Privileged Access Management (PAM) Solutions
Eradicate standing privilege and establish governance from day one
.webp?width=1600&height=1062&name=CPAM-Product-Analyze-Privileged-Activity-1600-o%20(1).webp)
Protect Your Organization On-Prem and in the Cloud
Privileged access is a primary attack vector—and the attack surface keeps expanding. This complexity makes it harder to monitor for privileged access risks.
An Agile Alternative to Infrastructure-Based PAM
Saviynt’s cloud-native privileged access management solution is delivered via an agentless, zero-touch cloud architecture for quick, secure deployment. With privileged access management, achieve zero-standing privileges with just-in-time (JIT) access and intelligent risk insights.

Minimize Risk Exposure
With Just-in-Time PAM.
Move off legacy identity management infrastructure and conquer cloud complexity with
just-in-time identity-driven PAM
Break Down Silos
View and manage risk across clouds, SaaS, DevOps, infrastructure, and applications to reduce the attack surface.
Automate Privileged Access
Streamline least privilege access enforcement and enable policy-based lifecycle management.
Converge PAM & IGA Onto One Platform
Obtain a unified control plane for all your assets & identities, regardless of the underlying technology
Provide Just-in-Time Access
Provision least-privilege time-bound access, or provide temporary role-based access elevation.
Gain a Cloud Advantage
Increase agility, and accelerate business transformation with cloud-native PAM.
Deploy Quickly
Rapidly deploy Saviynt in days across the most complex use cases without breaking the bank.
Power and Protect Your Business With Saviynt Identity-Driven PAM

