One Converged Platform. Complete Identity Control.
Turn on incredible business value
from day one
Simple to use.
Fast to deploy.
Onboard applications once, easily create reports, manage access policies and configure workflows through a single, simplified experience.
Detect earlier.
Respond smarter.
Identify compromised identities and abnormal access patterns with intelligence that transforms your security speed and effectiveness.
Lower cost.
Transform ROI.
Eliminate the cost of legacy and point solutions, manual provisioning and access certification with intelligent automation that delivers value from day one.
See Everything.
Control Everything.
Govern and secure workforce, external, and machine identities across your ecosystem through a single pane of glass that puts you in complete control of risk.
Redefine What’s Possible With a
Converged Identity Platform
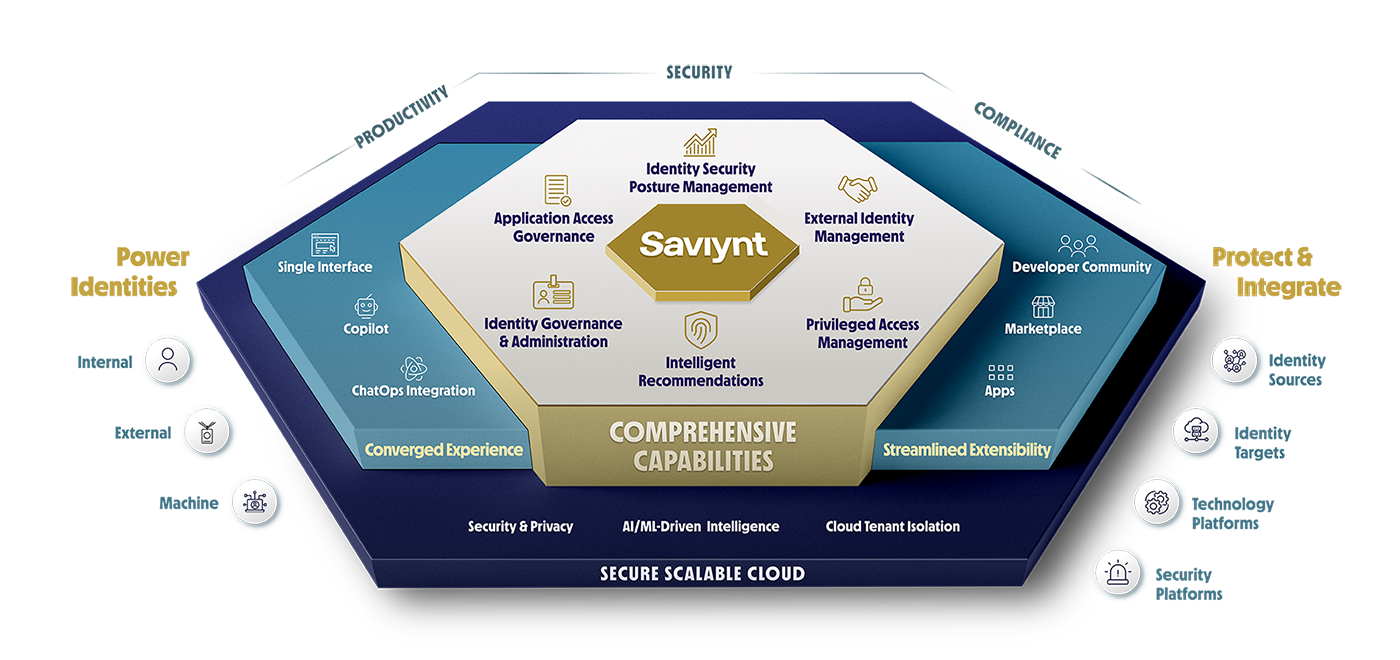
Onboard Once and Enable Anytime
Reduce Onboarding Time by up to 90%
- Centralized application management improves your security posture and shrinks the attack surface with cross-application governance
- Turn on additional capabilities including IGA, GRC, PAM, and Service Account Management at any time - no additional onboarding required
- Discover applications in your ecosystem with ITSM, CASB, and other integrations
- Accelerate implementation by up to 70% with hundreds of pre-built integrations
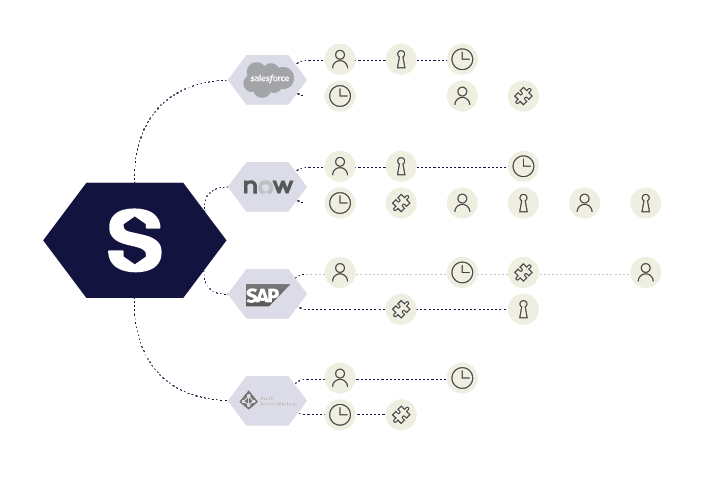
Leverage Rich Data for Actionable Insights
