Application Access Governance
Enforce application-centric policies and controls for security and compliance of critical applications
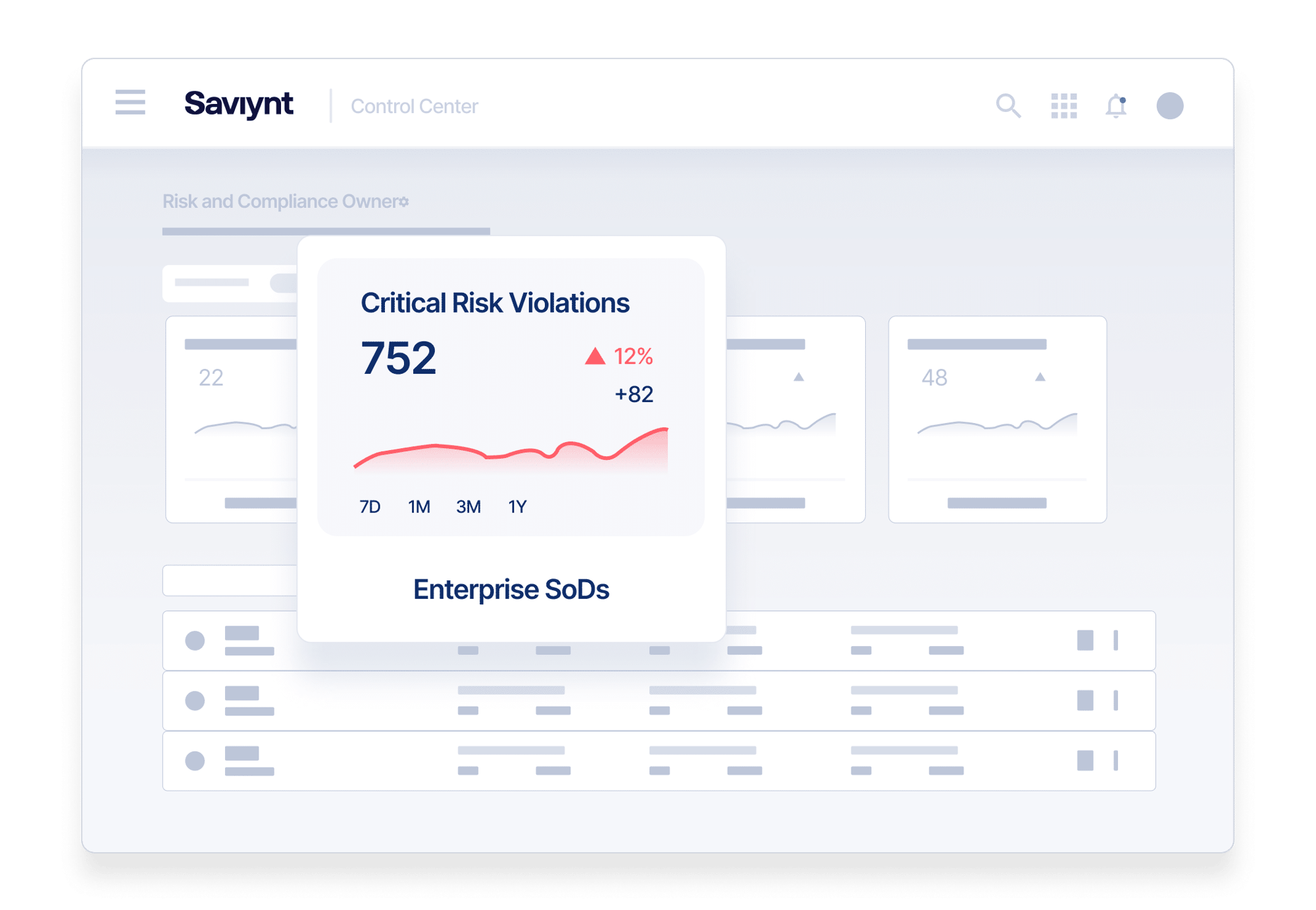

Detect Earlier, Respond Smarter
Rapid cloud adoption means new challenges for IT and security teams. They need consistent, compliant Governance, Risk, and Compliance (GRC) processes across all cloud and on-premises applications.
