Implement a robust ICAM solution with a Zero Trust security strategy with Oxford Computer
ICAM enables the right individual to access the right resource, at the right time, for the right reason.


Better Together
Together OCG and Saviynt, along with technology from Microsoft, can design and implement a zero trust-based Identity, Credential, and Access Management (ICAM) solution to help your organization stay compliant and safe from cyber attacks. Microsoft via Azure Active Directory provides the foundational Identity & Access Management layer natively integrated with Azure Government Cloud to meet the appropriate compliance requirements. Saviynt natively integrates with AD to provide Identity Governance and Administration, and OCG provides implementation services from discovery to deployment.
Eliminate implicit trust and adopt continuous verification to protect against cyber threats.
Granular, risk-based controls and security automation to better protect data and infrastructure from threats in real-time.
Centralize identity management to protect users and provide access to the right data at the right time, streamlining processes and improving efficiency.
Meet the Federal Zero Trust Mandate with an ICAM-focused architecture
Protect against external cyber threats and insider threats while staying compliant.
A primary target for cyber attacks is Federal Identity, Credentials, and Access Management (ICAM) systems. Compromising these systems enables attackers to assume the identity of federal users and can allow unfettered access to government data and systems.
The federal government is undertaking a massive transformation from on-premises to a cloud-first infrastructure. This transformation requires a radical change in how we view ICAM as it becomes the foundation for how we secure both cloud and on-premises data and applications.
Federal agencies must also comply with new requirements and upgrade their ICAM requirements as they move to the cloud. Oxford Computer Group (OCG) partnered with Microsoft and Saviynt to build and provide the solution for an effective ICAM program that meets the criteria for a robust Zero Trust security solution.
An effective ICAM program should be based on the following principles:
- Zero Trust mindset
- Single Identity Model
- Least Privilege Access
- Multi-Factor Authentication
- Risk-Based Identity Analytics
- Conditional Access
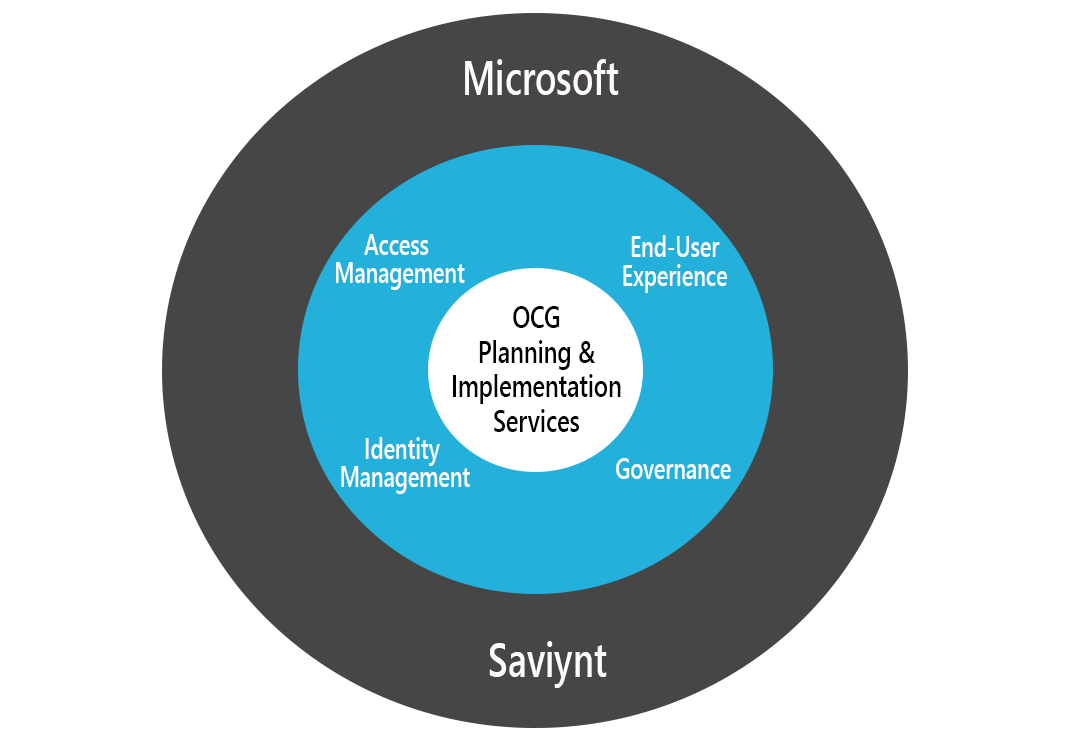
Microsoft via Azure Active Directory provides the foundational Identity & Access Management (IAM) layer natively integrated with Azure Government Cloud to meet the appropriate compliance requirements.
Saviynt natively integrates with AD to provide Identity Governance and Administration (IGA). OCG provides implementation services from discovery to deployment.
Explore: Saviynt + Oxford Computer Group

On-Demand Webinars
Identity, Credentialing, and Access Management (ICAM) and Executive Order 14028

Article
Moving Towards Zero Trust with an ICAM Solution Architecture

Solution Guide