Saviynt Integration for Cerner
Enable frictionless access to accelerate patient care delivery.

Fully Automated Access Governance
Saviynt’s integration for Cerner enhances access governance through fully automated access workflows, separation of duty (SoD) risk evaluations, robust role management, and powerful analytics for superior compliance and reduction in standing privileges. Enable Saviynt for Cerner individually, or as a part of Saviynt’s Healthcare Identity Cloud.
Improve Operational Efficiency
Centralize identity governance, automate access for internal and external personnel, and reduce friction for your staff, even as they frequently change roles.
Protect Patient & Organizational Data
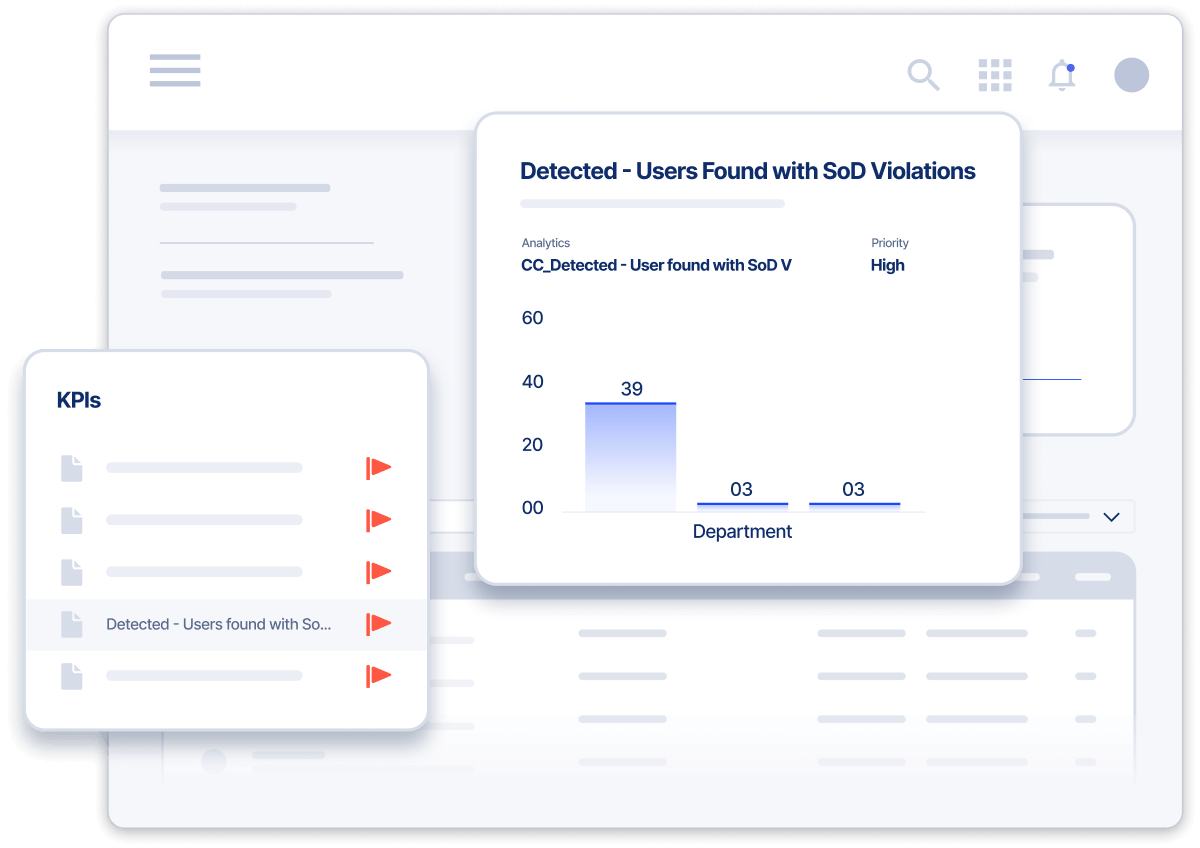
Leverage peer and behavioral analytics to detect high-risk activity based on risk scoring parameters, including outlier access, policy/control violations, threat intelligence and event rarity.
Ensure Compliance for HIPAA, HITECH and Other Regulations
Deliver continuous regulatory compliance and robust reporting for audits. Create risk-based controls that address various compliance mandates.