Prevent Insider Fraud
The challenge? Every application has its own security model to protect privileged and sensitive data.
Your organization needs an automated access governance solution to see across all applications to recognize cross-application access control violations, quickly identify access risks, and stop them in their tracks.
Simplify Risk Analysis and See the Whole Picture
Get fine-grained visibility into complex application security models
Mitigate Risk Across Applications
Reduce segregation of duties (SoD) risks with out-of-the-box risk and security controls.
Manage Real-time Emergency Access
Use “Break Glass” provisioning capabilities to control temporary access & continually monitor access
Ensure Audit-Ready Cross-Application Compliance
Manage multiple applications access and give compliance managers the reports they need
Deploy Cloud-First Application Access
Guard enterprise apps with cloud-architecture in ways that legacy systems can’t
Control Access to Limit Risks
Utilize risk-aware certifications, license management, and alerts on risky requests
Guide Decisions with Insights
Bring critical risks forward for remediation & optimize your security team’s workload

KuppingerCole Report: Saviynt Application Access Governance
An Executive View by KuppingerCole Analysts
Leave No Application Behind

Secure Access for Critical Cloud and On-Prem Applications
Unify access security policies across applications, workloads, and identities with a single cloud-native application governance platform.
- Bring identity management and application GRC under one roof
- Align security policies across apps, devices, and operating platforms
- Prioritize critical risks for remediation using advanced usage analytics
