What is a Cyber Kill Chain?
As digital transformation continues to shape the global business landscape, cybersecurity has become a top priority for organizations of all sizes. The rise of cyber threats, from malware to ransomware, to sophisticated state-sponsored attacks, demands a comprehensive understanding of how they occur and how they can be thwarted. One tool that has proven invaluable in this effort is the Cyber Kill Chain, a framework developed by Lockheed Martin that outlines the stages of a cyber attack. Understanding these cyber security attack phases can help security teams employ effective strategies to both prevent and break the cycle of an active attack. This discussion will explore the Cyber Kill Chain model, its practical business uses, and its benefits to an organization’s cybersecurity strategy.
What is the Cyber Kill Chain?
The “Cyber Kill Chain” is a framework developed by Lockheed Martin, a major U.S. defense contractor, to understand and analyze intrusions into computer networks. It’s a series of steps that trace stages of a cyberattack from the early reconnaissance stages to the exfiltration of data.
The cyber kill chain concept is derived from the military term “kill chain,” which refers to the structure of an attack involving identifying a target, dispatching forces to the target, deciding on and ordering an attack, and ultimately destroying the target.
The IT landscape has changed significantly since Lockheed Martin introduced the cyber kill chain concept in 2011. The traditional network perimeter has effectively dissolved, with workloads and data shifting to the cloud. Attackers are also constantly improving their tactics, techniques and procedures (TTPs). That said, understanding the Cyber Kill Chain steps is a good place to start:
-
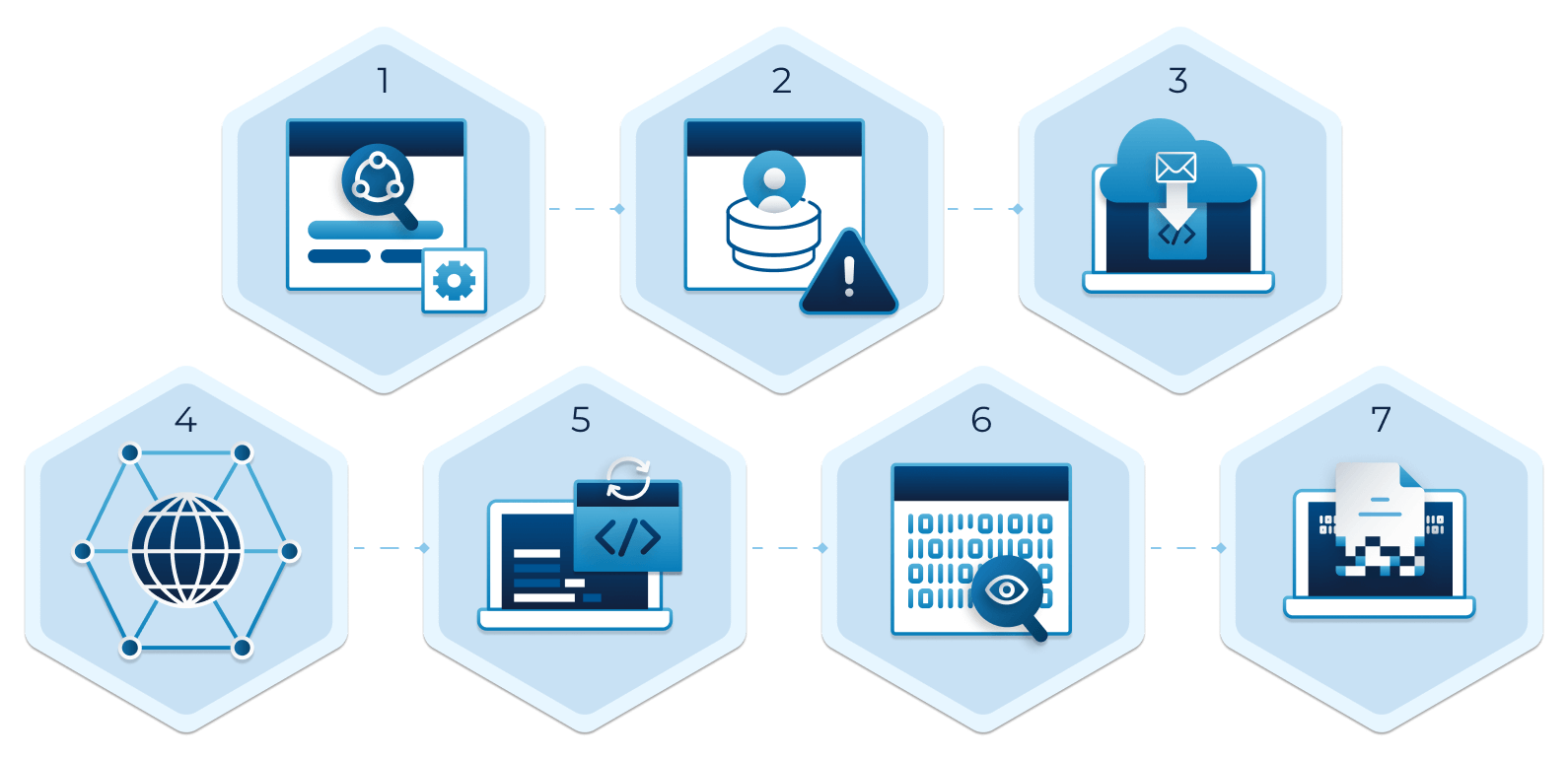
Reconnaissance is the first phase of the cyber kill chain, where the attacker gathers preliminary data or intelligence on a target to identify vulnerabilities. The information is often gathered using various techniques, such as public information on the internet and social engineering.
-
Weaponization: After reconnaissance, the attacker creates a malicious code to exploit the vulnerabilities discovered during the reconnaissance phase. Weaponization often involves packaging a payload (the part of the malware that performs the malicious action) with an exploit into a deliverable format like a PDF or Word document.
-
Delivery: The attacker delivers the weaponized bundle to the victim via email (phishing), a malicious website, or a USB drive. Delivery is the stage where the payload is sent to the victim.
-
Exploitation: This phase of the cyber kill chain involves the execution of the malicious code on the victim’s system. The exploit targets an application or system vulnerability, allowing the attacker to establish a foothold in your network and attempt to install malware, extract password hashes, and escalate privileges to gain control over the system.
