Identity Threat Detection and Response locks down threats with impeccable accuracy—and makes the “protect only” mindset a thing of the past.
There was a time when building a wall around an organization’s infrastructure was sufficient for cybersecurity. Now, we’ve entered the wild west of identities, accounts, entitlements, and data spread across cloud platforms, applications, and devices. Attack surfaces are everywhere, and each unique identity must be authenticated, authorized, and monitored.
The problem is, most identity security practices are primarily preventative, either with PAM solutions or authentication processes such as SSO and MFA. While an ounce of prevention is important, it can’t cure an identity-based breach. Without timely reactive response capabilities, attackers can destructively span applications, endpoints, and networks.
That’s where Identity Threat Detection and Response (ITDR) comes in. This emerging cybersecurity discipline fills security gaps by providing the missing context, access patterns, behavior analysis, and risk signals. Let’s look at how ITDR can boost discovery, confront these vulnerabilities in real-time, and stop an attack dead in its tracks.
Evolution of Detection and Response
A decade ago, standard “level one” technologies like SIEM or firewalls helped companies triage the influx of data. Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR) introduced more insights, response, and threat hunting into the environment. More recently, Extended Detection and Response (XDR) further improved threat intelligence and insights into vulnerability management.
But the demands of a post-COVID world require automation and identity telemetry. This is especially true for companies that had to make the leap to cloud without a comprehensive plan. Legacy solutions simply aren’t equipped to handle the scale and complexity of today’s use cases.
Too often, identity centricity has been focused on supplying identity context for individual incidents. The ability to understand advanced identity threat detection use cases such as privilege escalation is limited, particularly with popular point solutions.

At the end of the day, if you’re detecting anomalies, you need visibility into the how, the why, and the who. Has a user usurped privileged access? Is it isolated to a specific set of servers? Could it cut across the firewall? With ITDR’s identity context and correlation, you can detect potentially malicious behavior and restrict or terminate the identities with complete precision.
The Key Components of ITDR
If an identity seems to be compromised or is showing anomalous behavior, ITDR uses behavioral analytics to provide event context as well as a line of sight into different types of platforms, cloud environments, email environments, etc. This is particularly critical with the rise of insider threats that aren’t necessarily human—from CI/CD tools to Kubernetes, everything and anything that’s generating an identity has the potential to begin behaving strangely.
