What is Zero Standing Privilege (ZSP)?
TABLE OF CONTENTS
- What is Zero Standing Privilege (ZSP)?
- What is standing privilege?
- Zero Standing Privilege (ZSP) vs Least Privilege
- Why Zero Standing Privilege (ZSP) Matters
- Saviynt & Zero Standing Privilege (ZSP)
- Additional Resources
What is Zero Standing Privilege?
Zero standing privilege (ZSP) is a target state of limiting access as much as possible to critical information systems by applying Zero Trust principles to problems in privileged access management. Created by the analyst firm Gartner, ZSP represents the shift from traditional privilege management where account access was “always on,” to granting access to privileged resources for a limited time only, based on need. The traditional “always-on” model presents a security risk and makes your systems prone to attack. In the ZSP model, each access request is decided according to predetermined policies or criteria based on behavioral analytics.
Zero standing privilege is enabled by the Just-in-Time (JIT) access model, where users are granted elevated permission to complete a specific task on a specific resource and only for the length of time needed. Instead of administrators having persistent access to every system, JIT access provides the right access to the right resource for the right length of time.
Zero Trust access management removes implicit trust and instead, continuously re-evaluates risk and trust levels of every digital interaction. It is based on the principle of “never trust, always verify” and provides the “least access” required to relevant data, applications, and assets as they are needed to complete a job. It enables organizations to secure identity as the new perimeter and prepares them to defend modern infrastructures against today’s threats.
What is Standing Privilege?
Standing privilege refers to administrative accounts that are enabled indefinitely and are always on. They give users access to critical systems without authorization. Access is often broad-based, with users gaining additional privileges over time—whether the individual needs them or not. Also known as privilege sprawl, standing access can pose a security risk if malicious actors gain access to user credentials. In the age of the cloud, standing privilege is no longer viable. The cost and complexity of managing and protecting standing privilege credentials in today’s cloud environments are simply untenable. ZSP reduces the risk surface by making privilege credentials available on a temporary basis.
Zero Standing Privilege (ZSP) vs Least Privilege
Least privilege says that users should only have access to the required resources needed to complete a job (rather than being granted access to the entire network or large portions of it). Least privilege minimizes risk because it limits the damage done if the user becomes compromised or malicious.
Implementing least privilege is challenging when users are dynamic, moving from one role to another, from one team to another, over time. They need resources for one job that they no longer need in the next. This is where time-limited access comes in. If privileged access is automatically eliminated after a period of time, permissions won’t linger off the radar, and access management becomes less cumbersome.
Least privilege is the standard, and Zero Trust is the ideal. Zero standing privilege, which targets a state of no privilege existing, is a means by which organizations can achieve it. To move to a Zero Trust model, privileged accounts must be eliminated. Even for admins—admin credentials can be hacked and the damage can be substantial. Every access request must be evaluated to ensure it’s appropriate for the user’s current roles and responsibilities. And it should be time-limited to prevent unnecessary permissions. Zero standing privilege is a practical way to give users access to the exact resources they need, just for the specific period of time required.
Why Zero Standing Privilege (ZSP) Matters
Providing time-limited access to resources allows permissions to automatically revert to a secure state after the task at hand is completed. This has several primary benefits:
- Administrators no longer need to remember to lock down once the privileged work is done, reducing insider threats.
- If credentials are compromised by an outside attack, the scope of the damage is limited.
- Compliance requirements are met automatically by tracking when access is granted and revoked.
Securing your user access with standing privilege worked well when everyone was using on-prem servers and VPNs. But now that networks are in the cloud, standing privilege creates undue risk. Employees with privileged access can become insubordinate or fooled by phishing attacks. Hackers can steal credentials more easily with advanced technology and evolving methods. The problem isn’t a small one—74% of today’s data breaches involve compromised privileged access credentials.
A Zero Trust approach solves this issue by eliminating standing privilege. No one has automatic trust. Every user (human and non-human) must request privileged access each time they want into a system, database, or application. And access is only granted on a time-limited basis. As a result, Zero Trust significantly reduces the damage that access violations can cause.
Saviynt & Zero Standing Privilege (ZSP)
Saviynt’s Identity Cloud platform helps ease the move to the Zero Trust Model by drawing the perimeter at the identity layer. Identity-centered solutions provide a foundation for Zero Trust. Zero standing privilege, in-depth visibility, automation, and centralized, continuous monitoring are crucial pieces of Zero Trust.
Saviynt Privileged Access Management (PAM) specifically manages JIT access and enforces least privilege, moving you towards the ideal of Zero standing privilege.
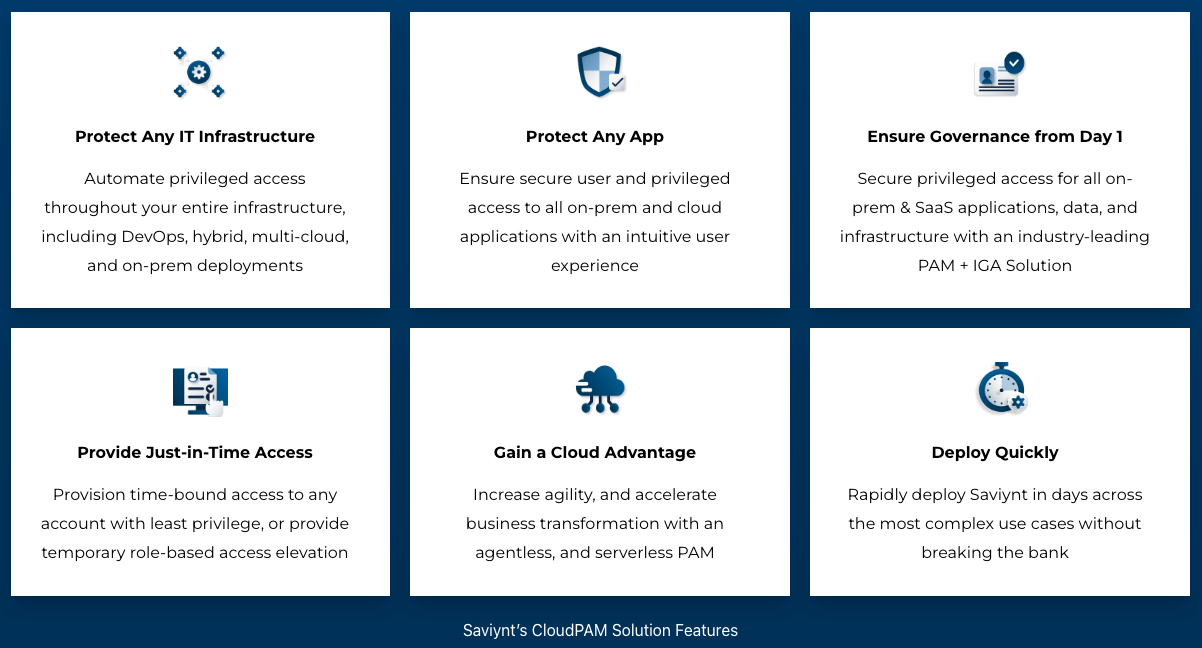
Here are some other features related to ZSP you can leverage with Saviynt:
- Explore an intelligent identity perimeter
- Achieve ZSP with just-in-time role elevation and time-bound access
- Simplify and streamline dynamic access management with “right-sized” access
- Gain complete control and visibility through continuous risk assessment
- Prevent data breaches and insider threats with real-time insights
- Support multi-cloud and hybrid infrastructure
Additional Resources
Resources


