
Ensure complete identity security for all humans and non-humans — AI agents, machines and more — and everything in between that interacts with your organization.
Scale without limits and govern your entire enterprise with an easy-to-use experience that extends into and integrates with every part of your tech stack.
Achieve comprehensive visibility, reduce complexity and lower risk, while optimizing costs and boosting productivity.
Help your entire organization to be more secure with an intelligent, AI-powered platform that enables smarter, easier, and faster identity security.
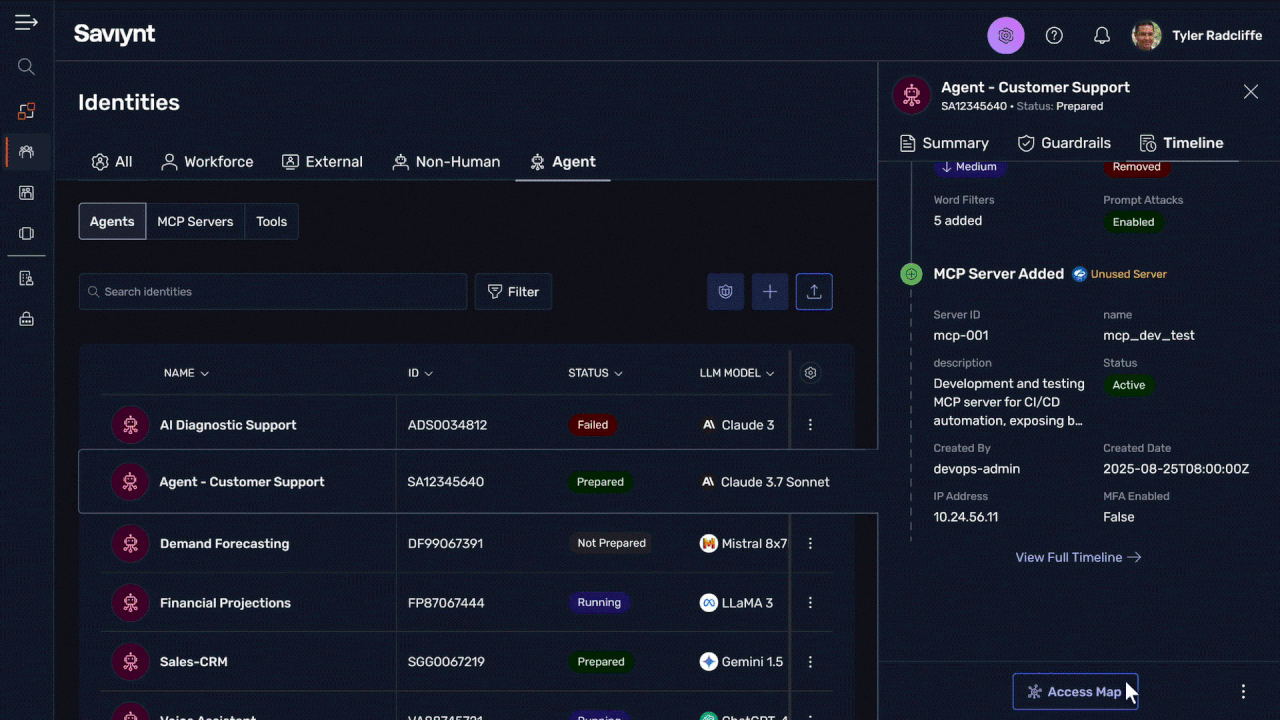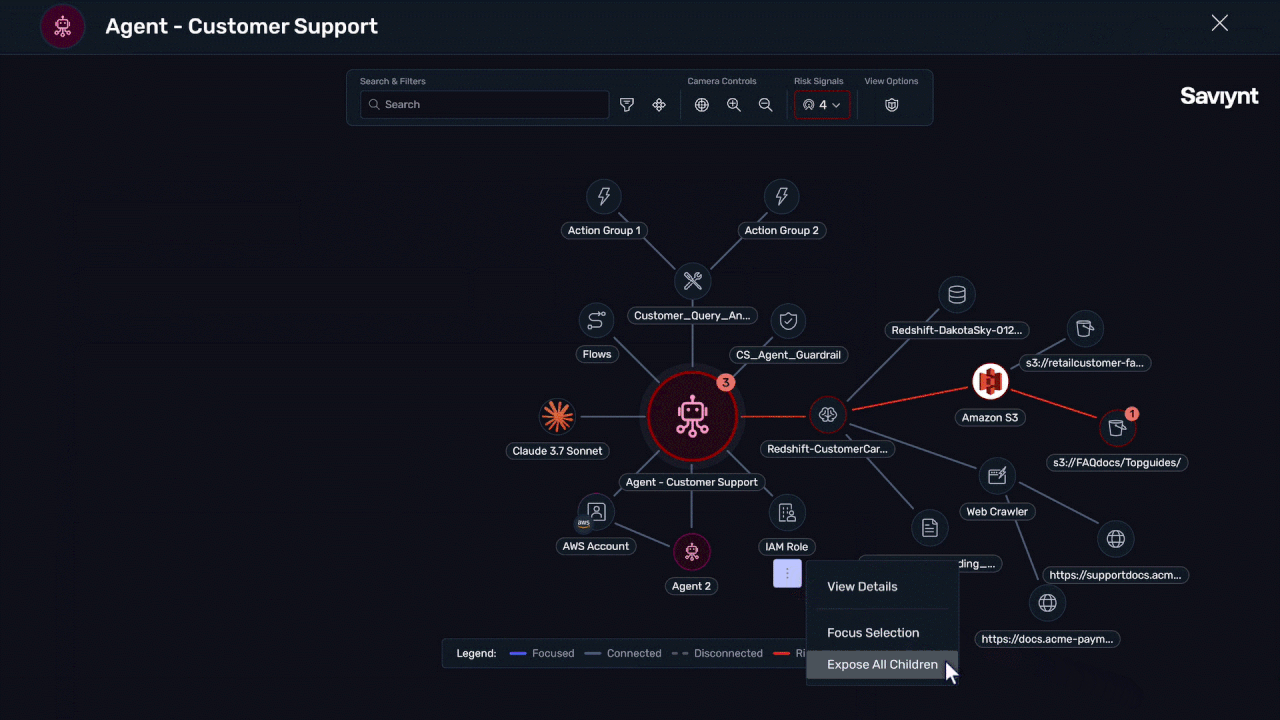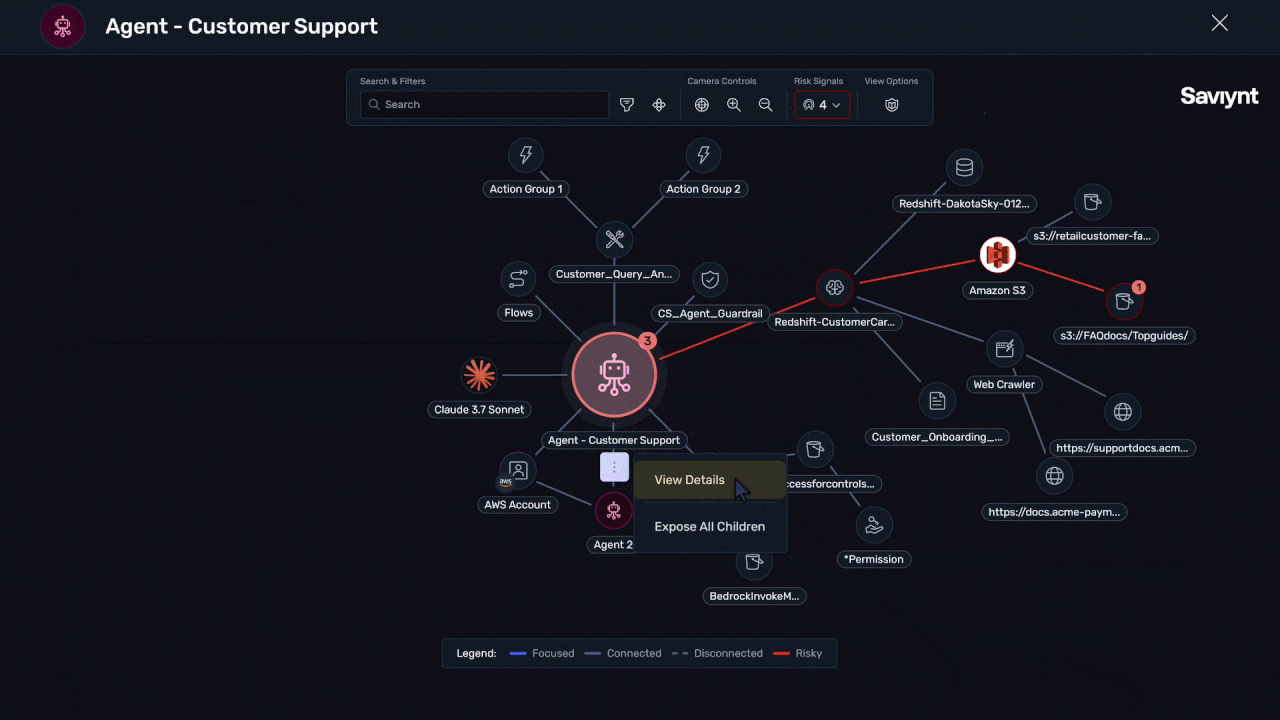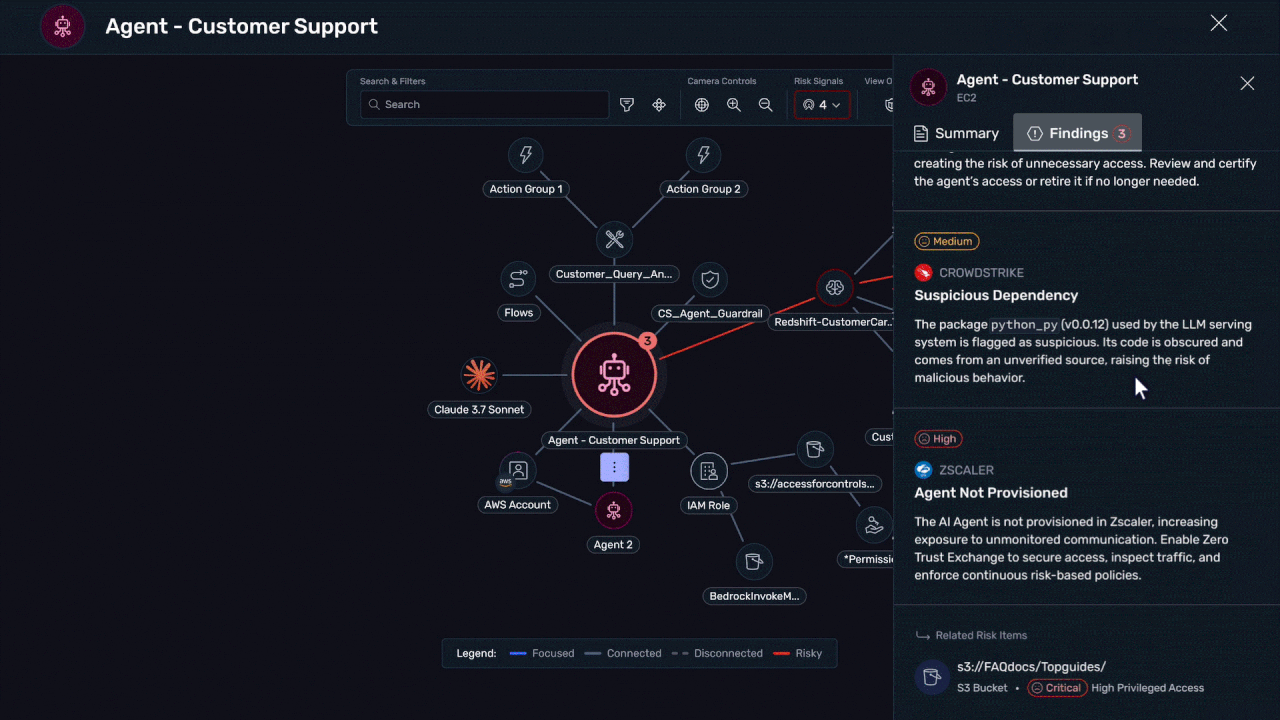
Empower your organization to use AI agents, agentic workflows, LLMs, etc., while keeping it protected from errant data leaks or excess access risks.
Legacy process elimination for Motability
Tasks eliminated for a pharmacy-led healthcare company
Entitlements secured at Syneos Health

.png?noresize&width=500&height=500&name=Director%20of%20IT%20Security%20and%20Compliance%2c%20Advanced%20Drainage%20Systems%2c%20Inc.%20(1).png)
.png?noresize&width=500&height=500&name=Director%20of%20IT%20Security%20and%20Compliance%2c%20Advanced%20Drainage%20Systems%2c%20Inc.%20(2).png)











“We chose Saviynt because we trust their leadership. They put the quality of their solutions above all else.”
