What is Cloud Infrastructure Entitlement Management?
What is CIEM?
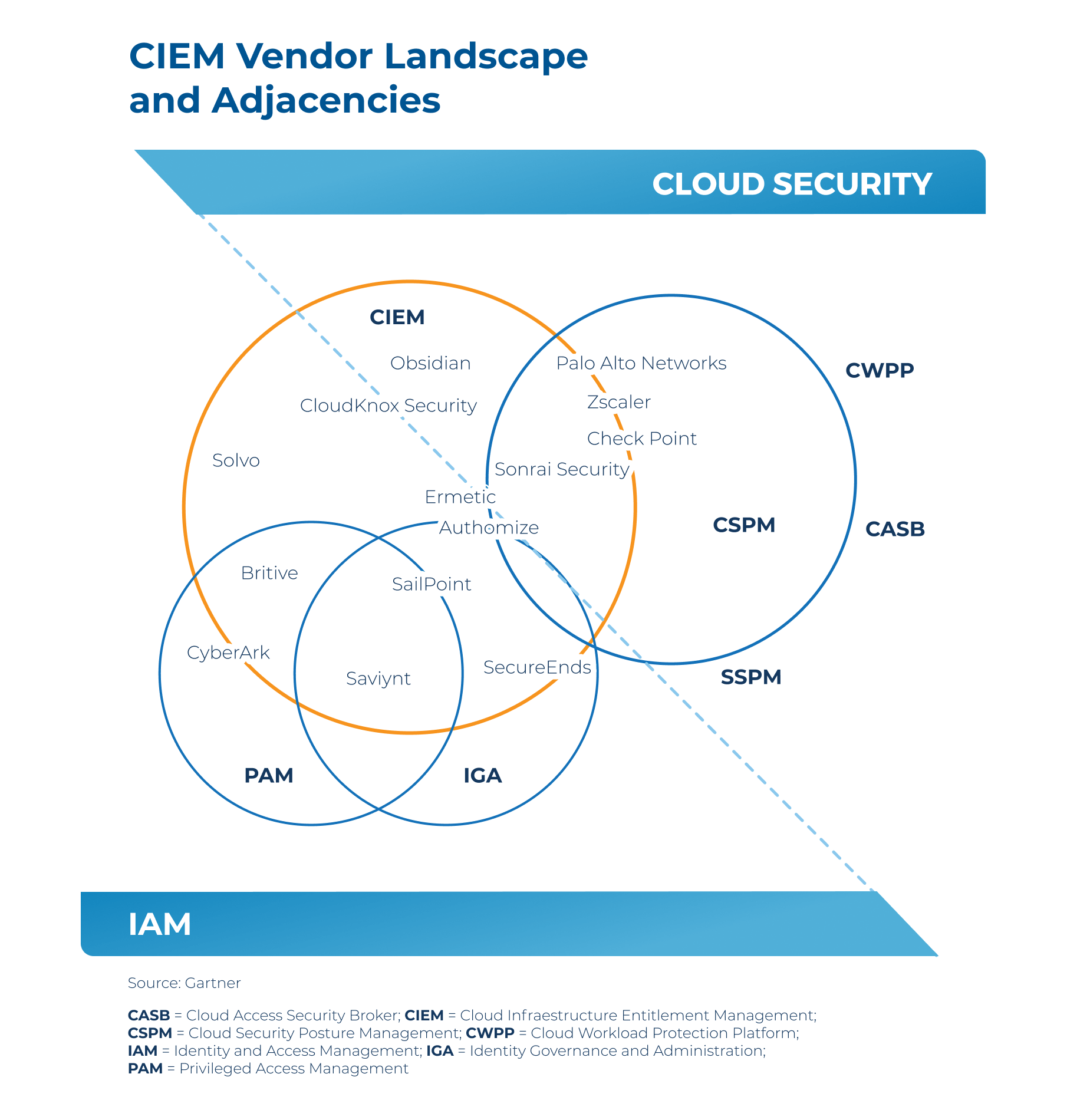
CIEM is part of an emerging new access control solution area in Cloud Security introduced in Gartner’s 2020 Cloud Security Hype Cycle. According to Gartner, cloud Infrastructure Entitlement Management (CIEM) is a specialized identity-centric SaaS solution that manages cloud access risk using time-limited access controls. Using analytics and machine learning to detect anomalies, CIEM manages entitlements and data governance in both hybrid and multi-cloud IaaS architectures. Given the complexity of managing access controls in the cloud, CIEM aims to streamline the implementation of least privilege access controls in highly-dynamic organizational IT environments.
The Challenges of Managing Entitlements in the Cloud
Cloud Infrastructure Entitlement Management (CIEM)’s Business Impact
CIEM is designed to protect data and prevent overly permissive or unintended usage. By reducing accounts that have been orphaned or have too many permissions, CIEM tools work to prevent data breaches. What makes it different from other forms of data protection? Automation.
Automation simplifies complex processes and scales with the cloud by utilizing policies that grant access only when necessary — and remove it when it’s not. This increases operational efficiency and creates an audit trail, making it easier to verify compliance and document evidence.
Increased Visibility
The CIEM discovery process is the part of its lifecycle that uncovers the unique human and machine entities that can access your cloud ecosystem. It identifies risk by analyzing user behaviors and resource access across the cloud ecosystem. In combination with how access policies are implemented, this identity information allows the CIEM solution to calculate risk and enforce least privilege. The discovery process continues throughout the lifecycle to ensure new identities are incorporated as they emerge.
Efficient Automation
CIEM incorporates automation to set fine-grained permissions across cloud assets. Instead of manually setting and configuring permissions and access every time a new asset or workload is created, CIEM automatically enforces policy configurations. Manually configuring this by hand is tedious — and prone to errors and oversights. You run the risk of leaving assets open or non-configured, creating opportunities for attack. Automation ensures consistency no matter how quickly assets scale up or get removed.
At the end of the day, incorporating CIEM into your security posture reduces the likelihood of a data breach.
Saviynt & Cloud Infrastructure Entitlement Management (CIEM)
Take An Integrated Approach
- Entitlement discovery
- Policy management
- Access provisioning
- Privileged access management
- Monitoring
Resources