With the Industry’s Only Intelligent – and Most Versatile – Identity Warehouse
- House every identity, human or machine, and understand complex relationships in a single repository
- Gain unmatched, fine-grained visibility of all identities, access, and usage
- Drive automation with intelligent recommendations that lower costs and fast track decisions
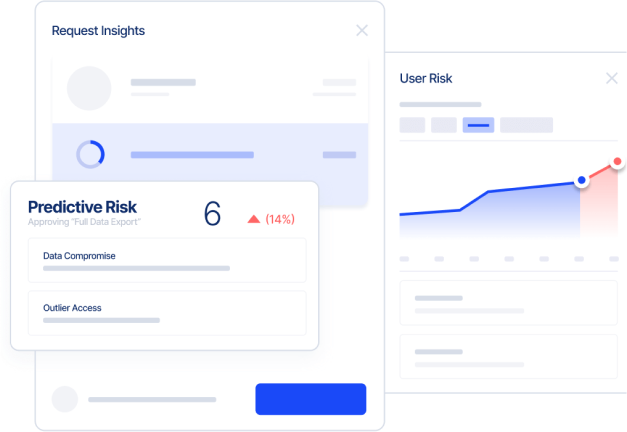
Reduce Risk With Better Insights
Advanced Analytics Deliver Cross-Platform Identity Intelligence
- Gain real-time identity risk profiles with additional data from other security platforms
- Enable cross-mapping between regulatory initiatives, control frameworks, and control types
- Automate alerts and get remediation suggestions
- Leverage advanced AI/ML capabilities that further enhance your identity program via Saviynt Intelligence
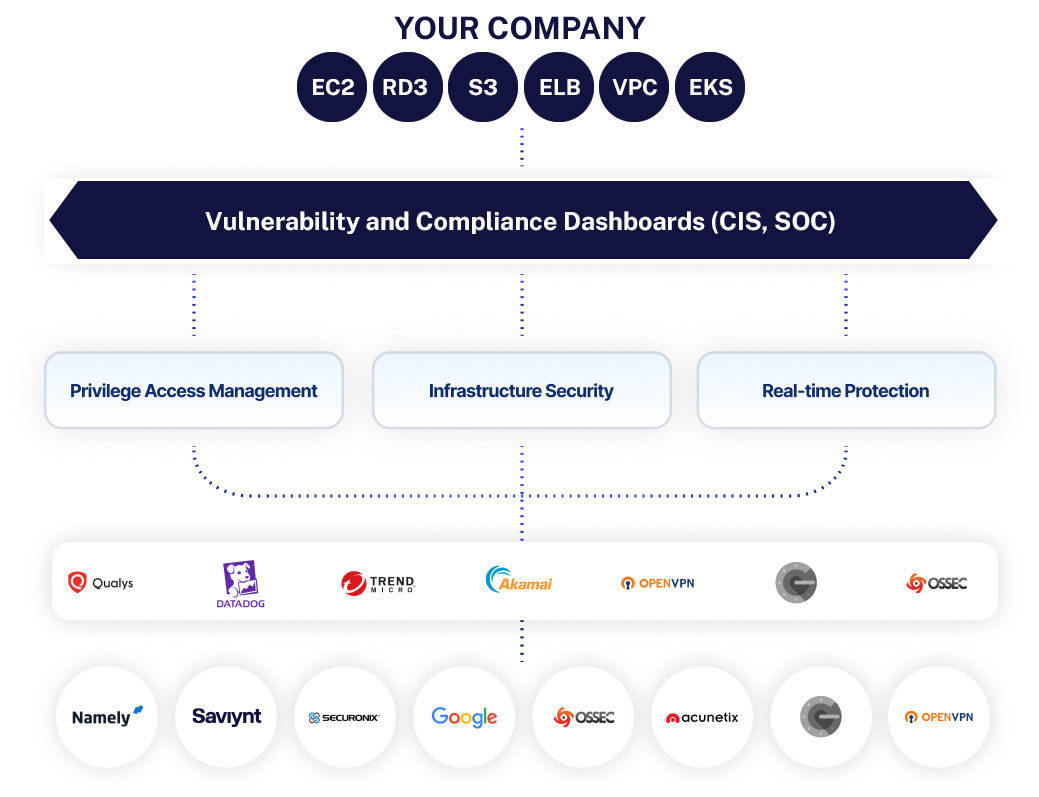
Adopt a Modern Enterprise Architecture
A Flexible Enterprise IAM Cloud Platform Built for Security and Scale
- Balance security and availability goals with a right tenancy, containerization, and auto scaling architecture
- Data residency support across 25+ regions globally
- Continuous, seamless capability updates without regression worries or additional upgrade costs
- Enhanced data security and control with Bring Your Own Key (BYOK) and Bring Your Own Vault (BYOV)
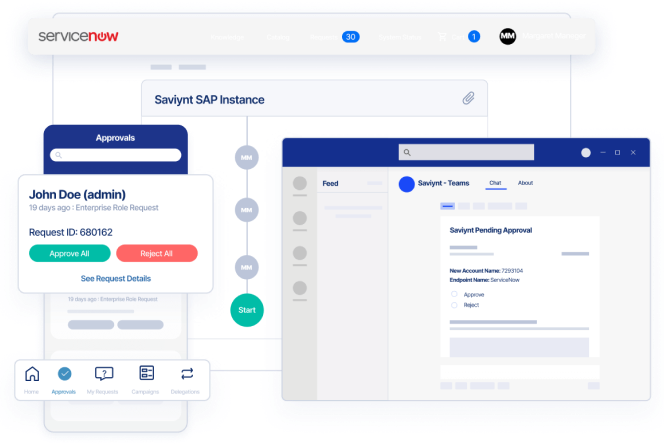
Deliver an Omni-Channel Experience
Frictionless Experiences, Anytime and Anywhere