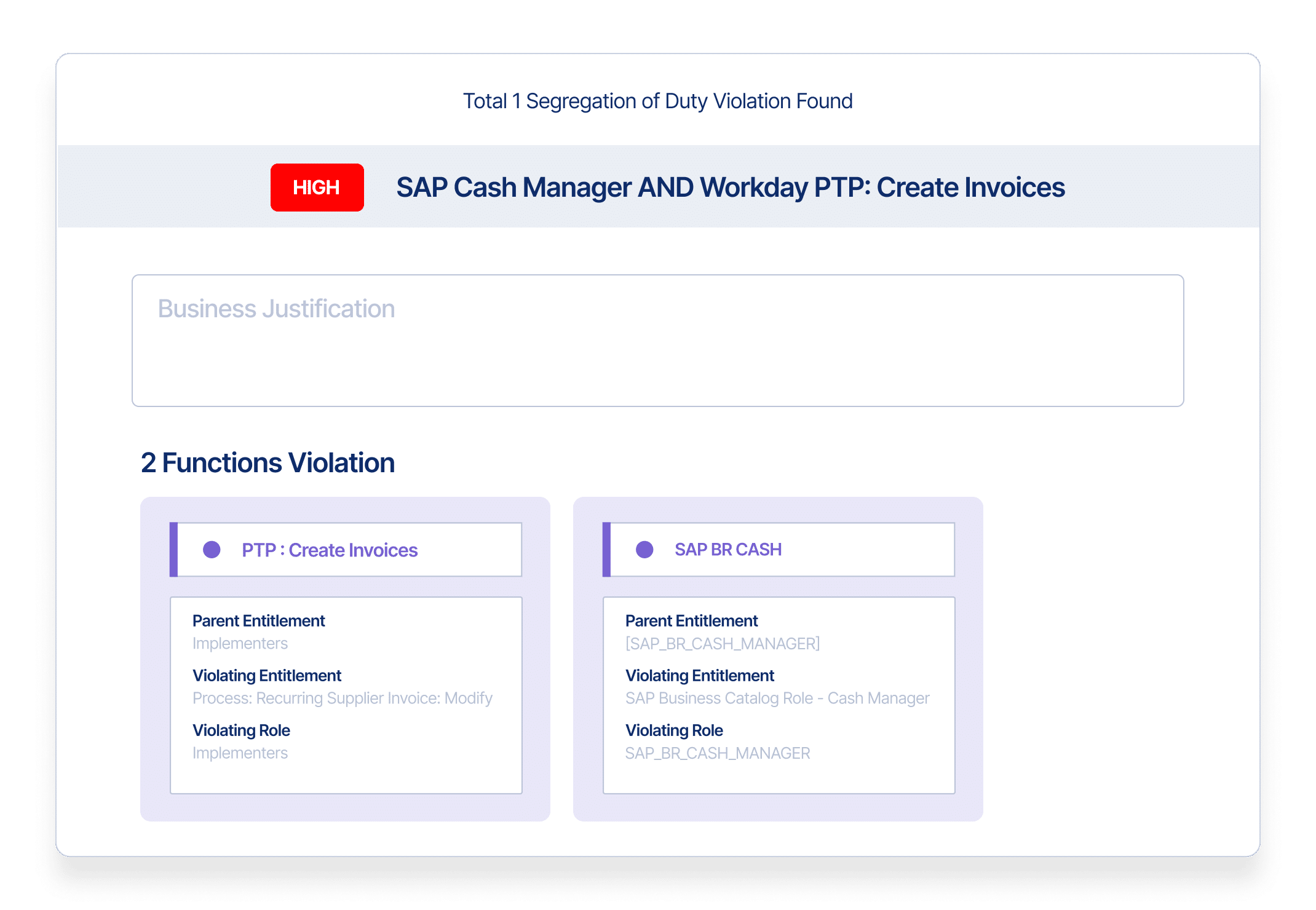
- Detect and prevent cross-application SoD violations before they happen
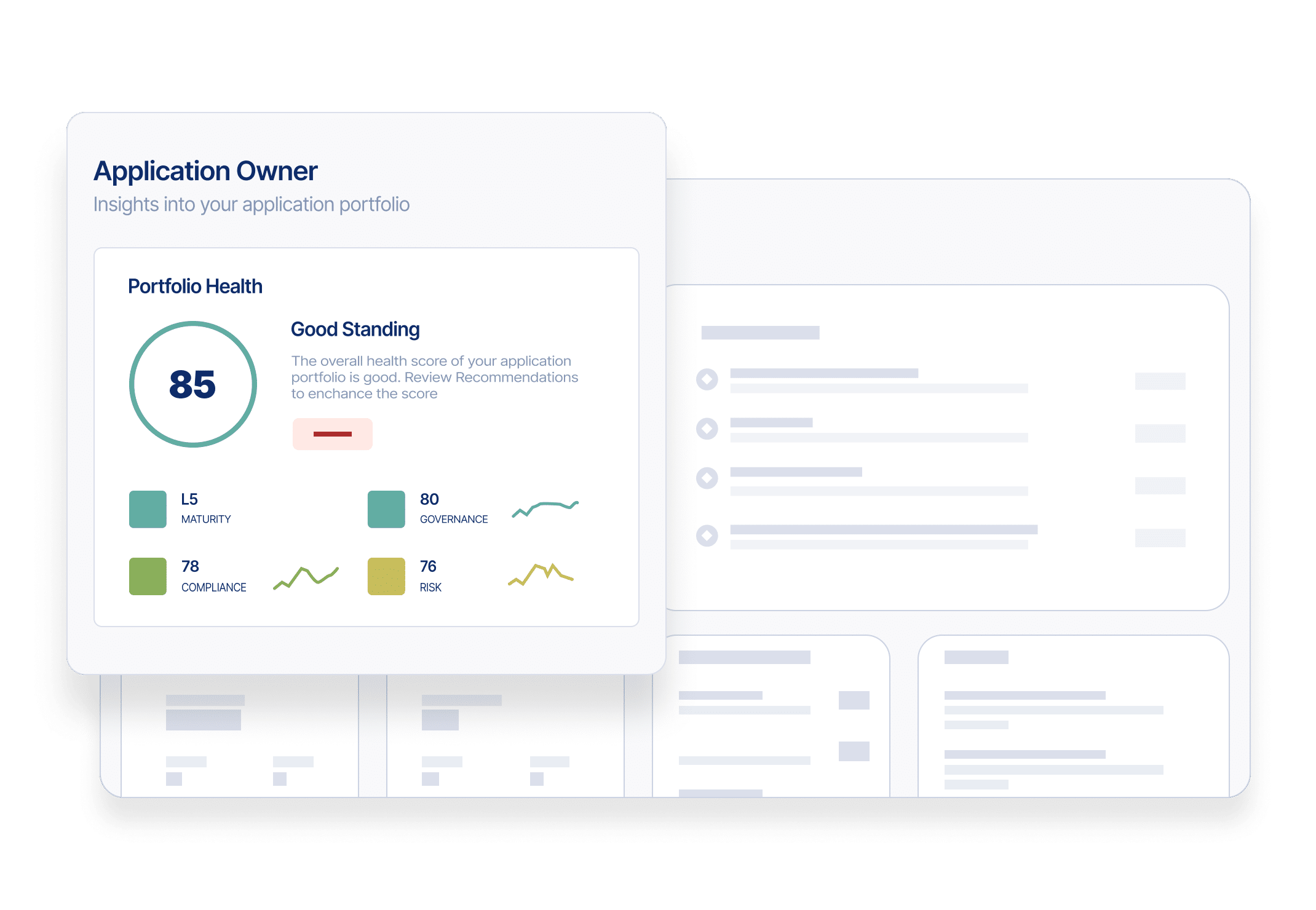
Maintain Audit Readiness at all Times
Understand risks across your application ecosystem with deep visibility, intelligent insights, and continuous controls monitoring.
- Use fine-grained visibility into user access and activity to see actual and potential violations
- Undertake real-time monitoring, compliance, and risk management
- Provide auditors and compliance managers comprehensive visibility, reporting and detailed audit trails
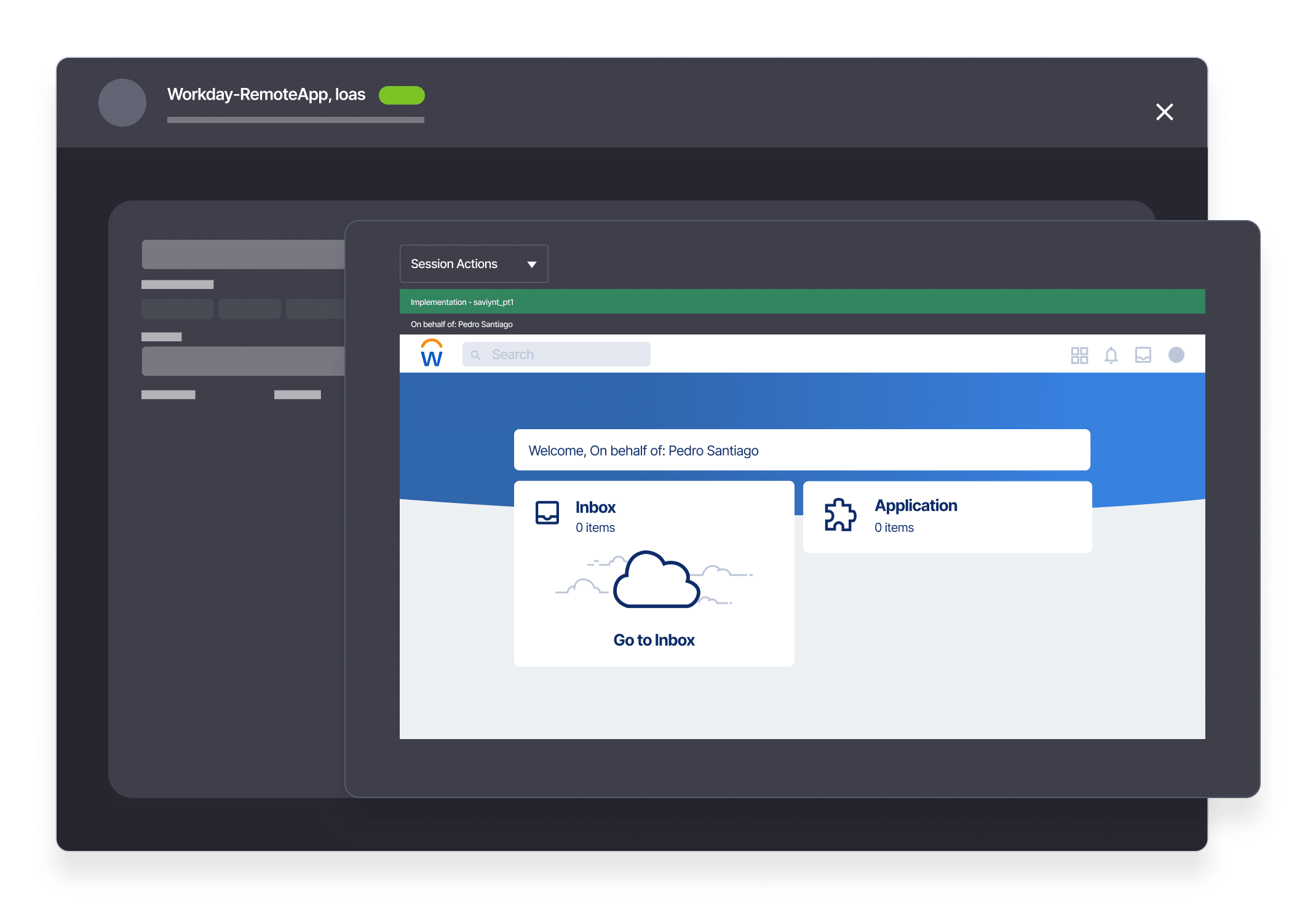
Emergency Access Management that Preserves Compliance
Control emergency access and monitor privileged activity to reduce your organization’s attack surface.
- Securely manage user accounts with elevated permissions to critical resources and sensitive data