-
Installation: The payload, if not immediately harmful (e.g., ransomware), is typically a backdoor that allows the attacker to maintain continued access to the compromised system.
-
Command and Control (C2): The attacker now has ‘hands on the keyboard’ control over the network. The attacker can continue navigating the network to find and reach their target.
-
Actions on Objectives: This is the final stage where the attacker achieves their goals, such as data exfiltration, data destruction, or encryption for ransom.
Understanding the Cyber Kill Chain can help cybersecurity professionals to anticipate and prevent cyberattacks by strengthening defenses at each stage and increasing the difficulty for attackers to progress.
How Can Defenders Use the Cyber Kill Chain to Thwart Attacks?
Cybersecurity professionals use the Cyber Kill Chain model to determine which controls to use at each phase of a cyberattack to block the adversary. Here’s how they use it:
-
Reconnaissance: It can be difficult to detect reconnaissance activities but security teams should monitor activity like multiple failed login attempts or port scanning on public-facing servers. Regular vulnerability scanning, patch management, and robust data protection controls can help deter an attacker. .
-
Weaponization: Security defenders cannot detect weaponization as it’s happening, they can make inferences based on analyzing malware artifacts and building detection rules for ongoing defense.
-
Delivery: This is the first opportunity for defenders to identify, detect and block malware delivery. Or, if an intrusion is detected after the fact, security teams should continue gathering intelligence to contain the damage.
-
Exploitation: Doing the basics, like vulnerability scanning, hardening endpoints, and user awareness training can help with prevention. Employing Zero Trust identity security and just-in-time privileged access management, can also help limit the attacker’s ability to move throughout the network in an active breach i.
-
Installation: Security operations teams can use their endpoint detection and response (EDR) tools to detect and analyze malware, and determine if malware requires administrator privileges or normal user privileges.
-
Command and Control: This is your defenders’ last chance to block the operation. Use monitoring tools to detect suspicious network activity like communications with unknown DNS servers.
-
Actions on Objectives: Use data forensics and incident response to understand indicators of compromise and assess breach impact.
However, it’s important to note that not all cyberattacks strictly follow the Cyber Kill Chain model. Advanced persistent threats (APTs), for example, may repeat stages or skip some altogether, and some attacks may be so fast and automated that there’s little time for an intervention. Nonetheless, the Cyber Kill Chain remains a helpful framework for understanding and combating cyber threats.