Configure Request, Approval, and Provisioning Workflows
Quickly design, implement, review, and adjust workflows and approval steps based on your needs and changing business requirements
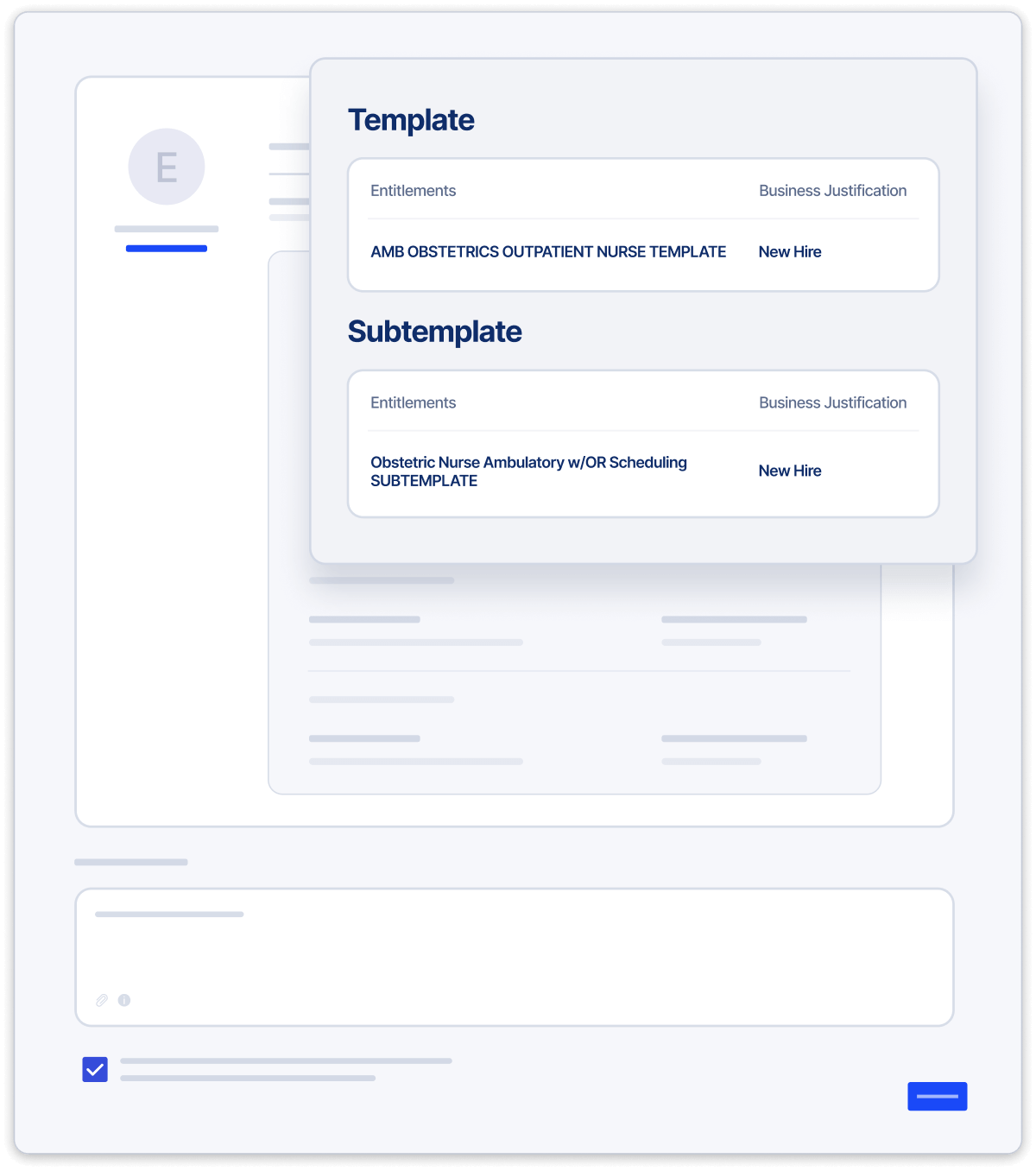
- Provision multiple security templates and sub-templates
- Powerful and flexible enough to handle straightforward auto-approvals, to complex and context-based multi-step approvals
- Integrate with your learning management system (LMS) to automate training compliance
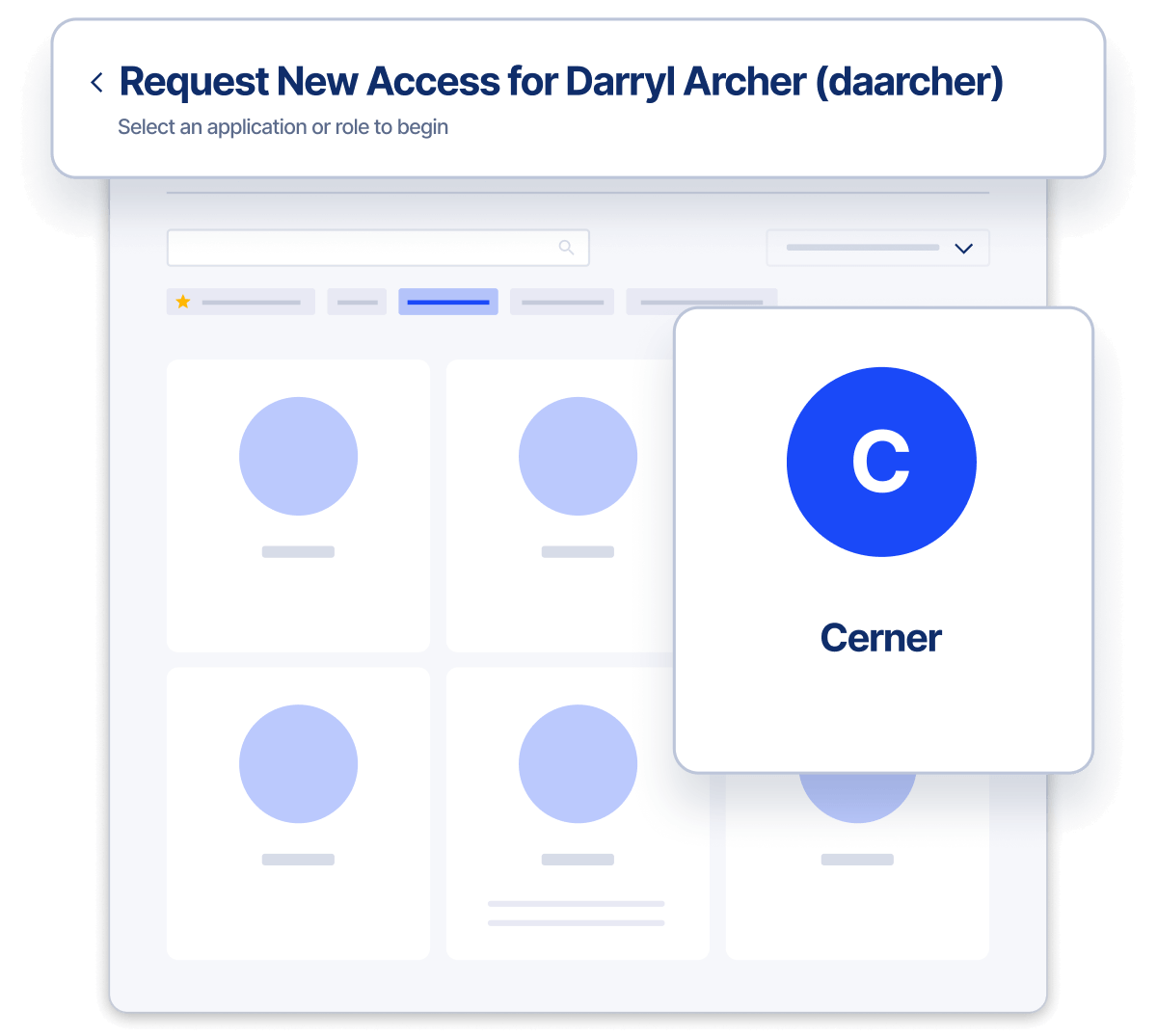
Seamlessly Integrate Without Custom Coding
Leverage a no/low code experience that reduce administrative headaches and simplifies onboarding
