NIST 800-53 Identity and Access Management (IAM) Compliance via Saviynt’s FedRAMP ATO

Identity and Access Management NIST
Digitalization requires agencies to start with people- whether employees or constituents. As federal agencies strive for modernization, they find themselves struggling to align with the strict identity and access requirements contained in the National Institute of Standards and Technology (NIST) 800 series to comply with FISMA. Legacy identity and access management systems fail to meet these NIST compliance requirements, leaving agencies unable to meet stringent NIST identity and access management requirements. Thus, federal agencies need to find a cloud-first FedRAMP authorized vendor, like Saviynt, to ease NIST identity and access management compliance.
What is NIST 800-53 Series?
NIST 800-53 focuses on creating a comprehensive set of cybersecurity and privacy safeguards across all computing platforms. Although currently still in Revision 4, summer of 2019 will bring the newest NIST 800-53, Revision 5. This revision of the NIST framework responds to the way that federal employees and agency constituents increasing access services from a wide range of systems, networks, software, and devices. In addition to federal government agencies and contractors adhering to the NIST framework, state and local governments and private organizations use the NIST framework for risk management.
What Are the NIST Identity and Access Management (IAM) Requirements?
NIST 800-53 sets out 25 access control requirements, complete with additional guidance, over the span of 21 pages. Of those, the ones below focus the most on identity management and governance:
- Access Control Policy:
- Address the purpose, scope, roles, responsibilities, commitment, internal commitment, and compliance objectives
- Designate an official to manage policy and procedures
- Determine review and update to policy and procedures
- Ensure implementation aligns with policy and controls
- Establish remediation procedures for violations
- Account Management Controls:
- Define and document system account types
- Assign account managers
- Establish group and role membership conditions
- Specify authorized users using group, role, privileges, and other attributes
- Provisioning
- Deprovisioning or changes
- Monitor use
- Notify account managers of changes
- Authorize access based on validity, intended user, and other attributes
- Review compliance with internal controls
- Establish deprovisioning processes for shared/group accounts
- Incorporate mover/leaver processes
- Establish time bound emergency access processes
- Separation of Duties: document and define access authorizations to ensure separation of duties (SOD).
- Least Privilege: ensure that user access is limited to what is necessary to do their jobs.
- Security and Privacy Attributes: define, establish, and determine the interconnected identity attributes attached to privacy and security of stored, processed, and transmitted data.
- External Systems:
- Establish terms and conditions governing relationships for other organizations owning, operating, and/or maintaining external systems
- Establish access and authorization rules linked to external systems
- Establish access and authorization rules for processing, storing, or transmitting data using external systems
- Information Sharing: Delegate sharing permissions based on matching partner access and employ mechanisms for collaboration
- Data Mining Protection: Establish processes and monitor to detect and protect against unauthorized data mining
- Access Control Decisions: Establish procedures to ensure policies are consistent for access requests before enforcing access
What are the NIST 800-53 Identity and Access Struggles in the Cloud?
Attempting to ease internal workloads and enable constituents, agencies increasing adopt:
- Infrastructure-as-a-Service (IaaS),
- Platform-as-a-Service (PaaS), and
- Software-as-a-Service (SaaS).
Legacy identity and access management infrastructures remain fragmented and disconnected. Legacy IAM is unequipped to manage NIST control requirements to sensitive information and applications. They cannot manage the different connected cloud entry points and cannot manage potential Segregation of Duties gaps as users move between and within agencies.
Legacy IAM systems focus primarily on “who and what”:
- Create ID
- Look up user access permissions
- Review the access control rule for role
- Compare individual’s access permissions to resource’s access control rules
These systems cannot manage the dynamic nature of both cloud migration and modern employee needs. Using and intended for outdated IT infrastructures, federal agencies seeking to modernize their IT environments find themselves unable to implement them in a timely manner.
Why Is Maintaining Compliance with Identity and Access Management NIST Requirements Difficult?
The new NIST 800-53 incorporates requirements that allow federal agencies to modernize their infrastructures. However, several challenges to maintaining an IAM program still plague them.
Managing Internal Movers/Joiners/Leavers
Agencies are similar to large enterprises. According to the Bureau of Labor Statistics, federal employee numbers ranged from 2.198 million in January 2017 to 2.183 million in January 2018 and back up to 2.195 million by February 2019. In short, people join, leave, and move throughout federal agencies.
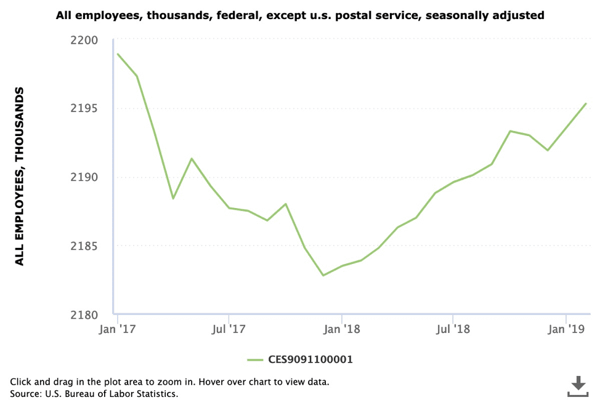
