Workforce Identity Management – Without All the Work
Empower your workforce from day one, wherever and whenever they work.

One Workforce. One Platform. Every Identity.
Simplify Your Identity Stack
Build a Zero Trust Foundation
Secure Remote Workers
Embrace Automation
Unite multiple identity management capabilities into a single platform. Unify controls and risk management for every identity, app, and cloud across your business.
Introduce just-in-time and just-enough privileged access to your workforce identity and access management program. Use pre-built access roles to provide precise access that expires automatically.
Mitigate risk, control access, and secure identities and assets quickly and confidently for all remote identities– including workforce, vendors, or devices.
Automate identity workflows with configurable policies and controls. Automatically grant users low-risk access while escalating higher-risk requests for review.
Workforce Identity Management That Just Works.
Make it easy for employees, contractors, and partners to access the applications, systems, and data they need with the #1 converged identity platform.
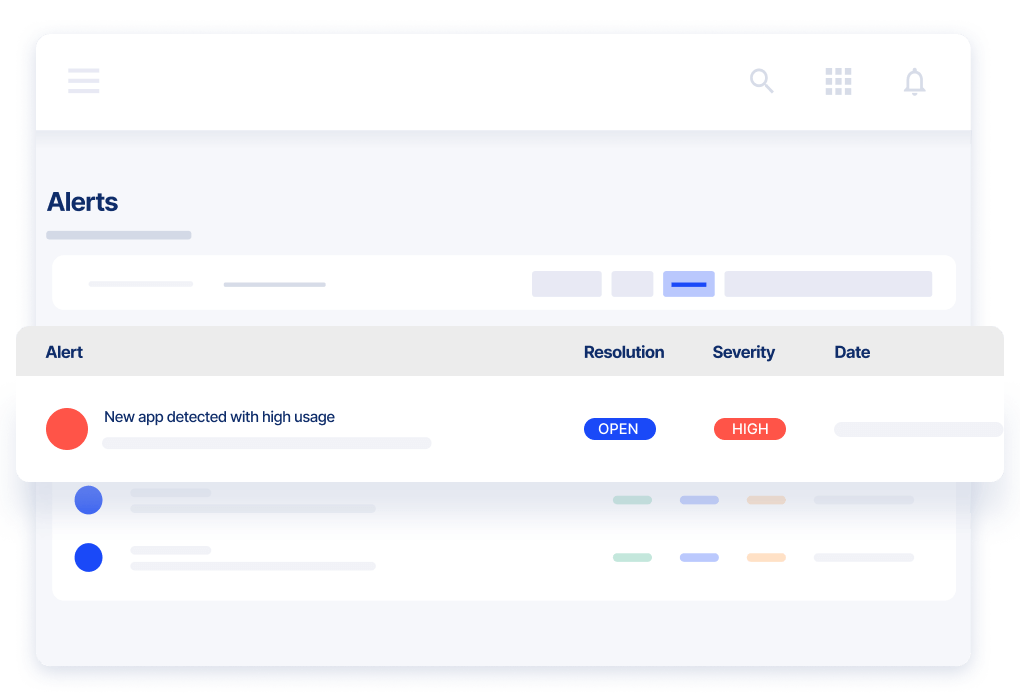
Simplify Security Controls
Monitor control violations, including those granted during emergency elevation. Generate risk-based remediation guidance to improve your team’s effectiveness.
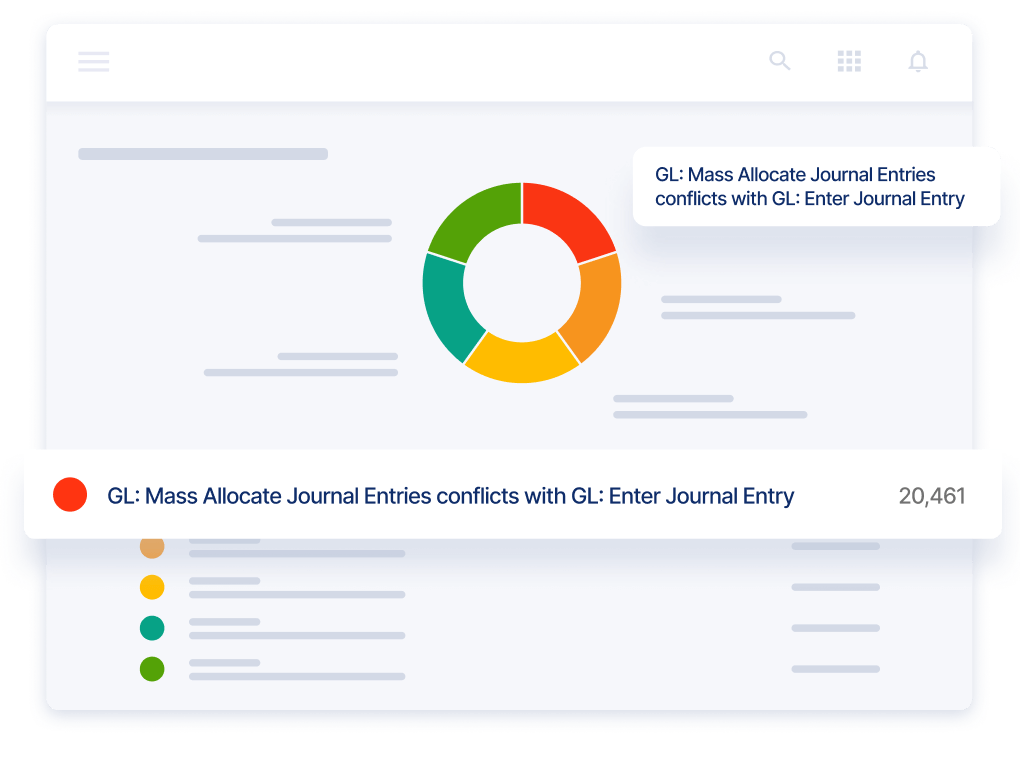
Control Risk Across Multiple Applications
Unlock fine-grained entitlement visibility across your application ecosystem. Decrease fraud risk with well-defined cross-application separation-of-duty (SoD) controls.

