The Identity Cloud for Healthcare Providers
Protect patient care and enable new digital health services.

Safeguard access with identity intelligence and
automated monitoring & remediation




Empower your clinicians
Deliver exceptional patient care wherever they are with right-time,
right-level access to critical digital tools and records
Remove barriers to patient care by natively integrating with EHR systems such as Epic and Cerner.
Secure patient, staff, and third-party identities on a single cloud-based platform.
Reduce security team workloads through automation and managed services.
Ensure data privacy and stay in continuous compliance with HIPAA, HITRUST, PCI, and other regulations.







Identity solutions for every use case
Modernizing legacy solutions
Multi-cloud governance
Workforce identity management
Machine identities
Continuous compliance
Zero Trust identity
M&A and divestitures
Remove the barriers slowing down your business transformation.
Lower costs, reduce enterprise risk, and increase productivity with the industry’s #1 converged identity platform. Eliminate technical debt, visibility gaps, and manual processes with a flexible SaaS solution built with powerful AI/ML capabilities that centralizes identity governance with strong and complete identity lifecycle management.
Secure your multi-cloud workloads and accelerate cloud adoption.
Aggregate data across multiple management consoles for more granular visibility. Intelligently manage identity processes, including provisioning via easily configurable policies and controls. Take control of every identity across your multi-cloud environment with the #1 converged identity platform.
Empower your people from day one, wherever and whenever they work.
Make it easy for employees, contractors, and partners to access the applications, systems, and data they need with the #1 converged identity platform built to protect everywhere people work.
Take control of machine identity management complexity and risk.
Apply Zero Trust principles to govern machine identities and move beyond basic controls for an identity-centric security approach. Gain a single view of all machine identities, including cryptographic keys, x509 certificates and other credentials from IoT devices, virtual machines, containers and bots to properly govern machine identity lifecycles.
Stay on top of audit and compliance requirements.
Maintain and sustain compliance with an identity security platform that centralizes management and reporting for relevant regulations and industry standards. Ensure complete audit trails, provide cross-application separation of duty (SoD) administration, and gain advanced, risk-based intelligence for fine-grained entitlement management across your entire application ecosystem.
Secure your identity perimeter with unparalleled visibility and control.
Make Zero Trust the foundation of your security by leveraging granular identity intelligence to enforce least privilege and right-time, right-level access. Maintain agility and administer access across multiple platforms, vendors, and deployment models and prevent breaches with real-time anomaly data.
Maximize the success of mergers, acquisitions and divestitures from day one.
Simplify identity security in rapidly changing business environments with a holistic view of identity access and activity with an authoritative identity warehouse that accelerates access rights planning, eliminates duplicate identities, and contains overprovisioning.
Deliver Secure Access From Day One
Ease administrative burdens on clinical staff across your organization:
- Automate complex EHR approval and provisioning
- Request access from anywhere — via browser, and collaboration platforms
- Streamline user onboarding and offboarding
- Provide seamless access as users change roles or departmentsGain granular access visibility and control for any application, even EHR systems
Simplify Your Identity Environment
Provide better support and improve efficiency without driving up costs. Converged IGA, PAM, and external and application access governance on a single platform can:
- Centralize administration and authoritative identity data sources
- Eliminate siloed and legacy system redundancies
- Automate EHR & access provisioning, requests, and approvals
- Use pre-built templates, control libraries, and app onboarding workflows to accelerate access
- Consolidate internal and external identity lifecycle management
- Leverage existing forms, tools, and user interfaces with our REST API library to maintain user continuity
Protect Patient and Organizational Data
Gain 360° app and identity visibility to ensure least-privilege access and zero trust — even for shadow IT.
- Enhance controls with fine-grained application access and permissions
- Reduce standing privilege risk with just-in-time access elevation
- Automatically enforce time-bound access
- Use analytics to gain deeper insights and strengthen controls
- Enable “one identity for life” with built-in identity matching
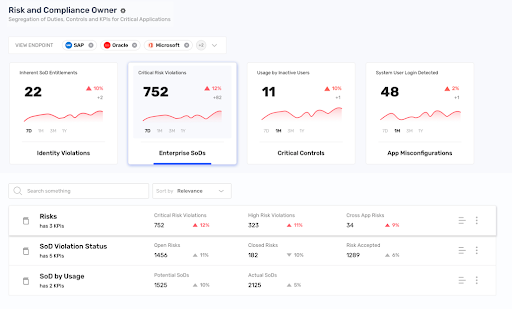
Stay Ahead of Audit & Compliance Requirements
Ensure continuous compliance and constantly monitor for anomalous access and behavior:
- Use built-in controls mapped to HIPAA, HITRUST, PCI, and other regulations
- Oversee cross-application SoD management (detection, monitoring, and compliance)
- Easily compile and deliver attestation reports to auditors and boards with a single source of documentation
- Integrate with learning management systems for training compliance (i.e. HIPAA/EHR)
DON’T TAKE OUR WORD FOR IT

Navigating the Complexities of Identity Access Management in Healthcare: A Journey of Readiness and Realization
Embark on a transformative journey towards a future rooted in digital identity. Watch this on-demand session as Saviynt and EY teams delve into the challenges faced by the modern enterprise in securing the digital identity landscape.
Resources for your identity journey

Solution Guide
Privileged Access Management for Healthcare Providers

Solution Guide
External Identity Governance for Healthcare Providers

Case Study
Pediatric Health System Moves Closer to Zero Trust

Case Study
Syneos Health Futureproofs Identity Governance for Flexibility and Rapid Growth

On-Demand Webinars
Modernizing Healthcare Identity Security
Solution Guide
Saviynt Identity Cloud

EBook
Making the Move to Modern IGA
-1.png)
EBook
PAM Buyer’s Guide
EBook