Let’s look closer at how ITDR recommends the action to be taken, traces the attack path, and discovers how the access got started.
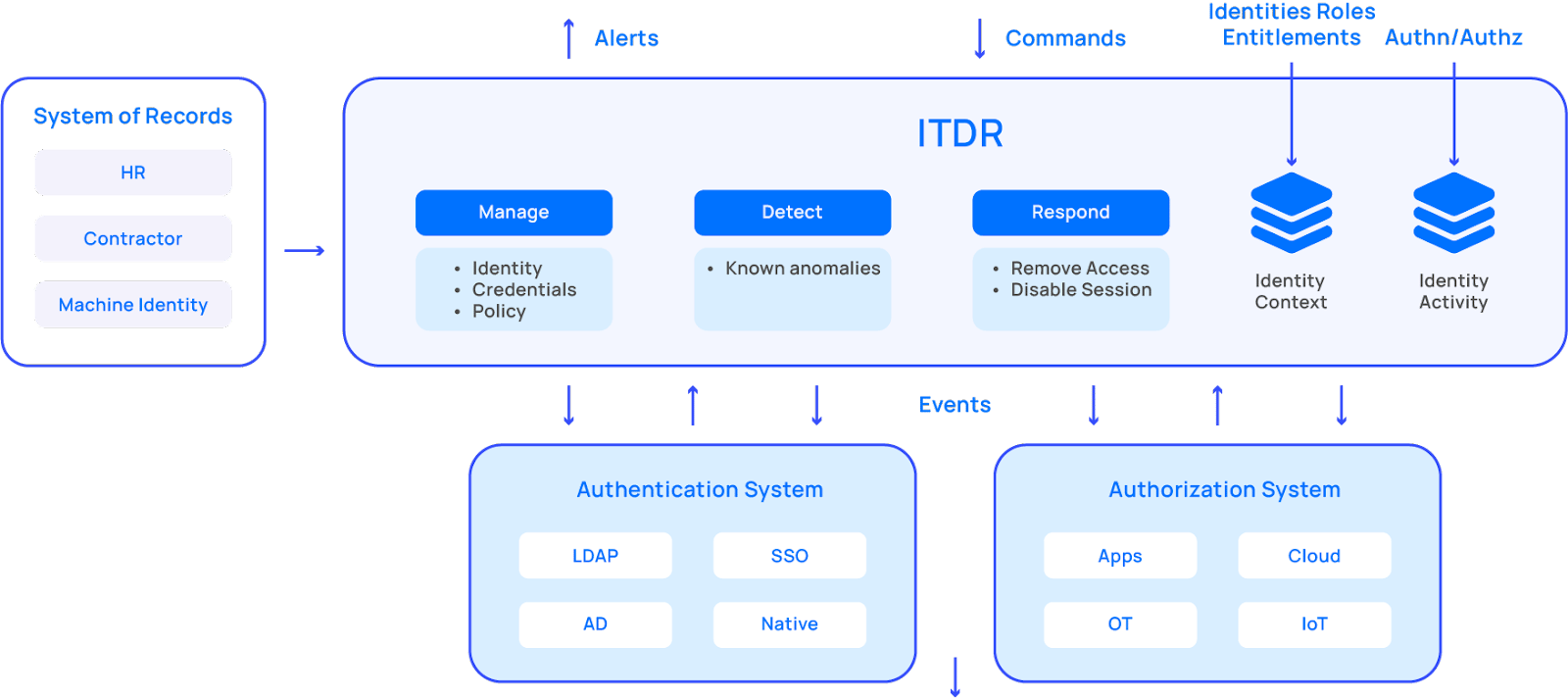
Beyond just prevention: ITDR can manage, detect, and respond.
Manage: an identity system is only as accurate as its data. ITDR delivers an authoritative source of truth and entitlement inventory for employees, contractors, and machine identities—whether they’re in the cloud or logging into a legacy app. No more checking logs, and no more siloed information. ITDR identifies who has access, what kind of access—and what they’re doing with that access.
Detect: ITDR automatically surfaces hidden risks that might otherwise slip through the cracks, such as unmanaged identities, misconfigured settings, and even credential misuse.
Respond: Once ITDR spots potentially malicious behavior on your corporate network, you can take immediate action. Restrict or terminate those identities causing trouble, and shut down threats before they have a chance to wreak havoc.
The Future of ITDR
There are two key takeaways here: breaches are inevitable, and preventative security measures are not enough. To maximize the data and intelligence that ITDR brings—particularly within broader XDR functions—practitioners need reskilling.
“There’s not enough triage analysts on the planet right now who understand identity security,” says Charlie Jacco, Principal, KPMG LLP. “The fear is that ITDR becomes another ingredient in a muddled ‘DR-soup. The silver bullet will be deep connections between identities and network information leading to an orchestrated, automated, identity-related security response.”
Forward-thinking enterprises will invest in data science capabilities to effectively extract knowledge and offer predictive insights. This may require retraining or reassessing hiring profiles, especially as threat sophistication grows. But this not only gives you more threat detection and response capabilities, it gets the most our of your internal cybersecurity talent.

While even early ITDR applications add usefulness, tools must do more than just simplify analysts’ workflows. During deployment, make the most of ITDR’s potential by integrating it with authorization systems native to your applications, cloud resources, infrastructure, and even your OT environment. It’s like giving ITDR a VIP pass to all the important areas of your enterprise, ensuring no stone is left unturned.
Up to now, the identity space has lacked a converged and fully integrated solution that contains privileged access (PAM), identity governance (IGA), granular application access (AAG), and Third-Party Governance (TPAG). Saviyint Enterprise Identity Cloud (EIC) is the industry’s only enterprise-grade SaaS solution that can deliver complete visibility in a single pane of glass.