Secure Every Identity With Zero Trust
Adopt Zero-Trust principles for any identity and app with fine-grained privileged access management across your application ecosystem
- Reduce credential leak with time-bound privileged sessions
- Minimize risk exposure by implementing least privileged access with zero standing accounts and privileges
- Perform entitlement metadata certification to improve business operations and ensure continuous compliance
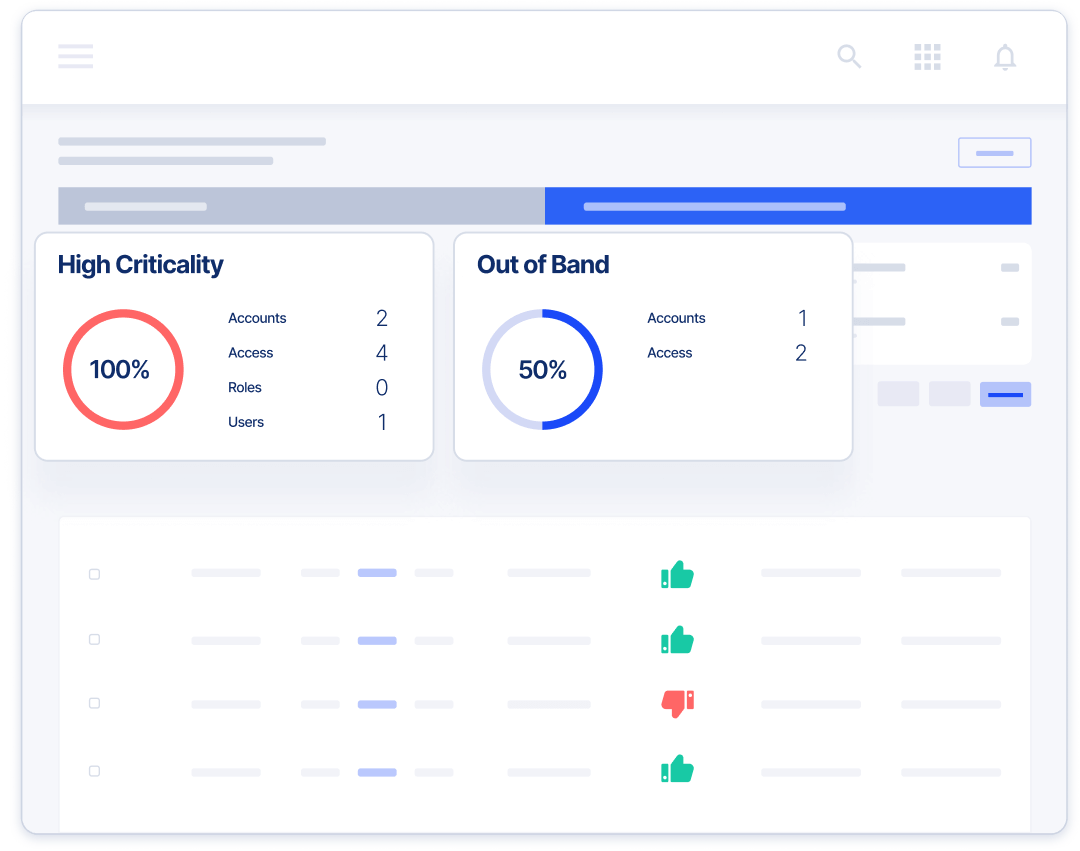
Certify Least Privilege Access With Built-in Governance
PAM & IGA are better together
- Manage standard and privileged access with a consistent user experience
- Integrate with HRIS and other identity sources for automated succession management and Joiner-Mover-Leaver processes
- Improve security insights by exchanging risk data with third-party solutions, such as SIEM, UEBA, and vulnerability scanning tools
