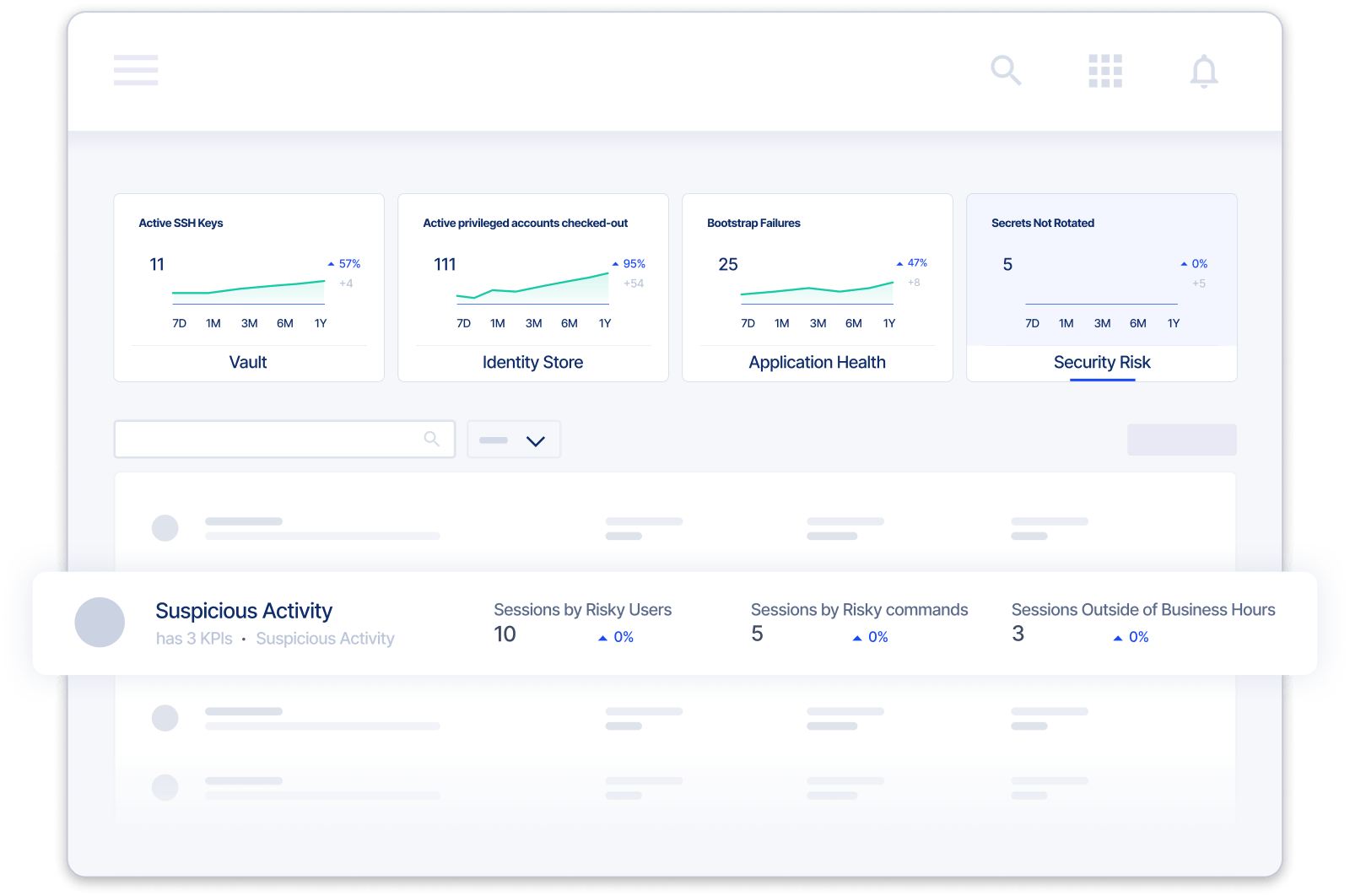

Secure Your Extended Enterprise Without Slowing Business Down
Despite the widespread use of third-party contractors, vendors, seasonal workers, and agencies, most organizations don’t understand the scope of the external access security risks in their supply chain.
