What is Health Insurance Portability and Accountability Act (HIPAA)?
What is the Health Insurance Portability and Accountability Act (HIPAA)?
The Health Insurance Portability and Accountability Act (HIPAA) is a United States regulation enacted in 1996 that addresses how Personal Identifying Information (PII) of patients should be managed by healthcare providers. It also provides protections for those who lose their healthcare coverage by creating options and enhancing the portability of Personal Health Information (PHI) for patients when they lose or change their jobs. The primary goal of the regulation is to enhance the privacy of patients by preventing their data from being shared without their consent so as to protect the data from theft and fraud.
The regulation applies to both “covered entities,” healthcare providers who retain or transmit PHI, and their “business associates,” vendors or partners who interact with PHI on behalf of the providers. The regulation is broken down into the following rules:
-
The Privacy Rule
Sets the standards for how PHI is used by providers, who can view this data, and guidelines for how it may be shared. The privacy rule also dictates how patients can access their data and requires the development of policies for the governance of this data.
-
The Security Rule
Sets the standards for how PHI is secured by healthcare providers. This includes the protection of PHI within Electronic Health Records (EHR) and guidelines for the storage and maintenance of these records.
-
The Omnibus Rule
Sets the standards for the legal agreements that must exist between healthcare providers and “business associates” who interact with PHI.
-
The Breach Notification Rule
In the case of a security breach, this rule outlines how patients must be notified of a breach and how such breaches must be legally reported.
-
The Enforcement Rule
The enforcement rule enables the US Department of Health & Human Services (HHS) to conduct compliance audits and enforce HIPAA regulations. HIPAA violations may lead to fines as large as $1.5M.
How to Achieve Compliance with the Health Insurance Portability and Accountability Act (HIPAA)
HIPAA-mandated entities need to enact robust and comprehensive healthcare data security measures, including a solid identity governance solution to address security and compliance requirements proactively. Keeping up with the challenges of managing third-party business associates requires a modern Identity Governance and Administration (IGA) platform that handles a rapidly changing workforce and aligns with HIPAA’s stringent privacy requirements.
Legacy solutions that utilize high-level or coarse-grained access controls fall short of the challenge as they do not fully meet nuanced HIPAA privacy restrictions. These solutions often provide high-level application restrictions without any in-depth visibility, rarely address the needs of a multi-cloud ecosystem, and too often lack detailed analytics. Legacy systems must be replaced or supplemented otherwise, healthcare organizations risk potential disclosure of patient health data and regardless of whether the breach is malicious or accidental, the result remains the same.
Let’s break down some of the requirements for HIPAA compliance.
Policy Creation
HIPAA requires that both healthcare providers and their business associates create and maintain privacy and security policies that prove they are adhering to HIPAA regulations. These policies must be communicated and taught to staff, and staff must sign agreements confirming their knowledge of the policies. Patients are also required to sign privacy agreements that inform them on how their PHI is managed and shared and provide options for how they may access their data.
Assigning Officers
HIPAA compliance requires that providers specify a Privacy Compliance Officer who manages the creation of privacy policies and keeps up with the latest HIPAA regulations. HHS also suggests larger organizations form a committee that oversees this officer and ensures that the organization remains in compliance. The Privacy Compliance Officer is also responsible for ensuring that policies are communicated and agreed to by staff and patients.
Organizations are also required to have a HIPAA Security Officer whose responsibility is to detect, manage, and respond to potential PHI security breaches. This officer should conduct risk analysis and audits to ensure breaches are predictable and detectable.
Security Controls
HHS has developed robust guidelines for the security controls that should be in place to ensure HIPAA compliance. In order to secure EHR, the security rule outlines three areas of focus:
- Administrative – governs the documentation of security policies, the specifications for Identity and Access Management (IAM) systems, guidelines for staff training, and the assessment of security controls.
- Physical – governs the requirements for physical access to EHR via workstations and other mediums.
- Technical – governs the technical requirements for access control to EHR ensuring employees of providers and business associates only have least-privilege access to the data required for their specified role. Technical requirements also include the encryption of PHI, the transmission of data, and controls for the hardware and software that store and manage EHR.