What is the Role of the Cyber Kill Chain in Cybersecurity
The benefits of employing the Cyber Kill Chain are manifold. Enhanced understanding of potential threats allows organizations to better prepare for and respond to cyberattacks. A more strategic defense approach saves resources and increases overall security efficacy. Improved incident response minimizes the damage and downtime caused by a breach.
Using the Cyber Kill Chain model can offer other key advantages:
-
Enhanced Understanding: It provides a conceptual framework for understanding the steps that adversaries take to launch attacks, which helps the organization recognize, prepare for, and potentially prevent cyber threats.
-
Strategic Defense: The model helps organizations prioritize their defenses by understanding the most critical stages of an attack and where their systems and networks are most vulnerable. This knowledge can help organizations allocate resources efficiently and build more effective defenses.
-
Incident Response: It aids in incident response and forensics by identifying the stage at which a cyber intrusion is detected. This can help an organization take appropriate action faster, such as isolating systems or networks, gathering evidence, and removing threats.
-
Predictive Capability: By understanding the typical progression of a cyber attack, an organization can better anticipate and counter threats before they cause significant damage.
-
Risk Management: It’s a valuable risk assessment and management tool, enabling organizations to identify gaps in their defenses and devise mitigation strategies.
-
Training and Awareness: The model can educate technical and non-technical staff about cyber threats, making them more aware of how attacks occur and how they can prevent them.
-
Proactive Security Culture: Overall, using the Cyber Kill Chain model helps foster a proactive security culture in an organization, which can make all the difference in today’s evolving cyber threats landscape.
Remember, while the Cyber Kill Chain model is a useful tool for combating cyber attacks, it doesn’t provide a complete solution to cybersecurity. It’s most effective when used as part of a multi-layered security approach that embraces Zero Trust principles, modern technologies that can share analytics and risk data, and constant vigilance against the latest threat trends.
Saviynt & the Cyber Kill Chain
Saviynt helps companies harden their defenses by enabling companies to adopt a Zero Trust identity strategy that recognizes that identity as the new security perimeter. Moving to Zero Trust helps organization strengthen their cybersecurity by limiting an attacker’s ability to access elevated credentials, move laterally throughout the network and access sensitive data or critical systems.
Saviynt Enterprise Identity Cloud helps ease the move to Zero Trust Model by providing in-depth visibility, automation, and centralized, continuous monitoring.
Saviynt Cloud Privileged Access Management (Cloud PAM) helps organizations shrink their attack surface by enabling them to move to just-in-time PAM, where all privileged accounts – except for those necessary for break-glass purposes – are removed. System administrators gain access only when it’s required and only in the period of time it’s required for. Once the administrative task is completed, access goes away, greatly minimizing the chance that an attacker is able to assume elevated rights and move to advanced Cyber Kill Chain stages like Command and Control and Actions on Objectives.
In addition to simplifying just-in-time privileged access, Saviynt Cloud PAM helps organization secure their multi-cloud footprint in the following ways:
Continuously Discovering Cloud Risks
Traditional PAM solutions scan environments at fixed intervals, but cloud resources are constantly scaling up and down. Saviynt’s cloud-native PAM solution discovers changes occurring within elastic workloads, new privileged accounts, and access in real-time. This helps security teams identify misconfigured objects and automatically trigger remediation steps, such as terminating a session and removing a user’s access.
Establishing Identity-Driven PAM Governance
Saviynt’s PAM solution is built on our converged Enterprise Identity Cloud platform and provides identity-driven access with integrated risk and governance. Combining PAM and identity governance on a unified platform, enables organization manage standard and privileged identities – both human and machine – across any platform and application and make smarter decisions with governance-driven risk data and AI-informed privileged access data
Simplify Deployment and Management
As the Identity and Access Management (IAM) market has evolved over the years, organizations have had to manage and integrate multiple, disparate tools, resulting in in high professional services or coding costs and ultimately, many gaps in risk visibility. With Saviynt Identity Cloud, organizations can unify critical identity management capabilities on one platform. Deploying our cloud-native SaaS-based solution helps organizations accelerate time to value, shrink TCO, and achieve rapid ROI with no on-prem infrastructure and an efficient user experience.
Resources

Modern Identity Governance & Administration for Mid-sized Organizations