
Related Post

Report
2024 Identity and Security Trends

Report
Saviynt a Gartner Peer® Insights Customers Choice for IGA

Solution Guide
IGA Buyer's Guide
-1.png)
Solution Guide
PAM Buyers Guide

Whitepaper
Use our partner finder to discover your perfect business match.
Tune in for expert-led live demos on how Saviynt’s identity security solutions transform your digital security with actionable insights and best practices.

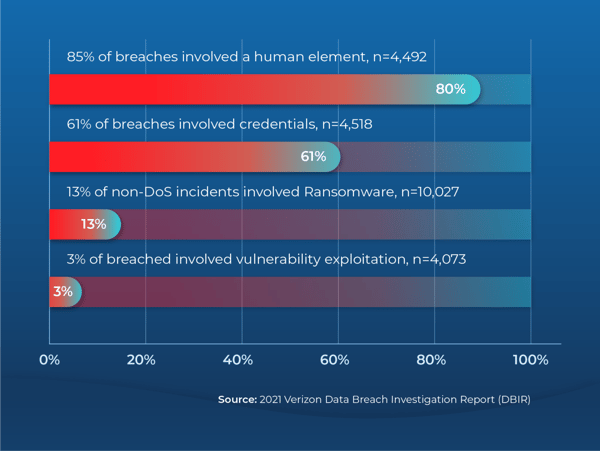
Privilege escalation attacks occur when bad actors exploit misconfigurations, bugs, or weak passwords to gain access to sensitive information or system controls. As organizations accelerate cloud adoption, the threat landscape has widened, and such attacks are becoming more frequent. According to the Verizon 2021 Data Breach Investigations Report, 80% of breaches involve compromised credentials. This makes them one of the most commonly used components in an attack.
Yet IT complexity, lack of visibility into risks, and privileged access sprawl make it difficult for security teams to get their arms around privileged access management (PAM), much to the delight of cyber attackers. Attackers love complexity in particular. In fact, they thrive on it. By taking over a low-level user account, a malicious attacker gains access to a system. From there, they can continue to take control of additional systems horizontally or escalate privileges vertically, gaining admin and root control systematically until they have access to the full environment. And the results can be devastating: privilege escalation can allow a simple malware infection to balloon into a catastrophic data breach.
What can you do to protect your organization? Let’s take a closer look at the 3 “Ms,” of common privilege escalation attacks: Mistakes, Misuse, and Malice — and what you can do to minimize these risks.
The number and variety of attack surfaces are increasing and changing as attackers continue to probe for weaknesses. Yet, CIOs must balance the need for security against providing users with access to the applications, systems, and services they need to do their jobs as quickly as possible.
According to a recent report from Stanford University, approximately 88% of data breaches are caused by human errors. Human errors usually occur when busy admins handle too many manual tasks under tight deadlines.
Given this scenario, mistakes are inevitable. They take the form of:
One way to limit the scope of an attack is to employ the principle of “least privilege” controls. As the name implies, such controls ensure that users only have access to the specific tools they need to complete a task to limit the blast radius of an attack by stopping lateral movement.
An identity-driven PAM solution can help organizations pinpoint these errors so that mitigating actions can be taken in a timely manner. Legacy infrastructure PAM tools were not designed to provide this functionality, which is why innovative, cloud-based PAM offerings are garnering lots of interest.
Misuse occurs when internal admins knowingly compromise a system for expediency or their own personal gain.
An estimated 74% of data breaches involve privilege access misuse or compromise. Misuse can be passive, taking the form of using default passwords for admin or root accounts, using undocumented backdoors into environments or shadow IT, not changing defaults in a new system, using weak passwords such as 123456, or simply not having an adequate privileged access management process in place. Or it can be active, as when a disgruntled employee who still has access deliberately steals data in an effort to harm the company on the way out.
But most often, misuse happens without malicious intent. For example, say someone is trying to share a large email attachment which is often blocked by most companies’ email systems. Rather than trying to securely share the file by working with the IT and security teams, users will often upload files to their personal Dropbox or OneDrive accounts. While they have no intention of doing something bad, all of a sudden, there’s corporate data in an unknown location. And that data is outside of IT purview, not controlled by security policy, with no governance, and potentially open to others.
One way to address misuse is to go beyond password vaulting and remove standing privilege. Centralizing privileged accounts in a vault – the foundation of traditional PAM solutions — won’t reduce the number of privileged accounts or reduce the risk of these privileges.
Our third “M,” Malice, is often the end result of our previous two “Ms.” Malice occurs when bad actors exploit vulnerabilities to get access to protected assets or disrupt operations, which they often do by using stolen credentials. It’s an understatement to say that tens of thousands of cloud credentials are for sale on the Dark Web at any given moment.
Malicious attacks are always in the news. These types of attacks take the form of spyware, malware, trojans, worms, and ransomware. When user credentials get into the wrong hands, attackers can wreak havoc. For example, in February of this year, a ransomware attack caused Nvidia, the largest microchip maker in the US, to shut down parts of its business for two days. The hacking group, known as Lapsus$, threatened to release 1TB worth of data — including employee credentials and proprietary company data, such as source codes — unless a ransom was paid. “
Traditional PAM solutions scan environments at fixed intervals, but cloud resources are constantly scaling up and down. This could result in cloud assets being unmonitored for a significant time period. Meanwhile, privileged credentials sit around, vulnerable to attack.
In addition, traditional approaches for securing privileged accounts don’t effectively address privilege sprawl or persistent privilege, nor do they provide timely visibility across hybrid environments and applications.
Enterprises must assess real-time activity among elastic workloads, accounts, and access. For example, remote workers routinely use multiple devices to connect to various data and systems. To reduce access misuse, these devices, accounts, and sessions should be in the real-time purview of security leaders.
Further, they must identify risky or misconfigured objects and automatically trigger remediation steps, including reversal, exception approval, or quarantine. This is akin to ‘closing the door’ on excessive permissioning — a remedy to the practice of giving privileged accounts excessive access in the name of expediency. Similarly, it addresses the orphaned account issue, those forgotten accounts that sit on the network, primed for misuse.
When we designed our Privileged Access Management solution, we recognized the need to remove all standing privileges. The vaulting of all discoverable, privileged credentials never reduced the number of privileged accounts anyway, nor did it limit the risk of standing privilege.
With PAM, Saviynt allows organizations to remove these accounts and incorporate least-privilege principles. Using a just-in-time approach to privileged access, end users receive the right level of privilege for their immediate task — across all assets, applications, and platforms. This is why we designed our PAM platform with Zero Trust, zero-standing privilege, and JIT access at the center. Without an on-prem footprint, the platform adds versatility, allowing you to secure privileged access and protect critical assets across your entire infrastructure.

Report

Report

Solution Guide
-1.png)
Solution Guide

Whitepaper