Ways to Leverage Machine Learning in Identity Security
ML delivers data-driven predictions and suggestions to help streamline workflows and minimize administrator frustration. There are several areas where ML can be successfully leveraged for identity security. By doing so, identity security programs can empower workforces, reduce management complexity, save costs, and more. With its contextual understanding, a system can automatically suggest the next step or revise a workflow. It helps improve and streamline processes, reduce human related errors, and strengthen overall security.
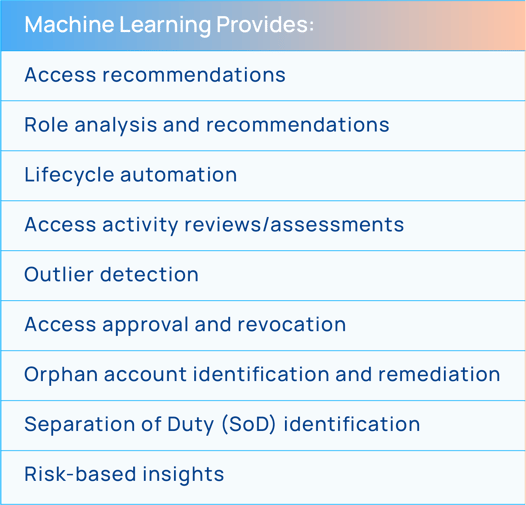
For example, by assessing and reviewing who has access to what and how that access is or isn’t being used, a system can provide access recommendations throughout an identity’s lifecycle, from the initial request through ongoing micro-certification campaigns. Additionally, many of the more mundane activities related to identity security can be automated, speeding up employee onboarding. Additional insights can be provided to entitlement owners as to how someone’s access stacks up against their peers and other roles to help accelerate approvals and reduce digital fatigue for both administrators and end users.
Machine learning can also identify anomalous activity and identity outliers that increase enterprise risk. Analyzing this data allows for the automation of access revocations or for providing a trigger for further reviews. When working with role development and maintenance, ML can analyze existing roles, see if there are similar roles that could be merged, and provide recommendations on new roles that may be beneficial.