- Provide emergency access, monitor actions, and remove access quickly
- Enhance role management with real-time what-if analysis
- Maintain compliance with SOX, HIPAA, PCI DSS, GLBA, ISO 27002, FISMA, CMMC, and other regulations
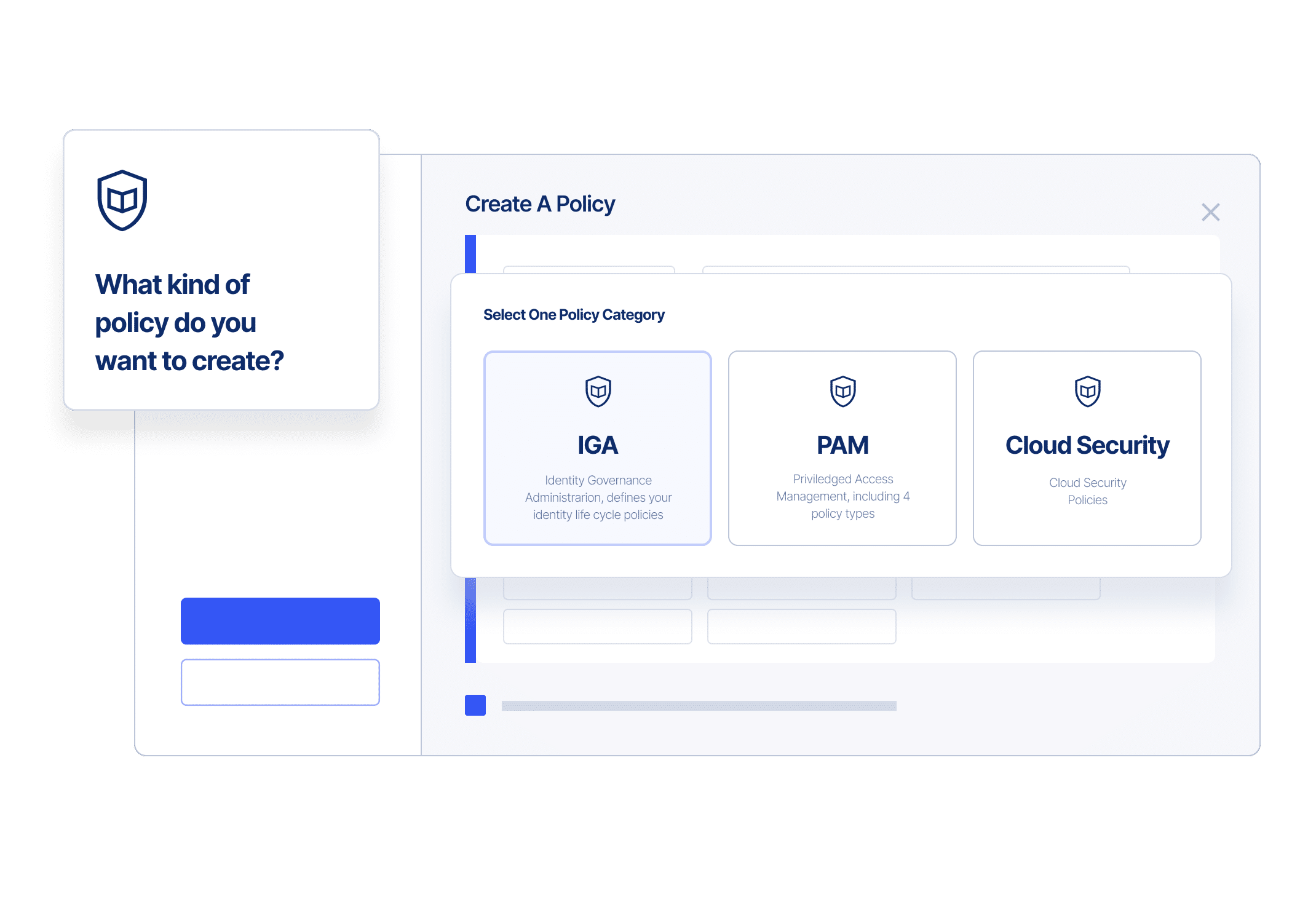
Automated Access Governance That Makes Compliance Easier
Simplify governance without sacrificing security.
- Automate time-bound access and remove access at expiration
- Enforce compliance policies within applications and prevent unauthorized application access or conflicting permissions
- Remove residual access and eliminate orphan accounts
- Get intelligent risk and remediation alerts about certifications, license management, and risky access requests
Go All-in on Zero Trust
Provide least privilege access to applications and support multiple security models.
- Address access needs and risks unique to critical applications such as SAP, Oracle, Workday, and more
- Assign just the right amount of access to critical systems or sensitive data
- Eliminate standing privileges and prevent unauthorized application access to protect against account take over
- Take advantage of deep granular access to apply risk-based analysis
Is Application Access Putting your Organization at Risk?
Take this 10-question 10-minute assessment to find-out!
Customers Share Their Stories
The world’s largest organizations trust Saviynt to protect their privileged accounts from cybercriminals and data breaches.
Award-Winning Deployment Achieves 83% Faster Onboarding

Danfoss transitioned 45k identities across 100 countries with its award-winning Saviynt IGA deployment that delivers 83% faster onboarding for employees.