Saviynt is built to protect everywhere people work. External access control makes it easy for employees, contractors, and partners to access the applications, systems, and data they need from day one with the #1 converged identity platform.
Better Collaboration. More Control.
Simplify identity security for your complete business eco-system and enable
the internal and external relationships your business needs to thrive.
Set the Stage for Success
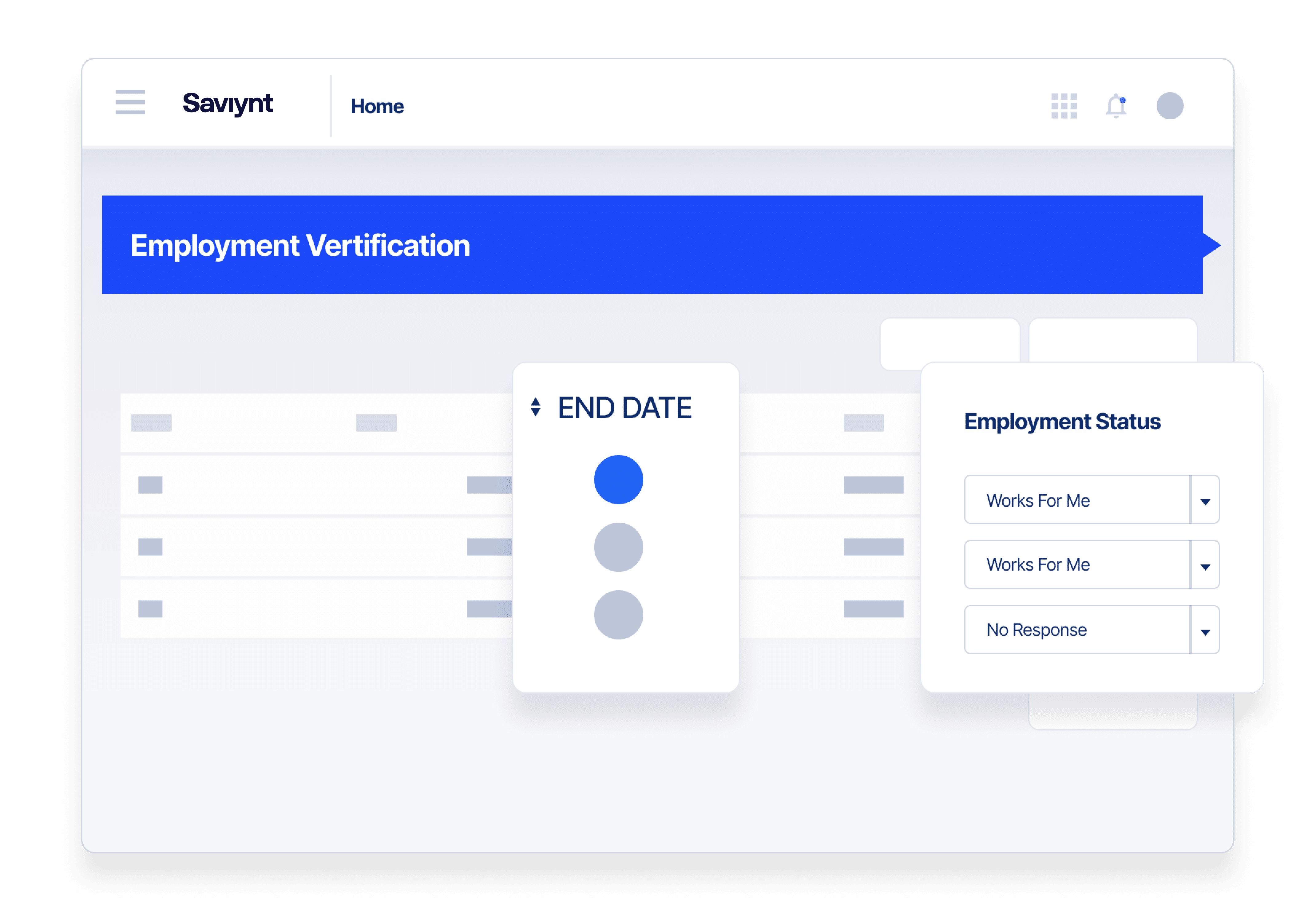
Tailor third-party access invitation processes, establish external risk-based policies, and access end dates.
