Saviynt for AWS
Simplify and secure AWS access – every workload, every instance, every time.

Reinforce AWS security with industry-leading governance and posture management
Gain visibility and control over who can access critical AWS resources. Enforce the principle of least-privilege access with just-in-time and just-enough access to eliminate standing permissions and reduce the attack surface. Continuously monitor access patterns and apply governance controls to proactively identify risks, maintain compliance and ensure audit readiness across your AWS environments.
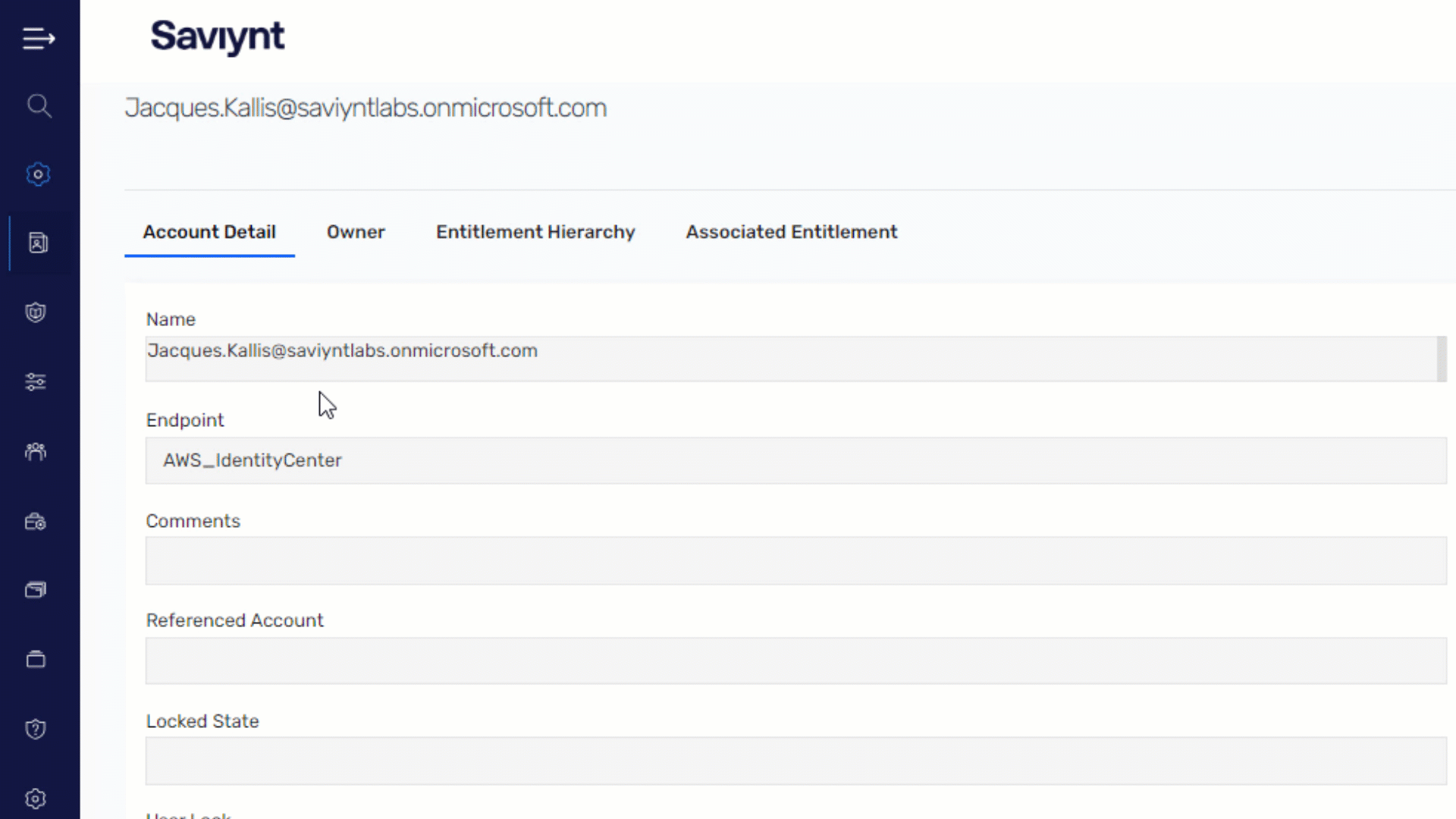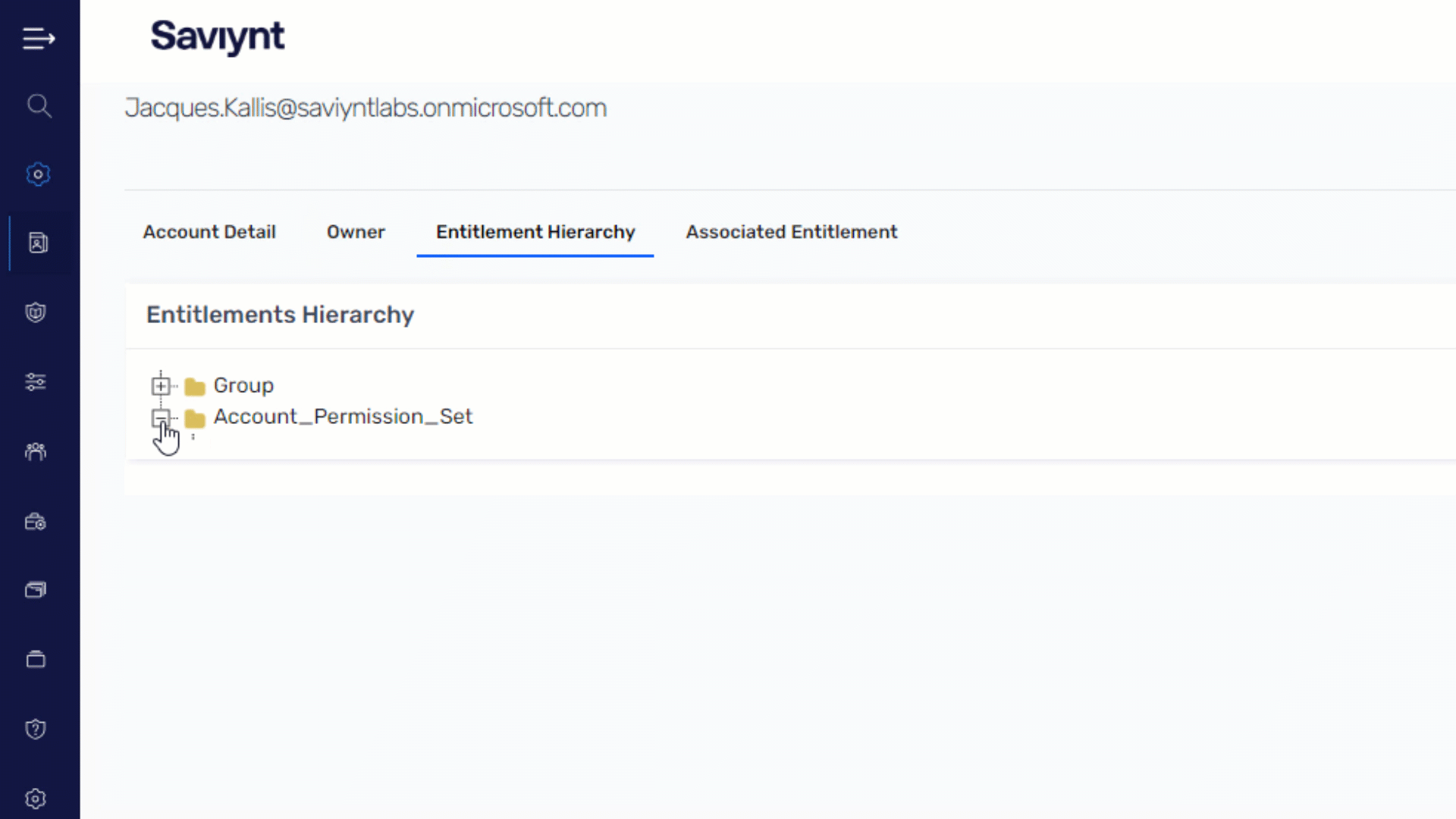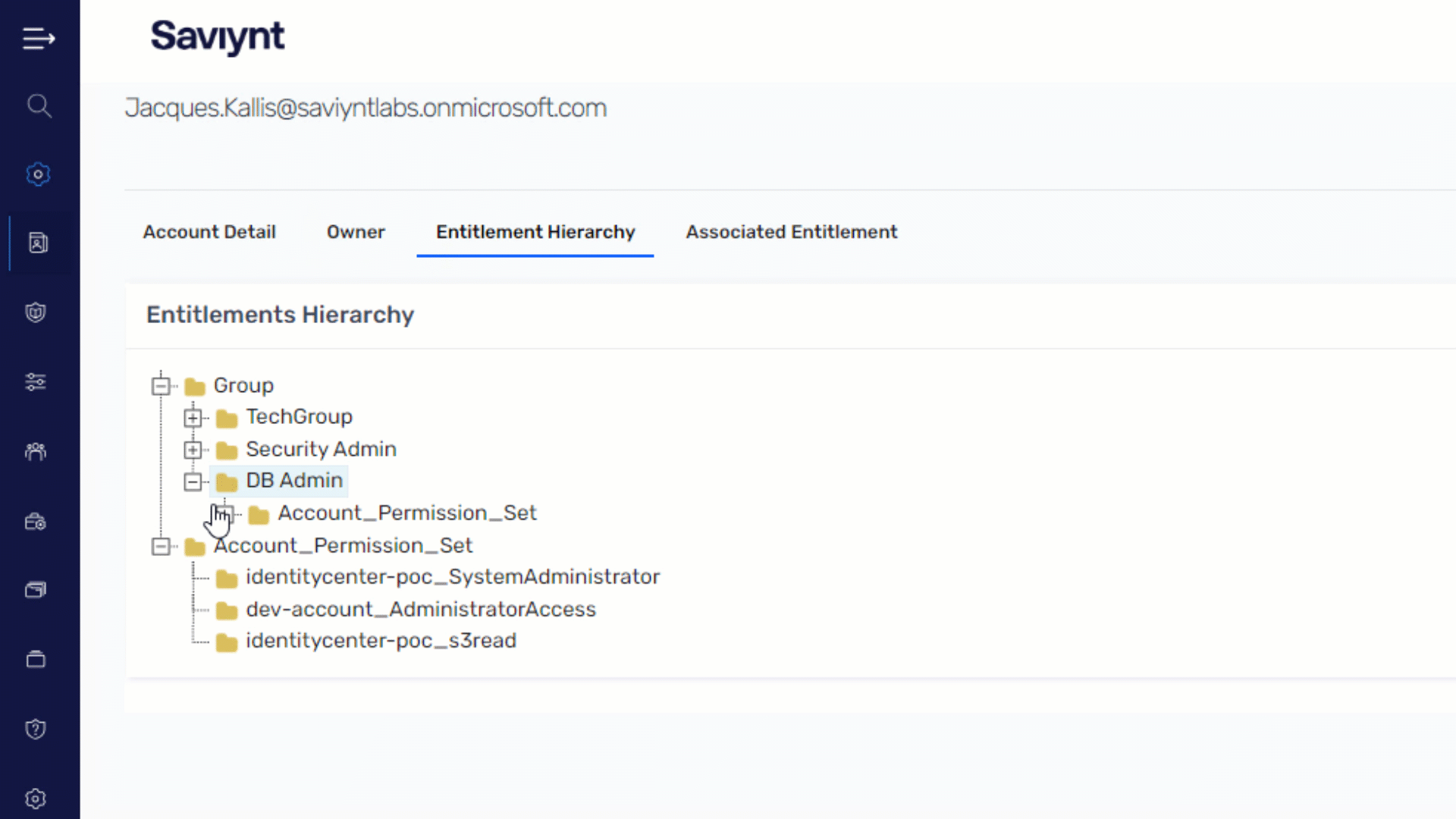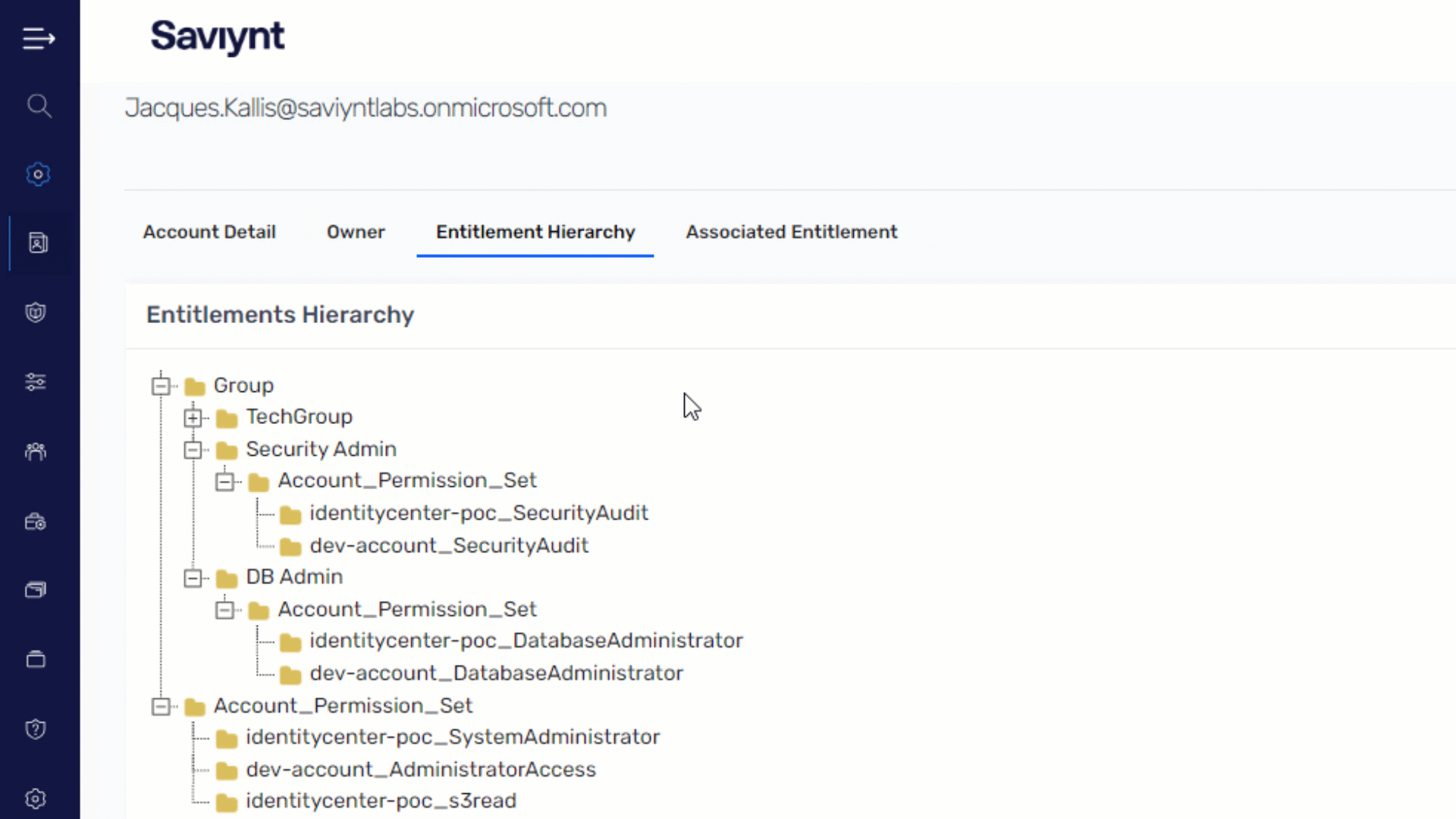
