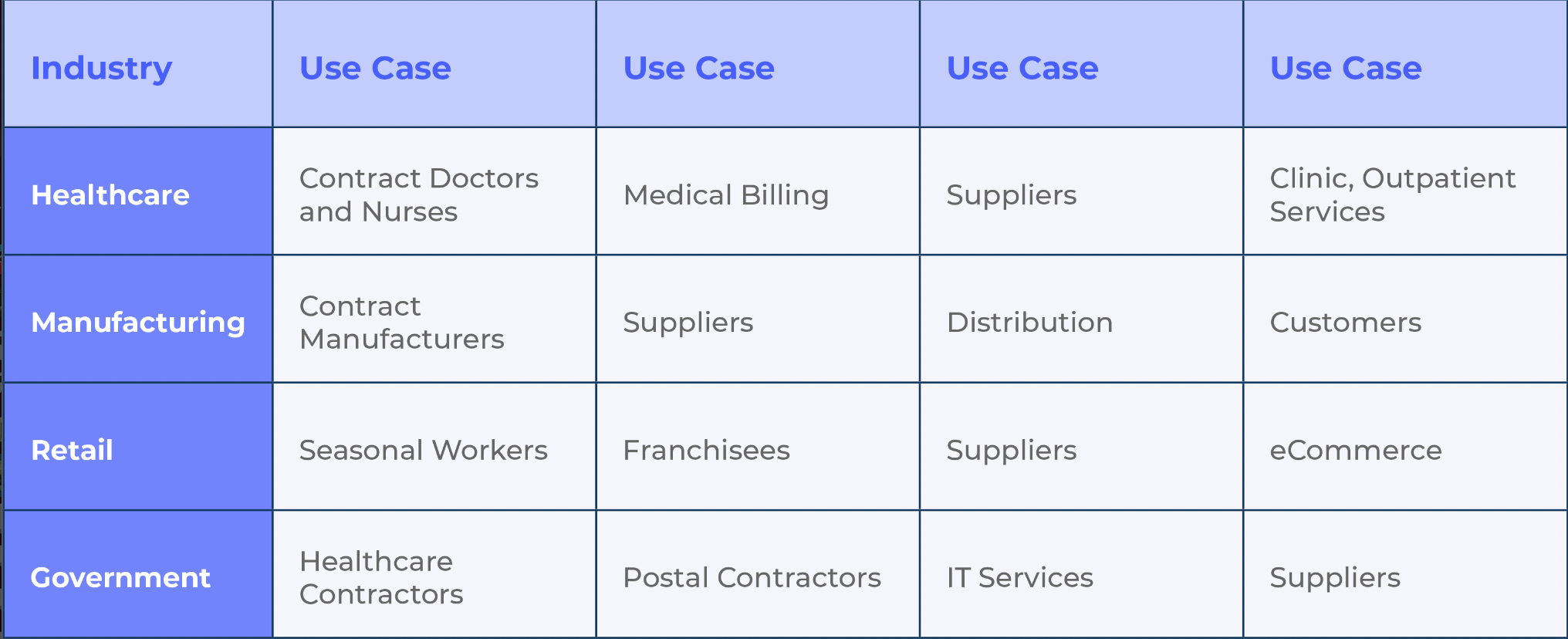
Use of third-party resources is widespread throughout many industries, yet many organizations don't know how many of these relationships they have.
The data is cause for concern, especially among enterprise identity and security teams. The third-party security gap leaves companies vulnerable to rising cyber risks and continues to be exploited by bad actors around the globe. The latest edition of Kaspersky’s annual IT Security Economics report found that third-party incidents became the most costly type of enterprise data breach in 2021.
While the third-party identities have a doorway into your secure perimeter, they do not go through the same level of scrutiny as your employees and internal staff. In most cases, these identities are not part of the corporate identity store and authentication directory. These identities access the business assets using shared accounts, generic accounts, or hotel IDs. The account and credentials are shared between multiple users.
While many organizations have identity management solutions in place, most of the solutions are not designed to manage the complexity of governing third-party identities.
To understand if you are effectively managing third-party risk, begin by asking yourself:
Once you have assessed your current situation, follow these five steps to ensure the security of third-party access in your organization.
Establishing an identity lifecycle management program for third parties begins with consolidating third parties into a system of record. This approach captures the pertinent information about the organization before moving on to grant access to third-party users.
As an initial step, companies should gather a list of current third-party relationships. Since many third parties have contractual relationships, procurement can be a good place to start.
Companies should designate a sponsor inside the company to facilitate communications with each third party. This initial step is undoubtedly the most time-consuming and challenging, but it serves as the foundation of a successful program.
Review the language in contracts to address the third parties’ responsibilities for promptly administering identity access for their joiners, movers, and leavers. Requiring third parties to disclose breaches quickly allows companies to take prompt action to reduce the potential fallout.