Right-Time, Right-Level External Access
Ensure B2B users have a seamless experience with the access they need to do the job from day one.
Automate External Identity Lifecycle Management
Develop policy-based, third-party access lifecycle management workflows to improve productivity and enhance security.
Make Audits and Compliance a Breeze
No more certification by spreadsheet. Get personal data out of email inboxes by launching certification campaigns through Saviynt’s identity cloud platform.
Empower Security Talent To Do More
Relieve your IAM team by empowering internal sponsors to take actions in our intuitive, user-friendly identity platform.
Close Out Projects With Confidence
Reliable access review process with policy-based access revocation.
Built to Protect Everywhere People Work
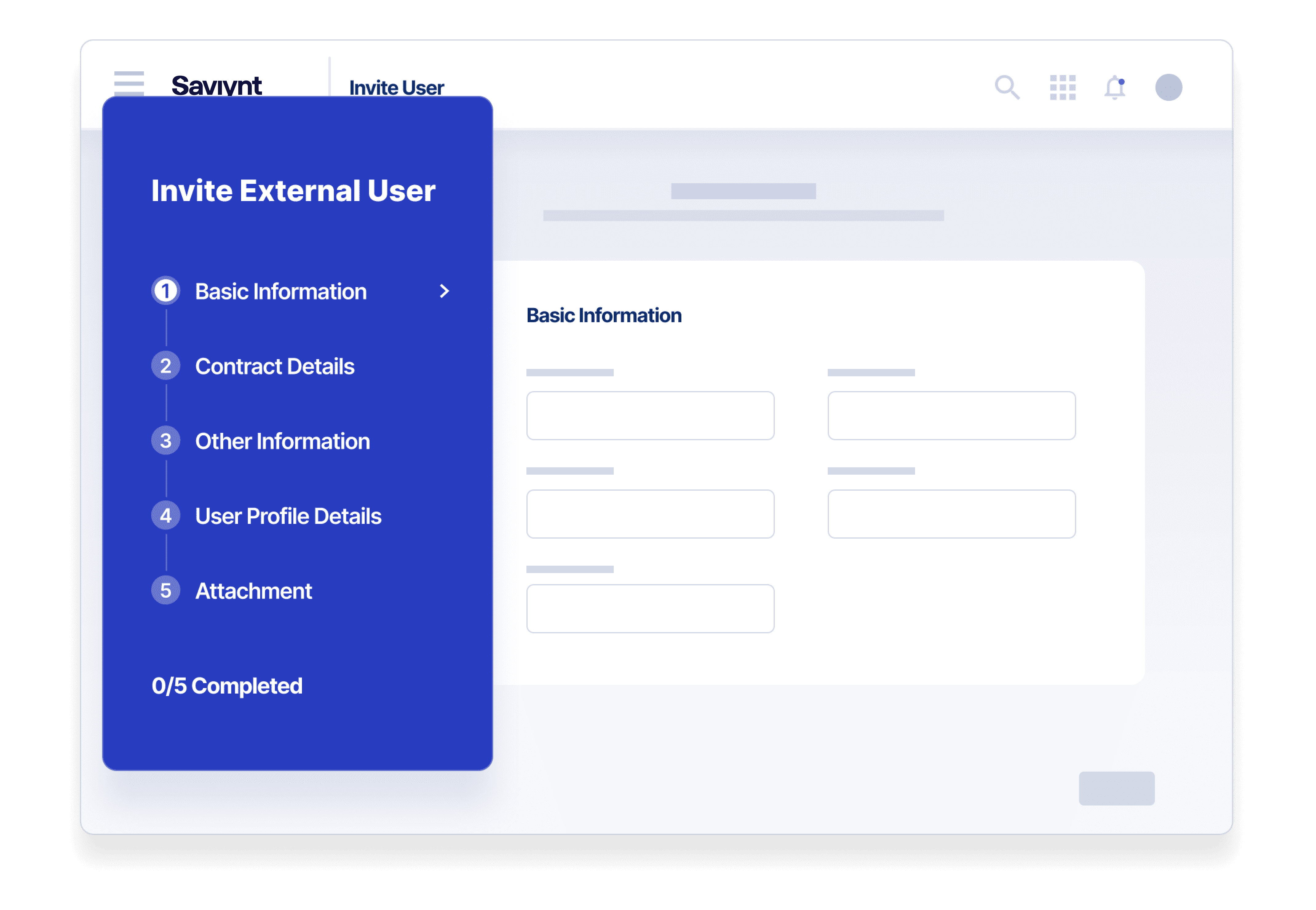
Know Who You’re Dealing With
Collect third-party non-employee data collaboratively with internal and external sources throughout the relationship
- Use a sponsorship model to ensure better communication with third-parties