Managing the provisioning/deprovisioning of this many employees is difficult. Moreover, for employees moving between agencies, maintaining appropriate access can be difficult, especially when agencies share databases or other technology resources.
Moving to IaaS/PaaS/SaaS Models
Federal agencies are not just adding users, but they’re increasingly adding new applications. Each application creates a new access point for the internal, or external, users.
Securing the identities across this ecosystem, in conjunction with employee joiner/mover/leaver issues creates a web of identity and access management issues. An employee at the Department of Energy needs different database access than an employee at the Environmental Protection Agency. However, both employees may need access to environmental contamination reports for critical infrastructure.
Agencies may implement an IaaS environment differently, but they may also be incorporating the same SaaS applications, such as Office 365, for information sharing. The intricate web of connected applications requires a complex access model that can also continuously monitor user access.
Preventing SOD Violations
With the interconnection of individuals and digital services, SOD violations can occur if the agency lacks visibility over its users and ecosystem. Overburdened administrators need easy insight into whether requested access will lead to a violation. Meanwhile, IT cybersecurity depends on managing user and data access rights to ensure that employees do not accidentally or maliciously compromise sensitive data.
However, complex security and access models across various cloud computing layers makes this difficult and often acts as a barrier to cloud migration. For example, IaaS environment access visibility remains embedded within a multitude of policies and directories which makes determining SOD violations difficult.
Continuously Monitoring Across the Ecosystem
The cloud’s ephemeral nature inherently makes monitoring difficult. The overwhelming volume and velocity with which changes occur in the cloud require a solution that ensures continuous monitoring and enforcement of baseline security policies.
Further, remote employees and cloud access via mobile devices also create barriers to agency cloud migration strategies. NIST 800-53 sets forth specific access and location requirements for these devices and connections. With federal employees increasingly seeking access to information as they travel or throughout the day, agencies need insight into not only who access information, such as email servers, but also where they are located and how they are accessing the information.
Constituent Access to Information
Cloud first mandates intend to ease constituent access to needed information. Whether accessing social security benefits or filing taxes, constituents access sensitive data similarly to employees. However, agencies lack control over external users. They cannot provide secure devices or control the location from which the user accesses the information.
Thus, they need to manage these identities and prove governance over their controls.
Saviynt Eases Federal Agency NIST Identity and Access Management Compliance Burdens
Saviynt is the first and only Identity and Access Management platform to achieve FedRAMP Moderate ATO status and is listed on the FedRAMP marketplace. This status provides federal agencies the needed assurance over our SaaS platform, allowing them to accelerate their cloud migration strategies.
Once agencies define digital identities, our intelligent analytics compare users to their peers so to ensure appropriate access to applications and provides suggestions to ensure that the agency maintains its SOD policy.
Saviynt’s core capabilities ease NIST 800-53 compliance enabling full identity life-cycle management covering all issues associated with the dynamic nature of federal employee access.
Saviynt also offers IaaS security and governance capabilities to accelerate cloud migration by providing visibility into risks, enabling management of entity and identity lifecycles across mission-critical cloud platforms as well as managing privileged access management to cloud workloads and objects. Additionally, our Controls Exchange provides out-of-box controls easing compliance burdens.
Extending the SSM core capabilities, the Data Access Governance module integrates with common SaaS and cloud-based solutions while also offering near real-time data protection that begins content classification and ends with access analytics.
Built to support multi-million identity user populations, External Access Governance module supports customer-facing offerings that ease constituent access burdens while also enabling federal agencies to streamline their internal governance processes.
Committed to federal agency data security, we secured our platform and obtained our FedRAMP Moderate ATO to provide assurance for our customers. We then extend our commitment by providing the next generation of IGA solutions so that federal and non-federal customers can more easily secure their own information and infrastructures.
Related Post

12 / 19 / 2025
Saviynt Recognized as a Leader in Frost Radar™: Non-Human Identity Solutions, 2025
READ BLOG

Report
Saviynt Named Gartner Voice of the Customer for IGA

EBook
Welcoming the Age of Intelligent Identity Security

Press Release
AWS Signs Strategic Collaboration Agreement With Saviynt to Advance AI-Driven Identity Security

Solution Guide