The company and the third-party organization need to determine a workflow for vetting and onboarding third-party users to ensure the users are who they claim to be — and ensure that the onboarding process follows the concept of least privilege.
Often referred to as just-enough access, third-party users should be granted the appropriate access to complete their assigned roles and nothing more. Make role definitions specific to the actual tasks: don’t simply duplicate them because the functions are similar.
A self-service portal to request access and provide required documentation aids in collecting information for third-party vetting and ID-proofing. This method speeds up vetting and provisioning processes to help the user ramp up and become productive quickly. Having a clear workflow between the company sponsor and the third-party administrator also reduces the phone calls and emails that typically slow down the process.

The company and the third-party organizations should define and continually optimize policies and controls to identify potential violations and reduce false positives, which helps reduce administrative workloads. Over time, teams can apply auto-remediation to improve efficiency even more.
The company and third-party administrators should test the policies and controls regularly (monthly or quarterly). Running periodic access reviews and ongoing certifications will help ensure no user is over-provisioned and that orphaned accounts won’t provide a conduit into sensitive data.
Securing third-party access is rising in importance with several regulatory frameworks and is becoming a focal point for auditors. Sarbanes-Oxley (SOX), for example, includes several specific controls for managing third-party risk.
Bring all third-party access under the same compliance process that employees undergo. This ensures consistency across the entire workforce and that security teams can mitigate violations quickly. Compliance controls can be tied to user type, and auto-remediation policies can be enacted to take swift action on non-compliant identities. Having out-of-the-box regulatory compliance reports for Sarbanes-Oxley, HIPAA, GDPR, PCI-DSS, and others makes it easier to enforce compliance controls and more efficient to provide audit documentation.
Once companies complete the first four steps, they can raise their cybersecurity maturity through converged governance. Using a platform that offers converged IGA, Privileged Access Governance, and Third Party Access Governance, they can get a single-pane-of-glass for complete visibility across their entire workforce.
It also provides another level of safety by immediately revoking access to downstream systems if warranted – so security teams can grant time-based access at the outset and revoke access when a contract ends. Adding Application Access Governance allows a company to identify potential and actual cross-application SoD violations across SaaS and on-premises applications.
Rather than managing multiple relationships and integrations to provide an end-to-end identity platform, companies can leverage Saviynt’s Enterprise Identity Cloud (EIC) to gain the business benefits of a world-class identity solution quickly.
EIC combines multiple identity management capabilities into a single cohesive platform to unify controls and risk management for every identity, app, and cloud across your business. EIC allows you to onboard people, apps, and machines in minutes and selectively turn on access & governance functionality. It features a Third-Party Access Governance solution that allows you to:
The use of third-party vendors, partners, contractors, freelancers, bots, service accounts, and other non-employee populations is only going to grow. By addressing the need for third-party access governance with Saviynt’s proven end-to-end, cloud-native solution, companies can close the third-party security gap and gain total security for their enterprises.
In the next blog, we’ll explore how creating a single system of record reduces third-party security risks.

07 / 16 / 2025



Report

Report

Solution Guide
-1.png)
Solution Guide

Whitepaper