Ensure Secure and Compliant Identity Access Management
Extend governance across your AWS environment to ensure right-level, right-time access for any identity
- Gain 360-degree visibility of all identities; govern access for workforce, external, service accounts, and non-human identities
- Automate identity lifecycle management across your AWS environment for any joiner, mover, or leaver scenario
- Identify and remediate SoD conflicts with preventative and detective measures
Enforce Least Privileged Access Across all AWS Environments
Ensure access is appropriate, controlled, and monitored to reduce the attack surface
- Automate just-in-time and just-enough-access to AWS and non-AWS systems to eliminate standing privilege
- Eliminate orphaned accounts with just-in-time account provisioning
- Support audits and prove compliance with end-to-end session recording and keystroke logging
- Define and manage access down to the resource level to support least privilege access
Elevate Your Identity Posture
Proactively identify and remediate risks before they become incidents
- Continuously monitor access, data, and governance posture to detect anomalous behavior and problematic access patterns
- Prioritize risk remediation for the highest impact risks with intelligent recommendations and minimize windows of opportunity for bad actors
- Cut through fatigue with smart, actionable reporting
- Promptly clip unused access across roles, passwords/secrets, access keys and permissions
Resources

Solution Guide
Saviynt for AWS

Solution Guide
Unify Identity Governance and Privileged Access Management with Saviynt Identity Cloud

Podcast
Getting Ahead of the Curve - How Saviynt Automates Identity Security at Scale

Solution Guide
Saviynt Identity Security Posture Management (ISPM)

Case Study
Saviynt for AWS Environment Case Studies

Press Release
AWS Signs Strategic Collaboration Agreement With Saviynt to Advance AI-Driven Identity Security

Press Release