- Exchange risk data with SIEM solutions to add context to investigations, make access decisions, and prevent privilege abuse
- View and manage any identity’s privileged access for any application
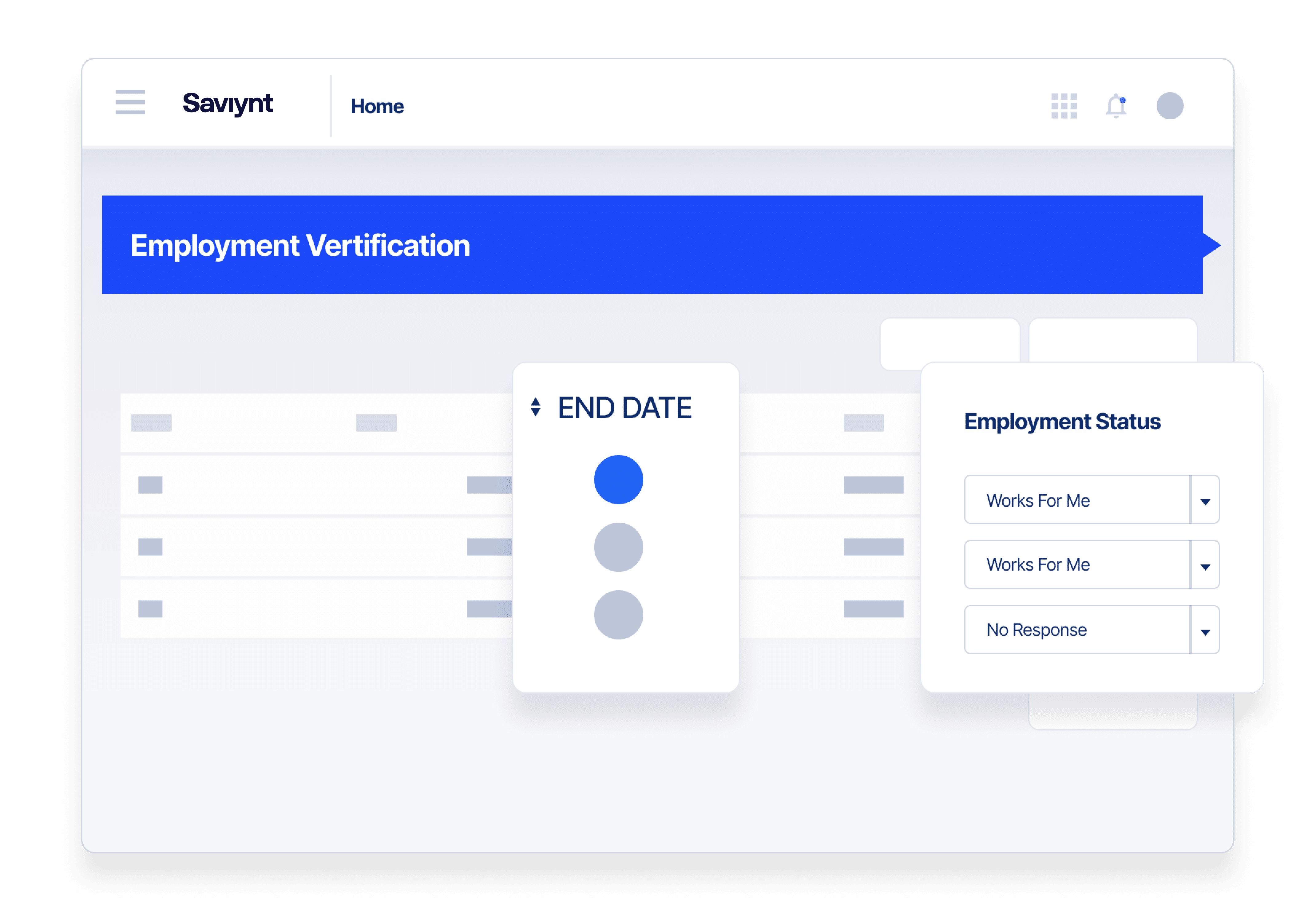
Collaborate Securely With External Users
Outside partners, suppliers, and contractors often require elevated access to critical systems and data. Establish more trust and control with:
- Secure, seamless onboarding
- Defined roles and entitlements
- Time-bound role elevation
- Session monitoring with intelligent notification
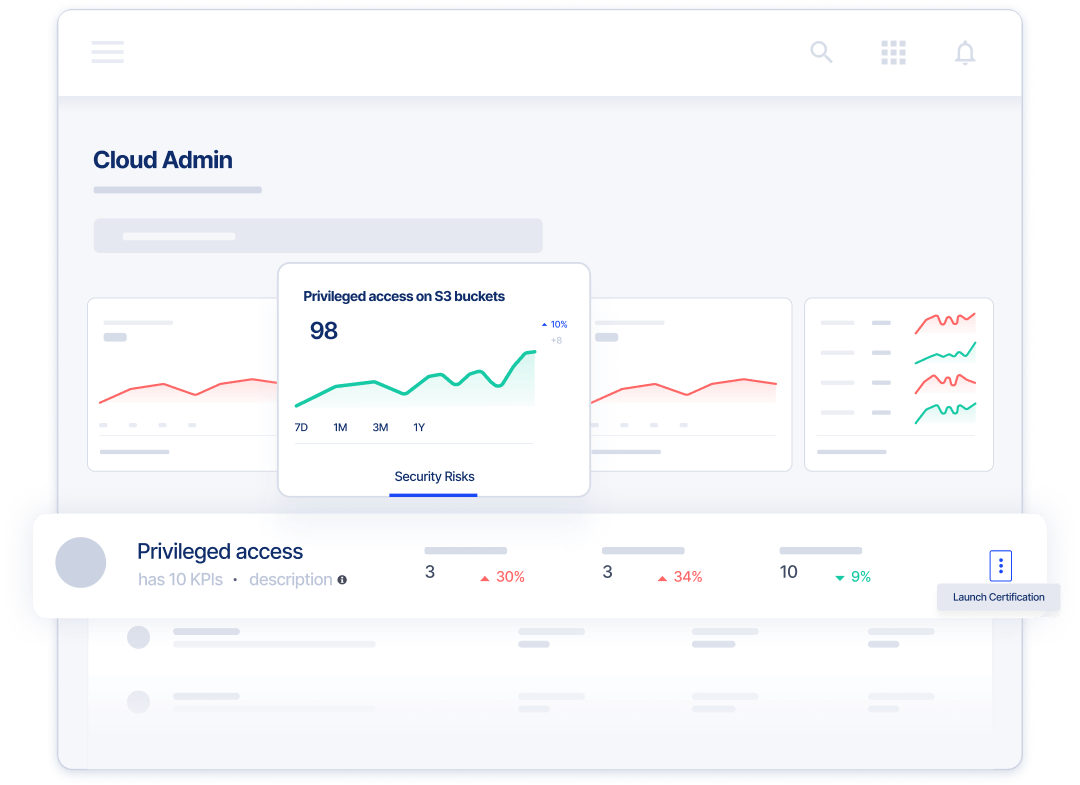
Secure Multi-Cloud Workloads and Accelerate Cloud Adoption
Secure your multi-cloud footprint with real-time insights including
- Continuous monitoring for misconfigurations and identity risks
- Built-in cloud infrastructure entitlements management to identify excessive & unused access