Journey to the Cloud with Phillips 66 and Saviynt IGA

Saviynt helped Phillips 66 with their IGA modernization initiative
"Our on-prem solution could only manage other things on-prem, and Saviynt has the ability to manage things both on-prem and in the cloud, so that was one of the things that made us realize that this is really a good solution for us in both realms."
Steve Edford
Analyst, Identity and Privileged Account Management

Resources for your identity journey

On-Demand Webinars
Transforming Access Management: Strategies for the New Digital Landscape

Analyst Report
KuppingerCole Executive View: Saviynt - Application Access Governance
EBook
Six Critical Capabilities of Saviynt’s Application Access Governance

Whitepaper
Three Steps to Application Access Governance Maturity

Analyst Report
Saviynt is named a Customers’ Choice in the 2023 Gartner® Peer Insights™ Voice of the Customer: IGA
Application Access Governance: FAQs
What is application access governance?
Application access governance are the processes and procedures a company implements to manage and monitor the access that employees, contractors, partners, and third-party service providers have to its applications.
The goal of an application access governance system is to ensure that only authorized individuals have access to specific applications and data. It grants these privileges based on the person’s job responsibilities, level of authority, risk factors, and other relevant criteria.
Implementing application user access management requires a collection of tools and technologies working together. This includes authentication and authorization protocols, data protection technology like encryption, identity and access management (IAM) platforms, and periodic access review.
Why is application access management important for businesses?
Application access management is critical because it allows businesses greater control over their applications’ use.
Unrestricted application access can be a significant security risk for companies, increasing the chance that malicious users will access sensitive data or perform illegal actions. Without this safeguard, it becomes easy for hackers to install and execute malware in the system.
An application governance model can prevent this by limiting access to only pre-approved software and data. Such access can only be granted based on criteria like role or risk profile and can be easily revoked if suspicious activity is detected.
What are the benefits of automated access governance solutions?
One of the key benefits of application access governance is enhanced application and data security. By controlling who has access to what app, businesses can reduce the risk of data breaches, cyberattacks, and other security threats.
These access governance solutions also improve efficiency, ensuring employees have the right level of access to the right applications and data for the right amount of time. And, by reducing the likelihood of data breaches, access governance solutions can help prevent data recovery fees, penalties, and lawsuits. Furthermore, limiting access means you can reduce software license fees and subscription costs (in the case of SaaS).
Another benefit is compliance. Many businesses are mandated by data regulations such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS). Access governance can help organizations comply with these by ensuring that sensitive data is restricted only to those authorized to access it.
But the best benefit of all is an improved reputation. Automated access governance solutions help prevent breaches that could damage consumer faith, leading to decreased revenue. Access governance also demonstrates to stakeholders that you take data security seriously.
What are common challenges in application governance?
There are a few common stumbling blocks to implementing an effective application security model.
The chief challenge is a lack of visibility. Organizations might not always have a clear line of sight into who has access to what applications and data.
Another is complexity, as access governance involves multiple technologies, policies, and procedures that must work seamlessly. Designing an effective access governance model for larger organizations can be especially tricky.
Finally, user management. Ensuring people can use the applications they need for their job while limiting unnecessary access is a complex balancing act.
The good news is that you can mitigate most of these challenges with the proper application access governance program.
What are some application service governance best practices?
Access governance starts with a clear policy outlining access control requirements for all applications and data. This policy should then be communicated to all employees and stakeholders.
Once a policy is in place, you can use role-based access control (RBAC) to implement it. This allows you to assign people specific roles, giving them access to relevant resources. The approach can simplify access management and reduce the risk of errors.
You should also automate access provisioning and deprovisioning to update access when the user is onboarded or when they leave. This reduces the risk of orphaned accounts that attackers can easily compromise.
Finally, you should provide training and education to your employees. Explain the importance of access governance and how they could comply with relevant policies and procedures.