What is the General Data Protection Regulation (GDPR)?
What is the General Data Protection Regulation (GDPR)?
Beginning in May 2018, the General Data Protection Regulation (GDPR) standardized data privacy regulation in Europe, giving power to individuals regarding the gathering and usage of their personal data. Specifically, GDPR covers how the personal data of people who live in EU is collected, stored, and managed. With 99 articles and 173 recitals, the GDPR represents a playbook for the rules and regulations governing the use of an EU citizen’s personal data by companies.
At its core, the regulation gives individuals the power to dictate how and when an organization collects and uses their personal data. Another goal of the GDPR is to simplify the compliance landscape as it standardizes data privacy laws across the entire region.
Understanding Personal Identifying Information (PII)
GDPR’s definition of Personal Identifying Information (PII) far exceeds that of existing definitions.
‘Personal data’ means any information relating to an identified or identifiable natural person (‘data subject’); an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person.
By this definition, any data associated with an individual qualifies as personal data. The GDPR also provides individuals with a number of rights.
The 8 Rights of the GDPR
- The right to be informed: information must be provided when you collect personal data directly from individuals.
- The right to access: individuals need to be able to access the personal data that is collected.
- The right to rectification: individuals can request that an organization correct inaccurate data, or complete incomplete data.
- The right to erasure: individuals have the right to ask that their data be erased.
- The right to restricted processing: under certain conditions, an individual may ask that an organization limit the processing of their data.
- The right to portability: if data is requested, it must be provided in a digestible and transportable format.
- The right to object: the ability to request that an organization stop processing their data.
- The right to avoid automated decision-making: if a decision will have a legal effect an individual has the right to ensure that it is not made via automation.
The GDPR requires organizations that gather, store, and process data belonging to EU citizens have the capabilities in place to protect their data and privacy. It also regulates the transfer and storage of PII outside of the EU. To achieve compliance with GDPR, an organization must be able to collect, house, and provide access to personal data in a manner consistent with the regulation.
Two key concepts incorporated into the GDPR are the roles of controller and processor. They are defined as follows:
- ‘Controller’ refers to the natural or legal person, public authority, agency or other body which, alone or jointly with others, determines the purposes and means of the processing of personal data; where the purposes and means of such processing are determined by Union or Member State law, the controller or the specific criteria for its nomination may be provided for by Union or Member State law.
- ‘Processor’ refers to a natural or legal person, public authority, agency or other body which processes personal data on behalf of the controller.
However, unlike other data privacy regulations, Article 25 of the GDPR raises the bar for corporate compliance as it calls for “data protection by design and default” often known as “security by design.”
Key Definitions & Principles Enshrined in GDPR
- Consent: a data subject’s consent to process data must be freely given, be specific, informed, and unambiguous. Consent should be provided per purpose, and subject to revoke at any time.
- Right to Erasure: data subjects have the right to request that the controller erase their data when the data is no longer necessary for the purpose(s) collected, the subject withdraws consent, or objects to data processing.
- Designation of Data Protection Officers: both controllers and processors must designate a data protection officer (DPO) if their primary activities involve regular and systematic monitoring or processing of personal data. A DPO reports to the organization’s highest level of management.
- Data Breach Notification: controllers must notify their country’s supervisory authority of a breach within 72 hours.
How to Achieve Compliance with the General Data Protection Regulation (GDPR)
Machine identities are software-based network “users” that are a subset of the broader category of “identities” which include humans, including both your employees and customers.
Examples of machine identities include Application Programming Interfaces (APIs) and Robotic Process Automation (RPAs or “bots”). They do the background jobs such as connecting services across the cloud ecosystem or managing repetitive administrative tasks.
These silicon-based “users” interact with sensitive company and personally identifiable information (PII) just as typical human users do.
Leveraging Identity Governance to Meet GDPR Requirements
Adjusting internal processes and systems in order to achieve compliance with GDPR takes time, given the depth and scope of the regulation. Compliance with GDPR requires organizations to have solutions deployed to manage personal data of different types of users — employees, contractors, customers, partners and suppliers, along with their access. Identity Governance solutions help manage digital identity and access rights of these user types across various systems. Enterprise IGA solutions focus on digital identities within the enterprise, namely employees and contractors, and provide visibility to the personal data that it disseminates to connected systems. It also helps govern access to systems that store or process personal data.
Enterprise IGA solutions can be used to achieve the objectives of data minimization and pseudonymization. On the other hand, Customer IDM (identity management) solutions provide similar capabilities to collect and manage customer data.
As part of an organization’s compliance efforts, these Identity Governance solutions can be leveraged to record consent to capture and process personal data, as well as comply with elements of GDPR such as the right to object to data processing, or the right to request the deletion of their data.
Another critical aspect is to discover and protect personal data stored in unstructured format within enterprise or cloud collaboration platforms. Identity Governance solutions help in identifying such data, assigning data ownership, and ensuring that only authorized users have access to personal data. Better Data Access Governance platforms increase an organization’s visibility of data breaches, and therefore, its ability to conduct to create notifications in a timely manner, consistent with the timelines outlined by the GDPR.