- Assess vendor risk prior to onboarding with risk-based creation policies
- Enhance external risk visibility with integrated SIEM and UEBA security monitoring data
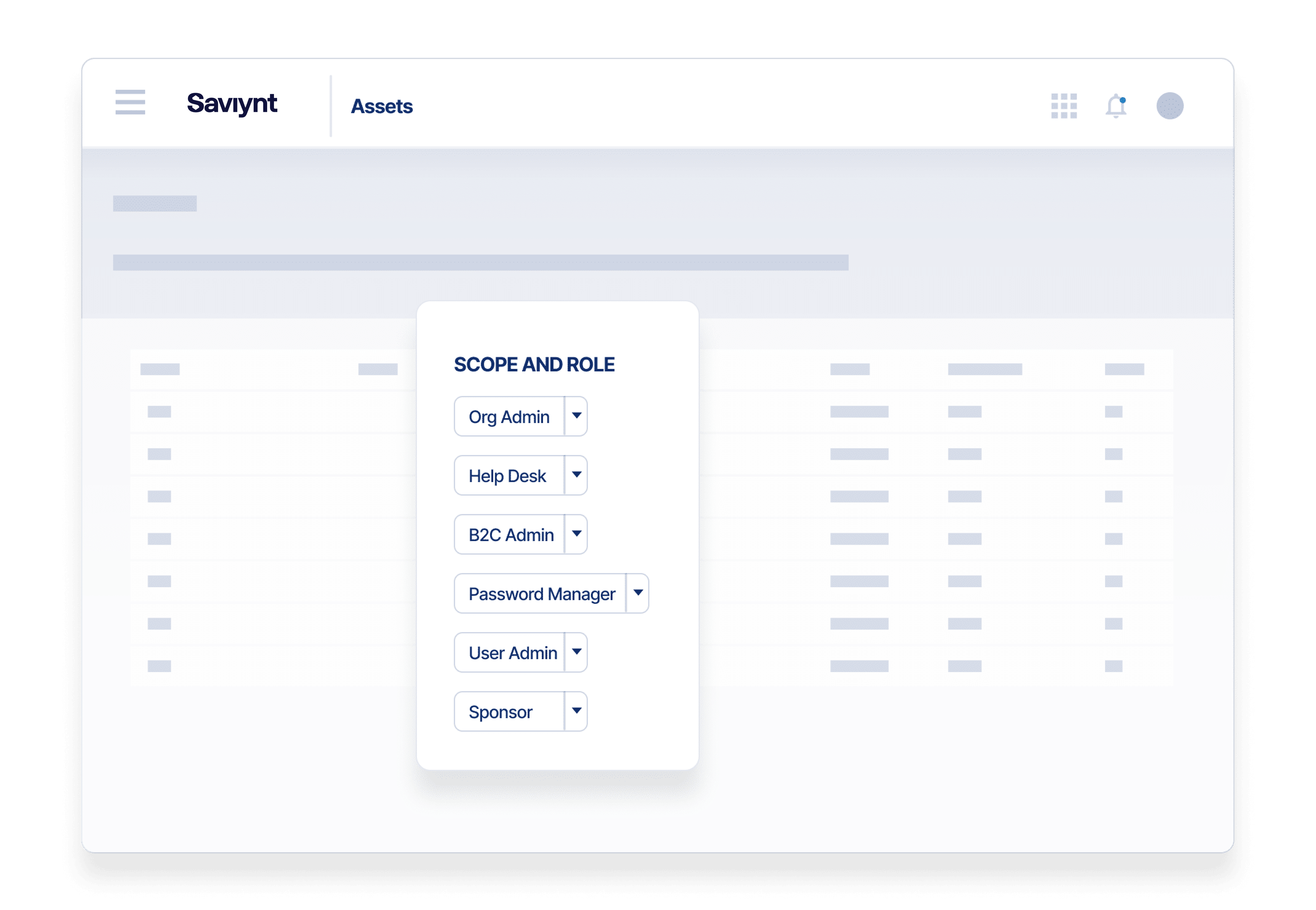
Secure Third-Party Access At Scale
Quickly onboard, provision, monitor, audit, and remove time-bound relationships
- Reduce time and operational costs with onboarding delegation
- Automate low-risk access with intelligent out-of-the-box and custom controls and policies
- Escalate high-risk third-party access requests for additional review and add just-in-time privileged access capabilities with Saviynt PAM
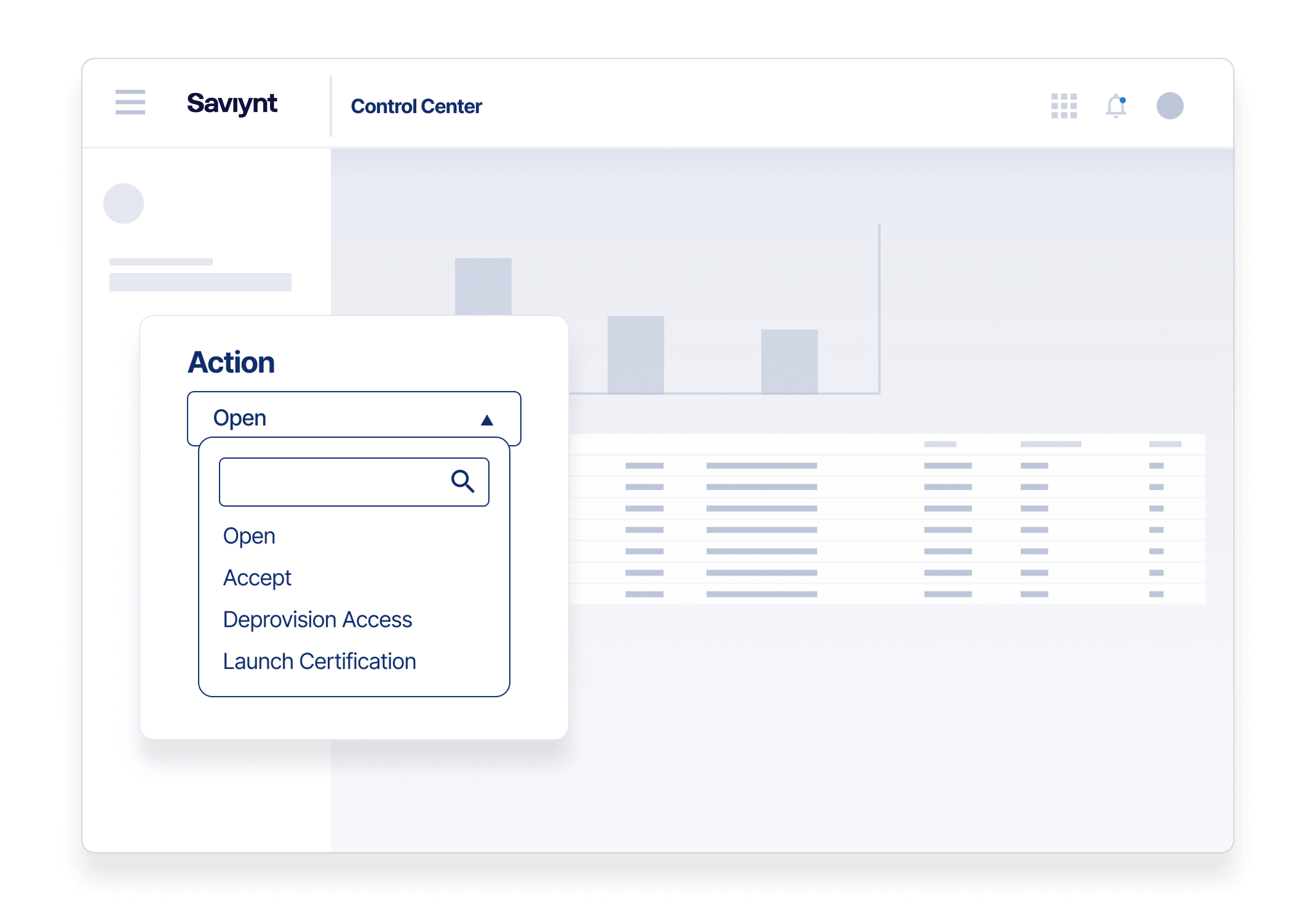
Enforce Least Privilege Access Governance
Assign right-time, right-level access to external workers and suppliers
- Grant external users the access they need from day one for a delightful user experience
- Leverage Saviynt’s Intelligent Identity Warehouse to accelerate audit prep and provide full documentation with compliance reports and dashboards
- Comply with regulations like SOX, HIPAA, PCI DSS, GLBA, ISO 27002, and FISMA,