- Improve self-service capabilities by leveraging your existing collaboration platforms, ITSM tools, and mobile devices to streamline identity workflows
- Manage all workflows and application access through ServiceNow
- Submit and approve access in real time via collaboration tools such as Microsoft Teams and Slack
- API-first approach enables headless experience for identity services

Saviynt Named a Gartner® Customers' Choice 4 Years in a Row!
Read the Gartner Peer Insights 2024 "Voice of the Customer" Report for IGA
A Converged Identity Platform You Can Trust

SOC 1 Type II Audit Report

ISO 27001:2013

SOC 2 Type II Audit Report

ISO 27017:2015

FedRAMP Moderate

PCI DSS Certified
Resources for your identity journey
Analyst Report
Saviynt Named a Customers’ Choice in the Gartner® Peer Insights™ Voice of the Customer for IGA Report

EBook
Making the Move to Modern IGA

Solution Guide
Saviynt Intelligence
Solution Guide
Saviynt Identity Cloud for Manufacturing

On-Demand Webinars
Al and ML - Transforming the Future of Identity Security?
Solution Guide
Unify IGA and PAM with Saviynt Identity Cloud

Video
Saviynt The Identity Cloud
Explore the Saviynt Identity Cloud
Identity Governance & Access Management
Secure your extended enterprise without slowing business down
Privileged Access Management
Create right-time, right-level privileged access for users, machines and applications
Saviynt Exchange
Take your business further with the power of Saviynt’s connected community