Customer IDM solutions support self-registration and social logins using Facebook and LinkedIn, also known as “bring your own identity” or BYOID, streamlining the process. Consequently, Customer IDM increases the number of successful registrations. However, instead of relying on social media credentials to facilitate a customer’s initial registration, an organization may want their Customer IDM solution to support a risk-based approach to registration, also known as Identity Proofing, that requires customers to provide information only they know such as their prior home addresses, educational institutions attended, or the lender on their automobile or primary residence.
In addition to helping companies satisfy existing regulatory requirements, Customer IDM integrates with internal platforms such as customer relationship management systems (CRMs), providing a single view of the customer’s activities and records — including the PII in the organization’s possession, customer consent approvals, and data access history. Furthermore, Customer IDM solutions are scalable in that they possess the ability to support large number of customers, usually in millions.
As it relates to GDPR compliance, Identity Governance solutions provide organizations with the ability to provision and manage access and therefore satisfy a number of requirements.
Consequences of Non-Compliance with the General Data Protection Regulation (GDPR)
Since the GDPR covers any organization that collects EU citizen data, its impact extends far beyond the region itself. And the GDPR carries significant fines and penalties for non-compliance of up to 4% of annual global revenue, or approximately $22 million (whichever is higher). GDPR also requires that companies report the existence of a data breach within 72 hours of its occurrence.
While the degree of compliance readiness varies, some companies in both Europe and the United States, in particular, appear unprepared to comply with GDPR.
Saviynt & the General Data Protection Regulation (GDPR)
Identity Governance and Administration (IGA) and by extension, Identity Access Management (IAM), play a critical role in providing organizations with the means to manage and maintain user identities and govern access to personal data to satisfy the onerous requirements enshrined within GPDR. Saviynt’s IGA solution can help you prioritize the capabilities that provide the most value, with less deployment risk.
Saviynt simplifies IGA by increasing organizational agility through automation and intuitive workflows. We do this by offering an identity and access governance platform that unifies identity governance capabilities into a single cloud-based solution. The solution provides visibility, IT efficiencies, and improved internal controls, reducing the risk of compromised credentials and audit failures.
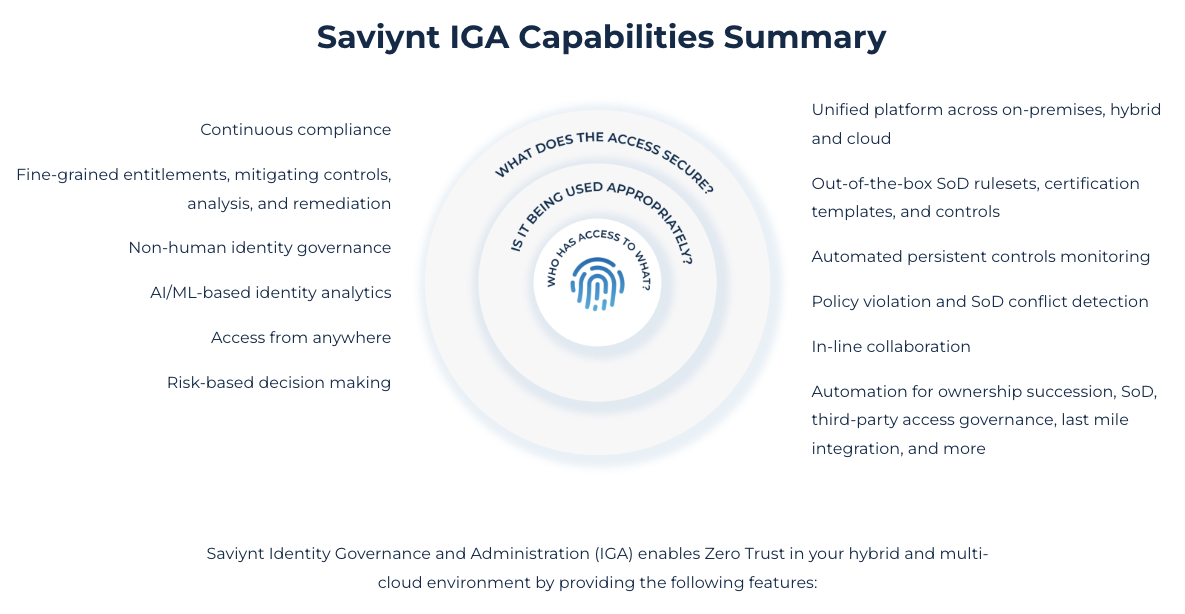
- Industry-leading cloud architecture built for enterprise scale & flexibility
- Governance for all human and machine identities – including third parties
- Modern web interface, mobile app, browser plug-in, and ServiceNow app
- Rapid application & identity onboarding with pre-built templates and discovery of unmanaged assets & applications
- AI & ML-powered identity analytics identify risk and duplicate identities, and close access gaps
- Actionable insights for identity management, compliance, and security via the Control Center
How does Saviynt’s IGA solution affect your bottom line? Forrester’s Total Economic Impact™ (TEI) study examines the return on investment (ROI) organizations realize with the Saviynt Enterprise Identity Cloud. In this commissioned study, Forrester estimates that implementing Saviynt can save your organization $34.4M and achieve a 240% ROI over three years.
Resources