Internal Audits
HIPAA requires that healthcare providers conduct annual internal audits and risk assessments to ensure they remain in compliance.
Agreements with Third-Party Business Associates
Healthcare providers must ensure that any business associates who interact with PHI are HIPAA compliant. Agreements must be established that confirm their status.
Notification of Breaches
In the event of a security breach of PHI, providers are required to report the breach and notify patients whose data was compromised. Failure to report the breach appropriately may result in significant fines.
Documentation
Organizations are required to document all HIPAA policies, internal audits, risk assessments, training, and processes. During an HHS audit, all this documentation will be reviewed to ensure the organization has taken the necessary steps to achieve compliance.
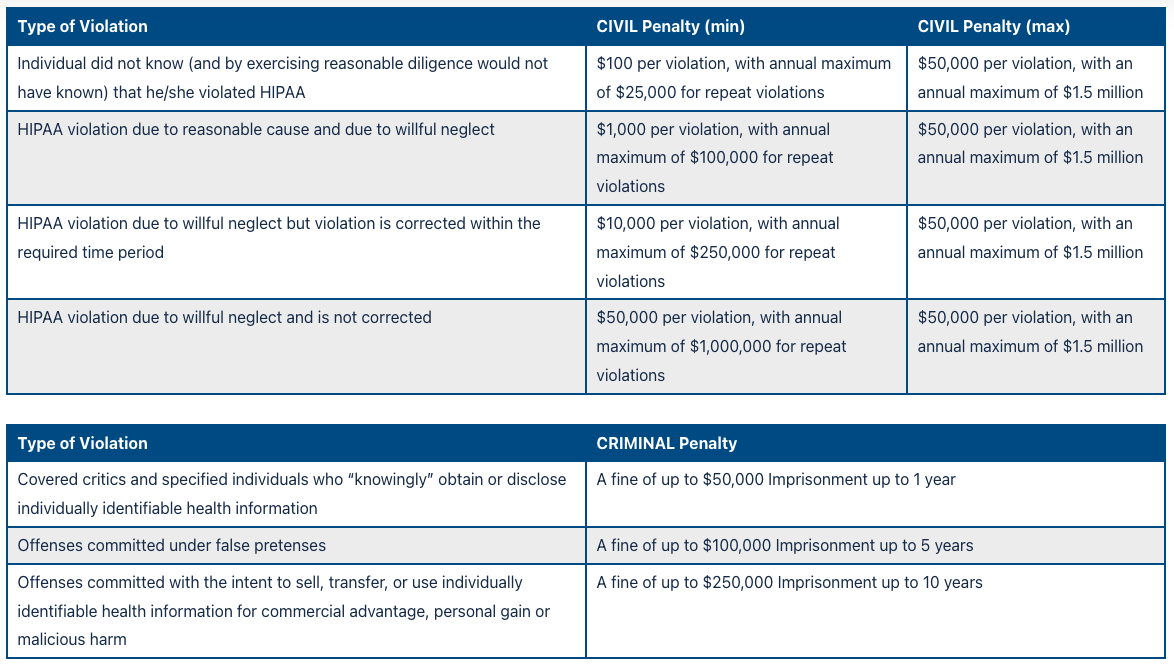
Consequences of Non-Compliance with HIPAA
Failure to adhere to HIPAA regulations may result in significant fines. The regulation outlines the following penalties.
Saviynt & the Health Insurance Portability and Accountability Act (HIPAA)
Saviynt Healthcare Identity Cloud is designed to provide seamless identity management, accelerate implementation timeframes, and help providers comply with regulations such as HIPAA, SOX, and PCI with pre-configured industry workflows and deep electronic healthcare record (EHR) platform integrations.