See Everything. Protect Everything.
Control the entire third-party access lifecycle from first introduction to relationship completion
- Use a sponsorship approach for consistent vendor onboarding
- Reduce orphaned accounts with time-bound access
- Secure infrastructure and sensitive data with advanced monitoring and access denial capabilities
Identity Complexity Across Industries
Today’s modern organizations depend on a complex web of third party suppliers, partners and non-employee workers to meet business and mission goals. Saviynt External Identity Management is built to help you gain control over B2B identities across all sectors. Here are a few examples of our industry solutions.
External Identity Management for Financial Services
Protect clients’ personal & financial data and simplify compliance with SOX, FINRA, GDPR, DORA & more.
External Identity Management for Healthcare
Simplify access & compliance for suppliers, affiliates and independent clinicians.
External Identity Management for Higher Education
Aggregate identity sources for staff, students, and alumni. Support scenarios like student-staff personas and students accessing alumni networks.
External Identity Management for Manufacturing
Improve collaboration and control with suppliers, contract labor and RPA processes at the identity layer.
External Identity Management for Retail
Onboard and manage your flexible workforce with greater speed and clarity.
External Identity Management for Energy
Protect critical infrastructure from cyber threats at the identity layer.
External Identity Management for Federal Government
Inventory third-party users and create more trusted, strategic relationships.
Customers Share Their Stories
The world’s largest organizations trust Saviynt to protect themselves
from cybercriminals and data breaches.
Modernizing Legacy IGA For Wienerberger
“We had a seamless Saviynt integration of our key applications such as SAP and were able to go live fast after the PoC. It’s the first time we have an integrated view available starting with IAM into SoD and privileged authorizations but also further into process and mitigating controls.”