- Improve cloud security and PAM adoption to your SaaS applications and hybrid, multi-cloud environments
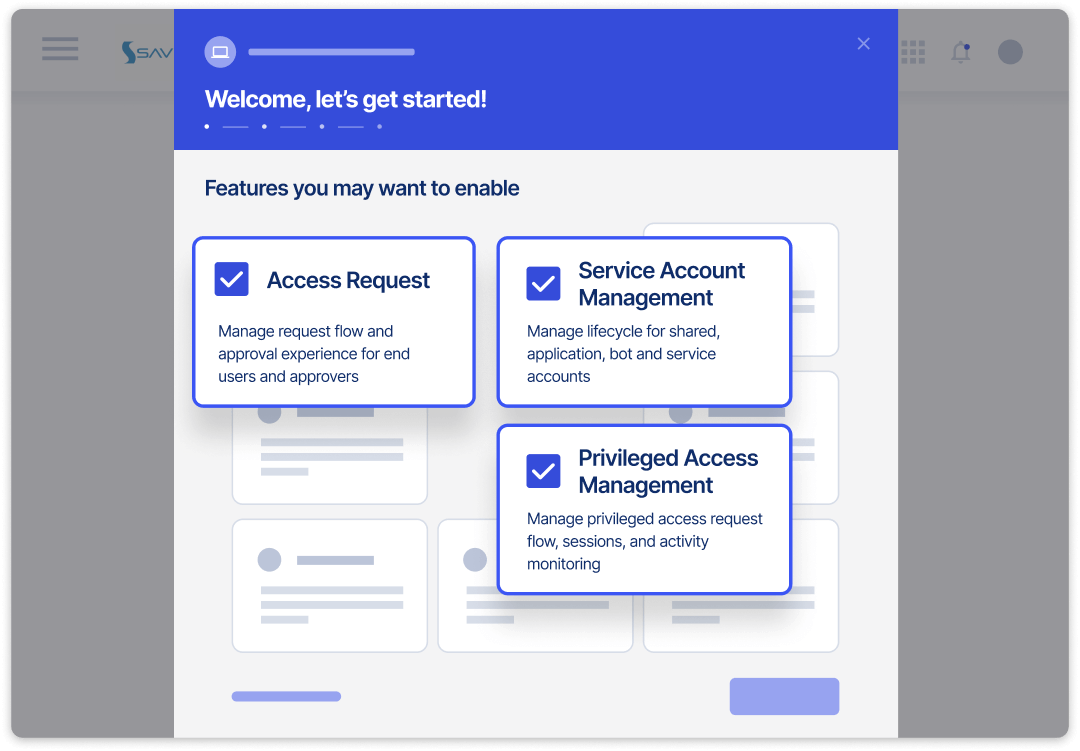
Execute at Scale With True PAM & Identity Convergence
Ditch complex deployments, shrink TCO, and achieve rapid ROI with Saviynt’s agentless PAM technology
- Simplify management with no on-prem components
- Break down identity silos with real-time Saviynt identity intelligence
- Achieve high availability and built-in trust with FedRAMP, SOC 1 & 2, ISO 27017, and more
ASSESS YOUR IDENTITY
Find out the maturity level of your identity security
Take this one-minute assessment and get some insights on strengths and potential gaps in your cloud PAM program.
Customers Share Their Stories
The world’s largest organizations trust Saviynt to reduce their privileged attack surface and minimize the impact of a data breach
Modernizing Identity Governance & Accelerating Compliance Maturity