- Use a pre-configured connector to utilize Cerner’s API for user record and position management
- Implement SOD management based on your specific rule sets
- Integrate with credentialing solutions to manage provider access
Maintain Compliance with Confidence
- Out of the box controls mapped to HIPAA, HITRUST, PCI and other mission-critical regulations to help maintain continuous compliance
- Compile and deliver attestation reports to auditors with end-to-end data trails
Reduce standing privileges with just-in-time access elevation - Consolidate identities and authoritative identity sources
- Reduce standing admin privileges to Cerner production through JIT access elevation workflows
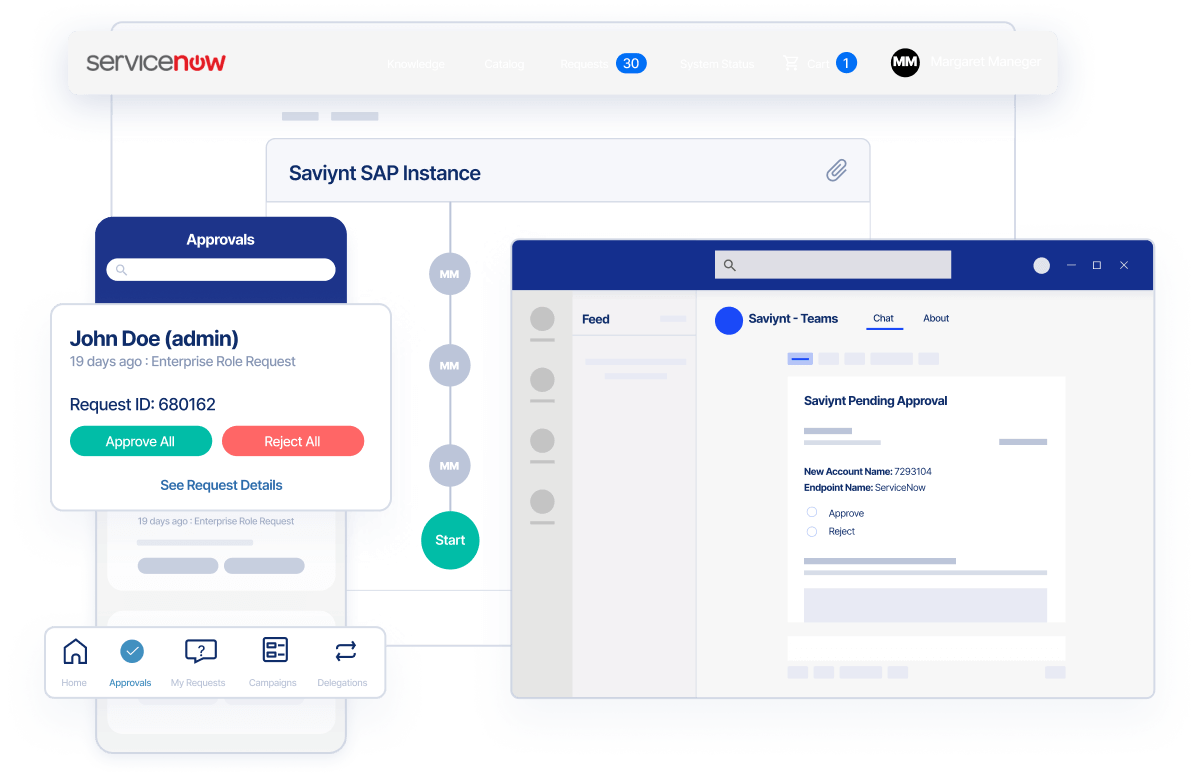
Deliver Frictionless Access
- Automate intelligent role and rule-based provisioning and attribute-based access controls
- Reduce manual steps and delays that create barriers to patient care delivery
- Request and approve access from anywhere with a mobile app, browser plug-in and collaboration tool (MS Teams and Slack) integration

Saviynt Healthcare Identity Cloud Solution Guide for Cerner
Read the Saviynt Healthcare Identity Cloud Solution Guide for Cerner to learn:
- Why you need Saviynt Healthcare Identity Cloud to secure your Cerner environment
- How you can improve operational efficiency
- How Saviynt provides broader visibility to Cerner identity risks