Andree Niebuhr
Head of IAM and SAP Compliance, Wienerberger AG

Securing Compliant Access for Origin Energy

Origin Energy found Saviynt reduced birthright provisioning from ten days to 24 hours, automated provisioning to their core applications, automated attestation approvals, and reviews, and eliminated manual spreadsheet analysis.

Resources for your identity journey
.jpg)
On-Demand Webinars
Powering and Protecting the Extended Workforce with an Identity-Centric Approach

Whitepaper
The Hidden Risks of Third-Party Access

EBook
Five Steps to Effective Third-Party Access Governance

On-Demand Webinars
Unlocking the Promise of Productivity in Your Third Party Workforce

On-Demand Webinars
Al and ML - Transforming the Future of Identity Security?
On-Demand Webinars
Best Practices for Implementing Third-Party Access Management

Solution Guide
Saviynt & SDG: Dynamic Duo Cracks the Code on Third-Party Risk

Solution Guide
External Identity and Risk Management

Solution Guide
External Identity Governance for Healthcare Providers

On-Demand Webinars
Use Identity Convergence to Collaborate More Securely with External Partners
Third Party / External Identity Management: FAQs
What is third-party governance?
Third-party governance involves the processes and controls an organization uses to manage its relationships with external parties such as vendors, suppliers, and service providers.
It's critical to ensure that these outsiders don't introduce any security issues and vulnerabilities. For instance, when a freelancer is onboarded into the system, they are not given access to sensitive data that is not needed in their day-to-day work.
To do this, third-party governance and risk management solutions must be in place.
Effective third-party management/governance requires carefully assessing relationships and implementing appropriate controls to mitigate external risks. This may include conducting due diligence on potential third-party partners, negotiating contracts, clearly defining responsibilities and performance expectations, and monitoring third-party partners closely.
Third-party identity management (TPIM) is a vital part of governance. This involves managing the lifecycle of third-party accounts, including onboarding, provisioning, access management, and offboarding. It also uses authorization and authentication technologies, like multi-factor authentication (MFA), to lessen the risk of hackers compromising the system through third-party accounts.
Why is external identity security important for business?
Applying rigorous identity security & governance to your external and third-party users is a critical step in mitigating risks of a cyber attack or compliance violation.
As organizations rely on outside partners, suppliers and contractors to perform critical functions, they also open the door to increased risk for companies of unauthorized access to sensitive data or systems that could be compromised.
The problem is that third parties accessing your system are beyond your control. They can easily share their credentials (willingly or accidentally) with hackers, who can then gain entry into your system.
External identity management can't prevent this from happening. However, it can prevent the hacker from doing more damage by limiting where they can move inside the network. You can also terminate the account, rendering it useless to the attacker.
In short, ensuring proper third-party access governance will protect your company from potential breaches while helping you stay ahead of the competition.
What are the benefits of external identity management?
External identity management can increase security, simplify compliance, and can help reduce operational headaches. By mitigating the impact of a data breach, organizations can minimize remediation expenses, such as data recovery, legal fees, and reputation damage.
External identity governance also helps companies improve visibility of all the access in your organization, as well what is being done with that access. This improved visibility improves companies' ability to comply with data privacy regulations, such as General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA).
Furthermore, third-party access governance sets clear expectations and mutual trust with all of your B2B relationships partners, helping build stronger relationships, while reducing the burden on your IAM team.
What are common challenges in external identity access control?
Strengthening secure access is perhaps the key challenge with third-party access control. Companies have minimal control over how external third-parties protect their login credentials—and no guarantee they can access your network from a secure workstation.
Thus, credentials must be regularly rotated and supported with other methods like MFA to boost security.
Monitoring third parties access is critical but time-consuming work. Unfortunately, not doing this exposes you to risks you may not be aware of, and if you do detect something suspicious, you need a way to enforce immediate action.
Saviynt helps resolve these issues with robust risk assessment during onboarding, data protection, continuous monitoring, privileged access management and seamless third-party access without a VPN.