“Before, when we didn’t have a modern solution, we felt stagnant. Today, we’re in a much better place. Overall, the implementation has been a success, and the Saviynt team was fantastic.”
Paul Dumbleton
Enterprise Information Security Team Manager

Resources for your identity journey

Analyst Report
KuppingerCole Leadership Compass: Privileged Access Management

Analyst Report
Saviynt PAM is Recognized as a Value Leader by Analyst Enterprise Management Associates (EMA)

Solution Guide
Privileged Access Management (PAM) for Applications

Solution Guide
Remote Privileged Access Management

On-Demand Webinars
How Unified IGA and PAM Can Protect Organizations from Ransomware and Other Identity-Based Threats

Whitepaper
Privileged Access Management Maturity in the Cloud
.png)
EBook
Just in Time PAM: Time To Turn off “Always On”
-1.png)
EBook
PAM Buyer’s Guide

Analyst Report
Saviynt Cloud PAM is Recognized as Best Privileged Access Governance and Strong Value by Analyst Enterprise Management Associates® (EMA)
Solution Guide
Unify IGA and PAM with Saviynt Identity Cloud
Privileged Access Management Solutions: FAQs
What is a PAM solution?
Privileged access management (PAM) tools are used to help organizations manage and secure accounts that have access to critical data and operations. Privileged identities can be human (employees or third parties) or silicon (e.g. “bots,” applications, or service accounts).
A human-privileged user is typically an IT admin with elevated rights (access) to make material changes to infrastructures, systems, or processes. Non-human privileged accounts have the ability to execute applications, run workloads, or perform other automated services. These privileged identity roles are typically granted with elevated credentials that enable access to sensitive data and resources. This makes it necessary to scrutinize these users’ activity and make sure their access is in accordance with the Principle of Least Privilege (PoLP): users should only be given the necessary access to perform their job.
The PAM solution provides a centralized, secure platform to manage privileged accounts and monitor privileged activity.
What are the primary functions of Privileged Access Management tools?
A PAM security tool should include the following capabilities:
Discovery of privileged workloads, accounts and entitlements across infrastructure, clouds and applications in real time. This helps make sure privileged access is appropriately managed, reducing the risk of misuse.
Credential management for privileged accounts. The system should include a vault to store and obscure privileged account passwords. A PAM vault should also offer the ability to rotate credentials manually or automatically, as required by the organization. To increase your odds of success, it’s best to start off with a policy of using strong passwords.
Privileged session management, which provides the ability to establish and monitor privileged sessions. Tools should allow administrators to monitor privileged user activity in real time and enable them to remediate risks by blocking risky activity or terminating the session to mitigate a potential threat. Privileged session recording is an important function for compliance purposes and can be used for digital forensics if a breach occurs.
Intelligence and analytics provides dashboards and reporting for administrators to view privileged accounts and entitlements, understand the attack surface, review access logs and privileged user activity. It provides security analysts with insights into usage patterns to preempt or mitigate breaches and gives certifiers insight as to whether users have appropriate access and permissions.
Enabling Just-in-time privileged access is perhaps the most critical capability to pursuing a zero standing privilege (ZSP) approach. ZSP is a PAM access management strategy that allows organizations to reduce the attack surface associated with standing privileges. PAM tools should make it easier for administrators to provide privileged access to users for only enough time to complete the task with the least possible privilege given, thus giving attackers a smaller window to act.
Finally, a privileged access management solution should offer role-based access control (RBAC). By establishing role-based elevation of privileged access, you can eradicate standing privilege and move towards an ephemeral privilege or ZSP model.
Why do I need a PAM solution?
Privileged accounts are one of the primary targets of hackers, given their ability to potentially exfiltrate sensitive data or carry out some other nefarious activity like taking down a system. This is why PAM solutions are considered a last line of defense and a vital part of a comprehensive cybersecurity program. By provisioning privileged access only when needed and only for the amount of time needed to complete the privileged activity, you can eliminate standing privileged accounts and reduce your organization’s attack surface.
In today’s hybrid network and cloud architectures, it’s especially vital to have cloud privileged access management. For cloud networks, it makes administration easier with one control plane to monitor activity and manage risk holistically.
Cloud PAM platforms also make your organization more accountable by controlling privileged access more holistically, improving compliance, and reducing standing privileged accounts that can be exploited due to human error or malicious intent.
A good PAM solution will help you provision privileged access efficiently so that you can reduce IT friction and allow admins to perform tasks more securely.
Finally, PAM solutions are vital for compliance with regulations like GDPR and HIPAA, cyber insurance mandates or industry frameworks.
What’s the difference between Privileged Access Management (PAM) and Identity Governance and Administration (IGA)?
While both PAM and IGA deal with access controls, they cover different domains.
PAM is mostly concerned with access management of privileged accounts. Since they’re considered high-risk, PAM typically involves more control and monitoring. For instance, privileged access management includes an audit trail and real-time monitoring to ensure accountability of a privileged identity.
IGA, on the other hand, is broader and tackles access management for the entire organization. It handles digital identity, role-based access control, and data governance for all users. IGA is also concerned with providing temporary access to third parties.
Both IGA and PAM are critical parts of a company’s overall identity management strategy. They need to work in tandem to keep the entire network secure.