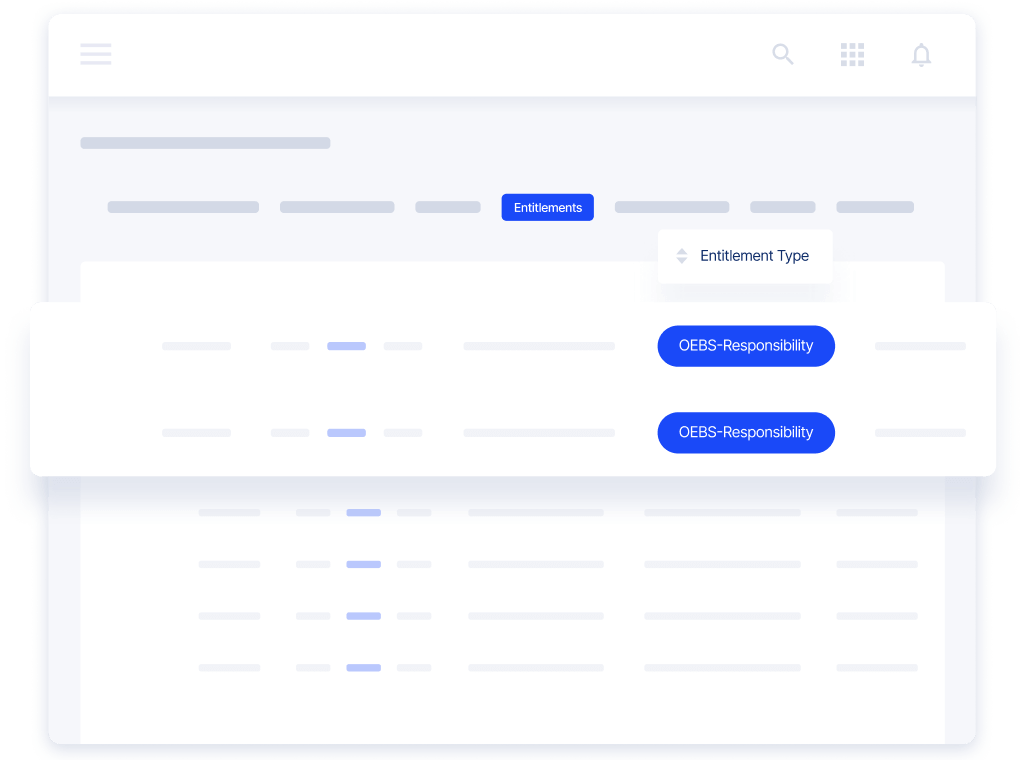
Provide Precise Application Access
Design complex security hierarchies for your workforce identity management program and view any identity’s entitlements – then apply least privilege access across your application ecosystem.
Expedite Onboarding
Onboard people, apps, and machines in minutes and provision least privilege access for a productive Day 1 experience.
Enable Widespread Zero Trust
Amplify Zero Trust via integrations across security ecosystems. Share risk information and application context to holistically govern and manage user access.
.png?width=1532&height=1600&name=Radar%20Image%20Workforce%20Identity%20and%20Access%20Management%20Saviynt%20(1).png)
Saviynt Named a Leader in Frost RadarTM : Workforce Identity & Access Management
Read the latest Frost & Sullivan analyst report