Intelligent Risk Analysis
Risk analysis and the implementation of risk-based controls are core HIPAA security requirements. Saviynt’s Healthcare Identity Cloud Platform offers healthcare organizations a single, centralized Intelligent Identity Hub to meet these requirements. Saviynt’s solution consumes, exchanges, and analyzes risk information by pulling data points that once were separate into a single interface, eliminating silos and streamlining security. Saviynt’s Risk Exchange builds a full portrait of an identity’s access and risk information by pulling in access analytics, usage analytics, individual user activity, and inherent user risk from across the entire IT ecosystem, including both the organizational cloud presence, UEBA, SIEM, CASB, and on-premises systems. Curating and combining these data sources into a single-pane-of-glass interface gives in-depth visibility into anomalous behavior and access.
Intelligent Compliance
We provide native integration with EHR platforms such as Cerner, Epic, and Meditech while also integrating with the most business-critical ERP, IaaS, PaaS, and Software-as-a-Service (SaaS) solutions used in the healthcare industry. Our platform provides a single location for managing HIPAA, HITECH, PCI, SOX, and other compliance requirements and connects across cloud-based infrastructures so that the organization can maintain compliance with internal Separation of Duties (SoD) policies as well as external governmental and industry-standard requirements. Saviynt comes with over 250 security controls and risk signatures available out-of-the-box. These controls directly map back to industry standard compliance frameworks such as HIPAA, HITECH, and PCI. With our easily customizable drag-and-drop interface, healthcare customers have a jump-start in configuring controls to meet compliance mandates.
Saviynt & Identity Governance and Administration (IGA)
Outsourcing may cut costs and maximize efficiency in a healthcare organization, but it requires diligence to ensure risk and compliance are properly managed, monitored, and continuously maintained. Healthcare Identity Cloud delivers a game-changing, one-stop solution for all contextual identity risk information. Saviynt’s cloud-native Identity Governance and Administration (IGA) platform protects your most sensitive information and increases organizational efficiency and agility by ensuring that the right people have the right access to the right resources for only the right amount of time.
Saviynt simplifies IGA by increasing organizational agility through automation and intuitive workflows. We do this by offering an identity and access governance platform that unifies identity governance capabilities into a single cloud-based solution. The solution provides visibility, IT efficiencies, and improved internal controls, reducing the risk of compromised credentials and audit failures.
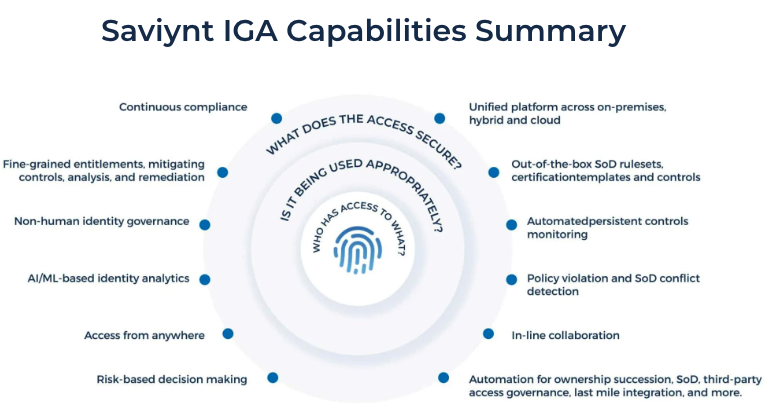
Powered by a comprehensive identity warehouse and user experience to drive frictionless access, Saviynt Identity Governance and Administration (IGA) enables Zero Trust in your hybrid and multi-cloud environment by providing the following features:
- Industry-leading cloud architecture
- Governance for all human and machine identities – including third parties
- Modern web interface, mobile app, browser plug-in, and ServiceNow app
- Rapid application & identity onboarding with pre-built templates and discovery of unmanaged assets & applications
- AI & ML-powered identity analytics identify risk and duplicate identities, and close access gaps
- Actionable insights for identity management, compliance, and security via the Control Center
How does Saviynt’s IGA solution affect your bottom line? Forrester’s Total Economic Impact™ (TEI) study examines the return on investment (ROI) organizations realize with the Saviynt Enterprise Identity Cloud. In this commissioned study, Forrester estimates that implementing Saviynt can save your organization $34.4M and achieve a 240% ROI over three years.
Resources