Identity solutions for every use case
Modernizing legacy solutions
Multi-cloud governance
Workforce identity management
Machine identities
Continuous compliance
Zero Trust identity
M&A and divestitures
Remove the barriers slowing down your business transformation.
Lower costs, reduce enterprise risk, and increase productivity with the industry’s #1 converged identity platform. Eliminate technical debt, visibility gaps, and manual processes with a flexible SaaS solution built with powerful AI/ML capabilities that centralizes identity governance with strong and complete identity lifecycle management.
Secure your multi-cloud workloads and accelerate cloud adoption.
Aggregate data across multiple management consoles for more granular visibility. Intelligently manage identity processes, including provisioning via easily configurable policies and controls. Take control of every identity across your multi-cloud environment with the #1 converged identity platform.
Empower your workforce from day one, wherever and whenever they work.
Make it easy for employees, contractors, and partners to access the applications, systems, and data they need with the #1 converged identity platform built to protect everywhere people work.
Take control of machine identity management complexity and risk.
Apply Zero Trust principles to govern machine identities and move beyond basic controls for an identity-centric security approach. Gain a single view of all machine identities, including cryptographic keys, x509 certificates and other credentials from IoT devices, virtual machines, containers and bots to properly govern machine identity lifecycles.
Stay on top of audit and compliance requirements.
Maintain and sustain compliance with an identity security platform that centralizes management and reporting for relevant regulations and industry standards. Ensure complete audit trails, provide cross-application separation of duty (SoD) administration, and gain advanced, risk-based intelligence for fine-grained entitlement management across your entire application ecosystem.
Secure your identity perimeter with unparalleled visibility and control.
Make Zero Trust the foundation of your security by leveraging granular identity intelligence to enforce least privilege and right-time, right-level access. Maintain agility and administer access across multiple platforms, vendors, and deployment models and prevent breaches with real-time anomaly data.
Maximize the success of mergers, acquisitions and divestitures from day one.
Simplify identity security in rapidly changing business environments with a holistic view of identity access and activity with an authoritative identity warehouse that accelerates access rights planning, eliminates duplicate identities, and contains overprovisioning.
Modernizing Identity Governance & Accelerating Compliance Maturity

Saviynt helped Gordon Food Service transform a patchwork of legacy on-premises Identity Management (IDM) systems.
"Before, when we didn’t have a modern solution, we felt stagnant. Today, we’re in a much better place. Overall, the implementation has been a success, and the Saviynt team was fantastic."
Paul Dumbleton
Enterprise Information Security Team Manager

Modernizing Legacy IGA For Wienerberger
Saviynt delivered a comprehensive identity access and management solution
"We had a seamless Saviynt integration of our key applications such as SAP and were able to go live fast after the PoC. It’s the first time we have an integrated view available starting with IAM into SoD and privileged authorisations but also further into process and mitigating controls."
Andree Niebuhr
Head of IAM and SAP Compliance

Workforce Identity FAQs
How can Saviynt help improve identity visibility across my complex ecosystem?
With its deep integration across multiple cloud platforms and enterprise applications, Saviynt’s Identity Cloud provides a single control plane to manage your hybrid, multi-cloud environment, bringing governance to all identity types. Break down siloed security apps and unify human & machine identity and application governance tame identity complexity and cost.
How will Saviynt help me scale application onboarding?
Take control of your identity program implementation with a converged identity experience. Onboard applications once, easily create reports, manage access policies, and configure workflows. Get off to the races in the time it takes traditional tools to “tie their laces.” Use our intuitive, wizard-based onboarding interface and deep API-based integrations to realize rapid time-to-value.
Is it possible to standardize user access across my distributed workforce?
Absolutely! Eliminate insecure manual processes, empower business stakeholders, and delight your extended workforce with a streamlined identity lifecycle experience. With our converged identity platform, you can easily establish a single source of truth for each identity, whether internal employee or external third party. Manage entitlements and enforce least privilege access controls.
Can I really secure workforce identities without multiplying costs, tools, and complexities?
Saviynt solves user access-related security problems and exposes costs from excess subscriptions to improve license management. Turn on PAM capabilities to protect privileged workflows and eliminate rarely-used administrative accounts and subscriptions. Take advantage of application access governance capabilities to surface underutilized license types to support right-sizing. Mitigate third-party access risk with robust role-based access controls.
Resources for your identity journey

Analyst Report
Frost Radar™: Workforce Identity and Access Management 2024

eBook
Just in Time PAM: Time To Turn off “Always On”

eBook
Six Critical Capabilities of Saviynt’s Application Access Governance

eBook